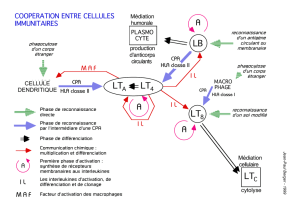
Cours de cryptologie avancée



CPA


Introduction to Modern Cryptography
Foundations of Cryptography - Volume 1 & 2
http://www.wisdom.weizmann.ac.il/~oded/foc.html
Lecture Notes on Cryptography
http://cseweb.ucsd.edu/~mihir/papers/gb.html
Le Chiement Asymétrique et la Sécurité Prouvée
http://www.di.ens.fr/users/pointche/Documents/Reports/2002_HDRThesis.pdf
 6
6
 7
7
 8
8
 9
9
 10
10
 11
11
 12
12
 13
13
 14
14
 15
15
 16
16
 17
17
 18
18
 19
19
1
/
19
100%