DOCUMENT NUMBER
9S12DP512DGV1/D
MC9S12DP512
Device Guide
V01.25
Covers also
MC9S12DT512, MC9S12DJ512,
MC9S12A512
Original Release Date: 27 Nov 2001
Revised: 05 Jul 2005
Motorola, Inc
Motorola reserves the right to make changes without further notice to any products herein to improve reliability, function or
design. Motorola does not assume any liability arising out of the application or use of any product or circuit described herein;
neither does it convey any license under its patent rights nor the rights of others. Motorola products are not designed, intended,
or authorized for use as components in systems intended for surgical implant into the body, or other applications intended to
support or sustain life, or for any other application in which the failure of the Motorola product could create a situation where
personal injury or death may occur. Should Buyer purchase or use Motorola products for any such unintended or unauthorized
application, Buyer shall indemnify and hold Motorola and its officers, employees, subsidiaries, affiliates, and distributors harmless
against all claims, costs, damages, and expenses, and reasonable attorney fees arising out of, directly or indirectly, any claim of
personal injury or death associated with such unintended or unauthorized use, even if such claim alleges that Motorola was
negligent regarding the design or manufacture of the part.
1
DOCUMENT NUMBER
9S12DP512DGV1/D
Revision History
Version Revision Effective
Number
Date
Date
V01.00
27 Nov
2001
Author
Description of Changes
11 Feb
2002
- Initial version based on DP256 V2.09.
V01.01
13 Mar
2002
13 Mar
2002
- Updated document formats.
- Removed reference to SIM in overview.
- Changed XCLKS to PE7 in signal description.
- Removed "Oscillator start-up time from POR or STOP" from Oscillator
Characterisitcs.
- Changed VDD and VDDPLL to 2.35V.
- Updated CINS.
- Updated IOL/IOH values.
- Updated input capacitance.
- Updated NVM timing characteristics.
V01.02
02 Apr
2002
02 Apr
2002
- Updated document reference (SPI, SCI).
V01.03
15 Apr
2002
15 Apr
2002
- Corrected values in device memory map (RAM start, flash protected
sector sizes).
- Updated document reference (SCI).
V01.04
06 Jun
2002
06 Jun
2002
- Changed all operating frequency references to 50MHz EXTAL and
removed references to 80 pin LQFP.
05 Jul
2002
- Preface Table "Document References": Changed to full naming for
each block.
- Table "Interrupt Vector Locations", Column "Local Enable": Corrected
several register and bit names.
- Table "Signal Properties": Added column "Internal Pull Resistor".
- Table "PLL Characteristics": Updated parameters K1 and f1
- Figure "Basic Pll functional diagram": Inserted XFC pin in diagram
- Enhanced section "XFC Component Selection"
- Added to Sections ATD, ECT and PWM: freeze mode = active BDM
mode.
V01.05
05 Jul
2002
Motorola reserves the right to make changes without further notice to any products herein to improve reliability, function or
design. Motorola does not assume any liability arising out of the application or use of any product or circuit described herein;
neither does it convey any license under its patent rights nor the rights of others. Motorola products are not designed, intended,
or authorized for use as components in systems intended for surgical implant into the body, or other applications intended to
support or sustain life, or for any other application in which the failure of the Motorola product could create a situation where
personal injury or death may occur. Should Buyer purchase or use Motorola products for any such unintended or unauthorized
application, Buyer shall indemnify and hold Motorola and its officers, employees, subsidiaries, affiliates, and distributors harmless
against all claims, costs, damages, and expenses, and reasonable attorney fees arising out of, directly or indirectly, any claim of
personal injury or death associated with such unintended or unauthorized use, even if such claim alleges that Motorola was
negligent regarding the design or manufacture of the part.
2
MC9S12DP512 Device Guide V01.25
Version Revision Effective
Number
Date
Date
V01.06
24 Jul
2002
24 Jul
2002
Author
Description of Changes
- Updated SPI electrical characteristics.
- Updated Derivative Differences table.
- Added ordering number example.
- Added Detailed Register Map.
- Changed Internal Pull Resistor column of signal table.
- Added pull device description for MODC pin.
- Corrected XCLKS figure titles. Moved table to section Modes of
Operation.
- Removed ’1/2’ from BDM in Figure Clock Connections.
- Completely reworked section Modes of Operation. Added Chip
Configuration Summary and Low Power Mode description.
- Changed classification to C for internal pull currents inTable 5V I/O
Characteristics.
- Changed input leakage to 1uA for all pins.
- Updated VREG section and layout recommendation.
- Moved Power and Gound Connection Summary table to start of
Power Supply Pins section.
- Added ROMONE to pinout
- Corrected mem map: ’MEBI map x of 3’
- Corrected mem map: KEYEN bits in FSEC.
- Added section Printed Circuit Board Layout Proposal.
- Corrected addresses in Reserved, CAN and EEP buffer map.
- Updated NVM electricals.
V01.07
29 Jul
2002
05 Aug
2002
V01.08
21 Aug
2002
21 Aug
2002
- Updated table ’Document References’
- Added section ’Oscillator (OSC) Block Description’
V01.09
24 Sep
2002
24 Sep
2002
- Section HCS12 Core Block Desciption: mentioned alternalte clock of
BDM to be equivalent to oscillator clock
- Corrected tables 0-1 and 0-2
V01.10
18 Oct
2002
18 Oct
2002
- Added derivatives to cover sheet.
- Added part ID for 1L00M maskset.
- Corrected in footnote of Table "PLL Characteristics": fOSC = 4MHz.
V01.11
29 Oct
2002
29 Oct
2002
- Renamed Preface section to Derivative Differences and Document
references.
- Added A512 derivative.
- Updated module set of DJ512 in Table 0-1.
- Added details for derivatives without CAN and/or BDLC modules.
V01.12
03 Dec
2002
03 Dec
2002
- Corrected several entries in ’Detailed Memory Map’.
- Removed footnote on input leakage current from table ’5V I/O
Characteristics’.
V01.13
08 Jan
2003
08 Jan
2003
- Updated section ’Unsecuring the Microcontroller’.
- Updated footnote 1 in table ’Operating Conditions’.
V01.14
23 Jan
2003
23 Jan
2003
- Renamed ROMONE pin to ROMCTL.
V01.15
28 Feb
2003
28 Feb
2003
- Corrected PE[1,0] pull specification in Signal Properties Summary
Table.
3
MC9S12DP512 Device Guide V01.25
Version Revision Effective
Number
Date
Date
Author
Description of Changes
V01.16
31 Mar
2003
31 Mar
2003
- Corrections in App. A ’NVM, Flash and EEPROM’:
- Number of words per flash row = 64
- Replaced ’burst programming’ with ’row programming’
- Sector erase size = 1024 bytes
- Corrected feature description ECT
- Corrected min. bus freq. in table ’Operating Conditions’
V01.17
30 May
2003
30 May
2003
- Replaced references to HCS12 Core Guide with the individual HCS12
Block guides throughout document
- Table ’Absolute Maximum Ratings’ corrected footnote on clamp of
TEST pin
V01.18
23 Jul
2003
23 Jul
2003
- Mentioned ’S12 LRAE’ bootloader in Flash section
- Document References: corrected S12 CPU document reference
V01.19
24 Jul
2003
24 Jul
2003
- Added part ID for 2L00M maskset.
V01.20
01 Sep
2003
01 Sep
2003
- Added part ID for 3L00M maskset.
- Added cycle definition to ’CPU 12 Block Description’.
- Diagram ’Clock Connections’: Connected Bus Clock to HCS12 Core.
- Corrected ’Background Debug Module’ to ’HCS12 Breakpoint’ at
address $0028 - $002F in table 1-1.
- Corrected ’Blank Check Time Flash’ value in table ’NVM Timing
Characteristics’
- Added EXTAL pin VIH, VIL and EXTAL pin hysteresis value to
’Oscillator Characteristics’. Updated oscillator description and table
note.
V01.21
08 Mar
2004
08 Mar
2004
- Added part ID for 4L00M maskset.
- Corrected pin name KWP5 in device pinout.
V01.22
23 Aug
2004
23 Aug
2004
- Updated VIH,EXTAL and VIL,EXTAL in table ’Oscillator Characteristics’
- Removed item ’Oscillator’ from table ’Operating Conditions’ as
already covered in table ’Oscillator Characteristics’
V01.23
09 Feb
2005
09 Feb
2005
- Corrected Flash Row Programming Time in NVM Timing
Characteristics
V01.24
01 Apr
2005
01 Apr
2005
- Changed TJavg and added footnote to data retention time in NVM
Reliability Characteristics
V01.25
05 Jul
2005
05 Jul
2005
- Updated NVM Reliability Characteristics
4
MC9S12DP512 Device Guide V01.25
Table of Contents
Section 1 Introduction
1.1
1.2
1.3
1.4
1.5
1.5.1
1.6
1.7
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .19
Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .19
Modes of Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
Block Diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .22
Device Memory Map. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .24
Detailed Register Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .27
Part ID Assignments. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .49
Memory Size Assignments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .49
Section 2 Signal Description
2.1
Device Pinout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .52
2.2
Signal Properties Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .53
2.3
Detailed Signal Descriptions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .55
2.3.1
EXTAL, XTAL — Oscillator Pins . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .55
2.3.2
RESET — External Reset Pin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .55
2.3.3
TEST — Test Pin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .55
2.3.4
VREGEN — Voltage Regulator Enable Pin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .55
2.3.5
XFC — PLL Loop Filter Pin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .56
2.3.6
BKGD / TAGHI / MODC — Background Debug, Tag High, and Mode Pin . . . . . . . .56
2.3.7
PAD15 / AN15 / ETRIG1 — Port AD Input Pin of ATD1 . . . . . . . . . . . . . . . . . . . . . .56
2.3.8
PAD[14:08] / AN[14:08] — Port AD Input Pins of ATD1 . . . . . . . . . . . . . . . . . . . . . .56
2.3.9
PAD7 / AN07 / ETRIG0 — Port AD Input Pin of ATD0 . . . . . . . . . . . . . . . . . . . . . . .56
2.3.10 PAD[06:00] / AN[06:00] — Port AD Input Pins of ATD0 . . . . . . . . . . . . . . . . . . . . . .56
2.3.11 PA[7:0] / ADDR[15:8] / DATA[15:8] — Port A I/O Pins . . . . . . . . . . . . . . . . . . . . . . .57
2.3.12 PB[7:0] / ADDR[7:0] / DATA[7:0] — Port B I/O Pins . . . . . . . . . . . . . . . . . . . . . . . . .57
2.3.13 PE7 / NOACC / XCLKS — Port E I/O Pin 7 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .57
2.3.14 PE6 / MODB / IPIPE1 — Port E I/O Pin 6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .58
2.3.15 PE5 / MODA / IPIPE0 — Port E I/O Pin 5 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .58
2.3.16 PE4 / ECLK — Port E I/O Pin 4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .58
2.3.17 PE3 / LSTRB / TAGLO — Port E I/O Pin 3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .59
2.3.18 PE2 / R/W — Port E I/O Pin 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .59
2.3.19 PE1 / IRQ — Port E Input Pin 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .59
5
MC9S12DP512 Device Guide V01.25
2.3.20
2.3.21
2.3.22
2.3.23
2.3.24
2.3.25
2.3.26
2.3.27
2.3.28
2.3.29
2.3.30
2.3.31
2.3.32
2.3.33
2.3.34
2.3.35
2.3.36
2.3.37
2.3.38
2.3.39
2.3.40
2.3.41
2.3.42
2.3.43
2.3.44
2.3.45
2.3.46
2.3.47
2.3.48
2.3.49
2.3.50
2.3.51
2.3.52
2.3.53
2.3.54
2.3.55
6
PE0 / XIRQ — Port E Input Pin 0. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .59
PH7 / KWH7 / SS2 — Port H I/O Pin 7 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .59
PH6 / KWH6 / SCK2 — Port H I/O Pin 6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .59
PH5 / KWH5 / MOSI2 — Port H I/O Pin 5 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .59
PH4 / KWH4 / MISO2 — Port H I/O Pin 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .59
PH3 / KWH3 / SS1 — Port H I/O Pin 3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .60
PH2 / KWH2 / SCK1 — Port H I/O Pin 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .60
PH1 / KWH1 / MOSI1 — Port H I/O Pin 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .60
PH0 / KWH0 / MISO1 — Port H I/O Pin 0 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .60
PJ7 / KWJ7 / TXCAN4 / SCL / TXCAN0 — PORT J I/O Pin 7. . . . . . . . . . . . . . . . . .60
PJ6 / KWJ6 / RXCAN4 / SDA / RXCAN0 — PORT J I/O Pin 6 . . . . . . . . . . . . . . . . .60
PJ[1:0] / KWJ[1:0] — Port J I/O Pins [1:0] . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .60
PK7 / ECS / ROMCTL — Port K I/O Pin 7 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .60
PK[5:0] / XADDR[19:14] — Port K I/O Pins [5:0] . . . . . . . . . . . . . . . . . . . . . . . . . . . .61
PM7 / TXCAN3 / TXCAN4 — Port M I/O Pin 7 . . . . . . . . . . . . . . . . . . . . . . . . . . . . .61
PM6 / RXCAN3 / RXCAN4 — Port M I/O Pin 6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . .61
PM5 / TXCAN2 / TXCAN0 / TXCAN4 / SCK0 — Port M I/O Pin 5. . . . . . . . . . . . . . .61
PM4 / RXCAN2 / RXCAN0 / RXCAN4/ MOSI0 — Port M I/O Pin 4. . . . . . . . . . . . . .61
PM3 / TXCAN1 / TXCAN0 / SS0 — Port M I/O Pin 3 . . . . . . . . . . . . . . . . . . . . . . . .61
PM2 / RXCAN1 / RXCAN0 / MISO0 — Port M I/O Pin 2 . . . . . . . . . . . . . . . . . . . . . .61
PM1 / TXCAN0 / TXB — Port M I/O Pin 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62
PM0 / RXCAN0 / RXB — Port M I/O Pin 0. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62
PP7 / KWP7 / PWM7 / SCK2 — Port P I/O Pin 7 . . . . . . . . . . . . . . . . . . . . . . . . . . .62
PP6 / KWP6 / PWM6 / SS2 — Port P I/O Pin 6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62
PP5 / KWP5 / PWM5 / MOSI2 — Port P I/O Pin 5. . . . . . . . . . . . . . . . . . . . . . . . . . .62
PP4 / KWP4 / PWM4 / MISO2 — Port P I/O Pin 4. . . . . . . . . . . . . . . . . . . . . . . . . . .62
PP3 / KWP3 / PWM3 / SS1 — Port P I/O Pin 3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62
PP2 / KWP2 / PWM2 / SCK1 — Port P I/O Pin 2 . . . . . . . . . . . . . . . . . . . . . . . . . . .63
PP1 / KWP1 / PWM1 / MOSI1 — Port P I/O Pin 1. . . . . . . . . . . . . . . . . . . . . . . . . . .63
PP0 / KWP0 / PWM0 / MISO1 — Port P I/O Pin 0. . . . . . . . . . . . . . . . . . . . . . . . . . .63
PS7 / SS0 — Port S I/O Pin 7 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .63
PS6 / SCK0 — Port S I/O Pin 6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .63
PS5 / MOSI0 — Port S I/O Pin 5 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .63
PS4 / MISO0 — Port S I/O Pin 4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .63
PS3 / TXD1 — Port S I/O Pin 3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .63
PS2 / RXD1 — Port S I/O Pin 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .64
MC9S12DP512 Device Guide V01.25
2.3.56 PS1 / TXD0 — Port S I/O Pin 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .64
2.3.57 PS0 / RXD0 — Port S I/O Pin 0 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .64
2.3.58 PT[7:0] / IOC[7:0] — Port T I/O Pins [7:0] . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .64
2.4
Power Supply Pins . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .64
2.4.1
VDDX,VSSX — Power & Ground Pins for I/O Drivers . . . . . . . . . . . . . . . . . . . . . . . .65
2.4.2
VDDR, VSSR — Power & Ground Pins for I/O Drivers & Internal Voltage Regulator65
2.4.3
VDD1, VDD2, VSS1, VSS2 — Internal Logic Power Supply Pins . . . . . . . . . . . . . . .65
2.4.4
VDDA, VSSA — Power Supply Pins for ATD and VREG . . . . . . . . . . . . . . . . . . . . .65
2.4.5
VRH, VRL — ATD Reference Voltage Input Pins . . . . . . . . . . . . . . . . . . . . . . . . . . .65
2.4.6
VDDPLL, VSSPLL — Power Supply Pins for PLL . . . . . . . . . . . . . . . . . . . . . . . . . . .65
2.4.7
VREGEN — On Chip Voltage Regulator Enable . . . . . . . . . . . . . . . . . . . . . . . . . . . .66
Section 3 System Clock Description
3.1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .67
Section 4 Modes of Operation
4.1
4.2
4.3
4.3.1
4.3.2
4.3.3
4.4
4.4.1
4.4.2
4.4.3
4.4.4
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .69
Chip Configuration Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .69
Security. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .70
Securing the Microcontroller . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .70
Operation of the Secured Microcontroller . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .70
Unsecuring the Microcontroller . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .71
Low Power Modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .71
Stop . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .71
Pseudo Stop. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .71
Wait . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .71
Run. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .72
Section 5 Resets and Interrupts
5.1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .73
5.2
Vectors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .73
5.2.1
Vector Table. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .73
5.3
Effects of Reset . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .74
5.3.1
I/O pins. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .74
5.3.2
Memory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .75
Section 6 HCS12 Core Block Description
7
MC9S12DP512 Device Guide V01.25
6.1
6.1.1
6.2
6.2.1
6.3
6.3.1
6.4
6.5
6.5.1
6.6
CPU12 Block Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .77
Device-specific information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .77
HCS12 Module Mapping Control (MMC) Block Description . . . . . . . . . . . . . . . . . . . . . .77
Device-specific information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .77
HCS12 Multiplexed External Bus Interface (MEBI) Block Description . . . . . . . . . . . . . .77
Device-specific information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .77
HCS12 Interrupt (INT) Block Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .77
HCS12 Background Debug (BDM) Block Description . . . . . . . . . . . . . . . . . . . . . . . . . .78
Device-specific information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .78
HCS12 Breakpoint (BKP) Block Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .78
Section 7 Clock and Reset Generator (CRG) Block Description
7.1
Device-specific information. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .78
Section 8 Oscillator (OSC) Block Description
8.1
Device-specific information. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .78
Section 9 Enhanced Capture Timer (ECT) Block Description
Section 10 Analog to Digital Converter (ATD) Block Description
Section 11 Inter-IC Bus (IIC) Block Description
Section 12 Serial Communications Interface (SCI) Block Description
Section 13 Serial Peripheral Interface (SPI) Block Description
Section 14 J1850 (BDLC) Block Description
Section 15 Pulse Width Modulator (PWM) Block Description
Section 16 Flash EEPROM 512K Block Description
Section 17 EEPROM 4K Block Description
Section 18 RAM Block Description
Section 19 MSCAN Block Description
8
MC9S12DP512 Device Guide V01.25
Section 20 Port Integration Module (PIM) Block Description
Section 21 Voltage Regulator (VREG) Block Description
Section 22 Printed Circuit Board Layout Proposal
Appendix A Electrical Characteristics
A.1 General. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .85
A.1.1
Parameter Classification . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .85
A.1.2
Power Supply . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .85
A.1.3
Pins . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .86
A.1.4
Current Injection. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .87
A.1.5
Absolute Maximum Ratings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .87
A.1.6
ESD Protection and Latch-up Immunity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .88
A.1.7
Operating Conditions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .89
A.1.8
Power Dissipation and Thermal Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . .89
A.1.9
I/O Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .91
A.1.10 Supply Currents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .92
A.2 ATD Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .95
A.2.1
ATD Operating Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .95
A.2.2
Factors influencing accuracy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .95
A.2.3
ATD accuracy. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .97
A.3 NVM, Flash and EEPROM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .99
A.3.1
NVM timing. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .99
A.3.2
NVM Reliability. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .101
A.4 Voltage Regulator. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .103
A.5 Reset, Oscillator and PLL. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .105
A.5.1
Startup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .105
A.5.2
Oscillator . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .106
A.5.3
Phase Locked Loop . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .107
A.6 MSCAN. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .111
A.7 SPI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .113
A.7.1
Master Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .113
A.7.2
Slave Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .115
A.8 External Bus Timing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .117
A.8.1
General Muxed Bus Timing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .117
9
MC9S12DP512 Device Guide V01.25
Appendix B Package Information
B.1
B.2
10
General. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .121
112-pin LQFP package. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .122
MC9S12DP512 Device Guide V01.25
List of Figures
Figure 0-1
Figure 1-1
Figure 1-2
Figure 2-1
Figure 2-2
Figure 2-3
Figure 2-4
Figure 2-5
Figure 3-1
Figure 22-1
Figure 22-2
Figure A-1
Figure A-2
Figure A-3
Figure A-4
Figure A-5
Figure A-6
Figure A-7
Figure A-8
Figure A-9
Figure A-10
Figure B-1
Order Part Number Example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .15
MC9S12DP512 Block Diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .23
MC9S12DP512 Memory Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .26
Pin Assignments in 112-pin LQFP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .52
PLL Loop Filter Connections . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .56
Colpitts Oscillator Connections (PE7=1) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .57
Pierce Oscillator Connections (PE7=0) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .58
External Clock Connections (PE7=0) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .58
Clock Connections. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .67
Recommended PCB Layout for 112LQFP Colpitts Oscillator . . . . . . . . . . . . . . .82
Recommended PCB Layout for 112LQFP Pierce Oscillator . . . . . . . . . . . . . . . .83
ATD Accuracy Definitions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98
Typical Endurance vs Temperature. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
Basic PLL functional diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
Jitter Definitions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Maximum bus clock jitter approximation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
SPI Master Timing (CPHA=0) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
SPI Master Timing (CPHA=1) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
SPI Slave Timing (CPHA=0) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
SPI Slave Timing (CPHA=1) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
General External Bus Timing. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
112-pin LQFP mechanical dimensions (case no. 987) . . . . . . . . . . . . . . . . . . 122
11
MC9S12DP512 Device Guide V01.25
12
MC9S12DP512 Device Guide V01.25
List of Tables
Table 0-1 Derivative Differences . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .15
Table 0-2 Document References . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .17
Table 1-1 Device Memory Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .24
$0000 - $000F
MEBI map 1 of 3 (HCS12 Multiplexed External Bus Interface) . . . . . . . . . .27
$0010 - $0014
MMC map 1 of 4 (HCS12 Module Mapping Control) . . . . . . . . . . . . . . . . . .27
$0015 - $0016
INT map 1 of 2 (HCS12 Interrupt) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .28
$0017 - $0019
Reserved . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .28
$001A - $001B
Device ID Register (Table 1-3) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .28
$001C - $001D MMC map 3 of 4 (HCS12 Module Mapping Control, Table 1-4) . . . . . . . . .28
$001E - $001E
MEBI map 2 of 3 (HCS12 Multiplexed External Bus Interface) . . . . . . . . . .28
$001F - $001F
INT map 2 of 2 (HCS12 Interrupt) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .28
$0020 - $0027
Reserved . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .28
$0028 - $002F
BKP (HCS12 Breakpoint) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .29
$0030 - $0031
MMC map 4 of 4 (HCS12 Module Mapping Control) . . . . . . . . . . . . . . . . . .29
$0032 - $0033
MEBI map 3 of 3 (HCS12 Multiplexed External Bus Interface) . . . . . . . . . .29
$0034 - $003F
CRG (Clock and Reset Generator) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .29
$0040 - $007F
ECT (Enhanced Capture Timer 16 Bit 8 Channels) . . . . . . . . . . . . . . . . . .30
$0080 - $009F
ATD0 (Analog to Digital Converter 10 Bit 8 Channel) . . . . . . . . . . . . . . . . .33
$00A0 - $00C7
PWM (Pulse Width Modulator 8 Bit 8 Channel). . . . . . . . . . . . . . . . . . . . . .34
$00C8 - $00CF SCI0 (Asynchronous Serial Interface) . . . . . . . . . . . . . . . . . . . . . . . . . . . . .36
$00D0 - $00D7 SCI1 (Asynchronous Serial Interface) . . . . . . . . . . . . . . . . . . . . . . . . . . . . .36
$00D8 - $00DF SPI0 (Serial Peripheral Interface) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .36
$00E0 - $00E7
IIC (Inter IC Bus) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .37
$00E8 - $00EF
BDLC (Bytelevel Data Link Controller J1850) . . . . . . . . . . . . . . . . . . . . . . .37
$00F0 - $00F7
SPI1 (Serial Peripheral Interface) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .38
$00F8 - $00FF
SPI2 (Serial Peripheral Interface) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .38
$0100 - $010F
Flash Control Register (fts512k4) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .38
$0110 - $011B
EEPROM Control Register (eets4k) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .39
$011C - $011F
Reserved for RAM Control Register . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .39
$0120 - $013F
ATD1 (Analog to Digital Converter 10 Bit 8 Channel) . . . . . . . . . . . . . . . . .40
$0140 - $017F
CAN0 (Motorola Scalable CAN - MSCAN) . . . . . . . . . . . . . . . . . . . . . . . . .41
Table 1-2 Detailed MSCAN Foreground Receive and Transmit Buffer Layout. . . . . . . . . . .42
$0180 - $01BF
CAN1 (Motorola Scalable CAN - MSCAN) . . . . . . . . . . . . . . . . . . . . . . . . .43
13
MC9S12DP512 Device Guide V01.25
$01C0 - $01FF
CAN2 (Motorola Scalable CAN - MSCAN) . . . . . . . . . . . . . . . . . . . . . . . . .44
$0200 - $023F
CAN3 (Motorola Scalable CAN - MSCAN) . . . . . . . . . . . . . . . . . . . . . . . . .45
$0240 - $027F
PIM (Port Integration Module PIM_9DP256) . . . . . . . . . . . . . . . . . . . . . . . .46
$0280 - $02BF
CAN4 (Motorola Scalable CAN - MSCAN) . . . . . . . . . . . . . . . . . . . . . . . . .48
$02C0 - $03FF
Reserved . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .49
Table 1-3 Assigned Part ID Numbers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .49
Table 1-4 Memory size registers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .49
Table 2-1 Signal Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .53
Table 2-2 MC9S12DP512 Power and Ground Connection Summary . . . . . . . . . . . . . . . . . .64
Table 4-1 Mode Selection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .69
Table 4-2 Clock Selection Based on PE7 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .70
Table 4-3 Voltage Regulator VREGEN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .70
Table 5-1 Interrupt Vector Locations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .73
Table 22-1 Suggested External Component Values . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .81
Table A-1 Absolute Maximum Ratings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .87
Table A-2 ESD and Latch-up Test Conditions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .88
Table A-3 ESD and Latch-up Protection Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . .88
Table A-4 Operating Conditions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .89
Table A-5 Thermal Package Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .91
Table A-6 5V I/O Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .92
Table A-7 Supply Current Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .93
Table A-8 ATD Operating Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .95
Table A-9 ATD Electrical Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .96
Table A-10 ATD Conversion Performance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .97
Table A-11 NVM Timing Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .100
Table A-12 NVM Reliability Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .101
Table A-13 Voltage Regulator Recommended Load Capacitances . . . . . . . . . . . . . . . . . . . .103
Table A-14 Startup Characteristics. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .105
Table A-15 Oscillator Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .106
Table A-16 PLL Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .110
Table A-17 MSCAN Wake-up Pulse Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .111
Table A-18 Measurement Conditions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .113
Table A-19 SPI Master Mode Timing Characteristics. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .114
Table A-20 SPI Slave Mode Timing Characteristics. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .116
Table A-21 Expanded Bus Timing Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .119
14
MC9S12DP512 Device Guide V01.25
Derivative Differences and Document References
Derivative Differences
Table 0-1 shows the availability of peripheral modules on the various derivatives. For details about the
compatibility within the MC9S12D-Family refer also to engineering bulletin EB386.
Table 0-1 Derivative Differences1
Modules
MC9S12DP512
MC9S12DT512
MC9S12DJ512
MC9S12A512
# of CANs
5
3
2
0
CAN0
✓
✓
✓
—
CAN1
✓
✓
—
—
CAN2
✓
—
—
—
CAN3
✓
—
—
—
CAN4
✓
✓
✓
—
J1850/BDLC
✓
—
✓
—
Package
112 LQFP
112 LQFP
112 LQFP
112 LQFP
Package
Code
PV
PV
PV
PV
Mask set
L00M
L00M
L00M
L00M
Temp Options
M, V, C
M, V, C
M, V, C
C
Notes
An errata exists
contact Sales
Office
An errata exists
contact Sales
Office
An errata exists
contact Sales
Office
An errata exists
contact Sales
Office
NOTES:
1. ✓: Available for this device, —: Not available for this device
The following figure provides an ordering number example for the MC9S12D-Family devices.
MC9S12 DP512
C PV
Package Option
Temperature Option
Device Title
Controller Family
Temperature Options
C = -40˚C to 85˚C
V = -40˚C to 105˚C
M = -40˚C to 125˚C
Package Options
FU = 80 QFP
PV = 112 LQFP
Figure 0-1 Order Part Number Example
15
MC9S12DP512 Device Guide V01.25
The following items should be considered when using a derivative (Table 0-1):
•
•
•
16
Registers
–
Do not write or read CAN0 registers (after reset: address range $0140 - $017F), if using a
derivative without CAN0.
–
Do not write or read CAN1registers (after reset: address range $0180 - $01BF), if using a
derivative without CAN1.
–
Do not write or read CAN2 registers (after reset: address range $01C0 - $01FF), if using a
derivative without CAN2.
–
Do not write or read CAN3 registers (after reset: address range $0200 - $023F), if using a
derivative without CAN3.
–
Do not write or read CAN4 registers (after reset: address range $0280 - $02BF), if using a
derivative without CAN4.
–
Do not write or read BDLC registers (after reset: address range $00E8 - $00EF), if using a
derivative without BDLC.
Interrupts
–
Fill the four CAN0 interrupt vectors ($FFB0 - $FFB7) according to your coding policies for
unused interrupts, if using a derivative without CAN0.
–
Fill the four CAN1 interrupt vectors ($FFA8 - $FFAF) according to your coding policies for
unused interrupts, if using a derivative without CAN1.
–
Fill the four CAN2 interrupt vectors ($FFA0 - $FFA7) according to your coding policies for
unused interrupts, if using a derivative without CAN2.
–
Fill the four CAN3 interrupt vectors ($FF98 - $FF9F) according to your coding policies for
unused interrupts, if using a derivative without CAN3.
–
Fill the four CAN4 interrupt vectors ($FF90 - $FF97) according to your coding policies for
unused interrupts, if using a derivative without CAN4.
–
Fill the BDLC interrupt vector ($FFC2, $FFC3) according to your coding policies for unused
interrupts, if using a derivative without BDLC.
Ports
–
The CAN0 pin functionality (TXCAN0, RXCAN0) is not available on port PJ7, PJ6, PM5,
PM4, PM3, PM2, PM1 and PM0, if using a derivative without CAN0.
–
The CAN1 pin functionality (TXCAN1, RXCAN1) is not available on port PM3 and PM2, if
using a derivative without CAN1.
–
The CAN2 pin functionality (TXCAN2, RXCAN2) is not available on port PM5 and PM4, if
using a derivative without CAN2.
–
The CAN3 pin functionality (TXCAN3, RXCAN3) is not available on port PM7 and PM6, if
using a derivative without CAN3.
MC9S12DP512 Device Guide V01.25
–
The CAN4 pin functionality (TXCAN4, RXCAN4) is not available on port PJ7, PJ6, PM7,
PM6, PM5 and PM4, if using a derivative without CAN0.
–
The BDLC pin functionality (TXB, RXB) is not available on port PM1 and PM0, if using a
derivative without BDLC.
–
Do not write MODRR1 and MODRR0 bits of Module Routing Register (PIM_9DP256 Block
Guide), if using a derivative without CAN0.
–
Do not write MODRR3 and MODRR2 bits of Module Routing Register (PIM_9DP256 Block
Guide), if using a derivative without CAN4.
Document References
The Device Guide provides information about the MC9S12DP512 device made up of standard HCS12
blocks and the HCS12 processor core.
This document is part of the customer documentation. A complete set of device manuals also includes the
individual Block Guides of the implemented modules. In an effort to reduce redundancy, all module
specific information is located only in the respective Block Guide. If applicable, special implementation
details of the module are given in the block description sections of this document.
See Table 0-2 for names and versions of the referenced documents throughout the Device Guide.
Table 0-2 Document References
Block Guide
Version
Document Order Number
HCS12 CPU Reference Manual
V02
S12CPUV2/D
HCS12 Module Mapping Control (MMC) Block Guide
V04
S12MMCV4/D
HCS12 Multiplexed External Bus Interface (MEBI) Block Guide
V03
S12MEBIV3/D
HCS12 Interrupt (INT) Block Guide
V01
S12INTV1/D
HCS12 Background Debug (BDM) Block Guide
V04
S12BDMV4/D
HCS12 Breakpoint (BKP) Block Guide
V01
S12BKPV1/D
Clock and Reset Generator (CRG) Block Guide
V04
S12CRGV4/D
Enhanced Capture Timer 16 Bit 8 Channel (ECT_16B8C) Block Guide
V01
S12ECT16B8V1/D
Analog to Digital Converter 10 Bit 8 Channel (ATD_10B8C) Block Guide
V02
S12ATD10B8CV2/D
Inter IC Bus (IIC) Block Guide
V02
S12IICV2/D
Asynchronous Serial Interface (SCI) Block Guide
V02
S12SCIV2/D
Serial Peripheral Interface (SPI) Block Guide
V03
S12SPIV3/D
Pulse Width Modulator 8 Bit 8 Channel (PWM_8B8C) Block Guide
V01
S12PWM8B8CV1/D
512K Byte Flash (FTS512K4) Block Guide
V01
S12FTS512K4V1/D
4K Byte EEPROM (EETS4K) Block Guide
V02
S12EETS4KV2/D
Byte Level Data Link Controller -J1850 (BDLC) Block Guide
V01
S12BDLCV1/D
Motorola Scalable CAN (MSCAN) Block Guide
V02
S12MSCANV2/D
Voltage Regulator (VREG) Block Guide
V01
S12VREGV1/D
Port Integration Module (PIM_9DP256) Block Guide1
V03
S12DP256PIMV3/D
Oscillator (OSC) Block Guide
V02
S12OSCV2/D
17
MC9S12DP512 Device Guide V01.25
NOTES:
1. Reused due to functional equivalence.
18
MC9S12DP512 Device Guide V01.25
Section 1 Introduction
1.1 Overview
The MC9S12DP512 microcontroller unit (MCU) is a 16-bit device composed of standard on-chip
peripherals including a 16-bit central processing unit (HCS12 CPU), 512K bytes of Flash EEPROM, 14K
bytes of RAM, 4K bytes of EEPROM, two asynchronous serial communications interfaces (SCI), three
serial peripheral interfaces (SPI), an 8-channel IC/OC enhanced capture timer, two 8-channel, 10-bit
analog-to-digital converters (ADC), an 8-channel pulse-width modulator (PWM), a digital Byte Data Link
Controller (BDLC), 29 discrete digital I/O channels (Port A, Port B, Port K and Port E), 20 discrete digital
I/O lines with interrupt and wake up capability, five CAN 2.0 A, B software compatible modules
(MSCAN12), and an Inter-IC Bus. The MC9S12DP512 has full 16-bit data paths throughout. However,
the external bus can operate in an 8-bit narrow mode so single 8-bit wide memory can be interfaced for
lower cost systems. The inclusion of a PLL circuit allows power consumption and performance to be
adjusted to suit operational requirements.
1.2 Features
•
HCS12 Core
–
16-bit HCS12 CPU
i. Upward compatible with M68HC11 instruction set
ii. Interrupt stacking and programmer’s model identical to M68HC11
iii. Instruction queue
iv. Enhanced indexed addressing
•
•
–
MEBI (Multiplexed External Bus Interface)
–
MMC (Module Mapping Control)
–
INT (Interrupt control)
–
BKP (Breakpoints)
–
BDM (Background Debug Mode)
CRG (Clock and Reset Generation)
–
Low current Colpitts oscillator or
–
Pierce oscillator
–
PLL
–
COP watchdog
–
Real Time Interrupt
–
Clock Monitor
8-bit and 4-bit ports with interrupt functionality
19
MC9S12DP512 Device Guide V01.25
•
•
•
•
•
•
•
–
Digital filtering
–
Programmable rising or falling edge trigger
Memory
–
512K Flash EEPROM
–
4K byte EEPROM
–
14K byte RAM
Two 8-channel Analog-to-Digital Converters
–
10-bit resolution
–
External conversion trigger capability
Five 1M bit per second, CAN 2.0 A, B software compatible modules
–
Five receive and three transmit buffers
–
Flexible identifier filter programmable as 2 x 32 bit, 4 x 16 bit or 8 x 8 bit
–
Four separate interrupt channels for Rx, Tx, error and wake-up
–
Low-pass filter wake-up function
–
Loop-back for self test operation
Enhanced Capture Timer
–
16-bit main counter with 7-bit prescaler
–
8 programmable input capture or output compare channels
–
Four 8-bit or two 16-bit pulse accumulators
8 PWM channels
–
Programmable period and duty cycle
–
8-bit 8-channel or 16-bit 4-channel
–
Separate control for each pulse width and duty cycle
–
Center-aligned or left-aligned outputs
–
Programmable clock select logic with a wide range of frequencies
–
Fast emergency shutdown input
–
Usable as interrupt inputs
Serial interfaces
–
Two asynchronous Serial Communications Interfaces (SCI)
–
Three Synchronous Serial Peripheral Interface (SPI)
Byte Data Link Controller (BDLC)
–
20
SAE J1850 Class B Data Communications Network Interface Compatible and ISO Compatible
for Low-Speed (<125 Kbps) Serial Data Communications in Automotive Applications
MC9S12DP512 Device Guide V01.25
•
•
Inter-IC Bus (IIC)
–
Compatible with I2C Bus standard
–
Multi-master operation
–
Software programmable for one of 256 different serial clock frequencies
112-Pin LQFP package
–
I/O lines with 5V input and drive capability
–
5V A/D converter inputs
–
Operation at 50MHz equivalent to 25MHz Bus Speed over -40˚C <= TA <= 125˚C
–
Development support
–
Single-wire background debug™ mode (BDM)
–
On-chip hardware breakpoints
1.3 Modes of Operation
User modes
•
•
Normal and Emulation Operating Modes
–
Normal Single-Chip Mode
–
Normal Expanded Wide Mode
–
Normal Expanded Narrow Mode
–
Emulation Expanded Wide Mode
–
Emulation Expanded Narrow Mode
Special Operating Modes
–
Special Single-Chip Mode with active Background Debug Mode
–
Special Test Mode (Motorola use only)
–
Special Peripheral Mode (Motorola use only)
Low power modes
•
Stop Mode
•
Pseudo Stop Mode
•
Wait Mode
21
MC9S12DP512 Device Guide V01.25
1.4 Block Diagram
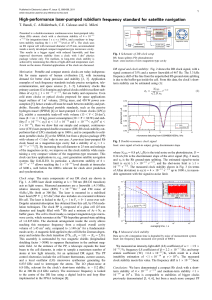
Figure 1-1 shows a block diagram of the MC9S12DP512 device.
22
MC9S12DP512 Device Guide V01.25
Multiplexed
Narrow Bus
PTB
DATA7
DATA6
DATA5
DATA4
DATA3
DATA2
DATA1
DATA0
Internal Logic 2.5V
VDD1,2
VSS1,2
PLL 2.5V
VDDPLL
VSSPLL
ADDR7
ADDR6
ADDR5
ADDR4
ADDR3
ADDR2
ADDR1
ADDR0
PB7
PB6
PB5
PB4
PB3
PB2
PB1
PB0
DDRB
PTA
DATA7
DATA6
DATA5
DATA4
DATA3
DATA2
DATA1
DATA0
Multiplexed
Wide Bus
DDRA
DATA15 ADDR15 PA7
DATA14 ADDR14 PA6
DATA13 ADDR13 PA5
DATA12 ADDR12 PA4
DATA11 ADDR11 PA3
DATA10 ADDR10 PA2
DATA9
ADDR9 PA1
DATA8
ADDR8 PA0
SPI0
BDLC
(J1850)
RXB
TXB
RXCAN
CAN0
TXCAN
RXCAN
CAN1
TXCAN
RXCAN
CAN2
TXCAN
RXCAN
CAN3
TXCAN
RXCAN
CAN4
TXCAN
IIC
SDA
SCL
KWJ0
KWJ1
KWJ6
KWJ7
PWM
PWM0
PWM1
PWM2
PWM3
PWM4
PWM5
PWM6
PWM7
KWP0
KWP1
KWP2
KWP3
KWP4
KWP5
KWP6
KWP7
MISO
MOSI
SCK
SS
MISO
MOSI
SCK
SS
KWH0
KWH1
KWH2
KWH3
KWH4
KWH5
KWH6
KWH7
I/O Driver 5V
VDDX
VSSX
A/D Converter 5V &
Voltage Regulator Reference
VDDA
VSSA
Voltage Regulator 5V & I/O
VDDR
VSSR
MISO
MOSI
SCK
SS
SPI1
SPI2
AD1
PTT
Multiplexed Address/Data Bus
PTS
SCI1
PS0
PS1
PS2
PS3
PS4
PS5
PS6
PS7
PTM
RXD
TXD
RXD
TXD
SCI0
TEST
PT0
PT1
PT2
PT3
PT4
PT5
PT6
PT7
PM0
PM1
PM2
PM3
PM4
PM5
PM6
PM7
PTJ
Enhanced Capture
Timer
IOC0
IOC1
IOC2
IOC3
IOC4
IOC5
IOC6
IOC7
PJ0
PJ1
PJ6
PJ7
PTP
XIRQ
IRQ
System
R/W
Integration
LSTRB
Module
ECLK
(SIM)
MODA
MODB
NOACC/XCLKS
DDRK
Periodic Interrupt
COP Watchdog
Clock Monitor
Breakpoints
PK0
PK1
PK2
PK3
PK4
PK5
PK7
PP0
PP1
PP2
PP3
PP4
PP5
PP6
PP7
XADDR14
XADDR15
XADDR16
XADDR17
XADDR18
XADDR19
ECS
PH0
PH1
PH2
PTH
PTE
PE0
PE1
PE2
PE3
PE4
PE5
PE6
PE7
Clock and
Reset
Generation
Module
PIX0
PIX1
PIX2
PIX3
PIX4
PIX5
ECS
DDRT
PLL
PPAGE
DDRS
XFC
VDDPLL
VSSPLL
EXTAL
XTAL
RESET
CPU12
PAD08
PAD09
PAD10
PAD11
PAD12
PAD13
PAD14
PAD15
AN08
AN09
AN10
AN11
AN12
AN13
AN14
AN15
DDRM
Single-wire Background
Debug Module
DDRE
BKGD
Voltage Regulator
PAD00
PAD01
PAD02
PAD03
PAD04
PAD05
PAD06
PAD07
VRH
VRL
VDDA
VSSA
DDRJ
VDDR
VSSR
VREGEN
VDD1,2
VSS1,2
AN00
AN01
AN02
AN03
AN04
AN05
AN06
AN07
VRH
VRL
VDDA
VSSA
DDRP
4K Byte EEPROM
ATD1
DDRH
14K Byte RAM
VRH
VRL
VDDA
VSSA
Module to Port Routing
ATD0
AD0
512K Byte Flash EEPROM
PTK
Figure 1-1 MC9S12DP512 Block Diagram
PH3
PH4
PH5
PH6
PH7
23
MC9S12DP512 Device Guide V01.25
1.5 Device Memory Map
Table 1-1 and Figure 1-2 show the device memory map of the MC9S12DP512 after reset. Note that after
reset the bottom 1k of the EEPROM ($0000 - $03FF) are hidden by the register space
Table 1-1 Device Memory Map
Address
Module
$0000 - $000F
HCS12 Multiplexed External Bus Interface
16
$0010 - $0014
HCS12 Module Mapping Control
5
$0015 - $0016
HCS12 Interrupt
2
$0017 - $0019
Reserved
3
$001A - $001B Device ID register (PARTID)
2
$001C - $001D HCS12 Module Mapping Control
2
$001E
HCS12 Multiplexed External Bus Interface
1
$001F
HCS12 Interrupt
1
$0020 - $0027
Reserved
8
$0028 - $002F
HCS12 Breakpoint
8
$0030 - $0031
HCS12 Module Mapping Control
2
$0032 - $0033
HCS12 Multiplexed External Bus Interface
2
$0034 - $003F
Clock and Reset Generator (PLL, RTI, COP)
12
$0040 - $007F
Enhanced Capture Timer 16-bit 8 channels
64
$0080 - $009F
Analog to Digital Converter 10-bit 8 channels (ATD0)
32
$00A0 - $00C7 Pulse Width Modulator 8-bit 8 channels (PWM)
40
$00C8 - $00CF Serial Communications Interface 0 (SCI0)
8
$00D0 - $00D7 Serial Communications Interface 0 (SCI1)
8
$00D8 - $00DF Serial Peripheral Interface (SPI0)
8
$00E0 - $00E7 Inter IC Bus
8
$00E8 - $00EF Byte Data Link Controller (BDLC)
8
$00F0 - $00F7
Serial Peripheral Interface (SPI1)
8
$00F8 - $00FF
Serial Peripheral Interface (SPI2)
8
$0100- $010F
Flash Control Register
16
$0110 - $011B
EEPROM Control Register
12
$011C - $011F Reserved
4
$0120 - $013F
Analog to Digital Converter 10-bit 8 channels (ATD1)
32
$0140 - $017F
Motorola Scalable Can (CAN0)
64
$0180 - $01BF
Motorola Scalable Can (CAN1)
64
$01C0 - $01FF Motorola Scalable Can (CAN2)
64
$0200 - $023F
Motorola Scalable Can (CAN3)
64
$0240 - $027F
Port Integration Module (PIM)
64
$0280 - $02BF
Motorola Scalable Can (CAN4)
$02C0 - $03FF Reserved
24
Size
(Bytes)
64
320
$0000 - $0FFF
EEPROM array
4096
$0800 - $3FFF
RAM array
14336
$4000 - $7FFF
Fixed Flash EEPROM array
incl. 1K, 2K, 4K or 8K Protected Sector at start
16384
MC9S12DP512 Device Guide V01.25
Table 1-1 Device Memory Map
Module
Size
(Bytes)
$8000 - $BFFF Flash EEPROM Page Window
16384
Fixed Flash EEPROM array
$C000 - $FFFF incl. 2K, 4K, 8K or 16K Protected Sector at end
and 256 bytes of Vector Space at $FF80 - $FFFF
16384
Address
25
MC9S12DP512 Device Guide V01.25
Figure 1-2 MC9S12DP512 Memory Map
$0000
$0000
$0400
REGISTERS
(Mappable to any 2k Block
within the first 32K)
$03FF
$0800
$0000
4K Bytes EEPROM
(Mappable to any 4K Block)
$0FFF
$0800
$4000
$3FFF
$4000
14K Bytes RAM
(Mappable to any 16K
and alignable to top or
bottom)
16K Fixed Flash
Page $3E = 62
(This is dependant on the
state of the ROMHM bit)
$7FFF
$8000
$8000
16K Page Window
32 x 16K Flash EEPROM
pages
EXTERN
$BFFF
$C000
$C000
16K Fixed Flash
Page $3F = 63
$FFFF
$FF00
BDM
(if active)
$FF00
VECTORS
VECTORS
VECTORS
EXPANDED*
NORMAL
SINGLE CHIP
SPECIAL
SINGLE CHIP
$FFFF
$FFFF
* Assuming that a ‘0’ was driven onto port K bit 7 during MCU is reset into normal expanded wide or narrow mode.
26
MC9S12DP512 Device Guide V01.25
1.5.1 Detailed Register Map
$0000 - $000F
Address
Name
$0000
PORTA
$0001
PORTB
$0002
DDRA
$0003
DDRB
$0004 $0007
Reserved
$0008
PORTE
$0009
DDRE
$000A
PEAR
$000B
MODE
$000C
PUCR
$000D
RDRIV
$000E
EBICTL
$000F
Reserved
$0010 - $0014
Address
Name
$0010
INITRM
$0011
INITRG
$0012
INITEE
$0013
MISC
$0014
Reserved
MEBI map 1 of 3 (HCS12 Multiplexed External Bus Interface)
Bit 7
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
0
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
NOACCE
Write:
Read:
MODC
Write:
Read:
PUPKE
Write:
Read:
RDPK
Write:
Read:
0
Write:
Read:
0
Write:
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
0
0
0
0
0
0
0
6
5
4
3
2
Bit 1
Bit 0
6
5
4
3
Bit 2
0
0
PIPOE
NECLK
LSTRE
RDWE
0
0
EMK
EME
PUPBE
PUPAE
RDPB
RDPA
0
MODB
MODA
0
0
0
0
0
0
0
0
0
IVIS
0
0
0
0
0
0
0
0
0
0
0
0
0
PUPEE
RDPE
ESTR
0
MMC map 1 of 4 (HCS12 Module Mapping Control)
Bit 7
Read:
RAM15
Write:
Read:
0
Write:
Read:
EE15
Write:
Read:
0
Write:
Read:
0
Write:
Bit 6
Bit 5
Bit 4
Bit 3
RAM14
RAM13
RAM12
RAM11
REG14
REG13
REG12
REG11
EE14
EE13
EE12
EE11
0
0
0
0
0
0
Bit 2
0
Bit 1
0
0
0
0
0
Bit 0
RAMHAL
0
EEON
EXSTR1 EXSTR0 ROMHM ROMON
0
0
0
0
27
MC9S12DP512 Device Guide V01.25
$0015 - $0016
Address
INT map 1 of 2 (HCS12 Interrupt)
Name
$0015
ITCR
$0016
ITEST
Read:
Write:
Read:
Write:
$0017 - $0019
Address
$0017$0019
Read:
Write:
$001A - $001B
Address
PARTIDH
$001B
PARTIDL
Read:
Write:
Read:
Write:
$001C - $001D
Address
Name
$001C
MEMSIZ0
$001D
MEMSIZ1
$001E
$001F
Read:
Write:
Read:
Write:
$0020 - $0027
Address
$0020 $0027
28
Bit 0
WRINT
ADR3
ADR2
ADR1
ADR0
INTE
INTC
INTA
INT8
INT6
INT4
INT2
INT0
Bit 7
0
Bit 6
0
Bit 5
0
Bit 4
0
Bit 3
0
Bit 2
0
Bit 1
0
Bit 0
0
Bit 7
ID15
Bit 6
ID14
Bit 5
ID13
Bit 4
ID12
Bit 3
ID11
Bit 2
ID10
Bit 1
ID9
Bit 0
ID8
ID7
ID6
ID5
ID4
ID3
ID2
ID1
ID0
Bit 3
0
0
Bit 2
Bit 1
Bit 0
ram_sw2 ram_sw1 ram_sw0
0
pag_sw1 pag_sw0
Bit 7
Bit 6
IRQE
IRQEN
Bit 5
0
Bit 4
0
Bit 3
0
Bit 2
0
Bit 1
0
Bit 0
0
Bit 0
0
Bit 7
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
PSEL7
PSEL6
PSEL5
PSEL4
PSEL3
PSEL2
PSEL1
Bit 5
0
Bit 4
0
Bit 3
0
Bit 2
0
Bit 1
0
Reserved
Name
Reserved
Bit 1
INT map 2 of 2 (HCS12 Interrupt)
Name
HPRIO
Bit 2
MEBI map 2 of 3 (HCS12 Multiplexed External Bus Interface)
$001F - $001F
Address
Bit 3
Bit 7
Bit 6
Bit 5
Bit 4
Read: reg_sw0
0
eep_sw1 eep_sw0
Write:
Read: rom_sw1 rom_sw0
0
0
Write:
Name
INTCR
Bit 4
MMC map 3 of 4 (HCS12 Module Mapping Control, Table 1-4)
$001E - $001E
Address
Bit 5
0
Device ID Register (Table 1-3)
Name
$001A
Bit 6
0
Reserved
Name
Reserved
Bit 7
0
Read:
Write:
Bit 7
0
Bit 6
0
Bit 0
0
MC9S12DP512 Device Guide V01.25
$0028 - $002F
Address
Name
$0028
BKPCT0
$0029
BKPCT1
$002A
BKP0X
$002B
BKP0H
$002C
BKP0L
$002D
BKP1X
$002E
BKP1H
$002F
BKP1L
BKP (HCS12 Breakpoint)
Bit 7
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
Read:
0
0
0
0
BKEN
BKFULL BKBDM BKTAG
Write:
Read:
BK0MBH BK0MBL BK1MBH BK1MBL BK0RWE BK0RW BK1RWE BK1RW
Write:
Read:
0
0
BK0V5
BK0V4
BK0V3
BK0V2
BK0V1
BK0V0
Write:
Read:
Bit 15
14
13
12
11
10
9
Bit 8
Write:
Read:
Bit 7
6
5
4
3
2
1
Bit 0
Write:
Read:
0
0
BK1V5
BK1V4
BK1V3
BK1V2
BK1V1
BK1V0
Write:
Read:
Bit 15
14
13
12
11
10
9
Bit 8
Write:
Read:
Bit 7
6
5
4
3
2
1
Bit 0
Write:
$0030 - $0031
Address
MMC map 4 of 4 (HCS12 Module Mapping Control)
Name
$0030
PPAGE
$0031
Reserved
Read:
Write:
Read:
Write:
$0032 - $0033
Address
PORTK
$0033
DDRK
Read:
Write:
Read:
Write:
$0034 - $003F
Address
SYNR
$0035
REFDV
$0036
CTFLG
Test Only
$0037
CRGFLG
$0038
CRGINT
0
0
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
PIX5
PIX4
PIX3
PIX2
PIX1
PIX0
0
0
0
0
0
0
Bit 7
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
Bit 7
6
5
4
3
2
1
Bit 0
Bit 7
6
5
4
3
2
1
Bit 0
CRG (Clock and Reset Generator)
Name
$0034
Bit 6
0
MEBI map 3 of 3 (HCS12 Multiplexed External Bus Interface)
Name
$0032
Bit 7
0
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Bit 7
0
Bit 6
0
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
SYN5
SYN4
SYN3
SYN2
SYN1
SYN0
0
0
0
0
TOUT7
TOUT6
TOUT5
TOUT4
RTIF
PROF
RTIE
0
0
0
LOCKIF
LOCKIE
REFDV3 REFDV2 REFDV1 REFDV0
TOUT3
TOUT2
LOCK
TRACK
0
0
TOUT1
SCMIF
SCMIE
TOUT0
SCM
0
29
MC9S12DP512 Device Guide V01.25
$0034 - $003F
Address
Name
$0039
CLKSEL
$003A
PLLCTL
$003B
RTICTL
$003C
COPCTL
$003D
$003E
$003F
FORBYP
Test Only
CTCTL
Test Only
ARMCOP
CRG (Clock and Reset Generator)
Bit 7
Bit 6
Bit 5
Bit 4
Read:
PLLSEL
PSTP
SYSWAI ROAWAI
Write:
Read:
CME
PLLON
AUTO
ACQ
Write:
Read:
0
RTR6
RTR5
RTR4
Write:
Read:
0
0
WCOP
RSBCK
Write:
Read:
0
RTIBYP COPBYP
PLLBYP
Write:
Read: TCTL7
TCTL6
TCTL5
TCTL4
Write:
Read:
0
0
0
0
Write:
Bit 7
6
5
4
$0040 - $007F
Address
30
TIOS
$0041
CFORC
$0042
OC7M
$0043
OC7D
$0044
TCNT (hi)
$0045
TCNT (lo)
$0046
TSCR1
$0047
TTOV
$0048
TCTL1
$0049
TCTL2
$004A
TCTL3
$004B
TCTL4
$004C
TIE
$004D
TSCR2
$004E
TFLG1
Bit 2
Bit 1
Bit 0
PLLWAI
CWAI
RTIWAI
COPWAI
PRE
PCE
SCME
RTR2
RTR1
RTR0
CR2
CR1
CR0
0
RTR3
0
0
0
TCLT3
TCTL2
TCTL1
TCTL0
0
3
0
2
0
1
0
Bit 0
FCM
0
ECT (Enhanced Capture Timer 16 Bit 8 Channels)
Name
$0040
Bit 3
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Bit 7
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
IOS7
IOS6
IOS5
IOS4
IOS3
IOS2
IOS1
IOS0
0
FOC7
0
FOC6
0
FOC5
0
FOC4
0
FOC3
0
FOC2
0
FOC1
0
FOC0
OC7M7
OC7M6
OC7M5
OC7M4
OC7M3
OC7M2
OC7M1
OC7M0
OC7D7
OC7D6
OC7D5
OC7D4
OC7D3
OC7D2
OC7D1
OC7D0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
TEN
TSWAI
TSFRZ
TFFCA
0
0
0
0
TOV7
TOV6
TOV5
TOV4
TOV3
TOV2
TOV1
TOV0
OM7
OL7
OM6
OL6
OM5
OL5
OM4
OL4
OM3
OL3
OM2
OL2
OM1
OL1
OM0
OL0
EDG7B
EDG7A
EDG6B
EDG6A
EDG5B
EDG5A
EDG4B
EDG4A
EDG3B
EDG3A
EDG2B
EDG2A
EDG1B
EDG1A
EDG0B
EDG0A
C7I
C6I
C5I
C4I
C3I
C2I
C1I
C0I
0
0
0
TCRE
PR2
PR1
PR0
C6F
C5F
C4F
C3F
C2F
C1F
C0F
TOI
C7F
MC9S12DP512 Device Guide V01.25
$0040 - $007F
Address
ECT (Enhanced Capture Timer 16 Bit 8 Channels)
Name
$004F
TFLG2
$0050
TC0 (hi)
$0051
TC0 (lo)
$0052
TC1 (hi)
$0053
TC1 (lo)
$0054
TC2 (hi)
$0055
TC2 (lo)
$0056
TC3 (hi)
$0057
TC3 (lo)
$0058
TC4 (hi)
$0059
TC4 (lo)
$005A
TC5 (hi)
$005B
TC5 (lo)
$005C
TC6 (hi)
$005D
TC6 (lo)
$005E
TC7 (hi)
$005F
TC7 (lo)
$0060
PACTL
$0061
PAFLG
$0062
PACN3 (hi)
$0063
PACN2 (lo)
$0064
PACN1 (hi)
$0065
PACN0 (lo)
$0066
MCCTL
$0067
MCFLG
Bit 7
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Bit 6
0
Bit 5
0
Bit 4
0
Bit 3
0
Bit 2
0
Bit 1
0
Bit 0
0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
PAEN
PAMOD
PEDGE
CLK1
CLK0
PAOVI
PAI
0
0
0
0
0
0
PAOVF
PAIF
Bit 7
6
5
4
3
2
1
Bit 0
Bit 7
6
5
4
3
2
1
Bit 0
Bit 7
6
5
4
3
2
1
Bit 0
Bit 7
6
5
4
3
2
1
Bit 0
MCZI
MODMC
RDMCL
MCPR1
MCPR0
0
0
FLMC
POLF3
MCEN
0
0
ICLAT
0
POLF2
POLF1
POLF0
TOF
0
MCZF
31
MC9S12DP512 Device Guide V01.25
$0040 - $007F
32
Address
Name
$0068
ICPAR
$0069
DLYCT
$006A
ICOVW
$006B
ICSYS
$006C
Reserved
$006D
TIMTST
Test Only
$006E $006F
Reserved
$0070
PBCTL
$0071
PBFLG
$0072
PA3H
$0073
PA2H
$0074
PA1H
$0075
PA0H
$0076
MCCNT (hi)
$0077
MCCNT (lo)
$0078
TC0H (hi)
$0079
TC0H (lo)
$007A
TC1H (hi)
$007B
TC1H (lo)
$007C
TC2H (hi)
$007D
TC2H (lo)
$007E
TC3H (hi)
$007F
TC3H (lo)
ECT (Enhanced Capture Timer 16 Bit 8 Channels)
Bit 7
Read:
0
Write:
Read:
0
Write:
Read:
NOVW7
Write:
Read:
SH37
Write:
Read:
Write:
Read:
0
Write:
Read:
Write:
Read:
0
Write:
Read:
0
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 15
Write:
Read:
Bit 7
Write:
Read: Bit 15
Write:
Read:
Bit 7
Write:
Read: Bit 15
Write:
Read:
Bit 7
Write:
Read: Bit 15
Write:
Read:
Bit 7
Write:
Read: Bit 15
Write:
Read:
Bit 7
Write:
Bit 6
0
Bit 5
0
Bit 4
0
Bit 3
Bit 2
Bit 1
Bit 0
PA3EN
PA2EN
PA1EN
PA0EN
0
0
0
0
0
DLY1
DLY0
NOVW6
NOVW5
NOVW4
NOVW3
NOVW2
NOVW1
NOVW0
SH26
SH15
SH04
TFMOD
PACMX
BUFEN
LATQ
0
0
0
0
0
0
0
0
0
0
0
0
0
0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
14
13
12
11
10
9
Bit 8
6
5
4
3
2
1
Bit 0
14
13
12
11
10
9
Bit 8
6
5
4
3
2
1
Bit 0
14
13
12
11
10
9
Bit 8
6
5
4
3
2
1
Bit 0
14
13
12
11
10
9
Bit 8
6
5
4
3
2
1
Bit 0
14
13
12
11
10
9
Bit 8
6
5
4
3
2
1
Bit 0
PBEN
TCBYP
PBOVI
PBOVF
0
0
0
MC9S12DP512 Device Guide V01.25
$0080 - $009F
Address
Name
$0080
ATD0CTL0
$0081
ATD0CTL1
$0082
ATD0CTL2
$0083
ATD0CTL3
$0084
ATD0CTL4
$0085
ATD0CTL5
$0086
ATD0STAT0
$0087
Reserved
$0088
ATD0TEST0
$0089
ATD0TEST1
$008A
Reserved
$008B
ATD0STAT1
$008C
Reserved
$008D
ATD0DIEN
$008E
Reserved
$008F
PORTAD0
$0090
ATD0DR0H
$0091
ATD0DR0L
$0092
ATD0DR1H
$0093
ATD0DR1L
$0094
ATD0DR2H
$0095
ATD0DR2L
$0096
ATD0DR3H
$0097
ATD0DR3L
$0098
ATD0DR4H
ATD0 (Analog to Digital Converter 10 Bit 8 Channel)
Bit 7
Read:
0
Write:
Read:
0
Write:
Read:
ADPU
Write:
Read:
0
Write:
Read:
SRES8
Write:
Read:
DJM
Write:
Read:
SCF
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read: CCF7
Write:
Read:
0
Write:
Read:
Bit 7
Write:
Read:
0
Write:
Read:
Bit 7
Write:
Read: Bit 15
Write:
Read:
Bit 7
Write:
Read: Bit 15
Write:
Read:
Bit 7
Write:
Read: Bit 15
Write:
Read:
Bit 7
Write:
Read: Bit 15
Write:
Read:
Bit 7
Write:
Read: Bit 15
Write:
Bit 6
0
Bit 5
0
Bit 4
0
Bit 3
0
Bit 2
0
Bit 1
0
Bit 0
0
0
0
0
0
0
0
0
AFFC
AWAI
ETRIG
ASCIE
S8C
S4C
S2C
S1C
FIFO
FRZ1
FRZ0
SMP1
SMP0
PRS4
PRS3
PRS2
PRS1
PRS0
DSGN
SCAN
MULT
CC
CB
CA
ETORF
FIFOR
0
CC2
CC1
CC0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
CCF6
CCF5
CCF4
CCF3
CCF2
CCF1
CCF0
0
0
0
0
0
0
0
6
5
4
3
2
1
Bit 0
0
0
0
0
0
0
0
6
5
4
3
2
1
Bit 0
14
13
12
11
10
9
Bit 8
6
5
4
3
2
1
Bit 0
14
13
12
11
10
9
Bit 8
6
5
4
3
2
1
Bit 0
14
13
12
11
10
9
Bit 8
6
5
4
3
2
1
Bit 0
14
13
12
11
10
9
Bit 8
6
5
4
3
2
1
Bit 0
14
13
12
11
10
9
Bit 8
0
ETRIGLE ETRIGP
0
ASCIF
SC
33
MC9S12DP512 Device Guide V01.25
$0080 - $009F
Address
Name
$0099
ATD0DR4L
$009A
ATD0DR5H
$009B
ATD0DR5L
$009C
ATD0DR6H
$009D
ATD0DR6L
$009E
ATD0DR7H
$009F
ATD0DR7L
$00A0 - $00C7
Address
$00A0
$00A1
$00A2
$00A3
$00A4
$00A5
$00A6
$00A7
$00A8
$00A9
$00AA
$00AB
$00AC
$00AD
$00AE
34
ATD0 (Analog to Digital Converter 10 Bit 8 Channel)
Name
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Bit 7
Bit 7
Bit 6
6
Bit 5
5
Bit 4
4
Bit 3
3
Bit 2
2
Bit 1
1
Bit 0
Bit 0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
PWM (Pulse Width Modulator 8 Bit 8 Channel)
Bit 7
Read:
PWME
PWME7
Write:
Read:
PWMPOL
PPOL7
Write:
Read:
PWMCLK
PCLK7
Write:
Read:
0
PWMPRCLK
Write:
Read:
PWMCAE
CAE7
Write:
Read:
PWMCTL
CON67
Write:
Read:
0
PWMTST
Test Only
Write:
Read:
0
PWMPRSC
Write:
Read:
PWMSCLA
Bit 7
Write:
Read:
PWMSCLB
Bit 7
Write:
Read:
0
PWMSCNTA
Write:
Read:
0
PWMSCNTB
Write:
Read:
Bit 7
PWMCNT0
Write:
0
Read:
Bit 7
PWMCNT1
Write:
0
Read:
Bit 7
PWMCNT2
Write:
0
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
PWME6
PWME5
PWME4
PWME3
PWME2
PWME1
PWME0
PPOL6
PPOL5
PPOL4
PPOL3
PPOL2
PPOL1
PPOL0
PCLK6
PCLK5
PCLK4
PCLK3
PCLK2
PCLK1
PCLK0
PCKB2
PCKB1
PCKB0
PCKA2
PCKA1
PCKA0
CAE6
CAE5
CAE4
CAE3
CAE2
CAE1
CAE0
CON45
CON23
CON01
PSWAI
PFRZ
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
6
0
6
0
6
0
5
0
5
0
5
0
4
0
4
0
4
0
3
0
3
0
3
0
2
0
2
0
2
0
1
0
1
0
1
0
Bit 0
0
Bit 0
0
Bit 0
0
0
MC9S12DP512 Device Guide V01.25
$00A0 - $00C7
Address
Name
$00AF
PWMCNT3
$00B0
PWMCNT4
$00B1
PWMCNT5
$00B2
PWMCNT6
$00B3
PWMCNT7
$00B4
PWMPER0
$00B5
PWMPER1
$00B6
PWMPER2
$00B7
PWMPER3
$00B8
PWMPER4
$00B9
PWMPER5
$00BA
PWMPER6
$00BB
PWMPER7
$00BC
PWMDTY0
$00BD
PWMDTY1
$00BE
PWMDTY2
$00BF
PWMDTY3
$00C0
PWMDTY4
$00C1
PWMDTY5
$00C2
PWMDTY6
$00C3
PWMDTY7
$00C4
PWMSDN
$00C5 $00C7
Reserved
PWM (Pulse Width Modulator 8 Bit 8 Channel)
Bit 7
Read:
Bit 7
Write:
0
Read:
Bit 7
Write:
0
Read:
Bit 7
Write:
0
Read:
Bit 7
Write:
0
Read:
Bit 7
Write:
0
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
Bit 7
Write:
Read:
PWMIF
Write:
Read:
0
Write:
Bit 6
6
0
6
0
6
0
6
0
6
0
Bit 5
5
0
5
0
5
0
5
0
5
0
Bit 4
4
0
4
0
4
0
4
0
4
0
Bit 3
3
0
3
0
3
0
3
0
3
0
Bit 2
2
0
2
0
2
0
2
0
2
0
Bit 1
1
0
1
0
1
0
1
0
1
0
Bit 0
Bit 0
0
Bit 0
0
Bit 0
0
Bit 0
0
Bit 0
0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
6
5
4
3
2
1
Bit 0
PWM7
INL
0
PWM7
ENA
0
PWMIE
0
PWM
RSTRT
0
PWMLVL
0
0
0
PWM7IN
0
35
MC9S12DP512 Device Guide V01.25
$00C8 - $00CF
Address
Name
$00C8
SCI0BDH
$00C9
SCI0BDL
$00CA
SC0CR1
$00CB
SCI0CR2
$00CC
SCI0SR1
$00CD
SC0SR2
$00CE
SCI0DRH
$00CF
SCI0DRL
SCI0 (Asynchronous Serial Interface)
Bit 7
Bit 6
Read:
0
0
Write:
Read:
SBR7
SBR6
Write:
Read:
LOOPS SCISWAI
Write:
Read:
TIE
TCIE
Write:
Read: TDRE
TC
Write:
Read:
0
0
Write:
Read:
R8
T8
Write:
Read:
R7
R6
Write:
T7
T6
$00D0 - $00D7
Address
Name
$00D0
SCI1BDH
$00D1
SCI1BDL
$00D2
SC1CR1
$00D3
SCI1CR2
$00D4
SCI1SR1
$00D5
SC1SR2
$00D6
SCI1DRH
$00D7
SCI1DRL
Bit 7
Bit 6
Read:
0
0
Write:
Read:
SBR7
SBR6
Write:
Read:
LOOPS SCISWAI
Write:
Read:
TIE
TCIE
Write:
Read: TDRE
TC
Write:
Read:
0
0
Write:
Read:
R8
T8
Write:
Read:
R7
R6
Write:
T7
T6
36
SPI0CR1
$00D9
SPI0CR2
$00DA
SPI0BR
$00DB
SPI0SR
Bit 3
Bit 2
Bit 1
Bit 0
SBR12
SBR11
SBR10
SBR9
SBR8
SBR5
SBR4
SBR3
SBR2
SBR1
SBR0
RSRC
M
WAKE
ILT
PE
PT
RIE
ILIE
TE
RE
RWU
SBK
RDRF
IDLE
OR
NF
FE
PF
0
0
0
BRK13
TXDIR
0
0
0
0
0
0
R5
T5
R4
T4
R3
T3
R2
T2
R1
T1
R0
T0
RAF
Bit 5
0
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
SBR12
SBR11
SBR10
SBR9
SBR8
SBR5
SBR4
SBR3
SBR2
SBR1
SBR0
RSRC
M
WAKE
ILT
PE
PT
RIE
ILIE
TE
RE
RWU
SBK
RDRF
IDLE
OR
NF
FE
PF
0
0
0
BRK13
TXDIR
0
0
0
0
0
0
R5
T5
R4
T4
R3
T3
R2
T2
R1
T1
R0
T0
RAF
SPI0 (Serial Peripheral Interface)
Name
$00D8
Bit 4
SCI1 (Asynchronous Serial Interface)
$00D8 - $00DF
Address
Bit 5
0
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Bit 7
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
SPIE
SPE
SPTIE
MSTR
CPOL
CPHA
SSOE
LSBFE
0
0
0
SPISWAI
SPC0
SPPR2
SPPR1
SPPR0
SPR2
SPR1
SPR0
0
SPTEF
MODF
0
0
0
0
SPIF
MODFEN BIDIROE
0
0
0
MC9S12DP512 Device Guide V01.25
$00D8 - $00DF
Address
SPI0 (Serial Peripheral Interface)
Name
$00DC
Reserved
$00DD
SPI0DR
$00DE $00DF
Reserved
Read:
Write:
Read:
Write:
Read:
Write:
$00E0 - $00E7
Address
IBAD
$00E1
IBFD
$00E2
IBCR
$00E3
IBSR
$00E4
IBDR
$00E5 $00E7
Reserved
$00E8 - $00EF
Address
Name
$00E8
DLCBCR1
$00E9
DLCBSVR
$00EA
DLCBCR2
$00EB
DLCBDR
$00EC
DLCBARD
$00ED
DLCBRSR
$00EE
DLCSCR
$00EF
DLCBSTAT
Bit 6
0
Bit 5
0
Bit 4
0
Bit 3
0
Bit 2
0
Bit 1
0
Bit 0
0
Bit 7
6
5
4
3
2
1
Bit 0
0
0
0
0
0
0
0
0
IIC (Inter IC Bus)
Name
$00E0
Bit 7
0
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Bit 7
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
ADR7
ADR6
ADR5
ADR4
ADR3
ADR2
ADR1
0
IBC7
IBC6
IBC5
IBC4
IBC3
IBC2
IBC1
IBC0
IBEN
IBIE
MS/SL
TX/RX
TXAK
0
TCF
IAAS
IBB
0
0
RSTA
SRW
D7
D6
D5
D4
D3
D2
D1
D0
0
0
0
0
0
0
0
0
IBAL
IBIF
IBSWAI
RXAK
BDLC (Bytelevel Data Link Controller J1850)
Bit 7
Read:
IMSG
Write:
Read:
0
Write:
Read:
SMRST
Write:
Read:
D7
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Bit 6
Bit 5
0
Bit 4
0
Bit 3
0
Bit 2
0
Bit 1
Bit 0
IE
WCM
0
I3
I2
I1
I0
0
0
DLOOP
RX4XE
NBFS
TEOD
TSIFR
TMIFR1
TMIFR0
D6
D5
D4
D3
D2
D1
D0
0
0
BO3
BO2
BO1
BO0
R5
R4
R3
R2
R1
R0
0
0
0
0
0
0
0
IDLE
CLKS
RXPOL
0
0
0
0
0
BDLCE
0
37
MC9S12DP512 Device Guide V01.25
$00F0 - $00F7
Address
SPI1 (Serial Peripheral Interface)
Name
$00F0
SPI1CR1
$00F1
SPI1CR2
$00F2
SPI1BR
$00F3
SPI1SR
$00F4
Reserved
$00F5
SPI1DR
$00F6 $00F7
Reserved
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
$00F8 - $00FF
Address
SPI2CR1
$00F9
SPI2CR2
$00FA
SPI2BR
$00FB
SPI2SR
$00FC
Reserved
$00FD
SPI2DR
$00FE $00FF
Reserved
$0100 - $010F
38
Address
Name
$0100
FCLKDIV
$0101
FSEC
$0102
FTSTMOD
$0103
FCNFG
$0104
FPROT
$0105
FSTAT
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
SPIE
SPE
SPTIE
MSTR
CPOL
CPHA
SSOE
LSBFE
0
0
0
SPISWAI
SPC0
SPPR2
SPPR1
SPPR0
SPR2
SPR1
SPR0
SPIF
0
SPTEF
MODF
0
0
0
0
0
0
0
0
0
0
0
0
Bit 7
6
5
4
3
2
1
Bit 0
0
0
0
0
0
0
0
0
0
MODFEN BIDIROE
0
0
SPI2 (Serial Peripheral Interface)
Name
$00F8
Bit 7
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Bit 7
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
SPIE
SPE
SPTIE
MSTR
CPOL
CPHA
SSOE
LSBFE
0
0
0
SPISWAI
SPC0
SPPR2
SPPR1
SPPR0
SPR2
SPR1
SPR0
SPIF
0
SPTEF
MODF
0
0
0
0
0
0
0
0
0
0
0
0
Bit 7
6
5
4
3
2
1
Bit 0
0
0
0
0
0
0
0
0
Bit 3
Bit 2
Bit 1
Bit 0
FDIV3
FDIV2
FDIV1
FDIV0
NV3
NV2
SEC1
SEC0
0
0
0
0
0
FPHS0
FPLDIS
0
MODFEN BIDIROE
0
0
Flash Control Register (fts512k4)
Bit 7
Bit 6
Bit 5
Bit 4
Read: FDIVLD
PRDIV8
FDIV5
FDIV4
Write:
Read: KEYEN1 KEYEN0
NV5
NV4
Write:
Read:
0
0
0
WRALL
Write:
Read:
0
CBEIE
CCIE
KEYACC
Write:
Read:
FPOPEN
NV6
FPHDIS FPHS1
Write:
Read:
CCIF
CBEIF
PVIOL ACCERR
Write:
0
BLANK
0
BKSEL1
BKSEL0
FPLS1
FPLS0
0
0
MC9S12DP512 Device Guide V01.25
$0100 - $010F
Address
Flash Control Register (fts512k4)
Name
$0106
FCMD
$0107
Reserved
$0108
FADDRHI
$0109
FADDRLO
$010A
FDATAHI
$010B
FDATALO
$010C $010F
Reserved
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
$0110 - $011B
Address
Name
$0110
ECLKDIV
$0111 $0112
Reserved
$0113
ECNFG
$0114
EPROT
$0115
ESTAT
$0116
ECMD
$0117
Reserved
$0118
EADDRHI
$0119
EADDRLO
$011A
EDATAHI
$011B
EDATALO
Bit 5
Bit 4
0
Bit 3
0
CMDB6
CMDB5
0
0
0
0
0
0
0
0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
0
0
0
0
0
0
0
0
Bit 7
Bit 6
Read: EDIVLD
PRDIV8
Write:
Read:
0
0
Write:
Read:
CBEIE
CCIE
Write:
Read:
NV6
EPOPEN
Write:
Read:
CCIF
CBEIF
Write:
Read:
0
CMDB6
Write:
Read:
0
0
Write:
Read:
0
0
Write:
Read:
Bit 7
6
Write:
Read:
Bit 15
14
Write:
Read:
Bit 7
6
Write:
Bit 2
CMDB2
Bit 1
0
Bit 0
CMDB0
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
EDIV5
EDIV4
EDIV3
EDIV2
EDIV1
EDIV0
0
0
0
0
0
0
0
0
0
0
0
0
NV5
NV4
EPDIS
EP2
EP1
EP0
PVIOL
ACCERR
0
0
0
0
0
0
0
0
0
0
0
5
4
13
5
CMDB5
BLANK
CMDB2
0
CMDB0
0
0
0
10
9
Bit 8
3
2
1
Bit 0
12
11
10
9
Bit 8
4
3
2
1
Bit 0
Bit 2
0
Bit 1
0
Bit 0
0
Reserved for RAM Control Register
Name
Reserved
Bit 6
EEPROM Control Register (eets4k)
$011C - $011F
Address
$011C $011F
Bit 7
0
Read:
Write:
Bit 7
0
Bit 6
0
Bit 5
0
Bit 4
0
Bit 3
0
39
MC9S12DP512 Device Guide V01.25
$0120 - $013F
40
Address
Name
$0120
ATD1CTL0
$0121
ATD1CTL1
$0122
ATD1CTL2
$0123
ATD1CTL3
$0124
ATD1CTL4
$0125
ATD1CTL5
$0126
ATD1STAT0
$0127
Reserved
$0128
ATD1TEST0
$0129
ATD1TEST1
$012A
Reserved
$012B
ATD1STAT1
$012C
Reserved
$012D
ATD1DIEN
$012E
Reserved
$012F
PORTAD1
$0130
ATD1DR0H
$0131
ATD1DR0L
$0132
ATD1DR1H
$0133
ATD1DR1L
$0134
ATD1DR2H
$0135
ATD1DR2L
$0136
ATD1DR3H
$0137
ATD1DR3L
$0138
ATD1DR4H
ATD1 (Analog to Digital Converter 10 Bit 8 Channel)
Bit 7
Read:
0
Write:
Read:
0
Write:
Read:
ADPU
Write:
Read:
0
Write:
Read:
SRES8
Write:
Read:
DJM
Write:
Read:
SCF
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read: CCF7
Write:
Read:
0
Write:
Read:
Bit 7
Write:
Read:
0
Write:
Read:
Bit 7
Write:
Read: Bit 15
Write:
Read:
Bit 7
Write:
Read: Bit 15
Write:
Read:
Bit 7
Write:
Read: Bit 15
Write:
Read:
Bit 7
Write:
Read: Bit 15
Write:
Read:
Bit 7
Write:
Read: Bit 15
Write:
Bit 6
0
Bit 5
0
Bit 4
0
Bit 3
0
Bit 2
0
Bit 1
0
Bit 0
0
0
0
0
0
0
0
0
AFFC
AWAI
ETRIG
ASCIE
S8C
S4C
S2C
S1C
FIFO
FRZ1
FRZ0
SMP1
SMP0
PRS4
PRS3
PRS2
PRS1
PRS0
DSGN
SCAN
MULT
CC
CB
CA
0
ETORF
FIFOR
0
CC2
CC1
CC0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
CCF6
CCF5
CCF4
CCF3
CCF2
CCF1
CCF0
0
0
0
0
0
0
0
6
5
4
3
2
1
Bit 0
0
0
0
0
0
0
0
6
5
4
3
2
1
Bit 0
14
13
12
11
10
9
Bit 8
6
5
4
3
2
1
Bit 0
14
13
12
11
10
9
Bit 8
6
5
4
3
2
1
Bit 0
14
13
12
11
10
9
Bit 8
6
5
4
3
2
1
Bit 0
14
13
12
11
10
9
Bit 8
6
5
4
3
2
1
Bit 0
14
13
12
11
10
9
Bit 8
ETRIGLE ETRIGP
0
0
0
ASCIF
SC
MC9S12DP512 Device Guide V01.25
$0120 - $013F
Address
Name
$0139
ATD1DR4L
$013A
ATD1DR5H
$013B
ATD1DR5L
$013C
ATD1DR6H
$013D
ATD1DR6L
$013E
ATD1DR7H
$013F
ATD1DR7L
$0140 - $017F
Address
ATD1 (Analog to Digital Converter 10 Bit 8 Channel)
Name
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Bit 7
Bit 7
Bit 6
6
Bit 5
5
Bit 4
4
Bit 3
3
Bit 2
2
Bit 1
1
Bit 0
Bit 0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
Bit 3
Bit 2
Bit 1
Bit 0
TIME
WUPE
SLPRQ
INITRQ
SLPAK
INITAK
BRP1
BRP0
CAN0 (Motorola Scalable CAN - MSCAN)
Bit 7
Read:
$0140
CAN0CTL0
RXFRM
Write:
Read:
$0141
CAN0CTL1
CANE
Write:
Read:
$0142
CAN0BTR0
SJW1
Write:
Read:
$0143
CAN0BTR1
SAMP
Write:
Read:
$0144
CAN0RFLG
WUPIF
Write:
Read:
$0145
CAN0RIER
WUPIE
Write:
Read:
0
$0146
CAN0TFLG
Write:
Read:
0
$0147
CAN0TIER
Write:
Read:
0
$0148
CAN0TARQ
Write:
Read:
0
$0149
CAN0TAAK
Write:
Read:
0
$014A
CAN0TBSEL
Write:
Read:
0
$014B
CAN0IDAC
Write:
Read:
0
$014C Reserved
$014D
Write:
Read: RXERR7
$014E
CAN0RXERR
Write:
Read: TXERR7
$014F
CAN0TXERR
Write:
Read:
$0150 - CAN0IDAR0 AC7
$0153 CAN0IDAR3
Write:
Bit 6
RXACT
Bit 5
CSWAI
Bit 4
SYNCH
CLKSRC
LOOPB
LISTEN
SJW0
BRP5
BRP4
0
BRP3
WUPM
BRP2
TSEG22 TSEG21 TSEG20 TSEG13 TSEG12 TSEG11 TSEG10
CSCIF
CSCIE
RSTAT1
RSTAT0
TSTAT1
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
IDAM1
IDAM0
0
0
0
OVRIF
RXF
OVRIE
RXFIE
TXE2
TXE1
TXE0
TXEIE2
TXEIE1
TXEIE0
RSTATE1 RSTATE0 TSTATE1 TSTATE0
0
0
TSTAT0
ABTRQ2 ABTRQ1 ABTRQ0
ABTAK2
ABTAK1
ABTAK0
TX2
TX1
TX0
0
IDHIT2
IDHIT1
IDHIT0
0
0
0
0
RXERR6 RXERR5 RXERR4 RXERR3 RXERR2 RXERR1 RXERR0
TXERR6 TXERR5 TXERR4 TXERR3 TXERR2 TXERR1 TXERR0
AC6
AC5
AC4
AC3
AC2
AC1
AC0
41
MC9S12DP512 Device Guide V01.25
$0140 - $017F
Address
Name
$0154 - CAN0IDMR0 $0157 CAN0IDMR3
$0158 - CAN0IDAR4 $015B CAN0IDAR7
$015C - CAN0IDMR4 $015F CAN0IDMR7
$0160 CAN0RXFG
$016F
$0170 CAN0TXFG
$017F
CAN0 (Motorola Scalable CAN - MSCAN)
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Bit 7
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
AM7
AM6
AM5
AM4
AM3
AM2
AM1
AM0
AC7
AC6
AC5
AC4
AC3
AC2
AC1
AC0
AM7
AM6
AM5
AM4
AM3
AM2
AM1
AM0
FOREGROUND RECEIVE BUFFER see Table 1-2
FOREGROUND TRANSMIT BUFFER see Table 1-2
Table 1-2 Detailed MSCAN Foreground Receive and Transmit Buffer Layout
Address
Name
Extended ID Read:
$xxx0
Standard ID Read:
CANxRIDR0 Write:
Extended ID Read:
$xxx1
Standard ID Read:
CANxRIDR1 Write:
Extended ID Read:
$xxx2
Standard ID Read:
CANxRIDR2 Write:
Extended ID Read:
$xxx3
Standard ID Read:
CANxRIDR3 Write:
$xxx4 - CANxRDSR0 - Read:
$xxxB CANxRDSR7 Write:
Read:
$xxxC
CANRxDLR
Write:
Read:
$xxxD
Reserved
Write:
Read:
$xxxE
CANxRTSRH
Write:
Read:
$xxxF
CANxRTSRL
Write:
Extended ID Read:
CANxTIDR0 Write:
$xx10
Standard ID Read:
Write:
Extended ID Read:
CANxTIDR1 Write:
$xx11
Standard ID Read:
Write:
Extended ID Read:
CANxTIDR2 Write:
$xx12
Standard ID Read:
Write:
42
Bit 7
ID28
ID10
Bit 6
ID27
ID9
Bit 5
ID26
ID8
Bit 4
ID25
ID7
Bit 3
ID24
ID6
Bit 2
ID23
ID5
Bit 1
ID22
ID4
Bit 0
ID21
ID3
ID20
ID2
ID19
ID1
ID18
ID0
SRR=1
RTR
IDE=1
IDE=0
ID17
ID16
ID15
ID14
ID13
ID12
ID11
ID10
ID9
ID8
ID7
ID6
ID5
ID4
ID3
ID2
ID1
ID0
RTR
DB7
DB6
DB5
DB4
DB3
DB2
DB1
DB0
DLC3
DLC2
DLC1
DLC0
TSR15
TSR14
TSR13
TSR12
TSR11
TSR10
TSR9
TSR8
TSR7
TSR6
TSR5
TSR4
TSR3
TSR2
TSR1
TSR0
ID28
ID27
ID26
ID25
ID24
ID23
ID22
ID21
ID10
ID9
ID8
ID7
ID6
ID5
ID4
ID3
ID20
ID19
ID18
SRR=1
IDE=1
ID17
ID16
ID15
ID2
ID1
ID0
RTR
IDE=0
ID14
ID13
ID12
ID11
ID10
ID9
ID8
ID7
MC9S12DP512 Device Guide V01.25
Table 1-2 Detailed MSCAN Foreground Receive and Transmit Buffer Layout
Address
$xx13
$xx14 $xx1B
$xx1C
$xx1D
$xx1E
$xx1F
Name
Extended ID
CANxTIDR3
Standard ID
Read:
Write:
Read:
Write:
Read:
CANxTDSR0 CANxTDSR7 Write:
Read:
CANxTDLR
Write:
Read:
CANxTTBPR
Write:
Read:
CANxTTSRH
Write:
Read:
CANxTTSRL
Write:
$0180 - $01BF
Address
Name
Bit 7
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
ID6
ID5
ID4
ID3
ID2
ID1
ID0
RTR
DB7
DB6
DB5
DB4
DB3
DB2
DB1
DB0
DLC3
DLC2
DLC1
DLC0
PRIO7
PRIO6
PRIO5
PRIO4
PRIO3
PRIO2
PRIO1
PRIO0
TSR15
TSR14
TSR13
TSR12
TSR11
TSR10
TSR9
TSR8
TSR7
TSR6
TSR5
TSR4
TSR3
TSR2
TSR1
TSR0
CAN1 (Motorola Scalable CAN - MSCAN)
Bit 7
Read:
$0180
CAN1CTL0
RXFRM
Write:
Read:
$0181
CAN1CTL1
CANE
Write:
Read:
$0182
CAN1BTR0
SJW1
Write:
Read:
$0183
CAN1BTR1
SAMP
Write:
Read:
$0184
CAN1RFLG
WUPIF
Write:
Read:
$0185
CAN1RIER
WUPIE
Write:
Read:
0
$0186
CAN1TFLG
Write:
Read:
0
$0187
CAN1TIER
Write:
Read:
0
$0188
CAN1TARQ
Write:
Read:
0
$0189
CAN1TAAK
Write:
Read:
0
$018A
CAN1TBSEL
Write:
Read:
0
$018B
CAN1IDAC
Write:
Read:
0
$018C Reserved
$018D
Write:
Read: RXERR7
$018E
CAN1RXERR
Write:
Read: TXERR7
$018F
CAN1TXERR
Write:
Read:
$0190 - CAN1IDAR0 AC7
$0193 CAN1IDAR3
Write:
Bit 6
RXACT
Bit 5
CSWAI
Bit 4
SYNCH
CLKSRC
LOOPB
LISTEN
SJW0
BRP5
BRP4
Bit 3
Bit 2
Bit 1
Bit 0
TIME
WUPE
SLPRQ
INITRQ
SLPAK
INITAK
BRP1
BRP0
0
BRP3
WUPM
BRP2
TSEG22 TSEG21 TSEG20 TSEG13 TSEG12 TSEG11 TSEG10
CSCIF
CSCIE
RSTAT1
RSTAT0
TSTAT1
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
IDAM1
IDAM0
0
0
0
OVRIF
RXF
OVRIE
RXFIE
TXE2
TXE1
TXE0
TXEIE2
TXEIE1
TXEIE0
RSTATE1 RSTATE0 TSTATE1 TSTATE0
0
0
TSTAT0
ABTRQ2 ABTRQ1 ABTRQ0
ABTAK2
ABTAK1
ABTAK0
TX2
TX1
TX0
0
IDHIT2
IDHIT1
IDHIT0
0
0
0
0
RXERR6 RXERR5 RXERR4 RXERR3 RXERR2 RXERR1 RXERR0
TXERR6 TXERR5 TXERR4 TXERR3 TXERR2 TXERR1 TXERR0
AC6
AC5
AC4
AC3
AC2
AC1
AC0
43
MC9S12DP512 Device Guide V01.25
$0180 - $01BF
Address
Name
$0194 - CAN1IDMR0 $0197 CAN1IDMR3
$0198 - CAN1IDAR4 $019B CAN1IDAR7
$019C - CAN1IDMR4 $019F CAN1IDMR7
$01A0 CAN1RXFG
$01AF
$01B0 CAN1TXFG
$01BF
$01C0 - $01FF
Address
Name
$01C0
CAN2CTL0
$01C1
CAN2CTL1
$01C2
CAN2BTR0
$01C3
CAN2BTR1
$01C4
CAN2RFLG
$01C5
CAN2RIER
$01C6
CAN2TFLG
$01C7
CAN2TIER
$01C8
CAN2TARQ
$01C9
CAN2TAAK
$01CA
CAN2TBSEL
$01CB
CAN2IDAC
$01CC $01CD
Reserved
$01CE
CAN2RXERR
$01CF
CAN2TXERR
$01D0 - CAN2IDAR0 $01D3 CAN2IDAR3
$01D4 - CAN2IDMR0 $01D7 CAN2IDMR3
44
CAN1 (Motorola Scalable CAN - MSCAN)
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Bit 7
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
AM7
AM6
AM5
AM4
AM3
AM2
AM1
AM0
AC7
AC6
AC5
AC4
AC3
AC2
AC1
AC0
AM7
AM6
AM5
AM4
AM3
AM2
AM1
AM0
FOREGROUND RECEIVE BUFFER see Table 1-2
FOREGROUND TRANSMIT BUFFER see Table 1-2
CAN2 (Motorola Scalable CAN - MSCAN)
Bit 7
Read:
RXFRM
Write:
Read:
CANE
Write:
Read:
SJW1
Write:
Read:
SAMP
Write:
Read:
WUPIF
Write:
Read:
WUPIE
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read: RXERR7
Write:
Read: TXERR7
Write:
Read:
AC7
Write:
Read:
AM7
Write:
Bit 6
RXACT
Bit 5
CSWAI
Bit 4
SYNCH
CLKSRC
LOOPB
LISTEN
SJW0
BRP5
BRP4
Bit 3
Bit 2
Bit 1
Bit 0
TIME
WUPE
SLPRQ
INITRQ
SLPAK
INITAK
BRP1
BRP0
0
BRP3
WUPM
BRP2
TSEG22 TSEG21 TSEG20 TSEG13 TSEG12 TSEG11 TSEG10
CSCIF
CSCIE
RSTAT1
RSTAT0
TSTAT1
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
IDAM1
IDAM0
0
0
0
OVRIF
RXF
OVRIE
RXFIE
TXE2
TXE1
TXE0
TXEIE2
TXEIE1
TXEIE0
RSTATE1 RSTATE0 TSTATE1 TSTATE0
0
0
TSTAT0
ABTRQ2 ABTRQ1 ABTRQ0
ABTAK2
ABTAK1
ABTAK0
TX2
TX1
TX0
0
IDHIT2
IDHIT1
IDHIT0
0
0
0
0
RXERR6 RXERR5 RXERR4 RXERR3 RXERR2 RXERR1 RXERR0
TXERR6 TXERR5 TXERR4 TXERR3 TXERR2 TXERR1 TXERR0
AC6
AC5
AC4
AC3
AC2
AC1
AC0
AM6
AM5
AM4
AM3
AM2
AM1
AM0
MC9S12DP512 Device Guide V01.25
$01C0 - $01FF
Address
Name
$01D8 - CAN2IDAR4 $01DB CAN2IDAR7
$01DC - CAN2IDMR4 $01DF CAN2IDMR7
$01E0 CAN2RXFG
$01EF
$01F0 CAN2TXFG
$01FF
$0200 - $023F
Address
Name
$0200
CAN3CTL0
$0201
CAN3CTL1
$0202
CAN3BTR0
$0203
CAN3BTR1
$0204
CAN3RFLG
$0205
CAN3RIER
$0206
CAN3TFLG
$0207
CAN3TIER
$0208
CAN3TARQ
$0209
CAN3TAAK
$020A
CAN3TBSEL
$020B
CAN3IDAC
$020C $020D
Reserved
$020E
CAN3RXERR
$020F
CAN3TXERR
$0210 $0213
$0214 $0217
$0218 $021B
CAN3IDAR0 CAN3IDAR3
CAN3IDMR0 CAN3IDMR3
CAN3IDAR4 CAN3IDAR7
CAN2 (Motorola Scalable CAN - MSCAN)
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Bit 7
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
AC7
AC6
AC5
AC4
AC3
AC2
AC1
AC0
AM7
AM6
AM5
AM4
AM3
AM2
AM1
AM0
FOREGROUND RECEIVE BUFFER see Table 1-2
FOREGROUND TRANSMIT BUFFER see Table 1-2
CAN3 (Motorola Scalable CAN - MSCAN)
Bit 7
Read:
RXFRM
Write:
Read:
CANE
Write:
Read:
SJW1
Write:
Read:
SAMP
Write:
Read:
WUPIF
Write:
Read:
WUPIE
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read: RXERR7
Write:
Read: TXERR7
Write:
Read:
AC7
Write:
Read:
AM7
Write:
Read:
AC7
Write:
Bit 6
RXACT
Bit 5
CSWAI
Bit 4
SYNCH
CLKSRC
LOOPB
LISTEN
SJW0
BRP5
BRP4
Bit 3
Bit 2
Bit 1
Bit 0
TIME
WUPE
SLPRQ
INITRQ
SLPAK
INITAK
BRP1
BRP0
0
BRP3
WUPM
BRP2
TSEG22 TSEG21 TSEG20 TSEG13 TSEG12 TSEG11 TSEG10
CSCIF
CSCIE
RSTAT1
RSTAT0
TSTAT1
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
IDAM1
IDAM0
0
0
0
OVRIF
RXF
OVRIE
RXFIE
TXE2
TXE1
TXE0
TXEIE2
TXEIE1
TXEIE0
RSTATE1 RSTATE0 TSTATE1 TSTATE0
0
0
TSTAT0
ABTRQ2 ABTRQ1 ABTRQ0
ABTAK2
ABTAK1
ABTAK0
TX2
TX1
TX0
0
IDHIT2
IDHIT1
IDHIT0
0
0
0
0
RXERR6 RXERR5 RXERR4 RXERR3 RXERR2 RXERR1 RXERR0
TXERR6 TXERR5 TXERR4 TXERR3 TXERR2 TXERR1 TXERR0
AC6
AC5
AC4
AC3
AC2
AC1
AC0
AM6
AM5
AM4
AM3
AM2
AM1
AM0
AC6
AC5
AC4
AC3
AC2
AC1
AC0
45
MC9S12DP512 Device Guide V01.25
$0200 - $023F
Address
Name
$021C - CAN3IDMR4 $021F CAN3IDMR7
$0220 CAN3RXFG
$022F
$0230 CAN3TXFG
$023F
CAN3 (Motorola Scalable CAN - MSCAN)
Read:
Write:
Read:
Write:
Read:
Write:
$0240 - $027F
Address
46
PTT
$0241
PTIT
$0242
DDRT
$0243
RDRT
$0244
PERT
$0245
PPST
$0246 $0247
Reserved
$0248
PTS
$0249
PTIS
$024A
DDRS
$024B
RDRS
$024C
PERS
$024D
PPSS
$024E
WOMS
$024F
Reserved
$0250
PTM
$0251
PTIM
$0252
DDRM
$0253
RDRM
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
AM7
AM6
AM5
AM4
AM3
AM2
AM1
AM0
FOREGROUND RECEIVE BUFFER see Table 1-2
FOREGROUND TRANSMIT BUFFER see Table 1-2
PIM (Port Integration Module PIM_9DP256)
Name
$0240
Bit 7
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Bit 7
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
PTT7
PTT6
PTT5
PTT4
PTT3
PTT2
PTT1
PTT0
PTIT7
PTIT6
PTIT5
PTIT4
PTIT3
PTIT2
PTIT1
PTIT0
DDRT7
DDRT7
DDRT5
DDRT4
DDRT3
DDRT2
DDRT1
DDRT0
RDRT7
RDRT6
RDRT5
RDRT4
RDRT3
RDRT2
RDRT1
RDRT0
PERT7
PERT6
PERT5
PERT4
PERT3
PERT2
PERT1
PERT0
PPST7
PPST6
PPST5
PPST4
PPST3
PPST2
PPST1
PPST0
0
0
0
0
0
0
0
0
PTS7
PTS6
PTS5
PTS4
PTS3
PTS2
PTS1
PTS0
PTIS7
PTIS6
PTIS5
PTIS4
PTIS3
PTIS2
PTIS1
PTIS0
DDRS7
DDRS7
DDRS5
DDRS4
DDRS3
DDRS2
DDRS1
DDRS0
RDRS7
RDRS6
RDRS5
RDRS4
RDRS3
RDRS2
RDRS1
RDRS0
PERS7
PERS6
PERS5
PERS4
PERS3
PERS2
PERS1
PERS0
PPSS7
PPSS6
PPSS5
PPSS4
PPSS3
PPSS2
PPSS1
PPSS0
WOMS7
WOMS6
WOMS5
WOMS4
WOMS3
WOMS2
WOMS1
WOMS0
0
0
0
0
0
0
0
0
PTM7
PTM6
PTM5
PTM4
PTM3
PTM2
PTM1
PTM0
PTIM7
PTIM6
PTIM5
PTIM4
PTIM3
PTIM2
PTIM1
PTIM0
DDRM7
DDRM7
DDRM5
DDRM4
DDRM3
DDRM2
DDRM1
DDRM0
RDRM7
RDRM6
RDRM5
RDRM4
RDRM3
RDRM2
RDRM1
RDRM0
MC9S12DP512 Device Guide V01.25
$0240 - $027F
Address
Name
$0254
PERM
$0255
PPSM
$0256
WOMM
$0257
MODRR
$0258
PTP
$0259
PTIP
$025A
DDRP
$025B
RDRP
$025C
PERP
$025D
PPSP
$025E
PIEP
$025F
PIFP
$0260
PTH
$0261
PTIH
$0262
DDRH
$0263
RDRH
$0264
PERH
$0265
PPSH
$0266
PIEH
$0267
PIFH
$0268
PTJ
$0269
PTIJ
$026A
DDRJ
$026B
RDRJ
$026C
PERJ
PIM (Port Integration Module PIM_9DP256)
Bit 7
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
Read:
PERM7 PERM6 PERM5 PERM4 PERM3 PERM2 PERM1 PERM0
Write:
Read:
PPSM7 PPSM6 PPSM5 PPSM4 PPSM3 PPSM2 PPSM1 PPSM0
Write:
Read:
WOMM7 WOMM6 WOMM5 WOMM4 WOMM3 WOMM2 WOMM1 WOMM0
Write:
Read:
0
MODRR6 MODRR5 MODRR4 MODRR3 MODRR2 MODRR1 MODRR0
Write:
Read:
PTP7
PTP6
PTP5
PTP4
PTP3
PTP2
PTP1
PTP0
Write:
Read: PTIP7
PTIP6
PTIP5
PTIP4
PTIP3
PTIP2
PTIP1
PTIP0
Write:
Read:
DDRP7 DDRP7 DDRP5 DDRP4 DDRP3 DDRP2 DDRP1 DDRP0
Write:
Read:
RDRP7 RDRP6 RDRP5 RDRP4 RDRP3 RDRP2 RDRP1 RDRP0
Write:
Read:
PERP7
PERP6
PERP5
PERP4
PERP3
PERP2
PERP1
PERP0
Write:
Read:
PPSP7
PPSP6
PPSP5
PPSP4
PPSP3
PPSP2
PPSP1
PPSS0
Write:
Read:
PIEP7
PIEP6
PIEP5
PIEP4
PIEP3
PIEP2
PIEP1
PIEP0
Write:
Read:
PIFP7
PIFP6
PIFP5
PIFP4
PIFP3
PIFP2
PIFP1
PIFP0
Write:
Read:
PTH7
PTH6
PTH5
PTH4
PTH3
PTH2
PTH1
PTH0
Write:
Read: PTIH7
PTIH6
PTIH5
PTIH4
PTIH3
PTIH2
PTIH1
PTIH0
Write:
Read:
DDRH7 DDRH7 DDRH5 DDRH4 DDRH3 DDRH2 DDRH1 DDRH0
Write:
Read:
RDRH7 RDRH6 RDRH5 RDRH4 RDRH3 RDRH2 RDRH1 RDRH0
Write:
Read:
PERH7 PERH6 PERH5 PERH4 PERH3 PERH2 PERH1 PERH0
Write:
Read:
PPSH7
PPSH6
PPSH5
PPSH4
PPSH3
PPSH2
PPSH1
PPSH0
Write:
Read:
PIEH7
PIEH6
PIEH5
PIEH4
PIEH3
PIEH2
PIEH1
PIEH0
Write:
Read:
PIFH7
PIFH6
PIFH5
PIFH4
PIFH3
PIFH2
PIFH1
PIFH0
Write:
Read:
0
0
0
0
PTJ7
PTJ6
PTJ1
PTJ0
Write:
Read: PTIJ7
PTIJ6
0
0
0
0
PTIJ1
PTIJ0
Write:
Read:
0
0
0
0
DDRJ7
DDRJ7
DDRJ1
DDRJ0
Write:
Read:
0
0
0
0
RDRJ7
RDRJ6
RDRJ1
RDRJ0
Write:
Read:
0
0
0
0
PERJ7
PERJ6
PERJ1
PERJ0
Write:
47
MC9S12DP512 Device Guide V01.25
$0240 - $027F
Address
Name
$026D
PPSJ
$026E
PIEJ
$026F
PIFJ
$0270 $027F
Reserved
$0280 - $02BF
48
PIM (Port Integration Module PIM_9DP256)
Address
Name
$0280
CAN4CTL0
$0281
CAN4CTL1
$0282
CAN4BTR0
$0283
CAN4BTR1
$0284
CAN4RFLG
$0285
CAN4RIER
$0286
CAN4TFLG
$0287
CAN4TIER
$0288
CAN4TARQ
$0289
CAN4TAAK
$028A
CAN4TBSEL
$028B
CAN4IDAC
$028C $028D
Reserved
$028E
CAN4RXERR
$028F
CAN4TXERR
$0290 $0293
$0294 $0297
$0298 $029B
CAN4IDAR0 CAN4IDAR3
CAN4IDMR0 CAN4IDMR3
CAN4IDAR4 CAN4IDAR7
Read:
Write:
Read:
Write:
Read:
Write:
Bit 7
Bit 6
PPSJ7
PPSJ6
PIEJ7
PIEJ6
PIFJ7
PIFJ6
Bit 5
0
Bit 4
0
Bit 3
0
Bit 2
0
0
0
0
0
0
0
0
0
Bit 1
Bit 0
PPSJ1
PPSJ0
PIEJ1
PIEJ0
PIFJ1
PIFJ0
Read:
CAN4 (Motorola Scalable CAN - MSCAN)
Bit 7
Read:
RXFRM
Write:
Read:
CANE
Write:
Read:
SJW1
Write:
Read:
SAMP
Write:
Read:
WUPIF
Write:
Read:
WUPIE
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read:
0
Write:
Read: RXERR7
Write:
Read: TXERR7
Write:
Read:
AC7
Write:
Read:
AM7
Write:
Read:
AC7
Write:
Bit 6
RXACT
Bit 5
CSWAI
Bit 4
SYNCH
CLKSRC
LOOPB
LISTEN
SJW0
BRP5
BRP4
Bit 3
Bit 2
Bit 1
Bit 0
TIME
WUPE
SLPRQ
INITRQ
SLPAK
INITAK
BRP1
BRP0
0
BRP3
WUPM
BRP2
TSEG22 TSEG21 TSEG20 TSEG13 TSEG12 TSEG11 TSEG10
CSCIF
CSCIE
RSTAT1
RSTAT0
TSTAT1
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
IDAM1
IDAM0
0
0
0
OVRIF
RXF
OVRIE
RXFIE
TXE2
TXE1
TXE0
TXEIE2
TXEIE1
TXEIE0
RSTATE1 RSTATE0 TSTATE1 TSTATE0
0
0
TSTAT0
ABTRQ2 ABTRQ1 ABTRQ0
ABTAK2
ABTAK1
ABTAK0
TX2
TX1
TX0
0
IDHIT2
IDHIT1
IDHIT0
0
0
0
0
RXERR6 RXERR5 RXERR4 RXERR3 RXERR2 RXERR1 RXERR0
TXERR6 TXERR5 TXERR4 TXERR3 TXERR2 TXERR1 TXERR0
AC6
AC5
AC4
AC3
AC2
AC1
AC0
AM6
AM5
AM4
AM3
AM2
AM1
AM0
AC6
AC5
AC4
AC3
AC2
AC1
AC0
MC9S12DP512 Device Guide V01.25
$0280 - $02BF
CAN4 (Motorola Scalable CAN - MSCAN)
Address
Name
$029C - CAN4IDMR4 $029F CAN4IDMR7
$02A0 CAN4RXFG
$02AF
$02B0 CAN4TXFG
$02BF
Read:
Write:
Read:
Write:
Read:
Write:
$02C0 - $03FF
Address
$02C0 $03FF
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
AM7
AM6
AM5
AM4
AM3
AM2
AM1
AM0
FOREGROUND RECEIVE BUFFER see Table 1-2
FOREGROUND TRANSMIT BUFFER see Table 1-2
Reserved
Name
Reserved
Bit 7
Bit 7
0
Read:
Write:
Bit 6
0
Bit 5
0
Bit 4
0
Bit 3
0
Bit 2
0
Bit 1
0
Bit 0
0
1.6 Part ID Assignments
The part ID is located in two 8-bit registers PARTIDH and PARTIDL (addresses $001A and $001B after
reset). The read-only value is a unique part ID for each revision of the chip. Table 1-3 shows the assigned
part ID number.
Table 1-3 Assigned Part ID Numbers
Device
Mask Set Number
Part ID1
MC9S12DP512
0L00M
$0400
MC9S12DP512
1L00M
$0401
MC9S12DP512
2L00M
$0402
MC9S12DP512
3L00M
$0403
MC9S12DP512
4L00M
$0404
NOTES:
1. The coding is as follows:
Bit 15 - 12: Major family identifier
Bit 11 - 8: Minor family identifier
Bit 7 - 4: Major mask set revision number including FAB transfers
Bit 3 - 0: Minor - non full - mask set revision
1.7 Memory Size Assignments
The device memory sizes are located in two 8-bit registers MEMSIZ0 and MEMSIZ1 (addresses $001C
and $001D after reset). Table 1-4 shows the read-only values of these registers. Refer to HCS12 Module
Mapping Control (MMC) Block Guide for further details.
Table 1-4 Memory size registers
Register name
Value
MEMSIZ0
$26
MEMSIZ1
$82
49
MC9S12DP512 Device Guide V01.25
50
MC9S12DP512 Device Guide V01.25
Section 2 Signal Description
This section describes signals that connect off-chip. It includes a pinout diagram, a table of signal
properties, and detailed discussion of signals. It is built from the signal description sections of the Block
Guides of the individual IP blocks on the device.
51
MC9S12DP512 Device Guide V01.25
2.1 Device Pinout
MC9S12DP512
112LQFP
84
83
82
81
80
79
78
77
76
75
74
73
72
71
70
69
68
67
66
65
64
63
62
61
60
59
58
57
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
ADDR5/DATA5/PB5
ADDR6/DATA6/PB6
ADDR7/DATA7/PB7
SS2/KWH7/PH7
SCK2/KWH6/PH6
MOSI2/KWH5/PH5
MISO2/KWH4/PH4
XCLKS/NOACC/PE7
MODB/IPIPE1/PE6
MODA/IPIPE0/PE5
ECLK/PE4
VSSR
VDDR
RESET
VDDPLL
XFC
VSSPLL
EXTAL
XTAL
TEST
SS1/KWH3/PH3
SCK1/KWH2/PH2
MOSI1/KWH1/PH1
MISO1/KWH0/PH0
LSTRB/TAGLO/PE3
R/W/PE2
IRQ/PE1
XIRQ/PE0
SS1/PWM3/KWP3/PP3
SCK1/PWM2/KWP2/PP2
MOSI1/PWM1/KWP1/PP1
MISO1/PWM0/KWP0/PP0
XADDR17/PK3
XADDR16/PK2
XADDR15/PK1
XADDR14/PK0
IOC0/PT0
IOC1/PT1
IOC2/PT2
IOC3/PT3
VDD1
VSS1
IOC4/PT4
IOC5/PT5
IOC6/PT6
IOC7/PT7
XADDR19/PK5
XADDR18/PK4
KWJ1/PJ1
KWJ0/PJ0
MODC/TAGHI/BKGD
ADDR0/DATA0/PB0
ADDR1/DATA1/PB1
ADDR2/DATA2/PB2
ADDR3/DATA3/PB3
ADDR4/DATA4/PB4
112
111
110
109
108
107
106
105
104
103
102
101
100
99
98
97
96
95
94
93
92
91
90
89
88
87
86
85
PP4/KWP4/PWM4/MISO2
PP5/KWP5/PWM5/MOSI2
PP6/KWP6/PWM6/SS2
PP7/KWP7/PWM7/SCK2
PK7/ECS/ROMCTL
VDDX
VSSX
PM0/RXCAN0/RXB
PM1/TXCAN0/TXB
PM2/RXCAN1/RXCAN0/MISO0
PM3/TXCAN1/TXCAN0/SS0
PM4/RXCAN2/RXCAN0/RXCAN4/MOSI0
PM5/TXCAN2/TXCAN0/TXCAN4/SCK0
PJ6/KWJ6/RXCAN4/SDA/RXCAN0
PJ7/KWJ7/TXCAN4/SCL/TXCAN0
VREGEN
PS7/SS0
PS6/SCK0
PS5/MOSI0
PS4/MISO0
PS3/TXD1
PS2/RXD1
PS1/TXD0
PS0/RXD0
PM6/RXCAN3/RXCAN4
PM7/TXCAN3/TXCAN4
VSSA
VRL
The MC9S12DP512 is available in a 112-pin low profile quad flat pack (LQFP). Most pins perform two
or more functions, as described in the Signal Descriptions. Figure 2-1 shows the pin assignments.
Figure 2-1 Pin Assignments in 112-pin LQFP
52
VRH
VDDA
PAD15/AN15/ETRIG1
PAD07/AN07/ETRIG0
PAD14/AN14
PAD06/AN06
PAD13/AN13
PAD05/AN05
PAD12/AN12
PAD04/AN04
PAD11/AN11
PAD03/AN03
PAD10/AN10
PAD02/AN02
PAD09/AN09
PAD01/AN01
PAD08/AN08
PAD00/AN00
VSS2
VDD2
PA7/ADDR15/DATA15
PA6/ADDR14/DATA14
PA5/ADDR13/DATA13
PA4/ADDR12/DATA12
PA3/ADDR11/DATA11
PA2/ADDR10/DATA10
PA1/ADDR9/DATA9
PA0/ADDR8/DATA8
MC9S12DP512 Device Guide V01.25
2.2 Signal Properties Summary
Table 2-1 summarizes the pin functionality.
Table 2-1 Signal Properties
Pin Name Pin Name Pin Name Pin Name Pin Name Power
Funct. 1
Funct. 2
Funct. 3 Funct. 4 Funct. 5 Supply
EXTAL
—
—
—
—
XTAL
—
—
—
—
RESET
—
—
—
—
VDDR
TEST
—
—
—
—
NA
Internal Pull
Resistor
CTRL Reset
State
VDDPLL
Description
Oscillator Pins
None
None
External Reset
Test Input
VREGEN
—
—
—
—
VDDX
Voltage Regulator Enable Input
XFC
—
—
—
—
VDDPLL
PLL Loop Filter
BKGD
TAGHI
MODC
—
—
VDDR
PAD15
AN15
ETRIG1
—
—
Port AD Input, Analog Input AN7 of
ATD1, External Trigger Input of ATD1
PAD[14:8]
AN[14:08]
—
—
—
Port AD Inputs, Analog Inputs
AN[6:0] of ATD1
PAD07
AN07
ETRIG0
—
—
Port AD Input, Analog Input AN7 of
ATD0, External Trigger Input of ATD0
PAD[06:00]
AN[06:00]
—
—
—
Port AD Inputs, Analog Inputs
AN[6:0] of ATD0
PA[7:0]
ADDR[15:8]/
DATA[15:8]
—
—
—
PB[7:0]
ADDR[7:0]/
DATA[7:0]
—
—
—
PUCR/
PUPBE
PE7
NOACC
XCLKS
—
—
PUCR/
PUPEE
PE6
IPIPE1
MODB
—
—
VDDA
IPIPE0
MODA
—
—
PE4
ECLK
—
—
—
PE3
LSTRB
TAGLO
—
—
None
PUCR/
PUPAE
VDDR
PE5
Always
Up
Up
None
Background Debug, Tag High, Mode
Input
Port A I/O, Multiplexed Address/Data
Disabled
Port B I/O, Multiplexed Address/Data
Up
Port E I/O, Access, Clock Select
While RESET
pin is low:
Down
Port E I/O, Pipe Status, Mode Input
While RESET
pin is low:
Down
Port E I/O, Pipe Status, Mode Input
Port E I/O, Bus Clock Output
Port E I/O, Byte Strobe, Tag Low
PUCR/
PUPEE
Up
PE2
R/W
—
—
—
PE1
IRQ
—
—
—
Port E I/O, R/W in expanded modes
Port E Input, Maskable Interrupt
PE0
XIRQ
—
—
—
Port E Input, Non Maskable Interrupt
53
MC9S12DP512 Device Guide V01.25
Pin Name Pin Name Pin Name Pin Name Pin Name Power
Funct. 1
Funct. 2
Funct. 3 Funct. 4 Funct. 5 Supply
Internal Pull
Resistor
CTRL Reset
State
Description
PH7
KWH7
SS2
—
—
Port H I/O, Interrupt, SS of SPI2
PH6
KWH6
SCK2
—
—
Port H I/O, Interrupt, SCK of SPI2
PH5
KWH5
MOSI2
—
—
Port H I/O, Interrupt, MOSI of SPI2
PH4
KWH4
MISO2
—
—
PH3
KWH3
SS1
—
—
PH2
KWH2
SCK1
—
—
Port H I/O, Interrupt, SCK of SPI1
PH1
KWH1
MOSI1
—
—
Port H I/O, Interrupt, MOSI of SPI1
PH0
KWH0
MISO1
—
—
Port H I/O, Interrupt, MISO of SPI1
PJ7
KWJ7
TXCAN4
SCL
TXCAN0
Port J I/O, Interrupt, TX of CAN4,
SCL of IIC, TX of CAN0
PJ6
KWJ6
RXCAN4
SDA
RXCAN0
PJ[1:0]
KWJ[1:0]
—
—
—
PK7
ECS
ROMCTL
—
—
PK[5:0]
XADDR
[19:14]
—
—
—
PM7
TXCAN3
TXCAN4
—
—
PM6
RXCAN3
RXCAN4
—
—
VDDR
VDDX
PERH/
PPSH
PERJ/
PPSJ
Disabled
Up
Port H I/O, Interrupt, MISO of SPI2
Port H I/O, Interrupt, SS of SPI1
Port J I/O, Interrupt, RX of CAN4,
SDA of IIC, RX of CAN0
Port J I/O, Interrupts
VDDX
PUCR/
PUPKE
Up
Port K I/O, Emulation Chip Select,
ROM Control
Port K I/O, Extended Addresses
Port M I/O, TX of CAN3, TX of CAN4
Port M I/O, RX of CAN3, RX of CAN4
Port M I/O, TX of CAN2, CAN0,
CAN4, SCK of SPI0
PM5
TXCAN2
TXCAN0
TXCAN4
SCK0
PM4
RXCAN2
RXCAN0
RXCAN4
MOSI0
PM3
TXCAN1
TXCAN0
—
SS0
PM2
RXCAN1
RXCAN0
—
MISO0
PM1
TXCAN0
TXB
—
—
PM0
RXCAN0
RXB
—
—
Port M I/O, RX of CAN0, RX of BDLC
VDDX
Port M I/O, RX of CAN2, CAN0,
CAN4, MOSI of SPI0
PERM/
Disabled
PPSM
Port M I/O, TX of CAN1, CAN0, SS
of SPI0
Port M I/O, RX of CAN1, CAN0,
MISO of SPI0
Port M I/O, TX of CAN0, RX of BDLC
PP7
KWP7
PWM7
SCK2
—
Port P I/O, Interrupt, Channel 7 of
PWM, SCK of SPI2
PP6
KWP6
PWM6
SS2
—
Port P I/O, Interrupt, Channel 6 of
PWM, SS of SPI2
PP5
KWP5
PWM5
MOSI2
—
Port P I/O, Interrupt, Channel 5 of
PWM, MOSI of SPI2
PP4
KWP4
PWM4
MISO2
—
PP3
KWP3
PWM3
SS1
—
PP2
KWP2
PWM2
SCK1
—
Port P I/O, Interrupt, Channel 2 of
PWM, SCK of SPI1
PP1
KWP1
PWM1
MOSI1
—
Port P I/O, Interrupt, Channel 1 of
PWM, MOSI of SPI1
PP0
KWP0
PWM0
MISO1
—
Port P I/O, Interrupt, Channel 0 of
PWM, MISO2 of SPI1
VDDX
54
PERP/
PPSP
Disabled
Port P I/O, Interrupt, Channel 4 of
PWM, MISO2 of SPI2
Port P I/O, Interrupt, Channel 3 of
PWM, SS of SPI1
MC9S12DP512 Device Guide V01.25
Pin Name Pin Name Pin Name Pin Name Pin Name Power
Funct. 1
Funct. 2
Funct. 3 Funct. 4 Funct. 5 Supply
Internal Pull
Resistor
CTRL Reset
State
Description
PS7
SS0
—
—
—
Port S I/O, SS of SPI0
PS6
SCK0
—
—
—
Port S I/O, SCK of SPI0
PS5
MOSI0
—
—
—
Port S I/O, MOSI of SPI0
PS4
MISO0
—
—
—
PS3
TXD1
—
—
—
PS2
RXD1
—
—
—
Port S I/O, RXD of SCI1
PS1
TXD0
—
—
—
Port S I/O, TXD of SCI0
PS0
RXD0
—
—
—
Port S I/O, RXD of SCI0
PT[7:0]
IOC[7:0]
—
—
—
VDDX
VDDX
PERS/
PPSS
PERT/
PPST
Up
Port S I/O, MISO of SPI0
Port S I/O, TXD of SCI1
Disabled Port T I/O, Timer channels
2.3 Detailed Signal Descriptions
2.3.1 EXTAL, XTAL — Oscillator Pins
EXTAL and XTAL are the crystal driver and external clock pins. On reset all the device clocks are derived
from the EXTAL input frequency. XTAL is the crystal output.
2.3.2 RESET — External Reset Pin
An active low bidirectional control signal, it acts as an input to initialize the MCU to a known start-up
state, and an output when an internal MCU function causes a reset.
2.3.3 TEST — Test Pin
This input only pin is reserved for test.
NOTE:
The TEST pin must be tied to VSS in all applications.
2.3.4 VREGEN — Voltage Regulator Enable Pin
This input only pin enables or disables the on-chip voltage regulator.
55
MC9S12DP512 Device Guide V01.25
2.3.5 XFC — PLL Loop Filter Pin
PLL loop filter. Please ask your Motorola representative for the interactive application note to compute
PLL loop filter elements. Any current leakage on this pin must be avoided.
XFC
R0
MCU
CP
CS
VDDPLL
VDDPLL
Figure 2-2 PLL Loop Filter Connections
2.3.6 BKGD / TAGHI / MODC — Background Debug, Tag High, and Mode Pin
The BKGD/TAGHI/MODC pin is used as a pseudo-open-drain pin for the background debug
communication. In MCU expanded modes of operation when instruction tagging is on, an input low on
this pin during the falling edge of E-clock tags the high half of the instruction word being read into the
instruction queue. It is used as a MCU operating mode select pin during reset. The state of this pin is
latched to the MODC bit at the rising edge of RESET. This pin has a permanently enabled pull-up device.
2.3.7 PAD15 / AN15 / ETRIG1 — Port AD Input Pin of ATD1
PAD15 is a general purpose input pin and analog input AN7 of the analog to digital converter ATD1. It
can act as an external trigger input for the ATD1.
2.3.8 PAD[14:08] / AN[14:08] — Port AD Input Pins of ATD1
PAD14 - PAD08 are general purpose input pins and analog inputs AN[6:0] of the analog to digital
converter ATD1.
2.3.9 PAD7 / AN07 / ETRIG0 — Port AD Input Pin of ATD0
PAD7 is a general purpose input pin and analog input AN7 of the analog to digital converter ATD0. It can
act as an external trigger input for the ATD0.
2.3.10 PAD[06:00] / AN[06:00] — Port AD Input Pins of ATD0
PAD06 - PAD00 are general purpose input pins and analog inputs AN[6:0] of the analog to digital
converter ATD0.
56
MC9S12DP512 Device Guide V01.25
2.3.11 PA[7:0] / ADDR[15:8] / DATA[15:8] — Port A I/O Pins
PA7-PA0 are general purpose input or output pins. In MCU expanded modes of operation, these pins are
used for the multiplexed external address and data bus.
2.3.12 PB[7:0] / ADDR[7:0] / DATA[7:0] — Port B I/O Pins
PB7-PB0 are general purpose input or output pins. In MCU expanded modes of operation, these pins are
used for the multiplexed external address and data bus.
2.3.13 PE7 / NOACC / XCLKS — Port E I/O Pin 7
PE7 is a general purpose input or output pin. During MCU expanded modes of operation, the NOACC
signal, when enabled, is used to indicate that the current bus cycle is an unused or “free” cycle. This signal
will assert when the CPU is not using the bus.
The XCLKS is an input signal which controls whether a crystal in combination with the internal Colpitts
(low power) oscillator is used or whether Pierce oscillator/external clock circuitry is used. The state of this
pin is latched at the rising edge of RESET. If the input is a logic low the EXTAL pin is configured for an
external clock drive or a Pierce Oscillator. If input is a logic high a Colpitts oscillator circuit is configured
on EXTAL and XTAL. Since this pin is an input with a pull-up device during reset, if the pin is left
floating, the default configuration is a Colpitts oscillator circuit on EXTAL and XTAL.
EXTAL
CDC *
MCU
C1
Crystal or
ceramic resonator
XTAL
C2
VSSPLL
* Due to the nature of a translated ground Colpitts oscillator a
DC voltage bias is applied to the crystal
Please contact the crystal manufacturer for crystal DC
bias conditions and recommended capacitor value CDC.
Figure 2-3 Colpitts Oscillator Connections (PE7=1)
57
MC9S12DP512 Device Guide V01.25
EXTAL
C1
MCU
XTAL
Crystal or
ceramic resonator
RB
RS*
C2
VSSPLL
* Rs can be zero (shorted) when used with higher frequency crystals.
Refer to manufacturer’s data.
Figure 2-4 Pierce Oscillator Connections (PE7=0)
EXTAL
CMOS-COMPATIBLE
EXTERNAL OSCILLATOR
(VDDPLL-Level)
MCU
XTAL
not connected
Figure 2-5 External Clock Connections (PE7=0)
2.3.14 PE6 / MODB / IPIPE1 — Port E I/O Pin 6
PE6 is a general purpose input or output pin. It is used as a MCU operating mode select pin during reset.
The state of this pin is latched to the MODB bit at the rising edge of RESET. This pin is shared with the
instruction queue tracking signal IPIPE1. This pin is an input with a pull-down device which is only active
when RESET is low.
2.3.15 PE5 / MODA / IPIPE0 — Port E I/O Pin 5
PE5 is a general purpose input or output pin. It is used as a MCU operating mode select pin during reset.
The state of this pin is latched to the MODA bit at the rising edge of RESET. This pin is shared with the
instruction queue tracking signal IPIPE0. This pin is an input with a pull-down device which is only active
when RESET is low.
2.3.16 PE4 / ECLK — Port E I/O Pin 4
PE4 is a general purpose input or output pin. It can be configured to drive the internal bus clock ECLK.
ECLK can be used as a timing reference.
58
MC9S12DP512 Device Guide V01.25
2.3.17 PE3 / LSTRB / TAGLO — Port E I/O Pin 3
PE3 is a general purpose input or output pin. In MCU expanded modes of operation, LSTRB can be used
for the low-byte strobe function to indicate the type of bus access and when instruction tagging is on,
TAGLO is used to tag the low half of the instruction word being read into the instruction queue.
2.3.18 PE2 / R/W — Port E I/O Pin 2
PE2 is a general purpose input or output pin. In MCU expanded modes of operations, this pin drives the
read/write output signal for the external bus. It indicates the direction of data on the external bus.
2.3.19 PE1 / IRQ — Port E Input Pin 1
PE1 is a general purpose input pin and the maskable interrupt request input that provides a means of
applying asynchronous interrupt requests. This will wake up the MCU from STOP or WAIT mode.
2.3.20 PE0 / XIRQ — Port E Input Pin 0
PE0 is a general purpose input pin and the non-maskable interrupt request input that provides a means of
applying asynchronous interrupt requests. This will wake up the MCU from STOP or WAIT mode.
2.3.21 PH7 / KWH7 / SS2 — Port H I/O Pin 7
PH7 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as slave select pin SS of the Serial Peripheral Interface
2 (SPI2).
2.3.22 PH6 / KWH6 / SCK2 — Port H I/O Pin 6
PH6 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as serial clock pin SCK of the Serial Peripheral Interface
2 (SPI2).
2.3.23 PH5 / KWH5 / MOSI2 — Port H I/O Pin 5
PH5 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as master output (during master mode) or slave input
pin (during slave mode) MOSI of the Serial Peripheral Interface 2 (SPI2).
2.3.24 PH4 / KWH4 / MISO2 — Port H I/O Pin 2
PH4 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as master input (during master mode) or slave output
(during slave mode) pin MISO of the Serial Peripheral Interface 2 (SPI2).
59
MC9S12DP512 Device Guide V01.25
2.3.25 PH3 / KWH3 / SS1 — Port H I/O Pin 3
PH3 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as slave select pin SS of the Serial Peripheral Interface
1 (SPI1).
2.3.26 PH2 / KWH2 / SCK1 — Port H I/O Pin 2
PH2 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as serial clock pin SCK of the Serial Peripheral Interface
1 (SPI1).
2.3.27 PH1 / KWH1 / MOSI1 — Port H I/O Pin 1
PH1 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as master output (during master mode) or slave input
pin (during slave mode) MOSI of the Serial Peripheral Interface 1 (SPI1).
2.3.28 PH0 / KWH0 / MISO1 — Port H I/O Pin 0
PH0 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as master input (during master mode) or slave output
(during slave mode) pin MISO of the Serial Peripheral Interface 1 (SPI1).
2.3.29 PJ7 / KWJ7 / TXCAN4 / SCL / TXCAN0 — PORT J I/O Pin 7
PJ7 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as the transmit pin TXCAN for the Motorola Scalable
Controller Area Network controller 0 or 4 (CAN0 or CAN4) or the serial clock pin SCL of the IIC module.
2.3.30 PJ6 / KWJ6 / RXCAN4 / SDA / RXCAN0 — PORT J I/O Pin 6
PJ6 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as the receive pin RXCAN for the Motorola Scalable
Controller Area Network controller 0 or 4 (CAN 0 or CAN4) or the serial data pin SDA of the IIC module.
2.3.31 PJ[1:0] / KWJ[1:0] — Port J I/O Pins [1:0]
PJ1 and PJ0 are general purpose input or output pins. They can be configured to generate an interrupt
causing the MCU to exit STOP or WAIT mode.
2.3.32 PK7 / ECS / ROMCTL — Port K I/O Pin 7
PK7 is a general purpose input or output pin. During MCU expanded modes of operation, this pin is used
as the emulation chip select output (ECS). During MCU normal expanded modes of operation, this pin is
60
MC9S12DP512 Device Guide V01.25
used to enable the Flash EEPROM memory in the memory map (ROMCTL). At the rising edge of RESET,
the state of this pin is latched to the ROMON bit.
2.3.33 PK[5:0] / XADDR[19:14] — Port K I/O Pins [5:0]
PK5-PK0 are general purpose input or output pins. In MCU expanded modes of operation, these pins
provide the expanded address XADDR[19:14] for the external bus.
2.3.34 PM7 / TXCAN3 / TXCAN4 — Port M I/O Pin 7
PM7 is a general purpose input or output pin. It can be configured as the transmit pin TXCAN of the
Motorola Scalable Controller Area Network controllers 3 or 4 (CAN3 or CAN4).
2.3.35 PM6 / RXCAN3 / RXCAN4 — Port M I/O Pin 6
PM6 is a general purpose input or output pin. It can be configured as the receive pin RXCAN of the
Motorola Scalable Controller Area Network controllers 3 or 4 (CAN3 or CAN4).
2.3.36 PM5 / TXCAN2 / TXCAN0 / TXCAN4 / SCK0 — Port M I/O Pin 5
PM5 is a general purpose input or output pin. It can be configured as the transmit pin TXCAN of the
Motorola Scalable Controller Area Network controllers 2, 0 or 4 (CAN2, CAN0 or CAN4). It can be
configured as the serial clock pin SCK of the Serial Peripheral Interface 0 (SPI0).
2.3.37 PM4 / RXCAN2 / RXCAN0 / RXCAN4/ MOSI0 — Port M I/O Pin 4
PM4 is a general purpose input or output pin. It can be configured as the receive pin RXCAN of the
Motorola Scalable Controller Area Network controllers 2, 0 or 4 (CAN2, CAN0 or CAN4). It can be
configured as the master output (during master mode) or slave input pin (during slave mode) MOSI for
the Serial Peripheral Interface 0 (SPI0).
2.3.38 PM3 / TXCAN1 / TXCAN0 / SS0 — Port M I/O Pin 3
PM3 is a general purpose input or output pin. It can be configured as the transmit pin TXCAN of the
Motorola Scalable Controller Area Network controllers 1 or 0 (CAN1 or CAN0). It can be configured as
the slave select pin SS of the Serial Peripheral Interface 0 (SPI0).
2.3.39 PM2 / RXCAN1 / RXCAN0 / MISO0 — Port M I/O Pin 2
PM2 is a general purpose input or output pin. It can be configured as the receive pin RXCAN of the
Motorola Scalable Controller Area Network controllers 1 or 0 (CAN1 or CAN0). It can be configured as
the master input (during master mode) or slave output pin (during slave mode) MISO for the Serial
Peripheral Interface 0 (SPI0).
61
MC9S12DP512 Device Guide V01.25
2.3.40 PM1 / TXCAN0 / TXB — Port M I/O Pin 1
PM1 is a general purpose input or output pin. It can be configured as the transmit pin TXCAN of the
Motorola Scalable Controller Area Network controller 0 (CAN0). It can be configured as the transmit pin
TXB of the BDLC.
2.3.41 PM0 / RXCAN0 / RXB — Port M I/O Pin 0
PM0 is a general purpose input or output pin. It can be configured as the receive pin RXCAN of the
Motorola Scalable Controller Area Network controller 0 (CAN0). It can be configured as the receive pin
RXB of the BDLC.
2.3.42 PP7 / KWP7 / PWM7 / SCK2 — Port P I/O Pin 7
PP7 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as Pulse Width Modulator (PWM) channel 7 output or
an input for the PWM emergency shutdown. It can be configured as serial clock pin SCK of the Serial
Peripheral Interface 2 (SPI2).
2.3.43 PP6 / KWP6 / PWM6 / SS2 — Port P I/O Pin 6
PP6 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as Pulse Width Modulator (PWM) channel 6 output. It
can be configured as slave select pin SS of the Serial Peripheral Interface 2 (SPI2).
2.3.44 PP5 / KWP5 / PWM5 / MOSI2 — Port P I/O Pin 5
PP5 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as Pulse Width Modulator (PWM) channel 5 output. It
can be configured as master output (during master mode) or slave input pin (during slave mode) MOSI of
the Serial Peripheral Interface 2 (SPI2).
2.3.45 PP4 / KWP4 / PWM4 / MISO2 — Port P I/O Pin 4
PP4 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as Pulse Width Modulator (PWM) channel 4 output. It
can be configured as master input (during master mode) or slave output (during slave mode) pin MISO of
the Serial Peripheral Interface 2 (SPI2).
2.3.46 PP3 / KWP3 / PWM3 / SS1 — Port P I/O Pin 3
PP3 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as Pulse Width Modulator (PWM) channel 3 output. It
can be configured as slave select pin SS of the Serial Peripheral Interface 1 (SPI1).
62
MC9S12DP512 Device Guide V01.25
2.3.47 PP2 / KWP2 / PWM2 / SCK1 — Port P I/O Pin 2
PP2 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as Pulse Width Modulator (PWM) channel 2 output. It
can be configured as serial clock pin SCK of the Serial Peripheral Interface 1 (SPI1).
2.3.48 PP1 / KWP1 / PWM1 / MOSI1 — Port P I/O Pin 1
PP1 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as Pulse Width Modulator (PWM) channel 1 output. It
can be configured as master output (during master mode) or slave input pin (during slave mode) MOSI of
the Serial Peripheral Interface 1 (SPI1).
2.3.49 PP0 / KWP0 / PWM0 / MISO1 — Port P I/O Pin 0
PP0 is a general purpose input or output pin. It can be configured to generate an interrupt causing the MCU
to exit STOP or WAIT mode. It can be configured as Pulse Width Modulator (PWM) channel 0 output. It
can be configured as master input (during master mode) or slave output (during slave mode) pin MISO of
the Serial Peripheral Interface 1 (SPI1).
2.3.50 PS7 / SS0 — Port S I/O Pin 7
PS6 is a general purpose input or output pin. It can be configured as the slave select pin SS of the Serial
Peripheral Interface 0 (SPI0).
2.3.51 PS6 / SCK0 — Port S I/O Pin 6
PS6 is a general purpose input or output pin. It can be configured as the serial clock pin SCK of the Serial
Peripheral Interface 0 (SPI0).
2.3.52 PS5 / MOSI0 — Port S I/O Pin 5
PS5 is a general purpose input or output pin. It can be configured as master output (during master mode)
or slave input pin (during slave mode) MOSI of the Serial Peripheral Interface 0 (SPI0).
2.3.53 PS4 / MISO0 — Port S I/O Pin 4
PS4 is a general purpose input or output pin. It can be configured as master input (during master mode) or
slave output pin (during slave mode) MOSI of the Serial Peripheral Interface 0 (SPI0).
2.3.54 PS3 / TXD1 — Port S I/O Pin 3
PS3 is a general purpose input or output pin. It can be configured as the transmit pin TXD of Serial
Communication Interface 1 (SCI1).
63
MC9S12DP512 Device Guide V01.25
2.3.55 PS2 / RXD1 — Port S I/O Pin 2
PS2 is a general purpose input or output pin. It can be configured as the receive pin RXD of Serial
Communication Interface 1 (SCI1).
2.3.56 PS1 / TXD0 — Port S I/O Pin 1
PS1 is a general purpose input or output pin. It can be configured as the transmit pin TXD of Serial
Communication Interface 0 (SCI0).
2.3.57 PS0 / RXD0 — Port S I/O Pin 0
PS0 is a general purpose input or output pin. It can be configured as the receive pin RXD of Serial
Communication Interface 0 (SCI0).
2.3.58 PT[7:0] / IOC[7:0] — Port T I/O Pins [7:0]
PT7-PT0 are general purpose input or output pins. They can be configured as input capture or output
compare pins IOC7-IOC0 of the Enhanced Capture Timer (ECT).
2.4 Power Supply Pins
MC9S12DP512 power and ground pins are described below.
Table 2-2 MC9S12DP512 Power and Ground Connection Summary
64
Pin Number
112-pin QFP
Nominal
Voltage
VDD1, 2
13, 65
2.5 V
VSS1, 2
14, 66
0V
VDDR
41
5.0 V
VSSR
40
0V
VDDX
107
5.0 V
VSSX
106
0V
VDDA
83
5.0 V
VSSA
86
0V
VRL
85
0V
VRH
84
5.0 V
VDDPLL
43
2.5 V
VSSPLL
45
0V
VREGEN
97
5V
Mnemonic
Description
Internal power and ground generated by internal regulator
External power and ground, supply to pin drivers and internal voltage
regulator.
External power and ground, supply to pin drivers.
Operating voltage and ground for the analog-to-digital converters and
the reference for the internal voltage regulator, allows the supply
voltage to the A/D to be bypassed independently.
Reference voltages for the analog-to-digital converter.
Provides operating voltage and ground for the Phased-Locked Loop.
This allows the supply voltage to the PLL to be bypassed
independently. Internal power and ground generated by internal
regulator.
Internal Voltage Regulator enable/disable
MC9S12DP512 Device Guide V01.25
NOTE:
All VSS pins must be connected together in the application.
2.4.1 VDDX,VSSX — Power & Ground Pins for I/O Drivers
External power and ground for I/O drivers. Because fast signal transitions place high, short-duration
current demands on the power supply, use bypass capacitors with high-frequency characteristics and place
them as close to the MCU as possible. Bypass requirements depend on how heavily the MCU pins are
loaded.
2.4.2 VDDR, VSSR — Power & Ground Pins for I/O Drivers & Internal Voltage
Regulator
External power and ground for I/O drivers and input to the internal voltage regulator. Because fast signal
transitions place high, short-duration current demands on the power supply, use bypass capacitors with
high-frequency characteristics and place them as close to the MCU as possible. Bypass requirements
depend on how heavily the MCU pins are loaded.
2.4.3 VDD1, VDD2, VSS1, VSS2 — Internal Logic Power Supply Pins
Power is supplied to the MCU through VDD and VSS. Because fast signal transitions place high,
short-duration current demands on the power supply, use bypass capacitors with high-frequency
characteristics and place them as close to the MCU as possible. This 2.5V supply is derived from the
internal voltage regulator. There is no static load on those pins allowed. The internal voltage regulator is
turned off, if VREGEN is tied to ground.
NOTE:
No load allowed except for bypass capacitors.
2.4.4 VDDA, VSSA — Power Supply Pins for ATD and VREG
VDDA, VSSA are the power supply and ground input pins for the voltage regulator and the analog to
digital converter. It also provides the reference for the internal voltage regulator. This allows the supply
voltage to the ATD and the reference voltage to be bypassed independently.
2.4.5 VRH, VRL — ATD Reference Voltage Input Pins
VRH and VRL are the reference voltage input pins for the analog to digital converter.
2.4.6 VDDPLL, VSSPLL — Power Supply Pins for PLL
Provides operating voltage and ground for the Oscillator and the Phased-Locked Loop. This allows the
supply voltage to the Oscillator and PLL to be bypassed independently. This 2.5V voltage is generated by
the internal voltage regulator.
NOTE:
No load allowed except for bypass capacitors.
65
MC9S12DP512 Device Guide V01.25
2.4.7 VREGEN — On Chip Voltage Regulator Enable
Enables the internal 5V to 2.5V voltage regulator. If this pin is tied low, VDD1,2 and VDDPLL must be
supplied externally.
66
MC9S12DP512 Device Guide V01.25
Section 3 System Clock Description
3.1 Overview
The Clock and Reset Generator provides the internal clock signals for the core and all peripheral modules.
Figure 3-1 shows the clock connections from the CRG to all modules.
Consult the CRG Block Guide and OSC Block Guide for details on clock generation.
Core Clock
HCS12 CORE
MEBI
CPU
INT
MMC
BDM
BKP
Flash
RAM
EEPROM
ECT
EXTAL
ATD0, 1
OSC
CRG
Bus Clock
PWM
SCI0, SCI1
Oscillator Clock
SPI0, 1, 2
XTAL
CAN0, 1, 2, 3, 4
IIC
BDLC
PIM
Figure 3-1 Clock Connections
67
MC9S12DP512 Device Guide V01.25
68
MC9S12DP512 Device Guide V01.25
Section 4 Modes of Operation
4.1 Overview
Eight possible modes determine the operating configuration of the MC9S12DP512. Each mode has an
associated default memory map and external bus configuration controlled by a further pin.
Three low power modes exist for the device (Section 4.4 Low Power Modes).
4.2 Chip Configuration Summary
The operating mode out of reset is determined by the states of the MODC, MODB, and MODA pins during
reset (Table 4-1). The MODC, MODB, and MODA bits in the MODE register show the current operating
mode and provide limited mode switching during operation. The states of the MODC, MODB, and MODA
pins are latched into these bits on the rising edge of the reset signal. The ROMCTL signal allows the setting
of the ROMON bit in the MISC register thus controlling whether the internal Flash is visible in the
memory map. ROMON = 1 means the Flash is visible in the memory map. The state of the ROMCTL pin
is latched into the ROMON bit in the MISC register on the rising edge of the reset signal.
Table 4-1 Mode Selection
BKGD =
MODC
PE6 =
MODB
PE5 =
MODA
PK7 =
ROMCTL
ROMON
Bit
Mode Description
0
0
0
X
1
Special Single Chip, BDM allowed and ACTIVE. BDM is
allowed in all other modes but a serial command is
required to make BDM active.
0
0
1
0
1
1
0
0
1
0
X
0
0
1
1
0
X
1
0
0
1
1
X
1
0
0
1
1
0
1
1
1
0
0
1
0
1
1
1
0
1
1
1
Emulation Expanded Narrow, BDM allowed
Special Test (Expanded Wide), BDM allowed
Emulation Expanded Wide, BDM allowed
Normal Single Chip, BDM allowed
Normal Expanded Narrow, BDM allowed
Peripheral; BDM allowed but bus operations would cause
bus conflicts (must not be used)
Normal Expanded Wide, BDM allowed
For further explanation on the modes refer to the HCS12 Multiplexed External Bus Interface (MEBI)
Block Guide.
69
MC9S12DP512 Device Guide V01.25
Table 4-2 Clock Selection Based on PE7
PE7 = XCLKS
Description
1
Colpitts Oscillator selected
0
Pierce Oscillator/external clock selected
Table 4-3 Voltage Regulator VREGEN
VREGEN
Description
1
Internal Voltage Regulator enabled
0
Internal Voltage Regulator disabled, VDD1,2 and
VDDPLL must be supplied externally with 2.5V
4.3 Security
The device will make available a security feature preventing the unauthorized read and write of the
memory contents. This feature allows:
•
Protection of the contents of FLASH,
•
Protection of the contents of EEPROM,
•
Operation in single-chip mode,
•
Operation from external memory with internal FLASH and EEPROM disabled.
The user must be reminded that part of the security must lie with the user’s code. An extreme example
would be user’s code that dumps the contents of the internal program. This code would defeat the purpose
of security. At the same time the user may also wish to put a back door in the user’s program. An example
of this is the user downloads a key through the SCI which allows access to a programming routine that
updates parameters stored in EEPROM.
4.3.1 Securing the Microcontroller
Once the user has programmed the FLASH and EEPROM (if desired), the part can be secured by
programming the security bits located in the FLASH module. These non-volatile bits will keep the part
secured through resetting the part and through powering down the part.
The security byte resides in a portion of the Flash array.
Check the Flash Block Guide for more details on the security configuration.
4.3.2 Operation of the Secured Microcontroller
4.3.2.1 Normal Single Chip Mode
This will be the most common usage of the secured part. Everything will appear the same as if the part was
not secured with the exception of BDM operation. The BDM operation will be blocked.
70
MC9S12DP512 Device Guide V01.25
4.3.2.2 Executing from External Memory
The user may wish to execute from external space with a secured microcontroller. This is accomplished
by resetting directly into expanded mode. The internal FLASH and EEPROM will be disabled. BDM
operations will be blocked.
4.3.3 Unsecuring the Microcontroller
In order to unsecure the microcontroller, the internal FLASH and EEPROM must be erased. This can be
done through an external program in expanded mode or via a sequence of BDM commands. Unsecuring
is also possible via the Backdoor Key Access. Refer to Flash Block Guide for details..
Once the user has erased the FLASH and EEPROM, the part can be reset into special single chip mode.
This invokes a program that verifies the erasure of the internal FLASH and EEPROM. Once this program
completes, the user can erase and program the FLASH security bits to the unsecured state. This is generally
done through the BDM, but the user could also change to expanded mode (by writing the mode bits
through the BDM) and jumping to an external program (again through BDM commands). Note that if the
part goes through a reset before the security bits are reprogrammed to the unsecure state, the part will be
secured again.
4.4 Low Power Modes
The microcontroller features three main low power modes. Consult the respective Block Guide for
information on the module behavior in Stop, Pseudo Stop, and Wait Mode. An important source of
information about the clock system is the Clock and Reset Generator Block Guide (CRG).
4.4.1 Stop
Executing the CPU STOP instruction stops all clocks and the oscillator thus putting the chip in fully static
mode. Wake up from this mode can be done via reset or external interrupts.
4.4.2 Pseudo Stop
This mode is entered by executing the CPU STOP instruction. In this mode the oscillator is still running
and the Real Time Interrupt (RTI) or Watchdog (COP) sub module can stay active. Other peripherals are
turned off. This mode consumes more current than the full STOP mode, but the wake up time from this
mode is significantly shorter.
4.4.3 Wait
This mode is entered by executing the CPU WAI instruction. In this mode the CPU will not execute
instructions. The internal CPU signals (address and databus) will be fully static. All peripherals stay active.
For further power consumption the peripherals can individually turn off their local clocks.
71
MC9S12DP512 Device Guide V01.25
4.4.4 Run
Although this is not a low power mode, unused peripheral modules should not be enabled in order to save
power.
72
MC9S12DP512 Device Guide V01.25
Section 5 Resets and Interrupts
5.1 Overview
Consult the Exception Processing section of the CPU12 Reference Manual for information on resets and
interrupts.
5.2 Vectors
5.2.1 Vector Table
Table 5-1 lists interrupt sources and vectors in default order of priority.
Table 5-1 Interrupt Vector Locations
Interrupt Source
CCR
Mask
Local Enable
HPRIO Value
to Elevate
$FFFE, $FFFF
Reset
None
None
–
$FFFC, $FFFD
Clock Monitor fail reset
None
PLLCTL (CME, SCME)
–
$FFFA, $FFFB
COP failure reset
None
COP rate select
–
$FFF8, $FFF9
Unimplemented instruction trap
None
None
–
$FFF6, $FFF7
SWI
None
None
–
$FFF4, $FFF5
XIRQ
X-Bit
None
–
$FFF2, $FFF3
IRQ
I-Bit
IRQCR (IRQEN)
$F2
$FFF0, $FFF1
Real Time Interrupt
I-Bit
CRGINT (RTIE)
$F0
$FFEE, $FFEF
Enhanced Capture Timer channel 0
I-Bit
TIE (C0I)
$EE
$FFEC, $FFED
Enhanced Capture Timer channel 1
I-Bit
TIE (C1I)
$EC
$FFEA, $FFEB
Enhanced Capture Timer channel 2
I-Bit
TIE (C2I)
$EA
$FFE8, $FFE9
Enhanced Capture Timer channel 3
I-Bit
TIE (C3I)
$E8
$FFE6, $FFE7
Enhanced Capture Timer channel 4
I-Bit
TIE (C4I)
$E6
$FFE4, $FFE5
Enhanced Capture Timer channel 5
I-Bit
TIE (C5I)
$E4
$FFE2, $FFE3
Enhanced Capture Timer channel 6
I-Bit
TIE (C6I)
$E2
$FFE0, $FFE1
Enhanced Capture Timer channel 7
I-Bit
TIE (C7I)
$E0
$FFDE, $FFDF
Enhanced Capture Timer overflow
I-Bit
TSRC2 (TOI)
$DE
$FFDC, $FFDD
Pulse accumulator A overflow
I-Bit
PACTL (PAOVI)
$DC
$FFDA, $FFDB
Pulse accumulator input edge
I-Bit
PACTL (PAI)
$DA
$FFD8, $FFD9
SPI0
I-Bit
SPICR1 (SPIE, SPTIE)
$D8
$D6
Vector Address
$FFD6, $FFD7
SCI0
I-Bit
SCICR2
(TIE, TCIE, RIE, ILIE)
$FFD4, $FFD5
SCI1
I-Bit
SCICR2
(TIE, TCIE, RIE, ILIE)
$D4
$FFD2, $FFD3
ATD0
I-Bit
ATDCTL2 (ASCIE)
$D2
$FFD0, $FFD1
ATD1
I-Bit
ATDCTL2 (ASCIE)
$D0
$FFCE, $FFCF
Port J
I-Bit
PIEJ
(PIEJ7, PIEJ6, PIEJ1, PIEJ0)
$CE
$FFCC, $FFCD
Port H
I-Bit
PIEH (PIEH7-0)
$CC
73
MC9S12DP512 Device Guide V01.25
$FFCA, $FFCB
Modulus Down Counter underflow
I-Bit
MCCTL (MCZI)
$CA
$FFC8, $FFC9
Pulse Accumulator B Overflow
I-Bit
PBCTL (PBOVI)
$C8
$FFC6, $FFC7
CRG PLL lock
I-Bit
CRGINT (LOCKIE)
$C6
$FFC4, $FFC5
CRG Self Clock Mode
I-Bit
CRGINT (SCMIE)
$C4
$FFC2, $FFC3
BDLC
I-Bit
DLCBCR1 (IE)
$C2
$FFC0, $FFC1
IIC Bus
I-Bit
IBCR (IBIE)
$C0
$FFBE, $FFBF
SPI1
I-Bit
SPICR1 (SPIE, SPTIE)
$BE
$FFBC, $FFBD
SPI2
I-Bit
SPICR1 (SPIE, SPTIE)
$BC
$FFBA, $FFBB
EEPROM
I-Bit
ECNFG (CCIE, CBEIE)
$BA
$FFB8, $FFB9
FLASH
I-Bit
FCNFG (CCIE, CBEIE)
$B8
$FFB6, $FFB7
CAN0 wake-up
I-Bit
CANRIER (WUPIE)
$B6
$FFB4, $FFB5
CAN0 errors
I-Bit
CANRIER (CSCIE, OVRIE)
$B4
$FFB2, $FFB3
CAN0 receive
I-Bit
CANRIER (RXFIE)
$B2
$FFB0, $FFB1
CAN0 transmit
I-Bit
CANTIER (TXEIE2-TXEIE0)
$B0
$FFAE, $FFAF
CAN1 wake-up
I-Bit
CANRIER (WUPIE)
$AE
$FFAC, $FFAD
CAN1 errors
I-Bit
CANRIER (CSCIE, OVRIE)
$AC
$FFAA, $FFAB
CAN1 receive
I-Bit
CANRIER (RXFIE)
$AA
$FFA8, $FFA9
CAN1 transmit
I-Bit
CANTIER (TXEIE2-TXEIE0)
$A8
$FFA6, $FFA7
CAN2 wake-up
I-Bit
CANRIER (WUPIE)
$A6
$FFA4, $FFA5
CAN2 errors
I-Bit
CANRIER (CSCIE, OVRIE)
$A4
$FFA2, $FFA3
CAN2 receive
I-Bit
CANRIER (RXFIE)
$A2
$FFA0, $FFA1
CAN2 transmit
I-Bit
CANTIER (TXEIE2-TXEIE0)
$A0
$FF9E, $FF9F
CAN3 wake-up
I-Bit
CANRIER (WUPIE)
$9E
$FF9C, $FF9D
CAN3 errors
I-Bit
CANRIER (CSCIE, OVRIE)
$9C
$FF9A, $FF9B
CAN3 receive
I-Bit
CANRIER (RXFIE)
$9A
$FF98, $FF99
CAN3 transmit
I-Bit
CANTIER (TXEIE2-TXEIE0)
$98
$FF96, $FF97
CAN4 wake-up
I-Bit
CANRIER (WUPIE)
$96
$FF94, $FF95
CAN4 errors
I-Bit
CANRIER (CSCIE, OVRIE)
$94
$FF92, $FF93
CAN4 receive
I-Bit
CANRIER (RXFIE)
$92
$FF90, $FF91
CAN4 transmit
I-Bit
CANTIER (TXEIE2-TXEIE0)
$90
$FF8E, $FF8F
Port P Interrupt
I-Bit
PIEP (PIEP7-0)
$8E
$FF8C, $FF8D
PWM Emergency Shutdown
I-Bit
PWMSDN (PWMIE)
$8C
$FF80 to
$FF8B
Reserved
5.3 Effects of Reset
When a reset occurs, MCU registers and control bits are changed to known start-up states. Refer to the
respective module Block Guides for register reset states.
5.3.1 I/O pins
Refer to the HCS12 Multiplexed External Bus Interface (MEBI) Block Guide for mode dependent pin
configuration of port A, B, E and K out of reset.
Refer to the PIM Block Guide for reset configurations of all peripheral module ports.
74
MC9S12DP512 Device Guide V01.25
5.3.2 Memory
Refer to Table 1-1 for locations of the memories depending on the operating mode after reset.
The RAM array is not automatically initialized out of reset.
75
MC9S12DP512 Device Guide V01.25
76
MC9S12DP512 Device Guide V01.25
Section 6 HCS12 Core Block Description
6.1 CPU12 Block Description
Consult the HCS12 CPU Reference Manual for information on the CPU.
6.1.1 Device-specific information
When the HCS12 CPU Reference Manual refers to cycles this is equivalent to Bus Clock periods.
So 1 cycle is equivalent to 1 Bus Clock period.
6.2 HCS12 Module Mapping Control (MMC) Block Description
Consult the MMC Block Guide for information on the HCS12 Module Mapping Control module.
6.2.1 Device-specific information
•
•
INITEE
–
Reset state: $01
–
Bits EE11-EE15 are "Write once in Normal and Emulation modes and write anytime in Special
modes".
PPAGE
–
Reset state: $00
–
Register is "Write anytime in all modes"
6.3 HCS12 Multiplexed External Bus Interface (MEBI) Block
Description
Consult the MEBI Block Guide for information on HCS12 Multiplexed External Bus Interface module.
6.3.1 Device-specific information
•
PUCR
–
Reset state: $90
6.4 HCS12 Interrupt (INT) Block Description
Consult the INT Block Guide for information on the HCS12 Interrupt module.
77
MC9S12DP512 Device Guide V01.25
6.5 HCS12 Background Debug (BDM) Block Description
Consult the BDM Block Guide for information on the HCS12 Background Debug module.
6.5.1 Device-specific information
When the BDM Block Guide refers to alternate clock this is equivalent to Oscillator Clock.
6.6 HCS12 Breakpoint (BKP) Block Description
Consult the BKP Block Guide for information on the HCS12 Breakpoint module.
Section 7 Clock and Reset Generator (CRG) Block
Description
Consult the CRG Block Guide for information about the Clock and Reset Generator module.
7.1 Device-specific information
The Low Voltage Reset feature of the CRG is not available on this device.
Section 8 Oscillator (OSC) Block Description
8.1 Device-specific information
The XCLKS input signal is active low (see 2.3.13 PE7 / NOACC / XCLKS — Port E I/O Pin 7).
Section 9 Enhanced Capture Timer (ECT) Block
Description
Consult the ECT_16B8C Block Guide for information about the Enhanced Capture Timer module.
When the ECT_16B8C Block Guide refers to freeze mode this is equivalent to active BDM mode.
Section 10 Analog to Digital Converter (ATD) Block
Description
78
MC9S12DP512 Device Guide V01.25
There are two Analog to Digital Converters (ATD1 and ATD0) implemented on the MC9S12DP512.
Consult the ATD_10B8C Block Guide for information about each Analog to Digital Converter module.
When the ATD_10B8C Block Guide refers to freeze mode this is equivalent to active BDM mode.
Section 11 Inter-IC Bus (IIC) Block Description
Consult the IIC Block Guide for information about the Inter-IC Bus module.
Section 12 Serial Communications Interface (SCI) Block
Description
There are two Serial Communications Interfaces (SCI1 and SCI0) implemented on the MC9S12DP512
device.
Consult the SCI Block Guide for information about each Serial Communications Interface module.
Section 13 Serial Peripheral Interface (SPI) Block
Description
There are three Serial Peripheral Interfaces (SPI2, SPI1 and SPI0) implemented on MC9S12DP512.
Consult the SPI Block Guide for information about each Serial Peripheral Interface module.
Section 14 J1850 (BDLC) Block Description
Consult the BDLC Block Guide for information about the J1850 module.
Section 15 Pulse Width Modulator (PWM) Block
Description
Consult the PWM_8B6C Block Guide for information about the Pulse Width Modulator module.
When the PWM_8B8C Block Guide refers to freeze mode this is equivalent to active BDM mode.
Section 16 Flash EEPROM 512K Block Description
Consult the FTS512K4 Block Guide for information about the flash module.
79
MC9S12DP512 Device Guide V01.25
The "S12 LRAE" is a generic Load RAM and Execute (LRAE) program which will be programmed into
the flash memory of this device during manufacture. This LRAE program will provide greater
programming flexibility to the end users by allowing the device to be programmed directly using CAN or
SCI after it is assembled on the PCB. Use of the LRAE program is at the discretion of the end user and, if
not required, it must simply be erased prior to flash programming. For more details of the S12 LRAE and
its implementation, please see the S12 LREA Application Note (AN2546/D).
It is planned that most HC9S12 devices manufactured after Q1 of 2004 will be shipped with the S12 LRAE
programmed in the Flash. Exact details of the changeover (i.e. blank to programmed) for each product will
be communicated in advance via GPCN and will be traceable by the customer via datecode marking on
the device.
Please contact Motorola SPS Sales if you have any additional questions.
Section 17 EEPROM 4K Block Description
Consult the EETS4K Block Guide for information about the EEPROM module.
Section 18 RAM Block Description
This module supports single-cycle misaligned word accesses.
Section 19 MSCAN Block Description
There are five MSCAN modules (CAN4, CAN3, CAN2, CAN1 and CAN0) implemented on the
MC9S12DP512.
Consult the MSCAN Block Guide for information about the Motorola Scalable CAN Module.
Section 20 Port Integration Module (PIM) Block Description
Consult the functionally equivalent PIM_9DP256 Block Guide for information about the Port Integration
Module.
Section 21 Voltage Regulator (VREG) Block Description
Consult the VREG Block Guide for information about the dual output linear voltage regulator.
80
MC9S12DP512 Device Guide V01.25
Section 22 Printed Circuit Board Layout Proposal
Table 22-1 Suggested External Component Values
Component
Purpose
Type
Value
C1
VDD1 filter cap
ceramic X7R
100 … 220nF
C2
VDD2 filter cap
ceramic X7R
100 … 220nF
C3
VDDA filter cap
ceramic X7R
100nF
C4
VDDR filter cap
X7R/tantalum
>= 100nF
C5
VDDPLL filter cap
ceramic X7R
100nF
C6
VDDX filter cap
X7R/tantalum
>= 100nF
C7
OSC load cap
C8
OSC load cap
C9 / CS
PLL loop filter cap
C10 / CP
PLL loop filter cap
C11 / CDC
DC cutoff cap
Colpitts mode only, if recommended by
quartz manufacturer
R1 / R
PLL loop filter res
See PLL Specification chapter
See PLL specification chapter
R2 / RB
Pierce mode only
R3 / RS
Q1
Quartz
The PCB must be carefully laid out to ensure proper operation of the voltage regulator as well as of the
MCU itself. The following rules must be observed:
•
Every supply pair must be decoupled by a ceramic capacitor connected as near as possible to the
corresponding pins (C1 – C6).
•
Central point of the ground star should be the VSSR pin.
•
Use low ohmic low inductance connections between VSS1, VSS2 and VSSR.
•
VSSPLL must be directly connected to VSSR.
•
Keep traces of VSSPLL, EXTAL and XTAL as short as possible and occupied board area for C7,
C8, C11 and Q1 as small as possible.
•
Do not place other signals or supplies underneath area occupied by C7, C8, C10 and Q1 and the
connection area to the MCU.
•
Central power input should be fed in at the VDDA/VSSA pins.
81
MC9S12DP512 Device Guide V01.25
Figure 22-1 Recommended PCB Layout for 112LQFP Colpitts Oscillator
VREGEN
C6
VDDX
VSSX
VSSA
C3
VDDA
VDD1
C1
VSS1
VSS2
C2
VDD2
VSSR
C4
C7
82
C8
C10
C9
R1
C11
C5
VDDR
Q1
VSSPLL
VDDPLL
MC9S12DP512 Device Guide V01.25
Figure 22-2 Recommended PCB Layout for 112LQFP Pierce Oscillator
VREGEN
C6
VDDX
VSSX
VSSA
C3
VDDA
VDD1
C1
VSS1
VSS2
C2
VDD2
VSSR
VSSPLL
C4
R3
C5
VDDR
R2
Q1
C7
C8
C10
C9
VDDPLL
R1
83
MC9S12DP512 Device Guide V01.25
84
MC9S12DP512 Device Guide V01.25
Appendix A Electrical Characteristics
A.1 General
NOTE:
The electrical characteristics given in this section are preliminary and should be
used as a guide only. Values cannot be guaranteed by Motorola and are subject to
change without notice.
This supplement contains the most accurate electrical information for the MC9S12DP512 microcontroller
available at the time of publication. The information should be considered PRELIMINARY and is subject
to change.
This introduction is intended to give an overview on several common topics like power supply, current
injection etc.
A.1.1 Parameter Classification
The electrical parameters shown in this supplement are guaranteed by various methods. To give the
customer a better understanding the following classification is used and the parameters are tagged
accordingly in the tables where appropriate.
NOTE:
This classification is shown in the column labeled “C” in the parameter tables
where appropriate.
P:
Those parameters are guaranteed during production testing on each individual device.
C:
Those parameters are achieved by the design characterization by measuring a statistically relevant
sample size across process variations.
T:
Those parameters are achieved by design characterization on a small sample size from typical devices
under typical conditions unless otherwise noted. All values shown in the typical column are within
this category.
D:
Those parameters are derived mainly from simulations.
A.1.2 Power Supply
The MC9S12DP512 utilizes several pins to supply power to the I/O ports, A/D converter, oscillator, PLL
and internal logic.
The VDDA, VSSA pair supplies the A/D converter and the resistor ladder of the internal voltage regulator.
85
MC9S12DP512 Device Guide V01.25
The VDDX, VSSX, VDDR and VSSR pairs supply the I/O pins, VDDR supplies also the internal voltage
regulator.
VDD1, VSS1, VDD2 and VSS2 are the supply pins for the digital logic, VDDPLL, VSSPLL supply the
oscillator and the PLL.
VSS1 and VSS2 are internally connected by metal.
VDDA, VDDX, VDDR as well as VSSA, VSSX, VSSR are connected by anti-parallel diodes for ESD
protection.
NOTE:
In the following context VDD5 is used for either VDDA, VDDR and VDDX; VSS5
is used for either VSSA, VSSR and VSSX unless otherwise noted.
IDD5 denotes the sum of the currents flowing into the VDDA, VDDX and VDDR
pins.
VDD is used for VDD1, VDD2 and VDDPLL, VSS is used for VSS1, VSS2 and
VSSPLL.
IDD is used for the sum of the currents flowing into VDD1 and VDD2.
A.1.3 Pins
There are four groups of functional pins.
A.1.3.1 5V I/O pins
Those I/O pins have a nominal level of 5V. This class of pins is comprised of all port I/O pins, the analog
inputs, BKGD and the RESET pins.The internal structure of all those pins is identical, however some of
the functionality may be disabled. E.g. for the analog inputs the output drivers, pull-up and pull-down
resistors are disabled permanently.
A.1.3.2 Analog Reference
This group is made up by the VRH and VRL pins.
A.1.3.3 Oscillator
The pins XFC, EXTAL, XTAL dedicated to the oscillator have a nominal 2.5V level. They are supplied
by VDDPLL.
A.1.3.4 TEST
This pin is used for production testing only.
A.1.3.5 VREGEN
This pin is used to enable the on chip voltage regulator.
86
MC9S12DP512 Device Guide V01.25
A.1.4 Current Injection
Power supply must maintain regulation within operating VDD5 or VDD range during instantaneous and
operating maximum current conditions. If positive injection current (Vin > VDD5) is greater than IDD5, the
injection current may flow out of VDD5 and could result in external power supply going out of regulation.
Ensure external VDD5 load will shunt current greater than maximum injection current. This will be the
greatest risk when the MCU is not consuming power; e.g. if no system clock is present, or if clock rate is
very low which would reduce overall power consumption.
A.1.5 Absolute Maximum Ratings
Absolute maximum ratings are stress ratings only. A functional operation under or outside those maxima
is not guaranteed. Stress beyond those limits may affect the reliability or cause permanent damage of the
device.
This device contains circuitry protecting against damage due to high static voltage or electrical fields;
however, it is advised that normal precautions be taken to avoid application of any voltages higher than
maximum-rated voltages to this high-impedance circuit. Reliability of operation is enhanced if unused
inputs are tied to an appropriate logic voltage level (e.g., either VSS5 or VDD5).
Table A-1 Absolute Maximum Ratings1
Num
Rating
Symbol
Min
Max
Unit
1
I/O, Regulator and Analog Supply Voltage
VDD5
-0.3
6.0
V
2
Digital Logic Supply Voltage 2
VDD
-0.3
3.0
V
3
PLL Supply Voltage (2)
VDDPLL
-0.3
3.0
V
4
Voltage difference VDDX to VDDR and VDDA
∆VDDX
-0.3
0.3
V
5
Voltage difference VSSX to VSSR and VSSA
∆VSSX
-0.3
0.3
V
6
Digital I/O Input Voltage
VIN
-0.3
6.0
V
7
Analog Reference
VRH, VRL
-0.3
6.0
V
8
XFC, EXTAL, XTAL inputs
VILV
-0.3
3.0
V
9
TEST input
VTEST
-0.3
10.0
V
10
Instantaneous Maximum Current
Single pin limit for all digital I/O pins 3
ID
-25
+25
mA
11
Instantaneous Maximum Current
Single pin limit for XFC, EXTAL, XTAL4
IDL
-25
+25
mA
12
Instantaneous Maximum Current
Single pin limit for TEST 5
IDT
-0.25
0
mA
13
Storage Temperature Range
T
– 65
155
°C
stg
NOTES:
1. Beyond absolute maximum ratings device might be damaged.
87
MC9S12DP512 Device Guide V01.25
2. The device contains an internal voltage regulator to generate the logic and PLL supply out of the I/O supply.
The absolute maximum ratings apply when the device is powered from an external source.
3. All digital I/O pins are internally clamped to VSSX and VDDX, VSSR and VDDR or VSSA and VDDA.
4. Those pins are internally clamped to VSSPLL and VDDPLL.
5. This pin is clamped low to VSSX, but not clamped high. This pin must be tied low in applications.
A.1.6 ESD Protection and Latch-up Immunity
All ESD testing is in conformity with CDF-AEC-Q100 Stress test qualification for Automotive Grade
Integrated Circuits. During the device qualification ESD stresses were performed for the Human Body
Model (HBM), the Machine Model (MM) and the Charge Device Model.
A device will be defined as a failure if after exposure to ESD pulses the device no longer meets the device
specification. Complete DC parametric and functional testing is performed per the applicable device
specification at room temperature followed by hot temperature, unless specified otherwise in the device
specification.
Table A-2 ESD and Latch-up Test Conditions
Model
Human Body
Machine
Description
Symbol
Value
Unit
Series Resistance
R1
1500
Ohm
Storage Capacitance
C
100
pF
Number of Pulse per pin
positive
negative
-
3
3
Series Resistance
R1
0
Ohm
Storage Capacitance
C
200
pF
Number of Pulse per pin
positive
negative
-
3
3
Minimum input voltage limit
-2.5
V
Maximum input voltage limit
7.5
V
Latch-up
Table A-3 ESD and Latch-up Protection Characteristics
Num C
88
Rating
Symbol
Min
Max
Unit
1
C Human Body Model (HBM)
VHBM
2000
-
V
2
C Machine Model (MM)
VMM
200
-
V
3
C Charge Device Model (CDM)
VCDM
500
-
V
4
Latch-up Current at TA = 125°C
C positive
negative
ILAT
+100
-100
-
mA
5
Latch-up Current at TA = 27°C
C positive
negative
ILAT
+200
-200
-
mA
MC9S12DP512 Device Guide V01.25
A.1.7 Operating Conditions
This chapter describes the operating conditions of the device. Unless otherwise noted those conditions
apply to all the following data.
NOTE:
Please refer to the temperature rating of the device (C, V, M) with regards to the
ambient temperature TA and the junction temperature TJ. For power dissipation
calculations refer to Section A.1.8 Power Dissipation and Thermal
Characteristics.
Table A-4 Operating Conditions
Rating
Symbol
Min
Typ
Max
Unit
I/O, Regulator and Analog Supply Voltage
VDD5
4.5
5
5.25
V
Digital Logic Supply Voltage 1
VDD
2.35
2.5
2.75
V
PLL Supply Voltage (1)
VDDPLL
2.35
2.5
2.75
V
Voltage Difference VDDX to VDDR and VDDA
∆VDDX
-0.1
0
0.1
V
Voltage Difference VSSX to VSSR and VSSA
∆VSSX
-0.1
0
0.1
V
Bus Frequency (MC9S12DP512C, V, M)
fbus
0.25 2
-
25
MHz
Operating Junction Temperature Range
T
J
-40
-
100
°C
Operating Ambient Temperature Range 3
T
A
-40
27
85
°C
Operating Junction Temperature Range
TJ
-40
-
120
°C
Operating Ambient Temperature Range (3)
TA
-40
27
105
°C
Operating Junction Temperature Range
TJ
-40
-
140
°C
Operating Ambient Temperature Range (3)
TA
-40
27
125
°C
MC9S12DP512C
MC9S12DP512V
MC9S12DP512M
NOTES:
1. The device contains an internal voltage regulator to generate the logic and PLL supply out of the I/O supply. The
given operating range applies when this regulator is disabled and the device is powered from an external source.
2. Some blocks e.g. ATD (conversion) and NVMs (program/erase) require higher bus frequencies for proper operation.
3. Please refer to Section A.1.8 Power Dissipation and Thermal Characteristics for more details about the relation between ambient temperature TA and device junction temperature TJ.
A.1.8 Power Dissipation and Thermal Characteristics
Power dissipation and thermal characteristics are closely related. The user must assure that the maximum
operating junction temperature is not exceeded. The average chip-junction temperature (TJ) in °C can be
obtained from:
89
MC9S12DP512 Device Guide V01.25
T J = T A + ( P D • Θ JA )
T J = Junction Temperature, [°C ]
T A = Ambient Temperature, [°C ]
P D = Total Chip Power Dissipation, [W]
Θ JA = Package Thermal Resistance, [°C/W]
The total power dissipation can be calculated from:
P D = P INT + P IO
P INT = Chip Internal Power Dissipation, [W]
Two cases with internal voltage regulator enabled and disabled must be considered:
1. Internal Voltage Regulator disabled
P INT = I DD ⋅ V DD + I DDPLL ⋅ V DDPLL + I DDA ⋅ V DDA
P IO =
∑ RDSON ⋅ IIOi
2
i
PIO is the sum of all output currents on I/O ports associated with VDDX and VDDR.
For RDSON is valid:
V OL
R DSON = ------------ ;for outputs driven low
I OL
respectively
V DD5 – V OH
R DSON = ------------------------------------ ;for outputs driven high
I OH
2. Internal voltage regulator enabled
P INT = I DDR ⋅ V DDR + I DDA ⋅ V DDA
IDDR is the current shown in Table A-7 and not the overall current flowing into VDDR, which
additionally contains the current flowing into the external loads with output high.
2
P IO =
R DSON ⋅ I IO
i
i
∑
PIO is the sum of all output currents on I/O ports associated with VDDX and VDDR.
90
MC9S12DP512 Device Guide V01.25
Table A-5 Thermal Package Characteristics1
Num C
Rating
Symbol
Min
Typ
Max
Unit
1
T Thermal Resistance LQFP112, single sided PCB2
θJA
-
-
54
o
2
T
Thermal Resistance LQFP112, double sided PCB
with 2 internal planes3
θJA
-
-
41
o
C/W
C/W
NOTES:
1. The values for thermal resistance are achieved by package simulations
2. PC Board according to EIA/JEDEC Standard 51-2
3. PC Board according to EIA/JEDEC Standard 51-7
A.1.9 I/O Characteristics
This section describes the characteristics of all 5V I/O pins. All parameters are not always applicable, e.g.
not all pins feature pull up/down resistances.
91
MC9S12DP512 Device Guide V01.25
Table A-6 5V I/O Characteristics
Conditions are shown in Table A-4 unless otherwise noted
Num C
Symbol
Min
Typ
Max
Unit
P Input High Voltage
V
IH
0.65*VDD5
-
-
V
T Input High Voltage
VIH
-
-
VDD5 + 0.3
V
P Input Low Voltage
VIL
-
-
0.35*VDD5
V
T Input Low Voltage
VIL
VSS5 - 0.3
-
-
V
3
C Input Hysteresis
V
HYS
-
250
-
mV
4
Input Leakage Current (pins in high impedance input
P mode)
V =V
or VSS5
in
DD5
Iin
–1
-
1
µA
5
Output High Voltage (pins in output mode)
P Partial Drive IOH = –2mA
Full Drive IOH = –10mA
V
VDD5 – 0.8
-
-
V
6
Output Low Voltage (pins in output mode)
P Partial Drive IOL = +2mA
Full Drive IOL = +10mA
V
OL
-
-
0.8
V
7
Internal Pull Up Device Current,
P tested at V Max.
IPUL
-
-
-130
µA
Internal Pull Up Device Current,
C tested at V Min.
IPUH
-10
-
-
µA
9
Internal Pull Down Device Current,
P tested at V Min.
IH
IPDH
-
-
130
µA
10
Internal Pull Down Device Current,
C tested at V Max.
IPDL
10
-
-
µA
11
D Input Capacitance
Cin
-
6
-
pF
12
Injection current1
T Single Pin limit
Total Device Limit. Sum of all injected currents
IICS
IICP
-2.5
-25
-
2.5
25
mA
13
P Port H, J, P Interrupt Input Pulse filtered2
tPIGN
-
-
3
µs
14
P Port H, J, P Interrupt Input Pulse passed(2)
tPVAL
10
-
-
µs
1
2
Rating
IL
8
IH
IL
OH
NOTES:
1. Refer to Section A.1.4 Current Injection, for more details
2. Parameter only applies in STOP or Pseudo STOP mode.
A.1.10 Supply Currents
This section describes the current consumption characteristics of the device as well as the conditions for
the measurements.
92
MC9S12DP512 Device Guide V01.25
A.1.10.1 Measurement Conditions
All measurements are without output loads. Unless otherwise noted the currents are measured in single
chip mode, internal voltage regulator enabled and at 25MHz bus frequency using a 4MHz oscillator in
Colpitts mode. Production testing is performed using a square wave signal at the EXTAL input.
A.1.10.2 Additional Remarks
In expanded modes the currents flowing in the system are highly dependent on the load at the address, data
and control signals as well as on the duty cycle of those signals. No generally applicable numbers can be
given. A very good estimate is to take the single chip currents and add the currents due to the external
loads.
Table A-7 Supply Current Characteristics
Conditions are shown in Table A-4 unless otherwise noted
Num C
Rating
Symbol
Run supply currents
Single Chip, Internal regulator enabled
IDD5
1
P
2
P
P
All modules enabled, PLL on
only RTI enabled (1)
C
P
C
C
P
C
P
C
P
Pseudo Stop Current (RTI and COP disabled) 1, 2
-40°C
27°C
70°C
85°C
"C" Temp Option 100°C
105°C
"V" Temp Option 120°C
125°C
"M" Temp Option 140°C
C
C
C
C
C
C
C
Pseudo Stop Current (RTI and COP enabled) (1), (2)
-40°C
27°C
70°C
85°C
105°C
125°C
140°C
Min
Typ
-
-
-
-
Max
65
Unit
mA
Wait Supply current
3
4
IDDW
IDDPS
IDDPS
-
-
370
400
450
550
600
650
800
850
1200
570
600
650
750
850
1200
1500
40
5
mA
500
1600
µA
2100
5000
-
µA
Stop Current (2)
5
C
P
C
C
P
C
P
C
P
-40°C
27°C
70°C
85°C
"C" Temp Option 100°C
105°C
"V" Temp Option 120°C
125°C
"M" Temp Option 140°C
IDDS
-
12
25
100
130
160
200
350
400
600
100
1200
µA
1700
5000
93
MC9S12DP512 Device Guide V01.25
NOTES:
1. PLL off
2. At those low power dissipation levels TJ = TA can be assumed
94
MC9S12DP512 Device Guide V01.25
A.2 ATD Characteristics
This section describes the characteristics of the analog to digital converter.
A.2.1 ATD Operating Characteristics
The Table A-8 shows conditions under which the ATD operates.
The following constraints exist to obtain full-scale, full range results:
VSSA ≤ VRL ≤ VIN ≤ VRH ≤ VDDA. This constraint exists since the sample buffer amplifier can not drive
beyond the power supply levels that it ties to. If the input level goes outside of this range it will effectively
be clipped.
Table A-8 ATD Operating Characteristics
Conditions are shown in Table A-4 unless otherwise noted
Num C
Rating
Symbol
Min
Typ
Max
Unit
VRL
VRH
VSSA
VDDA/2
-
VDDA/2
VDDA
V
V
Reference Potential
1
D
Low
High
2
C Differential Reference Voltage1
VRH-VRL
4.50
5.00
5.25
V
3
D ATD Clock Frequency
fATDCLK
0.5
-
2.0
MHz
4
D
NCONV10
TCONV10
14
7
-
28
14
Cycles
µs
5
D
NCONV8
TCONV8
12
6
-
26
13
Cycles
µs
6
D Recovery Time (VDDA=5.0 Volts)
tREC
-
-
20
µs
7
P Reference Supply current 2 ATD blocks on
IREF
-
-
0.750
mA
8
P Reference Supply current 1 ATD block on
IREF
-
-
0.375
mA
ATD 10-Bit Conversion Period
Clock Cycles2
Conv, Time at 2.0MHz ATD Clock fATDCLK
ATD 8-Bit Conversion Period
Clock Cycles(2)
Conv, Time at 2.0MHz ATD Clock fATDCLK
NOTES:
1. Full accuracy is not guaranteed when differential voltage is less than 4.50V
2. The minimum time assumes a final sample period of 2 ATD clocks cycles while the maximum time assumes a final sample
period of 16 ATD clocks.
A.2.2 Factors influencing accuracy
Three factors - source resistance, source capacitance and current injection - have an influence on the
accuracy of the ATD.
A.2.2.1 Source Resistance
Due to the input pin leakage current as specified in Table A-6 in conjunction with the source resistance
there will be a voltage drop from the signal source to the ATD input. The maximum source resistance RS
95
MC9S12DP512 Device Guide V01.25
specifies results in an error of less than 1/2 LSB (2.5mV) at the maximum leakage current. If device or
operating conditions are less than worst case or leakage-induced error is acceptable, larger values of source
resistance is allowed.
A.2.2.2 Source Capacitance
When sampling an additional internal capacitor is switched to the input. This can cause a voltage drop due
to charge sharing with the external and the pin capacitance. For a maximum sampling error of the input
voltage ≤ 1LSB, then the external filter capacitor, Cf ≥ 1024 * (CINS- CINN).
A.2.2.3 Current Injection
There are two cases to consider.
1. A current is injected into the channel being converted. The channel being stressed has conversion
values of $3FF ($FF in 8-bit mode) for analog inputs greater than VRH and $000 for values less than
VRL unless the current is higher than specified as disruptive condition.
2. Current is injected into pins in the neighborhood of the channel being converted. A portion of this
current is picked up by the channel (coupling ratio K), This additional current impacts the accuracy
of the conversion depending on the source resistance.
The additional input voltage error on the converted channel can be calculated as VERR = K * RS *
IINJ, with IINJ being the sum of the currents injected into the two pins adjacent to the converted
channel.
Table A-9 ATD Electrical Characteristics
Conditions are shown in Table A-4 unless otherwise noted
Num C
Rating
Symbol
Min
Typ
Max
Unit
1
C Max input Source Resistance
RS
-
-
1
KΩ
2
Total Input Capacitance
T Non Sampling
Sampling
CINN
CINS
-
-
10
22
pF
3
C Disruptive Analog Input Current
INA
-2.5
-
2.5
mA
4
C Coupling Ratio positive current injection
Kp
-
-
10-4
A/A
5
C Coupling Ratio negative current injection
Kn
-
-
10-2
A/A
96
MC9S12DP512 Device Guide V01.25
A.2.3 ATD accuracy
Table A-10 specifies the ATD conversion performance excluding any errors due to current injection,
input capacitance and source resistance.
Table A-10 ATD Conversion Performance
Conditions are shown in Table A-4 unless otherwise noted
VREF = VRH - VRL = 5.12V. Resulting to one 8 bit count = 20mV and one 10 bit count = 5mV
fATDCLK = 2.0MHz
Num C
Rating
Symbol
Min
Typ
Max
Unit
1
P 10-Bit Resolution
LSB
-
5
-
mV
2
P 10-Bit Differential Nonlinearity
DNL
–1
-
1
Counts
3
P 10-Bit Integral Nonlinearity
INL
–2.5
±1.5
2.5
Counts
4
P 10-Bit Absolute Error1
AE
-3
±2.0
3
Counts
5
P 8-Bit Resolution
LSB
-
20
-
mV
6
P 8-Bit Differential Nonlinearity
DNL
–0.5
-
0.5
Counts
7
P 8-Bit Integral Nonlinearity
INL
–1.0
±0.5
1.0
Counts
8
P 8-Bit Absolute Error(1)
AE
-1.5
±1.0
1.5
Counts
NOTES:
1. These values include the quantization error which is inherently 1/2 count for any A/D converter.
For the following definitions see also Figure A-1.
Differential Non-Linearity (DNL) is defined as the difference between two adjacent switching steps.
Vi – Vi – 1
DNL ( i ) = ------------------------ – 1
1LSB
The Integral Non-Linearity (INL) is defined as the sum of all DNLs:
n
INL ( n ) =
∑
i=1
Vn – V0
DNL ( i ) = -------------------- – n
1LSB
97
MC9S12DP512 Device Guide V01.25
DNL
10-Bit Absolute Error Boundary
LSB
Vi-1
Vi
$3FF
8-Bit Absolute Error Boundary
$3FE
$3FD
$3FC
$FF
$3FB
$3FA
$3F9
$3F8
$FE
$3F7
$3F6
$3F4
8-Bit Resolution
10-Bit Resolution
$3F5
$FD
$3F3
9
Ideal Transfer Curve
8
2
7
10-Bit Transfer Curve
6
5
4
1
3
8-Bit Transfer Curve
2
1
0
5
10
15
20
25
30
35
40
45
5055 5060 5065 5070 5075 5080 5085 5090 5095 5100 5105 5110 5115 5120
Vin
mV
Figure A-1 ATD Accuracy Definitions
NOTE:
98
Figure A-1 shows only definitions, for specification values refer to Table A-10.
MC9S12DP512 Device Guide V01.25
A.3 NVM, Flash and EEPROM
NOTE:
Unless otherwise noted the abbreviation NVM (Non Volatile Memory) is used for
both Flash and EEPROM.
A.3.1 NVM timing
The time base for all NVM program or erase operations is derived from the oscillator. A minimum
oscillator frequency fNVMOSC is required for performing program or erase operations. The NVM modules
do not have any means to monitor the frequency and will not prevent program or erase operation at
frequencies above or below the specified minimum. Attempting to program or erase the NVM modules at
a lower frequency a full program or erase transition is not assured.
The Flash and EEPROM program and erase operations are timed using a clock derived from the oscillator
using the FCLKDIV and ECLKDIV registers respectively. The frequency of this clock must be set within
the limits specified as fNVMOP.
The minimum program and erase times shown in Table A-11 are calculated for maximum fNVMOP and
maximum fbus. The maximum times are calculated for minimum fNVMOP and a fbus of 2MHz.
A.3.1.1 Single Word Programming
The programming time for single word programming is dependant on the bus frequency as a well as on
the frequency fNVMOP and can be calculated according to the following formula.
1
1
t swpgm = 9 ⋅ --------------------- + 25 ⋅ ---------f NVMOP
f bus
A.3.1.2 Row Programming
This applies only to the Flash where up to 64 words in a row can be programmed consecutively by keeping
the command pipeline filled. The time to program a consecutive word can be calculated as:
1
1
t bwpgm = 4 ⋅ --------------------- + 9 ⋅ ---------f NVMOP
f bus
The time to program a whole row is:
t brpgm = t swpgm + 63 ⋅ t bwpgm
Row programming is more than 2 times faster than single word programming.
A.3.1.3 Sector Erase
Erasing a 1024 byte Flash sector or a 4 byte EEPROM sector takes:
1
t era ≈ 4000 ⋅ --------------------f NVMOP
99
MC9S12DP512 Device Guide V01.25
The setup time can be ignored for this operation.
A.3.1.4 Mass Erase
Erasing a NVM block takes:
1
t mass ≈ 20000 ⋅ --------------------f NVMOP
The setup time can be ignored for this operation.
A.3.1.5 Blank Check
The time it takes to perform a blank check on the Flash or EEPROM is dependant on the location of the
first non-blank word starting at relative address zero. It takes one bus cycle per word to verify plus a setup
of the command.
t check ≈ location ⋅ t cyc + 10 ⋅ t cyc
Table A-11 NVM Timing Characteristics
Conditions are shown in Table A-4 unless otherwise noted
Num C
Rating
Symbol
Min
Typ
Max
Unit
1
D External Oscillator Clock
fNVMOSC
0.5
-
50 1
MHz
2
D Bus frequency for Programming or Erase Operations
fNVMBUS
1
-
-
MHz
3
D Operating Frequency
fNVMOP
150
-
200
kHz
4
P Single Word Programming Time
tswpgm
46 2
-
74.5 3
µs
5
D Flash Row Programming consecutive word 4
tbwpgm
20.4 (2)
-
31 (3)
µs
6
D Flash Row Programming Time for 64 Words (4)
tbrpgm
1331.2 (2)
-
2027.5 (3)
µs
7
P Sector Erase Time
tera
20 5
-
26.7 (3)
ms
8
P Mass Erase Time
tmass
100 (5)
-
133 (3)
ms
9
D Blank Check Time Flash per block
tcheck
11 6
-
65546 7
tcyc
10
D Blank Check Time EEPROM per block
tcheck
11 (6)
-
2058 (7)
tcyc
NOTES:
1. Restrictions for oscillator in crystal mode apply!
2. Minimum Programming times are achieved under maximum NVM operating frequency fNVMOP and maximum bus frequency
fbus.
3. Maximum Erase and Programming times are achieved under particular combinations of fNVMOP and bus frequency fbus.
Refer to formulae in Sections Section A.3.1.1 Single Word Programming- Section A.3.1.4 Mass Erasefor guidance.
4. Row Programming operations are not applicable to EEPROM
5. Minimum Erase times are achieved under maximum NVM operating frequency fNVMOP.
6. Minimum time, if first word in the array is not blank
7. Maximum time to complete check on an erased block
100
MC9S12DP512 Device Guide V01.25
A.3.2 NVM Reliability
The reliability of the NVM blocks is guaranteed by stress test during qualification, constant process
monitors and burn-in to screen early life failures.
The program/erase cycle count on the sector is incremented every time a sector or mass erase event is
executed
Table A-12 NVM Reliability Characteristics1
Conditions are shown in Table A-4 unless otherwise noted
Num C
Rating
Symbol
Min
Typ
Max
15
1002
—
Unit
Flash Reliability Characteristics
Data retention after 10,000 program/erase cycles at
an average junction temperature of TJavg ≤ 85°C
1
C
2
Data retention with <100 program/erase cycles at an
C
average junction temperature TJavg ≤ 85°C
3
C
4
Number of program/erase cycles
C
(0°C ≤ TJ ≤ 140°C)
Number of program/erase cycles
(–40°C ≤ TJ ≤ 0°C)
tFLRET
Years
20
1002
—
10,000
—
—
10,000
100,0003
—
1002
—
nFL
Cycles
EEPROM Reliability Characteristics
5
Data retention after up to 100,000 program/erase
C cycles at an average junction temperature of
TJavg ≤ 85°C
6
Data retention with <100 program/erase cycles at an
C
average junction temperature TJavg ≤ 85°C
7
C
8
Number of program/erase cycles
C
(0°C < TJ ≤ 140°C)
Number of program/erase cycles
(–40°C ≤ TJ ≤ 0°C)
15
tEEPRET
Years
20
1002
—
10,000
—
—
100,000
300,0003
nEEP
Cycles
—
NOTES:
1. TJavg will not exeed 85°C considering a typical temperature profile over the lifetime of a consumer, industrial or automotive
application.
2. Typical data retention values are based on intrinsic capability of the technology measured at high temperature and de-rated
to 25°C using the Arrhenius equation. For additional information on how Freescale defines Typical Data Retention, please
refer to Engineering Bulletin EB618.
3. Spec table quotes typical endurance evaluated at 25°C for this product family, typical endurance at various temperature can
be estimated using the graph below. For additional information on how Freescale defines Typical Endurance, please refer
to Engineering Bulletin EB619.
101
MC9S12DP512 Device Guide V01.25
Figure A-2 Typical Endurance vs Temperature
500
Typical Endurance [103 Cycles]
450
400
350
300
250
200
150
100
50
0
-40
-20
0
20
40
60
80
Operating Temperature TJ [°C]
------ Flash
------ EEPROM
102
100
120
140
MC9S12DP512 Device Guide V01.25
A.4 Voltage Regulator
The on-chip voltage regulator is intended to supply the internal logic and oscillator circuits. No external
DC load is allowed.
Table A-13 Voltage Regulator Recommended Load Capacitances
Rating
Symbol
Min
Typ
Max
Unit
Load Capacitance on VDD1, 2
CLVDD
-
220
-
nF
Load Capacitance on VDDPLL
CLVDDfcPLL
-
220
-
nF
103
MC9S12DP512 Device Guide V01.25
104
MC9S12DP512 Device Guide V01.25
A.5 Reset, Oscillator and PLL
This section summarizes the electrical characteristics of the various startup scenarios for Oscillator and
Phase-Locked-Loop (PLL).
A.5.1 Startup
Table A-14 summarizes several startup characteristics explained in this section. Detailed description of
the startup behavior can be found in the Clock and Reset Generator (CRG) Block Guide.
Table A-14 Startup Characteristics
Conditions are shown in Table A-4 unless otherwise noted
Num C
Rating
Symbol
Min
Typ
Max
Unit
1
T POR release level
VPORR
-
-
2.07
V
2
T POR assert level
VPORA
0.97
-
-
V
3
D Reset input pulse width, minimum input time
PWRSTL
2
-
-
tosc
4
D Startup from Reset
nRST
192
-
196
nosc
5
D Interrupt pulse width, IRQ edge-sensitive mode
PWIRQ
20
-
-
ns
6
D Wait recovery startup time
tWRS
-
-
14
tcyc
A.5.1.1 POR
The release level VPORR and the assert level VPORA are derived from the VDD Supply. They are also valid
if the device is powered externally. After releasing the POR reset the oscillator and the clock quality check
are started. If after a time tCQOUT no valid oscillation is detected, the MCU will start using the internal self
clock. The fastest startup time possible is given by nuposc.
A.5.1.2 SRAM Data Retention
Provided an appropriate external reset signal is applied to the MCU, preventing the CPU from executing
code when VDD5 is out of specification limits, the SRAM contents integrity is guaranteed if after the reset
the PORF bit in the CRG Flags Register has not been set.
A.5.1.3 External Reset
When external reset is asserted for a time greater than PWRSTL the CRG module generates an internal
reset, and the CPU starts fetching the reset vector without doing a clock quality check, if there was an
oscillation before reset.
A.5.1.4 Stop Recovery
Out of STOP the controller can be woken up by an external interrupt. A clock quality check as after POR
is performed before releasing the clocks to the system.
105
MC9S12DP512 Device Guide V01.25
A.5.1.5 Pseudo Stop and Wait Recovery
The recovery from Pseudo STOP and Wait are essentially the same since the oscillator was not stopped in
both modes. The controller can be woken up by internal or external interrupts. After twrs the CPU starts
fetching the interrupt vector.
A.5.2 Oscillator
The device features an internal Colpitts and Pierce oscillator. The selection of Colpitts oscillator or Pierce
oscillator/external clock depends on the XCLKS signal which is sampled during reset. Pierce
oscillator/external clock mode allows the input of a square wave. Before asserting the oscillator to the
internal system clocks the quality of the oscillation is checked for each start from either power-on, STOP
or oscillator fail. tCQOUT specifies the maximum time before switching to the internal self clock mode after
POR or STOP if a proper oscillation is not detected. The quality check also determines the minimum
oscillator start-up time tUPOSC . The device also features a clock monitor. A Clock Monitor Failure is
asserted if the frequency of the incoming clock signal is below the Assert Frequency fCMFA.
Table A-15 Oscillator Characteristics
Conditions are shown in Table A-4 unless otherwise noted
Num C
Rating
Symbol
Min
Typ
Max
Unit
1a
C Crystal oscillator range (Colpitts)
fOSC
0.5
-
16
MHz
1b
C Crystal oscillator range (Pierce) 1
fOSC
0.5
-
40
MHz
2
P Startup Current
iOSC
100
-
-
µA
3
C Oscillator start-up time (Colpitts)
tUPOSC
-
82
1003
ms
4
D Clock Quality check time-out
tCQOUT
0.45
-
2.5
s
5
P Clock Monitor Failure Assert Frequency
fCMFA
50
100
200
KHz
6
P External square wave input frequency 4
fEXT
0.5
-
50
MHz
7
D External square wave pulse width low 4
tEXTL
9.5
-
-
ns
8
D External square wave pulse width high 4
tEXTH
9.5
-
-
ns
9
D External square wave rise time 4
tEXTR
-
-
1
ns
10
D External square wave fall time 4
tEXTF
-
-
1
ns
11
D Input Capacitance (EXTAL, XTAL pins)
CIN
-
7
-
pF
12
C
VDCBIAS
-
1.1
-
V
13
P EXTAL Pin Input High Voltage 4
VIH,EXTAL
0.75*VDDPLL
-
-
V
T EXTAL Pin Input High Voltage 4
VIH,EXTAL
-
-
VDDPLL + 0.3
V
P EXTAL Pin Input Low Voltage 4
VIL,EXTAL
-
-
0.25*VSSPLL
V
T EXTAL Pin Input Low Voltage 4
VIL,EXTAL
VSSPLL - 0.3
-
-
V
C EXTAL Pin Input Hysteresis 4
VHYS,EXTAL
-
250
-
mV
14
15
106
DC Operating Bias in Colpitts Configuration on
EXTAL Pin
MC9S12DP512 Device Guide V01.25
NOTES:
1. Depending on the crystal a damping series resistor might be necessary
2. fosc = 4MHz, C = 22pF.
3. Maximum value is for extreme cases using high Q, low frequency crystals
4. Only valid if Pierce oscillator/external clock mode is selected
A.5.3 Phase Locked Loop
The oscillator provides the reference clock for the PLL. The PLL´s Voltage Controlled Oscillator (VCO)
is also the system clock source in self clock mode.
A.5.3.1 XFC Component Selection
This section describes the selection of the XFC components to achieve a good filter characteristics.
Cp
VDDPLL
Cs
fosc
1
refdv+1
fref
∆
fcmp
R
Phase
XFC Pin
KΦ
KV
VCO
fvco
Detector
Loop Divider
1
synr+1
1
2
Figure A-3 Basic PLL functional diagram
The following procedure can be used to calculate the resistance and capacitance values using typical
values for K1, f1 and ich from Table A-16.
The grey boxes show the calculation for fVCO = 50MHz and fref = 1MHz. E.g., these frequencies are used
for fOSC = 4MHz and a 25MHz bus clock.
The VCO Gain at the desired VCO frequency is approximated by:
KV = K1 ⋅ e
( f 1 – f vco )
----------------------K 1 ⋅ 1V
= – 100 ⋅ e
( 60 – 50 )
-----------------------– 100
= -90.48MHz/V
107
MC9S12DP512 Device Guide V01.25
The phase detector relationship is given by:
K Φ = – i ch ⋅ K V
= 316.7Hz/Ω
ich is the current in tracking mode.
The loop bandwidth fC should be chosen to fulfill the Gardner’s stability criteria by at least a factor of 10,
typical values are 50. ζ = 0.9 ensures a good transient response.
2 ⋅ ζ ⋅ f ref
f ref
1
f C < ------------------------------------------ ------ → f C < -------------- ;( ζ = 0.9 )
4 ⋅ 10
2 10
π ⋅ ⎛ζ + 1 + ζ ⎞
fC < 25kHz
⎝
⎠
And finally the frequency relationship is defined as
f VCO
n = ------------- = 2 ⋅ ( synr + 1 )
f ref
= 50
With the above values the resistance can be calculated. The example is shown for a loop bandwidth
fC=10kHz:
2 ⋅ π ⋅ n ⋅ fC
R = ----------------------------- = 2*π*50*10kHz/(316.7Hz/Ω)=9.9kΩ=~10kΩ
KΦ
The capacitance Cs can now be calculated as:
2
0.516
2⋅ζ
C s = ---------------------- ≈ --------------- ;( ζ = 0.9 ) = 5.19nF =~ 4.7nF
π ⋅ fC ⋅ R fC ⋅ R
The capacitance Cp should be chosen in the range of:
C s ⁄ 20 ≤ C p ≤ C s ⁄ 10
Cp = 470pF
A.5.3.2 Jitter Information
The basic functionality of the PLL is shown in Figure A-3. With each transition of the clock fcmp, the
deviation from the reference clock fref is measured and input voltage to the VCO is adjusted
accordingly.The adjustment is done continuously with no abrupt changes in the clock output frequency.
Noise, voltage, temperature and other factors cause slight variations in the control loop resulting in a clock
jitter. This jitter affects the real minimum and maximum clock periods as illustrated in Figure A-4.
108
MC9S12DP512 Device Guide V01.25
1
0
2
3
N-1
N
tmin1
tnom
tmax1
tminN
tmaxN
Figure A-4 Jitter Definitions
The relative deviation of tnom is at its maximum for one clock period, and decreases towards zero for larger
number of clock periods (N).
Defining the jitter as:
t min ( N ) ⎞
t max ( N )
⎛
J ( N ) = max ⎜ 1 – --------------------- , 1 – --------------------- ⎟
N ⋅ t nom
N ⋅ t nom ⎠
⎝
For N < 100, the following equation is a good fit for the maximum jitter:
j1
J ( N ) = -------- + j 2
N
J(N)
1
5
10
20
N
Figure A-5 Maximum bus clock jitter approximation
109
MC9S12DP512 Device Guide V01.25
This is very important to notice with respect to timers, serial modules where a pre-scaler will eliminate the
effect of the jitter to a large extent.
Table A-16 PLL Characteristics
Conditions are shown in Table A-4 unless otherwise noted
Num C
Rating
Symbol
Min
Typ
Max
Unit
1
P Self Clock Mode frequency
fSCM
1
-
5.5
MHz
2
D VCO locking range
fVCO
8
-
50
MHz
3
D
|∆trk|
3
-
4
%1
4
D Lock Detection
|∆Lock|
0
-
1.5
%(1)
5
D Un-Lock Detection
|∆unl|
0.5
-
2.5
%(1)
6
D
|∆unt|
6
-
8
%(1)
7
C PLLON Total Stabilization delay (Auto Mode) 2
tstab
-
0.5
-
ms
8
D PLLON Acquisition mode stabilization delay (2)
tacq
-
0.3
-
ms
9
D PLLON Tracking mode stabilization delay (2)
tal
-
0.2
-
ms
10
D Fitting parameter VCO loop gain
K1
-
-100
-
MHz/V
11
D Fitting parameter VCO loop frequency
f1
-
60
-
MHz
12
D Charge pump current acquisition mode
| ich |
-
38.5
-
µA
13
D Charge pump current tracking mode
| ich |
-
3.5
-
µA
14
C Jitter fit parameter 1(2)
j1
-
-
1.1
%
15
C Jitter fit parameter 2(2)
j2
-
-
0.13
%
Lock Detector transition from Acquisition to Tracking
mode
Lock Detector transition from Tracking to Acquisition
mode
NOTES:
1. % deviation from target frequency
2. fOSC = 4MHz, fBUS = 25MHz equivalent fVCO = 50MHz: REFDV = #$03, SYNR = #$018, Cs = 4.7nF, Cp = 470pF, Rs =
10KΩ.
110
MC9S12DP512 Device Guide V01.25
A.6 MSCAN
Table A-17 MSCAN Wake-up Pulse Characteristics
Conditions are shown in Table A-4 unless otherwise noted
Num C
Rating
Symbol
Min
Typ
Max
Unit
1
P MSCAN Wake-up dominant pulse filtered
tWUP
-
-
2
µs
2
P MSCAN Wake-up dominant pulse pass
tWUP
5
-
-
µs
111
MC9S12DP512 Device Guide V01.25
112
MC9S12DP512 Device Guide V01.25
A.7 SPI
This section provides electrical parametrics and ratings for the SPI.
In Table A-18 the measurement conditions are listed.
Table A-18 Measurement Conditions
Description
Value
Unit
full drive mode
—
50
pF
(20% / 80%) VDDX
V
Drive mode
Load capacitance CLOAD,
on all outputs
Thresholds for delay
measurement points
A.7.1 Master Mode
In Figure A-6 the timing diagram for master mode with transmission format CPHA=0 is depicted.
SS1
(OUTPUT)
2
1
SCK
(CPOL = 0)
(OUTPUT)
13
12
13
3
4
SCK
(CPOL = 1)
(OUTPUT)
5
MISO
(INPUT)
6
MSB IN2
10
MOSI
(OUTPUT)
12
4
BIT 6 . . . 1
LSB IN
9
MSB OUT2
BIT 6 . . . 1
11
LSB OUT
1.if configured as an output.
2. LSBF = 0. For LSBF = 1, bit order is LSB, bit 1, ..., bit 6, MSB.
Figure A-6 SPI Master Timing (CPHA=0)
In Figure A-7 the timing diagram for master mode with transmission format CPHA=1 is depicted.
113
MC9S12DP512 Device Guide V01.25
SS1
(OUTPUT)
1
2
12
13
12
13
3
SCK
(CPOL = 0)
(OUTPUT)
4
4
SCK
(CPOL = 1)
(OUTPUT)
5
MISO
(INPUT)
6
MSB IN2
BIT 6 . . . 1
LSB IN
11
9
MOSI
(OUTPUT) PORT DATA
MASTER MSB OUT2
BIT 6 . . . 1
MASTER LSB OUT
PORT DATA
1.If configured as output
2. LSBF = 0. For LSBF = 1, bit order is LSB, bit 1, ..., bit 6, MSB.
Figure A-7 SPI Master Timing (CPHA=1)
In Table A-19 the timing characteristics for master mode are listed.
Table A-19 SPI Master Mode Timing Characteristics
Num
Characteristic
Symbol
Min
Typ
Max
Unit
1
SCK Frequency
fsck
1/2048
—
1/2
fbus
1
SCK Period
tsck
2
—
2048
tbus
2
Enable Lead Time
tlead
—
1/2
—
tsck
3
Enable Lag Time
tlag
—
1/2
—
tsck
4
Clock (SCK) High or Low Time
twsck
—
1/2
—
tsck
5
Data Setup Time (Inputs)
tsu
8
—
—
ns
6
Data Hold Time (Inputs)
thi
8
—
—
ns
9
Data Valid after SCK Edge
tvsck
—
—
30
ns
10
Data Valid after SS fall (CPHA=0)
tvss
—
—
15
ns
11
Data Hold Time (Outputs)
tho
20
—
—
ns
Rise and Fall Time Inputs
trfi
—
—
8
ns
Rise and Fall Time Outputs
trfo
—
—
8
ns
12
13
114
MC9S12DP512 Device Guide V01.25
A.7.2 Slave Mode
In Figure A-8 the timing diagram for slave mode with transmission format CPHA=0 is depicted.
SS
(INPUT)
1
12
13
12
13
3
SCK
(CPOL = 0)
(INPUT)
4
2
4
SCK
(CPOL = 1)
(INPUT) 10
8
7
MISO
(OUTPUT)
9
see
note
SLAVE MSB
5
MOSI
(INPUT)
BIT 6 . . . 1
11
11
SLAVE LSB OUT
SEE
NOTE
6
MSB IN
BIT 6 . . . 1
LSB IN
NOTE: Not defined!
Figure A-8 SPI Slave Timing (CPHA=0)
In Figure A-9 the timing diagram for slave mode with transmission format CPHA=1 is depicted.
115
MC9S12DP512 Device Guide V01.25
SS
(INPUT)
3
1
2
12
13
12
13
SCK
(CPOL = 0)
(INPUT)
4
4
SCK
(CPOL = 1)
(INPUT)
see
note
SLAVE
7
5
MOSI
(INPUT)
8
11
9
MISO
(OUTPUT)
MSB OUT
BIT 6 . . . 1
SLAVE LSB OUT
BIT 6 . . . 1
LSB IN
6
MSB IN
NOTE: Not defined!
Figure A-9 SPI Slave Timing (CPHA=1)
In Table A-20 the timing characteristics for slave mode are listed.
Table A-20 SPI Slave Mode Timing Characteristics
Num
Characteristic
Symbol
Min
Typ
Max
Unit
1
SCK Frequency
fsck
DC
—
1/4
fbus
1
SCK Period
tsck
4
—
∞
tbus
2
Enable Lead Time
tlead
4
—
—
tbus
3
Enable Lag Time
tlag
4
—
—
tbus
4
Clock (SCK) High or Low Time
twsck
4
—
—
tbus
5
Data Setup Time (Inputs)
tsu
8
—
—
ns
6
Data Hold Time (Inputs)
thi
8
—
—
ns
Slave Access Time (time to data active)
ta
—
—
20
ns
Slave MISO Disable Time
tdis
—
—
22
7
8
9
Data Valid after SCK Edge
tvsck
—
—
ns
30 + tbus
1
ns
1
ns
10
Data Valid after SS fall
tvss
—
—
30 + tbus
11
Data Hold Time (Outputs)
tho
20
—
—
ns
12
Rise and Fall Time Inputs
trfi
—
—
8
ns
13
Rise and Fall Time Outputs
trfo
—
—
8
ns
NOTES:
1. tbus added due to internal synchronization delay
116
MC9S12DP512 Device Guide V01.25
A.8 External Bus Timing
A timing diagram of the external multiplexed-bus is illustrated in Figure A-10 with the actual timing
values shown on table Table A-21. All major bus signals are included in the diagram. While both a data
write and data read cycle are shown, only one or the other would occur on a particular bus cycle.
A.8.1 General Muxed Bus Timing
The expanded bus timings are highly dependent on the load conditions. The timing parameters shown
assume a balanced load across all outputs.
117
MC9S12DP512 Device Guide V01.25
1, 2
3
4
ECLK
PE4
5
9
Addr/Data
(read)
PA, PB
6
data
16
15
7
data
8
14
13
data
addr
17
11
data
addr
12
Addr/Data
(write)
PA, PB
10
19
18
Non-Multiplexed
Addresses
PK5:0
20
21
22
23
ECS
PK7
24
25
26
27
28
29
30
31
32
33
34
R/W
PE2
LSTRB
PE3
NOACC
PE7
35
36
IPIPE0
IPIPE1, PE6,5
Figure A-10 General External Bus Timing
118
MC9S12DP512 Device Guide V01.25
Table A-21 Expanded Bus Timing Characteristics
Conditions are shown in Table A-4 unless otherwise noted, CLOAD = 50pF
Num C
Rating
Symbol
Min
Typ
Max
Unit
1
P Frequency of operation (E-clock)
fo
0
-
25.0
MHz
2
P Cycle time
tcyc
40
-
-
ns
3
D Pulse width, E low
PWEL
19
-
-
ns
4
D Pulse width, E high1
PWEH
19
-
-
ns
5
D Address delay time
tAD
-
-
8
ns
6
D Address valid time to E rise (PWEL–tAD)
tAV
11
-
-
ns
7
D Muxed address hold time
tMAH
2
-
-
ns
8
D Address hold to data valid
tAHDS
7
-
-
ns
9
D Data hold to address
tDHA
2
-
-
ns
10
D Read data setup time
tDSR
13
-
-
ns
11
D Read data hold time
tDHR
0
-
-
ns
12
D Write data delay time
tDDW
-
-
7
ns
13
D Write data hold time
tDHW
2
-
-
ns
14
D Write data setup time(1) (PWEH–tDDW)
tDSW
12
-
-
ns
15
D Address access time(1) (tcyc–tAD–tDSR)
tACCA
19
-
-
ns
16
D E high access time(1) (PWEH–tDSR)
tACCE
6
-
-
ns
17
D Non-multiplexed address delay time
tNAD
-
-
6
ns
18
D Non-muxed address valid to E rise (PWEL–tNAD)
tNAV
13
-
-
ns
19
D Non-multiplexed address hold time
tNAH
2
-
-
ns
20
D Chip select delay time
tCSD
-
-
16
ns
21
D Chip select access time(1) (tcyc–tCSD–tDSR)
tACCS
11
-
-
ns
22
D Chip select hold time
tCSH
2
-
-
ns
23
D Chip select negated time
tCSN
8
-
-
ns
24
D Read/write delay time
tRWD
-
-
7
ns
25
D Read/write valid time to E rise (PWEL–tRWD)
tRWV
14
-
-
ns
26
D Read/write hold time
tRWH
2
-
-
ns
27
D Low strobe delay time
tLSD
-
-
7
ns
28
D Low strobe valid time to E rise (PWEL–tLSD)
tLSV
14
-
-
ns
29
D Low strobe hold time
tLSH
2
-
-
ns
30
D NOACC strobe delay time
tNOD
-
-
7
ns
31
D NOACC valid time to E rise (PWEL–tNOD)
tNOV
14
-
-
ns
119
MC9S12DP512 Device Guide V01.25
Table A-21 Expanded Bus Timing Characteristics
Conditions are shown in Table A-4 unless otherwise noted, CLOAD = 50pF
Num C
Rating
Symbol
Min
Typ
Max
Unit
32
D NOACC hold time
tNOH
2
-
-
ns
33
D IPIPE[1:0] delay time
tP0D
2
-
7
ns
34
D IPIPE[1:0] valid time to E rise (PWEL–tP0D)
tP0V
11
-
-
ns
35
D IPIPE[1:0] delay time(1) (PWEH-tP1V)
tP1D
2
-
7
ns
36
D IPIPE[1:0] valid time to E fall
tP1V
11
-
-
ns
NOTES:
1. Affected by clock stretch: add N x tcyc where N=0,1,2 or 3, depending on the number of clock stretches.
120
MC9S12DP512 Device Guide V01.25
Appendix B Package Information
B.1 General
This section provides the physical dimensions of the MC9S12DP512 packages.
121
MC9S12DP512 Device Guide V01.25
B.2 112-pin LQFP package
0.20 T L-M N
4X
PIN 1
IDENT
0.20 T L-M N
4X 28 TIPS
112
J1
85
4X
P
J1
1
CL
84
VIEW Y
108X
G
X
X=L, M OR N
VIEW Y
B
L
V
M
B1
28
57
29
F
D
56
SECTION J1-J1
ROTATED 90 ° COUNTERCLOCKWISE
A1
S1
A
S
C2
VIEW AB
θ2
0.050
0.10 T
112X
SEATING
PLANE
θ3
T
θ
R R2
0.25
R R1
GAGE PLANE
(K)
C1
E
(Y)
(Z)
VIEW AB
θ1
NOTES:
1. DIMENSIONING AND TOLERANCING PER
ASME Y14.5M, 1994.
2. DIMENSIONS IN MILLIMETERS.
3. DATUMS L, M AND N TO BE DETERMINED AT
SEATING PLANE, DATUM T.
4. DIMENSIONS S AND V TO BE DETERMINED AT
SEATING PLANE, DATUM T.
5. DIMENSIONS A AND B DO NOT INCLUDE
MOLD PROTRUSION. ALLOWABLE
PROTRUSION IS 0.25 PER SIDE. DIMENSIONS
A AND B INCLUDE MOLD MISMATCH.
6. DIMENSION D DOES NOT INCLUDE DAMBAR
PROTRUSION. ALLOWABLE DAMBAR
PROTRUSION SHALL NOT CAUSE THE D
DIMENSION TO EXCEED 0.46.
DIM
A
A1
B
B1
C
C1
C2
D
E
F
G
J
K
P
R1
R2
S
S1
V
V1
Y
Z
AA
θ
θ1
θ2
θ3
MILLIMETERS
MIN
MAX
20.000 BSC
10.000 BSC
20.000 BSC
10.000 BSC
--1.600
0.050
0.150
1.350
1.450
0.270
0.370
0.450
0.750
0.270
0.330
0.650 BSC
0.090
0.170
0.500 REF
0.325 BSC
0.100
0.200
0.100
0.200
22.000 BSC
11.000 BSC
22.000 BSC
11.000 BSC
0.250 REF
1.000 REF
0.090
0.160
8 °
0°
7 °
3 °
13
°
11 °
11 °
13 °
Figure B-1 112-pin LQFP mechanical dimensions (case no. 987)
122
BASE
METAL
0.13 M T L-M N
N
C
AA
J
V1
MC9S12DP512 Device Guide V01.25
User Guide End Sheet
123
MC9S12DP512 Device Guide V01.25
FINAL PAGE OF
124
PAGES
124
DOCUMENT NUMBER
S12ATD10B8CV2/D
ATD_10B8C
Block User Guide
V02.12
Original Release Date: 27 OCT 2000
Revised: 28 June 2005
Motorola Inc.
Motorola reserves the right to make changes without further notice to any products herein to improve reliability, function or
design. Motorola does not assume any liability arising out of the application or use of any product or circuit described herein;
neither does it convey any license under its patent rights nor the rights of others. Motorola products are not designed, intended,
or authorized for use as components in systems intended for surgical implant into the body, or other applications intended to
support or sustain life, or for any other application in which the failure of the Motorola product could create a situation where
personal injury or death may occur. Should Buyer purchase or use Motorola products for any such unintended or unauthorized
application, Buyer shall indemnify and hold Motorola and its officers, employees, subsidiaries, affiliates, and distributors harmless
against all claims, costs, damages, and expenses, and reasonable attorney fees arising out of, directly or indirectly, any claim of
personal injury or death associated with such unintended or unauthorized use, even if such claim alleges that Motorola was
negligent regarding the design or manufacture of the part.
1
ATD_10B8C Block User Guide — V02.12
Revision History
Version
Number
Revision
Date
Effective
Date
00.00
27-10-2000
-
Initial SRS2 release.
01.00
06-06-2001
-
Updated the description of ATDDIEN and PORTAD1 register.
-
Made SRS2 Compliant
Author
Description of Changes
01.10
16-06-2001
V02.00
20 June 2001 20 June 2001
Reworked whole document to make it more user friendly
V02.01
26 July 2001
-
Added document names
Variable definitions and names have been hidden
V02.02
5 Sept 2001
5 Sept 2001
Corrected sampling phase description, other minor corrections
V02.03
8 Nov 2001
8 Nov 2001
Corrected AWAI bit description
V02.04
16 Jan 2002
16 Jan 2002
Syntax corrections
V02.05
8 Mar 2002
8 Mar 2002
Removed document number from all pages except cover sheet
V02.06
11 Apr 2002
11 Apr 2002
Documented special channel conversion in ATDTEST1 register
V02.07
22 Apr 2002
22 Apr 2002
Corrected Table "Available Result Data Formats"
V02.08
16 Aug 2002
16 Aug 2002
FIFOR flag: corrected clearing mechanism B)
V02.09
23 Aug 2002
23 Aug 2002
Detailed AWAI Bit description.
Functional Description: Detailed and corrected Low power
modes
Table "Available Result Data Formats": Re-corrected
V02.10
21 Feb 2003
21 Feb 2003
Formal corrections on ATDTEST0/1 and ATDDRHx/ATDDRLx
register descriptions
V02.11
24 Mar 2005
24 Mar 2005
Corrected PAD7-0 port description
V02.12
28 June 2005 28 June 2005
Enhanced FIFO bit description
Table 0-1 Revision History
2
ATD_10B8C Block User Guide — V02.12
Table of Contents
Section 1 Introduction
1.1
1.2
1.3
1.3.1
1.3.2
1.4
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9
Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9
Modes of Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9
Conversion modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9
MCU Operating Modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9
Block Diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .10
Section 2 Signal Description
2.1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
2.2
Detailed Signal Descriptions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
2.2.1
AN7 / ETRIG / PAD7 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
2.2.2
AN6 / PAD6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
2.2.3
AN5 / PAD5 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
2.2.4
AN4 / PAD4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
2.2.5
AN3 / PAD3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
2.2.6
AN2 / PAD2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
2.2.7
AN1 / PAD1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
2.2.8
AN0 / PAD0 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
2.2.9
VRH, VRL. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .12
2.2.10 VDDA, VSSA . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .12
Section 3 Memory Map and Register Definition
3.1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .13
3.2
Module Memory Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .13
3.3
Register Descriptions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .14
3.3.1
Reserved Register (ATDCTL0) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .14
3.3.2
Reserved Register (ATDCTL1) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .14
3.3.3
ATD Control Register 2 (ATDCTL2). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .14
3.3.4
ATD Control Register 3 (ATDCTL3). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .16
3.3.5
ATD Control Register 4 (ATDCTL4). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .18
3.3.6
ATD Control Register 5 (ATDCTL5). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .20
3.3.7
ATD Status Register 0 (ATDSTAT0) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .23
3
ATD_10B8C Block User Guide — V02.12
3.3.8
3.3.9
3.3.10
3.3.11
3.3.12
3.3.13
Reserved Register (ATDTEST0) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .24
ATD Test Register 1 (ATDTEST1). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .24
ATD Status Register 1 (ATDSTAT1) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .25
ATD Input Enable Register (ATDDIEN) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .26
Port Data Register (PORTAD) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .27
ATD Conversion Result Registers (ATDDRHx/ATDDRLx) . . . . . . . . . . . . . . . . . . . .27
Section 4 Functional Description
4.1
General. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31
4.2
Analog Sub-block . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31
4.2.1
Sample and Hold Machine . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31
4.2.2
Analog Input Multiplexer. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31
4.2.3
Sample Buffer Amplifier . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31
4.2.4
Analog-to-Digital (A/D) Machine. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31
4.3
Digital Sub-block. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .32
4.3.1
External Trigger Input (ETRIG) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .32
4.3.2
General Purpose Digital Input Port Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .33
4.3.3
Low Power Modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .33
Section 5 Resets
5.1
General. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .35
Section 6 Interrupts
6.1
General. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .37
4
ATD_10B8C Block User Guide — V02.12
List of Figures
Figure 1-1
Figure 3-1
Figure 3-2
Figure 3-3
Figure 3-4
Figure 3-5
Figure 3-6
Figure 3-7
Figure 3-8
Figure 3-9
Figure 3-10
Figure 3-11
Figure 3-12
Figure 3-13
Figure 3-14
Figure 3-15
Figure 3-16
ATD_10B8C Block Diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .10
Reserved Register (ATDCTL0) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .14
Reserved Register (ATDCTL1) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .14
ATD Control Register 2 (ATDCTL2) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .15
ATD Control Register 3 (ATDCTL3) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .16
ATD Control Register 4 (ATDCTL4) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .18
ATD Control Register 5 (ATDCTL5) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
ATD Status Register 0 (ATDSTAT0) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .23
Reserved Register (ATDTEST0) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .24
ATD Test Register 1 (ATDTEST1) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .25
ATD Status Register 1 (ATDSTAT1) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .26
ATD Input Enable Register (ATDDIEN). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .26
Port Data Register (PORTAD). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .27
Left Justified, ATD Conversion Result Register, High Byte (ATDDRxH). . . . . . .28
Left Justified, ATD Conversion Result Register, Low Byte (ATDDRxL) . . . . . . .28
Right Justified, ATD Conversion Result Register, High Byte (ATDDRxH) . . . . .28
Right Justified, ATD Conversion Result Register, Low Byte (ATDDRxL) . . . . . .29
5
ATD_10B8C Block User Guide — V02.12
.
6
ATD_10B8C Block User Guide — V02.12
List of Tables
Table 0-1 Revision History . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2
Table 3-1 Module Memory Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .13
Table 3-2 External Trigger Configurations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .16
Table 3-3 Conversion Sequence Length Coding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .17
Table 3-4 ATD Behavior in Freeze Mode (breakpoint) . . . . . . . . . . . . . . . . . . . . . . . . . . . . .18
Table 3-5 Sample Time Select. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .19
Table 3-6 Clock Prescaler Values . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .20
Table 3-7 Available Result Data Formats . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
Table 3-8 Left Justified, Signed and Unsigned ATD Output Codes. . . . . . . . . . . . . . . . . . . .22
Table 3-9 Analog Input Channel Select Coding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .22
Table 3-10 Special Channel Select Coding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .25
Table 4-1 External Trigger Control Bits . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .32
Table 6-1 ATD_10B8C Interrupt Vectors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .37
7
ATD_10B8C Block User Guide — V02.12
.
8
ATD_10B8C Block User Guide — V02.12
Section 1 Introduction
1.1 Overview
The ATD_10B8C is an 8-channel, 10-bit, multiplexed input successive approximation analog-to-digital
converter. Refer to device electrical specifications for ATD accuracy.
The block is designed to be upwards compatible with the 68HC11 standard 8-bit A/D converter. In
addition, there are new operating modes that are unique to the HC12 design.
1.2 Features
•
8/10 Bit Resolution.
•
7 µsec, 10-Bit Single Conversion Time.
•
Sample Buffer Amplifier.
•
Programmable Sample Time.
•
Left/Right Justified, Signed/Unsigned Result Data.
•
External Trigger Control.
•
Conversion Completion Interrupt Generation.
•
Analog Input Multiplexer for 8 Analog Input Channels.
•
Analog/Digital Input Pin Multiplexing.
•
1 to 8 Conversion Sequence Lengths.
•
Continuous Conversion Mode.
•
Multiple Channel Scans.
1.3 Modes of Operation
1.3.1 Conversion modes
There is software programmable selection between performing single or continuous conversion on a
single channel or multiple channels.
1.3.2 MCU Operating Modes
•
Stop Mode
Entering Stop Mode causes all clocks to halt and thus the system is placed in a minimum power
standby mode. This aborts any conversion sequence in progress. During recovery from Stop Mode,
there must be a minimum delay for the Stop Recovery Time tSR before initiating a new ATD
conversion sequence.
9
ATD_10B8C Block User Guide — V02.12
•
Wait Mode
Entering Wait Mode the ATD conversion either continues or aborts for low power depending on
the logical value of the AWAIT bit.
•
Freeze Mode
In Freeze Mode the ATD_10B8C will behave according to the logical values of the FRZ1 and FRZ0
bits. This is useful for debugging and emulation.
1.4 Block Diagram
ATD_10B8C
Bus Clock
ATD clock
Clock
Prescaler
Conversion
Complete Interrupt
Mode and Timing Control
Results
VRH
VRL
VDDA
VSSA
ATD 0
ATD 1
ATD 2
ATD 3
ATD 4
ATD 5
ATD 6
ATD 7
Successive
Approximation
Register (SAR)
and DAC
AN7 / PAD7
AN6 / PAD6
AN5 / PAD5
AN4 / PAD4
AN3 / PAD3
AN2 / PAD2
AN1 / PAD1
AN0 / PAD0
+
Sample & Hold
1
1
Comparator
Analog
MUX
ATD Input Enable Register
Port AD Data Register
Figure 1-1 ATD_10B8C Block Diagram
10
ATD_10B8C Block User Guide — V02.12
Section 2 Signal Description
2.1 Overview
The ATD_10B8C has a total of 12 external pins.
2.2 Detailed Signal Descriptions
2.2.1 AN7 / ETRIG / PAD7
This pin serves as the analog input Channel 7. It can be configured to provide an external trigger for the
ATD conversion. It can be configured as digital port pin.
2.2.2 AN6 / PAD6
This pin serves as the analog input Channel 6. It can be configured as digital port pin.
2.2.3 AN5 / PAD5
This pin serves as the analog input Channel 5. It can be configured as digital port pin.
2.2.4 AN4 / PAD4
This pin serves as the analog input Channel 4. It can be configured as digital port pin.
2.2.5 AN3 / PAD3
This pin serves as the analog input Channel 3. It can be configured as digital port pin.
2.2.6 AN2 / PAD2
This pin serves as the analog input Channel 2. It can be configured as digital port pin.
2.2.7 AN1 / PAD1
This pin serves as the analog input Channel 1. It can be configured as digital port pin.
2.2.8 AN0 / PAD0
This pin serves as the analog input Channel 0. It can be configured as digital port pin.
11
ATD_10B8C Block User Guide — V02.12
2.2.9 VRH, VRL
VRH is the high reference voltage and VRL is the low reference voltage for ATD conversion.
2.2.10 VDDA, VSSA
These pins are the power supplies for the analog circuitry of the ATD_10B8C block.
12
ATD_10B8C Block User Guide — V02.12
Section 3 Memory Map and Register Definition
3.1 Overview
This section provides a detailed description of all registers accessible in the ATD_10B8C.
3.2 Module Memory Map
Table 3-1 gives an overview on all ATD_10B8C registers.
Table 3-1 Module Memory Map
Address
Offset
Use
Access
$_00
ATD Control Register 0 (ATDCTL0)1
R
$_01
ATD Control Register 1 (ATDCTL1)2
R
$_02
ATD Control Register 2 (ATDCTL2)
R/W
$_03
ATD Control Register 3 (ATDCTL3)
R/W
$_04
ATD Control Register 4 (ATDCTL4)
R/W
$_05
ATD Control Register 5 (ATDCTL5)
R/W
$_06
ATD Status Register 0 (ATDSTAT0)
R/W
$_07
Unimplemented
$_08
ATD Test Register 0 (ATDTEST0)3
R
$_09
ATD Test Register 1 (ATDTEST1)
R/W
$_0A
$_0B
$_0C
$_0D
$_0E
Unimplemented
ATD Status Register 1 (ATDSTAT1)
R
Unimplemented
ATD Input Enable Register (ATDDIEN)
R/W
Unimplemented
$_0F
Port Data Register (PORTAD)
R
$_10, $_11
ATD Result Register 0 (ATDDR0H, ATDDR0L)
R/W
$_12, $_13
ATD Result Register 1 (ATDDR1H, ATDDR1L)
R/W
$_14, $_15
ATD Result Register 2 (ATDDR2H, ATDDR2L)
R/W
$_16, $_17
ATD Result Register 3 (ATDDR3H, ATDDR3L)
R/W
$_18, $_19
ATD Result Register 4 (ATDDR4H, ATDDR4L)
R/W
$_1A, $_1B
ATD Result Register 5 (ATDDR5H, ATDDR5L)
R/W
$_1C, $_1D
ATD Result Register 6 (ATDDR6H, ATDDR6L)
R/W
$_1E, $_1F
ATD Result Register 7 (ATDDR7H, ATDDR7L)
R/W
NOTES:
1. ATDCTL0 is intended for factory test purposes only.
2. ATDCTL1 is intended for factory test purposes only.
3. ATDTEST0 is intended for factory test purposes only.
NOTE:
Register Address = Base Address + Address Offset, where the Base Address is
defined at the MCU level and the Address Offset is defined at the module level.
13
ATD_10B8C Block User Guide — V02.12
3.3 Register Descriptions
This section describes in address order all the ATD_10B8C registers and their individual bits.
3.3.1 Reserved Register (ATDCTL0)
$_00
R
W
RESET:
7
0
6
0
5
0
4
0
3
0
2
0
1
0
0
0
0
0
0
0
0
0
0
0
= Unimplemented or Reserved
Figure 3-1 Reserved Register (ATDCTL0)
Read: always read $00 in normal modes
Write: unimplemented in normal modes
3.3.2 Reserved Register (ATDCTL1)
$_01
R
W
RESET:
7
0
6
0
5
0
4
0
3
0
2
0
1
0
0
0
0
0
0
0
0
0
0
0
= Unimplemented or Reserved
Figure 3-2 Reserved Register (ATDCTL1)
Read: always read $00 in normal modes
Write: unimplemented in normal modes
NOTE:
Writing to this registers when in special modes can alter functionality.
3.3.3 ATD Control Register 2 (ATDCTL2)
This register controls power down, interrupt and external trigger. Writes to this register will abort current
conversion sequence but will not start a new sequence.
14
ATD_10B8C Block User Guide — V02.12
$_02
R
W
RESET:
7
6
5
4
3
2
1
ADPU
AFFC
AWAI
ETRIGLE
ETRIGP
ETRIGE
ASCIE
0
0
0
0
0
0
0
0
ASCIF
0
= Unimplemented or Reserved
Figure 3-3 ATD Control Register 2 (ATDCTL2)
Read: anytime
Write: anytime
ADPU — ATD Power Up
This bit provides on/off control over the ATD_10B8C block allowing reduced MCU power
consumption. Because analog electronic is turned off when powered down, the ATD requires a
recovery time period after ADPU bit is enabled.
1 = Normal ATD functionality
0 = Power down ATD
AFFC — ATD Fast Flag Clear All
1 = Changes all ATD conversion complete flags to a fast clear sequence. Any access to a result
register will cause the associate CCF flag to clear automatically.
0 = ATD flag clearing operates normally (read the status register ATDSTAT1 before reading the
result register to clear the associate CCF flag).
AWAI — ATD Power Down in Wait Mode
When entering Wait Mode this bit provides on/off control over the ATD_10B8C block allowing
reduced MCU power. Because analog electronic is turned off when powered down, the ATD requires
a recovery time period after exit from Wait mode.
1 = Halt conversion and power down ATD during Wait mode
After exiting Wait mode with an interrupt conversion will resume. But due to the recovery time
the result of this conversion should be ignored.
0 = ATD continues to run in Wait mode
ETRIGLE — External Trigger Level/Edge Control
This bit controls the sensitivity of the external trigger signal. See Table 3-2 for details.
ETRIGP — External Trigger Polarity
This bit controls the polarity of the external trigger signal. See Table 3-2 for details.
15
ATD_10B8C Block User Guide — V02.12
Table 3-2 External Trigger Configurations
ETRIGLE
ETRIGP
0
0
1
1
0
1
0
1
External Trigger
Sensitivity
falling edge
rising edge
low level
high level
ETRIGE — External Trigger Mode Enable
This bit enables the external trigger on ATD channel 7. The external trigger allows to synchronize
sample and ATD conversions processes with external events.
1 = Enable external trigger
0 = Disable external trigger
NOTE:
The conversion results for the external trigger ATD channel 7 have no meaning
while external trigger mode is enabled.
ASCIE — ATD Sequence Complete Interrupt Enable
1 = ATD Interrupt will be requested whenever ASCIF=1 is set.
0 = ATD Sequence Complete interrupt requests are disabled.
ASCIF — ATD Sequence Complete Interrupt Flag
If ASCIE=1 the ASCIF flag equals the SCF flag (see 3.3.7), else ASCIF reads zero. Writes have no
effect.
1 = ATD sequence complete interrupt pending
0 = No ATD interrupt occurred
3.3.4 ATD Control Register 3 (ATDCTL3)
This register controls the conversion sequence length, FIFO for results registers and behavior in Freeze
Mode. Writes to this register will abort current conversion sequence but will not start a new sequence.
$_03
R
W
RESET:
7
0
0
6
5
4
3
2
1
0
S8C
S4C
S2C
S1C
FIFO
FRZ1
FRZ0
0
1
0
0
0
0
0
= Unimplemented or Reserved
Figure 3-4 ATD Control Register 3 (ATDCTL3)
Read: anytime
Write: anytime
16
ATD_10B8C Block User Guide — V02.12
S8C, S4C, S2C, S1C — Conversion Sequence Length
These bits control the number of conversions per sequence. Table 3-3 shows all combinations. At
reset, S4C is set to 1 (sequence length is 4). This is to maintain software continuity to HC12 family.
Table 3-3 Conversion Sequence Length Coding
S8C
S4C
S2C
S1C
Number of Conversions
per Sequence
0
0
0
0
8
0
0
0
1
1
0
0
1
0
2
0
0
1
1
3
0
1
0
0
4
0
1
0
1
5
0
1
1
0
6
0
1
1
1
7
1
X
X
X
8
FIFO — Result Register FIFO Mode
If this bit is zero (non-FIFO mode), the A/D conversion results map into the result registers based on
the conversion sequence; the result of the first conversion appears in the first result register, the second
result in the second result register, and so on.
If this bit is one (FIFO mode) the conversion counter is not reset at the beginning or ending of a
conversion sequence; sequential conversion results are placed in consecutive result registers. In a
continuously scanning conversion sequence, the result register counter will wrap around when it
reaches the end of the result register file. The conversion counter value (CC2-0 in ATDSTAT0) can
be used to determine where in the result register file, the current conversion result will be placed.
Aborting a conversion or starting a new conversion by write to an ATDCTL register (ATDCTL5-0)
clears the conversion counter even if FIFO=1. So the first result of a new conversion sequence, started
by writing to ATDCTL5, will always be place in the first result register (ATDDDR0). Intended usage
of FIFO mode is continuos conversion (SCAN=1) or triggered conversion (ETRIG=1).
Which result registers hold valid data can be tracked using the conversion complete flags. Fast flag
clear mode may or may not be useful in a particular application to track valid data.
1 = Conversion results are placed in consecutive result registers (wrap around at end).
0 = Conversion results are placed in the corresponding result register up to the selected sequence
length.
FRZ1, FRZ0 — Background Debug Freeze Enable
When debugging an application, it is useful in many cases to have the ATD pause when a breakpoint
(Freeze Mode) is encountered. These 2 bits determine how the ATD will respond to a breakpoint as
shown in Table 3-4. Leakage onto the storage node and comparator reference capacitors may
compromise the accuracy of an immediately frozen conversion depending on the length of the freeze
period.
17
ATD_10B8C Block User Guide — V02.12
Table 3-4 ATD Behavior in Freeze Mode (breakpoint)
FRZ1
FRZ0
Behavior in Freeze mode
0
0
Continue conversion
0
1
Reserved
1
0
Finish current conversion, then freeze
1
1
Freeze Immediately
3.3.5 ATD Control Register 4 (ATDCTL4)
This register selects the conversion clock frequency, the length of the second phase of the sample time and
the resolution of the A/D conversion (i.e.: 8-bits or 10-bits). Writes to this register will abort current
conversion sequence but will not start a new sequence.
$_04
R
W
RESET:
7
6
5
4
3
2
1
0
SRES8
SMP1
SMP0
PRS4
PRS3
PRS2
PRS1
PRS0
0
0
0
0
0
1
0
1
= Unimplemented or Reserved
Figure 3-5 ATD Control Register 4 (ATDCTL4)
Read: anytime
Write: anytime
SRES8 — A/D Resolution Select
This bit selects the resolution of A/D conversion results as either 8 or 10 bits. The A/D converter has
an accuracy of 10 bits; however, if low resolution is required, the conversion can be speeded up by
selecting 8-bit resolution.
1 = 8 bit resolution
0 = 10 bit resolution
SMP1, SMP0 — Sample Time Select
These two bits select the length of the second phase of the sample time in units of ATD conversion
clock cycles. Note that the ATD conversion clock period is itself a function of the prescaler value (bits
PRS4-0). The sample time consists of two phases. The first phase is two ATD conversion clock cycles
long and transfers the sample quickly (via the buffer amplifier) onto the A/D machine’s storage node.
The second phase attaches the external analog signal directly to the storage node for final charging and
high accuracy. Table 3-5 lists the lengths available for the second sample phase.
18
ATD_10B8C Block User Guide — V02.12
Table 3-5 Sample Time Select
SMP1
SMP0
Length of 2nd phase of sample time
0
0
2 A/D conversion clock periods
0
1
4 A/D conversion clock periods
1
0
8 A/D conversion clock periods
1
1
16 A/D conversion clock periods
PRS4, PRS3, PRS2, PRS1, PRS0 — ATD Clock Prescaler
These 5 bits are the binary value prescaler value PRS. The ATD conversion clock frequency is calculated
as follows:
[ BusClock ]
ATDclock = -------------------------------- × 0.5
[ PRS + 1 ]
Note that the maximum ATD conversion clock frequency is half the Bus Clock. The default (after reset)
prescaler value is 5 which results in a default ATD conversion clock frequency that is Bus Clock divided
by 12. Table 3-6 illustrates the divide-by operation and the appropriate range of the Bus Clock.
19
ATD_10B8C Block User Guide — V02.12
Table 3-6 Clock Prescaler Values
Prescale Value
Total Divisor
Value
Max. Bus Clock1
Min. Bus Clock2
00000
00001
00010
00011
00100
00101
00110
00111
01000
01001
01010
01011
01100
01101
01110
01111
10000
10001
10010
10011
10100
10101
10110
10111
11000
11001
11010
11011
11100
11101
11110
11111
divide by 2
divide by 4
divide by 6
divide by 8
divide by 10
divide by 12
divide by 14
divide by 16
divide by 18
divide by 20
divide by 22
divide by 24
divide by 26
divide by 28
divide by 30
divide by 32
divide by 34
divide by 36
divide by 38
divide by 40
divide by 42
divide by 44
divide by 46
divide by 48
divide by 50
divide by 52
divide by 54
divide by 56
divide by 58
divide by 60
divide by 62
divide by 64
4 MHz
8 MHz
12 MHz
16 MHz
20 MHz
24 MHz
28 MHz
32 MHz
36 MHz
40 MHz
44 MHz
48 MHz
52 MHz
56 MHz
60 MHz
64 MHz
68 MHz
72 MHz
76 MHz
80 MHz
84 MHz
88 MHz
92 MHz
96 MHz
100 MHz
104 MHz
108 MHz
112 MHz
116 MHz
120 MHz
124 MHz
128 MHz
1 MHz
2 MHz
3 MHz
4 MHz
5 MHz
6 MHz
7 MHz
8 MHz
9 MHz
10 MHz
11 MHz
12 MHz
13 MHz
14 MHz
15 MHz
16 MHz
17 MHz
18 MHz
19 MHz
20 MHz
21 MHz
22 MHz
23 MHz
24 MHz
25 MHz
26 MHz
27 MHz
28 MHz
29 MHz
30 MHz
31 MHz
32 MHz
NOTE:
1. Maximum ATD conversion clock frequency is 2MHz. The maximum allowed Bus Clock frequency is shown in this column.
2. Minimum ATD conversion clock frequency is 500KHz. The minimum allowed Bus Clock frequency is shown in this column.
3.3.6 ATD Control Register 5 (ATDCTL5)
This register selects the type of conversion sequence and the analog input channels sampled. Writes to this
register will abort current conversion sequence and start a new conversion sequence.
20
ATD_10B8C Block User Guide — V02.12
$_05
R
W
RESET:
7
6
5
4
DJM
DSGN
SCAN
MULT
0
0
0
0
3
0
0
2
1
0
CC
CB
CA
0
0
0
= Unimplemented or Reserved
Figure 3-6 ATD Control Register 5 (ATDCTL5)
Read: anytime
Write: anytime
DJM — Result Register Data Justification
This bit controls justification of conversion data in the result registers. See 3.3.13 ATD Conversion
Result Registers (ATDDRHx/ATDDRLx) for details.
1 = Right justified data in the result registers
0 = Left justified data in the result registers
DSGN — Result Register Data Signed or Unsigned Representation
This bit selects between signed and unsigned conversion data representation in the result registers.
Signed data is represented as 2’s complement. Signed data is not available in right justification. See
3.3.13 ATD Conversion Result Registers (ATDDRHx/ATDDRLx) for details.
1 = Signed data representation in the result registers
0 = Unsigned data representation in the result registers
Table 3-7 summarizes the result data formats available and how they are set up using the control bits.
Table 3-8 illustrates the difference between the signed and unsigned, left justified output codes for an
input signal range between 0 and 5.12 Volts.
Table 3-7 Available Result Data Formats
SRES8
DJM
DSGN
Result Data Formats
Description and Bus Bit Mapping
1
1
1
0
0
0
0
0
1
0
0
1
0
1
X
0
1
X
8-bit / left justified / unsigned - bits 8-15
8-bit / left justified / signed - bits 8-15
8-bit / right justified / unsigned - bits 0-7
10-bit / left justified / unsigned - bits 6-15
10-bit / left justified / signed - bits 6-15
10-bit / right justified / unsigned - bits 0-9
21
ATD_10B8C Block User Guide — V02.12
Table 3-8 Left Justified, Signed and Unsigned ATD Output Codes.
Input Signal
Vrl = 0 Volts
Vrh = 5.12 Volts
Signed
8-Bit
Codes
Unsigned
8-Bit
Codes
Signed
10-Bit
Codes
Unsigned
10-Bit
Codes
5.120 Volts
5.100
5.080
7F
7F
7E
FF
FF
FE
7FC0
7F00
7E00
FFC0
FF00
FE00
2.580
2.560
2.540
01
00
FF
81
80
7F
0100
0000
FF00
8100
8000
7F00
0.020
0.000
81
80
01
00
8100
8000
0100
0000
SCAN — Continuous Conversion Sequence Mode
This bit selects whether conversion sequences are performed continuously or only once.
1 = Continuous conversion sequences (scan mode)
0 = Single conversion sequence
MULT — Multi-Channel Sample Mode
When MULT is 0, the ATD sequence controller samples only from the specified analog input channel
for an entire conversion sequence. The analog channel is selected by channel selection code (control
bits CC/CB/CA located in ATDCTL5). When MULT is 1, the ATD sequence controller samples
across channels. The number of channels sampled is determined by the sequence length value (S8C,
S4C, S2C, S1C). The first analog channel examined is determined by channel selection code (CC, CB,
CA control bits); subsequent channels sampled in the sequence are determined by incrementing the
channel selection code.
1 = Sample across several channels
0 = Sample only one channel
CC, CB, CA — Analog Input Channel Select Code
These bits select the analog input channel(s) whose signals are sampled and converted to digital codes.
Table 3-9 lists the coding used to select the various analog input channels. In the case of single
channel scans (MULT=0), this selection code specified the channel examined. In the case of
multi-channel scans (MULT=1), this selection code represents the first channel to be examined in the
conversion sequence. Subsequent channels are determined by incrementing channel selection code;
selection codes that reach the maximum value wrap around to the minimum value.
Table 3-9 Analog Input Channel Select Coding
22
CC
CB
CA
Analog Input
Channel
0
0
0
AN0
0
0
1
AN1
0
1
0
AN2
0
1
1
AN3
ATD_10B8C Block User Guide — V02.12
Table 3-9 Analog Input Channel Select Coding
CC
CB
CA
Analog Input
Channel
1
0
0
AN4
1
0
1
AN5
1
1
0
AN6
1
1
1
AN7
3.3.7 ATD Status Register 0 (ATDSTAT0)
This read-only register contains the Sequence Complete Flag, overrun flags for external trigger and FIFO
mode, and the conversion counter.
$_06
7
R
W
RESET:
SCF
0
6
0
0
5
4
ETORF
FIFOR
0
0
3
0
2
CC2
1
CC1
0
CC0
0
0
0
0
= Unimplemented or Reserved
Figure 3-7 ATD Status Register 0 (ATDSTAT0)
Read: anytime
Write: anytime (No effect on (CC2, CC1, CC0))
SCF — Sequence Complete Flag
This flag is set upon completion of a conversion sequence. If conversion sequences are continuously
performed (SCAN=1), the flag is set after each one is completed. This flag is cleared when one of the
following occurs:
A) Write “1” to SCF
B) Write to ATDCTL5 (a new conversion sequence is started)
C) If AFFC=1 and read of a result register
1 = Conversion sequence has completed
0 = Conversion sequence not completed
ETORF — External Trigger Overrun Flag
While in edge trigger mode (ETRIGLE=0), if additional active edges are detected while a conversion
sequence is in process the overrun flag is set. This flag is cleared when one of the following occurs:
A) Write “1” to ETORF
B) Write to ATDCTL2, ATDCTL3 or ATDCTL4 (a conversion sequence is aborted)
C) Write to ATDCTL5 (a new conversion sequence is started)
1 = External trigger over run error has occurred
23
ATD_10B8C Block User Guide — V02.12
0 = No External trigger over run error has occurred
FIFOR - FIFO Over Run Flag.
This bit indicates that a result register has been written to before its associated conversion complete
flag (CCF) has been cleared. This flag is most useful when using the FIFO mode because the flag
potentially indicates that result registers are out of sync with the input channels. However, it is also
practical for non-FIFO modes, and indicates that a result register has been over written before it has
been read (i.e. the old data has been lost). This flag is cleared when one of the following occurs:
A) Write “1” to FIFOR
B) Start a new conversion sequence (write to ATDCTL5 or external trigger)
1 = An over run condition exists
0 = No over run has occurred
CC2, CC1, CC0 — Conversion Counter
These 3 read-only bits are the binary value of the conversion counter. The conversion counter points
to the result register that will receive the result of the current conversion. E.g. CC2=1, CC1=1, CC0=0
indicates that the result of the current conversion will be in ATD Result Register 6. If in non-FIFO
mode (FIFO=0) the conversion counter is initialized to zero at the begin and end of the conversion
sequence. If in FIFO mode (FIFO=1) the register counter is not initialized. The conversion counters
wraps around when its maximum value is reached.
Aborting a conversion or starting a new conversion by write to an ATDCTL register (ATDCTL5-0)
clears the conversion counter even if FIFO=1.
3.3.8 Reserved Register (ATDTEST0)
$_08
R
W
RESET:
7
U
6
U
5
U
4
U
3
U
2
U
1
U
0
U
1
0
0
0
0
0
0
0
= Unimplemented or Reserved
Figure 3-8 Reserved Register (ATDTEST0)
Read: anytime, returns unpredictable values
Write: anytime in special modes, unimplemented in normal modes
NOTE:
Writing to this registers when in special modes can alter functionality.
3.3.9 ATD Test Register 1 (ATDTEST1)
This register contains the SC bit used to enable special channel conversions.
24
ATD_10B8C Block User Guide — V02.12
$_09
R
W
RESET:
7
U
6
U
5
0
4
0
3
0
2
0
1
0
0
0
0
0
0
0
0
0
SC
0
= Unimplemented or Reserved
Figure 3-9 ATD Test Register 1 (ATDTEST1)
Read: anytime, returns unpredictable values for Bit7 and Bit6
Write: anytime
SC - Special Channel Conversion Bit
If this bit is set, then special channel conversion can be selected using CC, CB and CA of ATDCTL5.
Table 3-10 lists the coding.
1 = Special channel conversions enabled
0 = Special channel conversions disabled
NOTE:
Always write remaining bits of ATDTEST1 (Bit7 to Bit1) zero when writing SC bit.
Not doing so might result in unpredictable ATD behavior.
Table 3-10 Special Channel Select Coding
SC
CC
CB
CA
Analog Input
Channel
1
0
X
X
Reserved
1
1
0
0
VRH
1
1
0
1
VRL
1
1
1
0
(VRH+VRL) / 2
1
1
1
1
Reserved
3.3.10 ATD Status Register 1 (ATDSTAT1)
This read-only register contains the Conversion Complete Flags.
25
ATD_10B8C Block User Guide — V02.12
$_0B
R
W
RESET:
7
CCF7
6
CCF6
5
CCF5
4
CCF4
3
CCF3
2
CCF2
1
CCF1
0
CCF0
0
0
0
0
0
0
0
0
= Unimplemented or Reserved
Figure 3-10 ATD Status Register 1 (ATDSTAT1)
Read: anytime
Write: anytime, no effect
CCFx — Conversion Complete Flag x (x=7,6,5,4,3,2,1,0)
A conversion complete flag is set at the end of each conversion in a conversion sequence. The flags
are associated with the conversion position in a sequence (and also the result register number).
Therefore, CCF0 is set when the first conversion in a sequence is complete and the result is available
in result register ATDDR0; CCF1 is set when the second conversion in a sequence is complete and the
result is available in ATDDR1, and so forth. A flag CCFx (x=7,6,5,4,3,2,1,0) is cleared when one of
the following occurs:
A) Write to ATDCTL5 (a new conversion sequence is started)
B) If AFFC=0 and read of ATDSTAT1 followed by read of result register ATDDRx
C) If AFFC=1 and read of result register ATDDRx
1 = Conversion number x has completed, result ready in ATDDRx
0 = Conversion number x not completed
3.3.11 ATD Input Enable Register (ATDDIEN)
$_0D
R
W
RESET:
7
6
5
4
3
2
1
0
IEN7
IEN6
IEN5
IEN4
IEN3
IEN2
IEN1
IEN0
0
0
0
0
0
0
0
0
= Unimplemented or Reserved
Figure 3-11 ATD Input Enable Register (ATDDIEN)
Read: anytime
Write: anytime
IENx — ATD Digital Input Enable on channel x (x= 7, 6, 5, 4, 3, 2, 1, 0)
This bit controls the digital input buffer from the analog input pin (ANx) to PTADx data register.
1 = Enable digital input buffer to PTADx.
26
ATD_10B8C Block User Guide — V02.12
0 = Disable digital input buffer to PTADx
NOTE:
Setting this bit will enable the corresponding digital input buffer continuously. If
this bit is set while simultaneously using it as an analog port, there is potentially
increased power consumption because the digital input buffer maybe in the linear
region.
3.3.12 Port Data Register (PORTAD)
The digital port pins are shared with the analog A/D inputs AN7-0.
$_0F
R
W
RESET:
Pin
Function
7
PTAD7
6
PTAD6
5
PTAD5
4
PTAD4
3
PTAD3
2
PTAD2
1
PTAD1
0
PTAD0
1
1
1
1
1
1
1
1
AN7
AN6
AN5
AN4
AN3
AN2
AN1
AN0
= Unimplemented or Reserved
Figure 3-12 Port Data Register (PORTAD)
Read: anytime
Write: anytime, no effect
PTADx — A/D Channel x (ANx) Digital Input (x= 7,6,5,4,3,2,1,0)
If the digital input buffer on the ANx pin is enabled (IENx=1) read returns the logic level on ANx pin
(signal potentials not meeting VIL or VIH specifications will have an indeterminate value)).
If the digital input buffers are disabled (IENx=0), read returns a “1”.
Reset sets all PORTAD bits to “1”.
3.3.13 ATD Conversion Result Registers (ATDDRHx/ATDDRLx)
The A/D conversion results are stored in 8 read-only result registers ATDDRHx/ATDDRLx. The result
data is formatted in the result registers based on two criteria. First there is left and right justification; this
selection is made using the DJM control bit in ATDCTL5. Second there is signed and unsigned data; this
selection is made using the DSGN control bit in ATDCTL5. Signed data is stored in 2’s complement
format and only exists in left justified format. Signed data selected for right justified format is ignored.
Read: anytime
Write: anytime, no effect in normal modes
27
ATD_10B8C Block User Guide — V02.12
3.3.13.1 Left Justified Result Data
$_10 = ATDDR0H, $_12 = ATDDR1H, $_14 = ATDDR2H, $_16 = ATDDR3H
$_18 = ATDDR4H, $_1A = ATDDR5H, $_1C = ATDDR6H, $_1E = ATDDR7H
7
R
BIT 9 MSB
W
BIT 7 MSB
RESET:
0
6
BIT 8
BIT 6
0
5
BIT 7
BIT 5
0
4
BIT 6
BIT 4
0
3
BIT 5
BIT 3
0
2
BIT 4
BIT 2
0
1
BIT 3
BIT 1
0
0
BIT 2
BIT 0
0
10-bit data
8-bit data
= Unimplemented or Reserved
Figure 3-13 Left Justified, ATD Conversion Result Register, High Byte (ATDDRxH)
$_11 = ATDDR0L, $_13 = ATDDR1L, $_15 = ATDDR2L, $_17 = ATDDR3L
$_19 = ATDDR4L, $_1B = ATDDR5L, $_1D = ATDDR6L, $_1F = ATDDR7L
R
W
RESET:
7
BIT 1
U
0
6
BIT 0
U
0
5
0
0
0
4
0
0
0
3
0
0
0
2
0
0
0
1
0
0
0
0
0
0
0
10-bit data
8-bit data
= Unimplemented or Reserved
Figure 3-14 Left Justified, ATD Conversion Result Register, Low Byte (ATDDRxL)
3.3.13.2 Right Justified Result Data
$_10 = ATDDR0H, $_12 = ATDDR1H, $_14 = ATDDR2H, $_16 = ATDDR3H
$_18 = ATDDR4H, $_1A = ATDDR5H, $_1C = ATDDR6H, $_1E = ATDDR7H
R
W
RESET:
7
0
0
0
6
0
0
0
5
0
0
0
4
0
0
0
3
0
0
0
2
0
0
0
1
BIT 9 MSB
0
0
0
BIT 8
0
0
10-bit data
8-bit data
= Unimplemented or Reserved
Figure 3-15 Right Justified, ATD Conversion Result Register, High Byte (ATDDRxH)
28
ATD_10B8C Block User Guide — V02.12
$_11 = ATDDR0L, $_13 = ATDDR1L, $_15 = ATDDR2L, $_17 = ATDDR3L
$_19 = ATDDR4L, $_1B = ATDDR5L, $_1D = ATDDR6L, $_1F = ATDDR7L
7
R
BIT 7
W
BIT 7 MSB
RESET:
0
6
BIT 6
BIT 6
0
5
BIT 5
BIT 5
0
4
BIT 4
BIT 4
0
3
BIT 3
BIT 3
0
2
BIT 2
BIT 2
0
1
BIT 1
BIT 1
0
0
BIT 0
BIT 0
0
10-bit data
8-bit data
= Unimplemented or Reserved
Figure 3-16 Right Justified, ATD Conversion Result Register, Low Byte (ATDDRxL)
29
ATD_10B8C Block User Guide — V02.12
30
ATD_10B8C Block User Guide — V02.12
Section 4 Functional Description
4.1 General
The ATD_10B8C is structured in an analog and a digital sub-block.
4.2 Analog Sub-block
The analog sub-block contains all analog electronics required to perform a single conversion. Separate
power supplies VDDA and VSSA allow to isolate noise of other MCU circuitry from the analog sub-block.
4.2.1 Sample and Hold Machine
The Sample and Hold (S/H) Machine accepts analog signals from the external surroundings and stores
them as capacitor charge on a storage node.
The sample process uses a two stage approach. During the first stage, the sample amplifier is used to
quickly charge the storage node.The second stage connects the input directly to the storage node to
complete the sample for high accuracy.
When not sampling, the sample and hold machine disables its own clocks. The analog electronics still draw
their quiescent current. The power down (ADPU) bit must be set to disable both the digital clocks and the
analog power consumption.
The input analog signals are unipolar and must fall within the potential range of VSSA to VDDA.
4.2.2 Analog Input Multiplexer
The analog input multiplexer connects one of the 8 external analog input channels to the sample and hold
machine.
4.2.3 Sample Buffer Amplifier
The sample amplifier is used to buffer the input analog signal so that the storage node can be quickly
charged to the sample potential.
4.2.4 Analog-to-Digital (A/D) Machine
The A/D Machine performs analog to digital conversions. The resolution is program selectable at either 8
or 10 bits. The A/D machine uses a successive approximation architecture. It functions by comparing the
stored analog sample potential with a series of digitally generated analog potentials. By following a binary
search algorithm, the A/D machine locates the approximating potential that is nearest to the sampled
potential.
31
ATD_10B8C Block User Guide — V02.12
When not converting the A/D machine disables its own clocks. The analog electronics still draws
quiescent current. The power down (ADPU) bit must be set to disable both the digital clocks and the
analog power consumption.
Only analog input signals within the potential range of VRL to VRH (A/D reference potentials) will result
in a non-railed digital output codes.
4.3 Digital Sub-block
This subsection explains some of the digital features in more detail. See register descriptions for all details.
4.3.1 External Trigger Input (ETRIG)
The external trigger feature allows the user to synchronize ATD conversions to the external environment
events rather than relying on software to signal the ATD module when ATD conversions are to take place.
The input signal (ATD channel 7) is programmable to be edge or level sensitive with polarity control.
Table 4-1 gives a brief description of the different combinations of control bits and their affect on the
external trigger function.
Table 4-1 External Trigger Control Bits
ETRIGLE
ETRIGP
ETRIGE
SCAN
Description
X
X
0
0
Ignores external trigger. Performs one
conversion sequence and stops.
X
X
0
1
Ignores external trigger. Performs
continuous conversion sequences.
0
0
1
X
Falling edge triggered. Performs one
conversion sequence per trigger.
0
1
1
X
Rising edge triggered. Performs one
conversion sequence per trigger.
1
0
1
X
Trigger active low. Performs
continuous conversions while trigger
is active.
1
1
1
X
Trigger active high. Performs
continuous conversions while trigger
is active.
During a conversion, if additional active edges are detected the overrun error flag ETORF is set.
In either level or edge triggered modes, the first conversion begins when the trigger is received. In both
cases, the maximum latency time is one Bus Clock cycle plus any skew or delay introduced by the trigger
circuitry.
NOTE:
32
The conversion results for the external trigger ATD channel 7 have no meaning
while external trigger mode is enabled.
ATD_10B8C Block User Guide — V02.12
Once ETRIGE is enabled, conversions cannot be started by a write to ATDCTL5, but rather must be
triggered externally.
If the level mode is active and the external trigger both de-asserts and re-asserts itself during a conversion
sequence, this does not constitute an overrun; therefore, the flag is not set. If the trigger is left asserted in
level mode while a sequence is completing, another sequence will be triggered immediately.
4.3.2 General Purpose Digital Input Port Operation
The input channel pins can be multiplexed between analog and digital data. As analog inputs, they are
multiplexed and sampled to supply signals to the A/D converter. As digital inputs, they supply external
input data that can be accessed through the digital port register PORTAD (input-only).
The analog/digital multiplex operation is performed in the input pads. The input pad is always connected
to the analog inputs of the ATD_10B8C. The input pad signal is buffered to the digital port registers. This
buffer can be turned on or off with the ATDDIEN register. This is important so that the buffer does not
draw excess current when analog potentials are presented at its input.
4.3.3 Low Power Modes
The ATD_10B8C can be configured for lower MCU power consumption in 3 different ways:
•
Stop Mode: This halts A/D conversion. Exit from Stop mode will resume A/D conversion, But due
to the recovery time the result of this conversion should be ignored.
•
Wait Mode with AWAI=1: This halts A/D conversion. Exit from Wait mode will resume A/D
conversion, but due to the recovery time the result of this conversion should be ignored.
•
Writing ADPU=0 (Note that all ATD registers remain accessible.): This aborts any A/D conversion
in progress.
Note that the reset value for the ADPU bit is zero. Therefore, when this module is reset, it is reset into the
power down state.
33
ATD_10B8C Block User Guide — V02.12
34
ATD_10B8C Block User Guide — V02.12
Section 5 Resets
5.1 General
At reset the ATD_10B8C is in a power down state. The reset state of each individual bit is listed within
the Register Description section (see Section 3 Memory Map and Register Definition) which details the
registers and their bit-field.
35
ATD_10B8C Block User Guide — V02.12
36
ATD_10B8C Block User Guide — V02.12
Section 6 Interrupts
6.1 General
The interrupt requested by the ATD_10B8C is listed in Table 6-1. Refer to MCU specification for related
vector address and priority.
Table 6-1 ATD_10B8C Interrupt Vectors
Interrupt Source
CCR
Mask
Local Enable
Sequence Complete
Interrupt
I bit
ASCIE in ATDCTL2
See register descriptions for further details.
37
ATD_10B8C Block User Guide — V02.12
38
ATD_10B8C Block User Guide — V02.12
User Guide End Sheet
39
ATD_10B8C Block User Guide — V02.12
FINAL PAGE OF
40
PAGES
40
DOCUMENT NUMBER
S12BDLC_BG
BDLC
Block Guide
V01.03
Original Release Date:19 JAN 2001
Revised: July 19, 2001
Motorola, Inc
Motorola reserves the right to make changes without further notice to any products herein to improve reliability, function or
design. Motorola does not assume any liability arising out of the application or use of any product or circuit described herein;
neither does it convey any license under its patent rights nor the rights of others. Motorola products are not designed, intended,
or authorized for use as components in systems intended for surgical implant into the body, or other applications intended to
support or sustain life, or for any other application in which the failure of the Motorola product could create a situation where
personal injury or death may occur. Should Buyer purchase or use Motorola products for any such unintended or unauthorized
application, Buyer shall indemnify and hold Motorola and its officers, employees, subsidiaries, affiliates, and distributors harmless
against all claims, costs, damages, and expenses, and reasonable attorney fees arising out of, directly or indirectly, any claim of
personal injury or death associated with such unintended or unauthorized use, even if such claim alleges that Motorola was
negligent regarding the design or manufacture of the part.
1
Block Guide — S12BDLC_BG V01.03
Revision History
Version
Number
Revision
Date
Effective
Date
V01.00
04/20/2001
01/19/2001
Original Release
06/13/2001
Corrected formal issues w/paragraph formats, cross
references and master pages.
06/14/2001
Removed references to internal signals
Moved initialization chap. in ’RESETS’ to functional descrip
Removed redundant references in the Interrupts section
Updated the Interrupts table
Changed some explanations to bullets
V01.01
06/12/2001
V01.02
06/13/2001
V01.03
07/19/2001
2
Author
Description of Changes
Document names have been added
Names and Variable defenitions have been hidden
Block Guide — S12BDLC_BG V01.03
Table of Contents
Section 1 Introduction
1.1
1.2
1.3
1.4
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
Modes of Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
Block Diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .16
Section 2 Signal Description
2.1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .19
2.2
Detailed Signal Descriptions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .19
2.2.1
TXB - BDLC Transmit Pin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .19
2.2.2
RXB - BDLC Receive Pin. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .19
Section 3 Memory Map and Registers
3.1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
3.2
Module Memory Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
3.3
Register Descriptions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
3.3.1
BDLC Control Register 1 (DLCBCR1) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
3.3.2
BDLC State Vector Register (DLCBSVR) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .23
3.3.3
BDLC Control Register 2 (DLCBCR2) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .25
3.3.4
BDLC Data Register (DLCBDR) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31
3.3.5
BDLC Analog Round Trip Delay Register (DLCBARD) . . . . . . . . . . . . . . . . . . . . . . .32
3.3.6
BDLC Rate Select Register (DLCBRSR) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .33
3.3.7
BDLC Control Register (DLCSCR) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .35
3.3.8
BDLC Status Register (DLCBSTAT) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .35
Section 4 Functional Description
4.1
General. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .37
4.1.1
J1850 Frame Format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .37
4.1.2
J1850 VPW Symbols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .39
4.1.3
J1850 VPW Valid/Invalid Bits & Symbols. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .41
4.1.4
J1850 Bus Errors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .50
4.2
Mux Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .53
4.2.1
Mux Interface - Rx Digital Filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .53
3
Block Guide — S12BDLC_BG V01.03
4.3
4.3.1
4.4
4.4.1
4.4.2
4.4.3
4.5
4.5.1
4.5.2
4.5.3
4.5.4
4.6
4.6.1
4.6.2
4.6.3
4.6.4
4.6.5
4.6.6
4.6.7
4.7
4.7.1
4.7.2
4.8
4.8.1
4.8.2
4.9
4.9.1
4.9.2
4.9.3
4.9.4
Protocol Handler. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .55
Protocol Architecture . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .55
Transmitting A Message . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .58
BDLC Transmission Control Bits . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .58
Transmitting Exceptions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .60
Aborting a Transmission . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .61
Receiving A Message . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62
BDLC Reception Control Bits. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .63
Receiving a Message with the BDLC module . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .63
Filtering Received Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .64
Receiving Exceptions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .64
Transmitting An In-Frame Response (IFR) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .67
IFR Types Supported by the BDLC module. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .67
BDLC IFR Transmit Control Bits . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .68
Transmit Single Byte IFR . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .69
Transmit Multi-Byte IFR 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .69
Transmit Multi-Byte IFR 0 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .70
Transmitting An IFR with the BDLC module . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .70
Transmitting IFR Exceptions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .76
Receiving An In-Frame Response (IFR) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .78
Receiving an IFR with the BDLC module. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .78
Receiving IFR Exceptions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .79
Special BDLC Module Operations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .80
Transmitting Or Receiving A Block Mode Message. . . . . . . . . . . . . . . . . . . . . . . . . .80
Receiving A Message In 4X Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .80
BDLC Module Initialization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .81
Initialization Sequence . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .82
Initializing the Configuration Bits . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .82
Exiting Loopback Mode and Enabling the BDLC module . . . . . . . . . . . . . . . . . . . . .83
Enabling BDLC Interrupts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .83
Section 5 Resets
5.1
General. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .87
Section 6 Interrupts
6.1
General. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .89
4
Block Guide — S12BDLC_BG V01.03
Appendix A Electrical Specifications
5
Block Guide — S12BDLC_BG V01.03
6
Block Guide — S12BDLC_BG V01.03
List of Tables
Table 3-1
Table 3-2
Table 3-3
Table 3-4
Table 3-5
Table 3-6
Table 4-1
Table 4-2
Table 4-3
Table 4-4
Table 4-5
Table 4-6
Table 4-7
Table 4-8
Table 6-1
Module Memory Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
Interrupt Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .23
Transmit In-Frame Response Control Bit Priority Encoding . . . . . . . . . . . . . . . . .27
BARD Values vs. Transceiver Delay and Transmitter Timing Adjustment . . . . . .33
BDLC Rate Selection for Binary Frequencies [CLKS = 1] . . . . . . . . . . . . . . . . . . .34
BDLC Rate Selection for Integer Frequencies [CLKS = 0] . . . . . . . . . . . . . . . . . .35
BDLC Transmitter VPW Symbol Timing for Integer Frequencies . . . . . . . . . . . . .42
BDLC Transmitter VPW Symbol Timing for Binary Frequencies . . . . . . . . . . . . . .43
BDLC Receiver VPW Symbol Timing for Integer Frequencies . . . . . . . . . . . . . . .43
BDLC Receiver VPW Symbol Timing for Binary Frequencies . . . . . . . . . . . . . . . .44
BDLC Receiver VPW 4X Symbol Timing for Integer Frequencies. . . . . . . . . . . . .44
BDLC Receiver VPW 4X Symbol Timing for Binary Frequencies . . . . . . . . . . . . .44
BDLC module J1850 Error Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .52
IFR Control Bit Priority Encoding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .69
Interrupt Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .89
7
Block Guide — S12BDLC_BG V01.03
8
Block Guide — S12BDLC_BG V01.03
List of Figures
Figure 1-1
Figure 1-2
Figure 3-1
Figure 3-2
Figure 3-3
Figure 3-4
Figure 3-5
Figure 3-6
Figure 3-7
Figure 3-8
Figure 3-9
Figure 4-1
Figure 4-2
Figure 4-3
Figure 4-4
Figure 4-5
Figure 4-6
Figure 4-7
Figure 4-8
Figure 4-9
Figure 4-10
Figure 4-11
Figure 4-12
Figure 4-13
Figure 4-14
Figure 4-15
Figure 4-16
Figure 4-17
BDLC Operating Modes State Diagram. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .12
BDLC Block Diagram. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .16
BDLC Control Register 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
BDLC State Vector Register . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .23
BDLC Control Register 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .25
Types of In-Frame Response . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .28
BDLC Data Register . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31
BDLC Analog Round Trip Delay Register . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .32
BDLC Rate Select Register . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .34
BDLC Control Register . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .35
BDLC Status Register . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .36
J1850 Bus Message Format (VPW) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .37
J1850 VPW Symbols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40
J1850 VPW Passive Symbols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .46
J1850 VPW EOF and IFS Symbols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .47
J1850 VPW Active Symbols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .48
J1850 VPW BREAK Symbol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .49
J1850 VPW Bitwise Arbitrations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .50
BDLC Module Rx Digital Filter Block Diagram. . . . . . . . . . . . . . . . . . . . . . . . . . .54
BDLC Protocol Handler Outline . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .56
Basic BDLC Transmit Flowchart . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62
Basic BDLC Receive Flowchart. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .66
Transmitting A Type 1 IFR. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .72
Transmitting A Type 2 IFR. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .74
Transmitting A Type 3 IFR. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .77
Receiving An IFR With the BDLC module . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .79
Basic BDLC Module Transmit Flowchart . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .81
Basic BDLC Module Initialization Flowchart . . . . . . . . . . . . . . . . . . . . . . . . . . . .85
9
Block Guide — S12BDLC_BG V01.03
10
Block Guide — S12BDLC_BG V01.03
Section 1 Introduction
1.1 Overview
The BDLC module is a serial communication module which allows the user to send and receive messages
across a Society of Automotive Engineers (SAE) J1850 serial communication network. The user’s
software handles each transmitted or received message on a byte-by-byte basis, while the BDLC performs
all of the network access, arbitration, message framing and error detection duties.
It is recommended that the reader be familiar with the operation and requirements of the SAE J1850
protocol as described in the document “SAE Standard J1850 Class B Data Communications Network
Interface” prior to proceeding with this specification.
The BDLC module is designed in a modular structure for use as an IP block. A general working knowledge
of the IP Bus signals and bus control is assumed in the writing of this document. For details, refer to the
SRS IP Bus specifications.
1.2 Features
Features of the BDLC module include the following:
•
SAE J1850 Class B Data Communications Network Interface Compatible and ISO Compatible for
Low-Speed (≤ 125 Kbps) Serial Data Communications in Automotive Applications
•
10.4 Kbps Variable Pulse Width (VPW) Bit Format
•
Digital Noise Filter
•
Digital Loopback Mode
•
4X Receive Mode, 41.6 Kbps, Supported
•
Block Mode Receive and Transmit Supported
•
Collision Detection
•
Hardware Cyclical Redundancy Check (CRC) Generation and Checking
•
Dedicated Register for Symbol Timing Adjustments
•
IP Bus Interface
•
In-Frame Response (IFR) Types 0, 1, 2, and 3 Supported
•
Power-Saving Stop and Wait Modes with Automatic Wakeup on Network Activity
•
Polling and CPU Interrupt Generation with Vector Lookup Available
1.3 Modes of Operation
•
The BDLC module has 6 main modes of operation which interact with the power supplies, pins, and
the rest of the MCU as shown below.
11
Block Guide — S12BDLC_BG V01.03
Power Off
Vdd > Vdd(Min.) and
Any MCU reset source asserted
Vdd ≤ Vdd(Min.)
Reset
Any MCU reset source asserted
(from any mode)
No MCU reset source asserted
BDLC
Disabled
BDLCE cleared in DLCSCR register
Network activity or
other MCU wake-up
BDLC Stop
BDLCE set in DLCSCR register
Run
STOP instruction or
(WAIT instruction and WCM=1)
Network activity or
other MCU wake-up
(WAIT instruction and WCM=0)
BDLC Wait
Figure 1-1 BDLC Operating Modes State Diagram
•
Power Off
This mode is entered from the Reset mode whenever the BDLC module supply voltage Vdd drops
below its minimum specified value for the BDLC module to guarantee operation. The BDLC
module will be placed in the Reset mode by a system Low Voltage Reset (LVR) before being
powered down. In this mode, the pin input and output specifications are not guaranteed.
•
Reset
This mode is entered from the Power Off mode whenever the BDLC module supply voltage Vdd
rises above its minimum specified value (Vdd(MIN)) and some MCU reset source is asserted. To
prevent the BDLC from entering an unknown state, the internal MCU reset is asserted while
12
Block Guide — S12BDLC_BG V01.03
powering up the BDLC module. BDLC Reset mode is also entered from any other mode as soon as
one of the MCU’s possible reset sources (e.g. LVR, POR, COP watchdog, Reset pin etc.) is
asserted.
In this mode, the internal BDLC module voltage references are operative, Vdd is supplied to the
internal circuits, which are held in their reset state and the internal BDLC module system clock is
running. Registers will assume their reset condition. Outputs are held in their programmed Reset
state, inputs and network activity are ignored.
•
BDLC Disabled
This mode is entered from the Reset mode after all MCU reset sources are no longer asserted. It is
entered from the Run mode whenever the BDLCE bit in the DLCSCR register is cleared.
In this mode the mux interface clock (fbdlc) is stopped to conserve power and allow the BDLC
module to be configured for proper operation on the J1850 bus. The IP bus interface clocks are left
running in this mode to allow access to all BDLC module registers for initialization.
•
Run
This mode is entered from the BDLC Disabled mode when the BDLCE bit in the DLCSCR register
is set. It is entered from the BDLC Wait mode whenever activity is sensed on the J1850 bus or some
other MCU source wakes the CPU out of Wait mode.
It is entered from the BDLC Stop mode whenever network activity is sensed or some other MCU
source wakes the CPU out of Stop mode. Messages will not be received properly until the clocks
have stabilized and the CPU is also in the Run mode.
•
BDLC Wait (Core Specific)
This power conserving mode is automatically entered from the Run mode whenever the CPU
executes a WAIT instruction and if the WCM bit in the DLCBCR1 register is previously cleared.
In this mode, the BDLC module internal clocks continue to run. Any activity on the J1850 network
will cause the BDLC module to exit BDLC Wait mode and generate an unmaskable interrupt of the
CPU. This wakeup interrupt state is reflected in the DLCBSVR, encoded as the highest priority
interrupt. This interrupt can be cleared by the CPU with a read of the DLCBSVR.
–
Wakeup from BDLC Wait with CPU in WAIT
If the CPU executes the WAIT instruction and the BDLC module enters the WAIT mode
(WCM = 0), the clocks to the BDLC module as well as the clocks in the MCU continue to run.
Therefore, the message which wakes up the BDLC module from WAIT and the CPU from
WAIT mode will also be received correctly by the BDLC module. This is because all of the
required clocks continue to run in the BDLC module in WAIT mode.The wakeup behavior of
the BDLC module applies regardless of whether the BDLC module is in normal or 4X mode
when the WAIT instruction is executed.
•
BDLC Stop (Core Specific)
This power conserving mode is automatically entered from the Run mode whenever the CPU
executes a STOP instruction, or if the CPU executes a WAIT instruction and the WCM bit in the
DLCBCR1 register is previously set. In this mode, the BDLC internal clocks are stopped. Any
activity on the network will cause the BDLC module to exit BDLC Stop mode and generate an
13
Block Guide — S12BDLC_BG V01.03
unmaskable interrupt of the CPU. This wakeup interrupt state is reflected in the DLCBSVR,
encoded as the highest priority interrupt. This interrupt can be cleared by the CPU with a read of
the DLCBSVR. Depending upon which low-power mode instruction the CPU executes to cause the
BDLC module to enter BDLC Stop, the message which wakes up the BDLC module (and the CPU)
may or may not be received. There are two different possibilities, both of which is described below.
These descriptions apply regardless of whether the BDLC module is in normal or 4X mode when
the STOP or WAIT instruction is executed.
–
Wakeup from BDLC Stop with CPU in STOP
When the CPU executes the STOP instruction, all clocks in the MCU, including clocks to the
BDLC module, are turned off. Therefore, the message which wakes up the BDLC module and
the CPU from STOP mode will not be received. This is due primarily to the amount of time
required for the MCU’s oscillator to stabilize before the clocks can be applied internally to the
other MCU modules, including the BDLC module.
–
Wakeup from BDLC Stop with CPU in WAIT
If the CPU executes the WAIT instruction and the BDLC module enters the Stop mode (WCM
= 1), the clocks to the BDLC module are turned off, but the clocks in the MCU continue to run.
Therefore, the message which wakes up the BDLC module from Stop and the CPU from WAIT
mode will be received correctly by the BDLC module. This is because very little time is required
for the CPU to turn the clocks to the BDLC module back on once the wakeup interrupt occurs.
NOTE:
•
While the BDLC module will correctly receive a message which arrives when the
BDLC module is in Stop mode or Wait mode and the MCU is in WAIT mode, if the
user enters this mode while a message is being received, the data in the message
will become corrupted. This is due to the steps required for the BDLC module to
resume operation upon exiting Stop mode or Wait mode, and its subsequent
resynchronization with the SAE J1850 bus.
Digital Loopback
When a bus fault has been detected, the digital loopback mode is used to determine if the fault
condition is caused by failure in the node’s internal circuits or elsewhere in the network, including
the node’s analog physical interface. In this mode, the input to the digital filter is disconnected from
the receive pin input (RXB). The input to the digital filter is then connected to the transmitter output
to form the loopback connection. The transmit pin (TXB) is negated and will always drive a passive
state onto the bus. Digital loopback mode is entered by setting the DLOOP bit in Section 3.3.3
BDLC Control Register 2 (DLCBCR2).
•
Normal and Emulation Mode Operation (Core Specific)
The BDLC module operates in the same manner in all Normal and Emulation Modes. All BDLC
module registers can be read and written except those that are reserved, unimplemented, or write
once. The user must be careful not to unintentionally write a register when using 16-bit writes in
order to avoid unexpected BDLC module behavior.
•
14
Special Mode Operation (Core Specific)
Block Guide — S12BDLC_BG V01.03
Some aspects of BDLC module operation can be modified in special test mode. This mode is
reserved for internal use only.
•
Low Power Options (Core Specific)
The BDLC module can save power in Disabled, Wait, and Stop modes. A complete description of
what the BDLC module does while in a low power mode can be found in Section 1.3 Modes of
Operation.
15
Block Guide — S12BDLC_BG V01.03
1.4 Block Diagram
To CPU
bus clock
CPU INTERFACE
CPU Interface
BCR1
8
bus clock
BCR2
BDR
BARD
Control/ Status
TX Data
TX Shadow Register
8
Protocol Handler
BSVR
8
RX Shadow Register
8
TX Data
TX Shift Register
RX Data
RX Data
RX Shift Register
Protocol State Machine
TX Data
Control/ Status
RX Data
bus clock
Symbol Encoder/Decoder
RX Data
RX Digital
Filter
TX Data
MUX Interface
RX Data
Loopback
Multiplexer
RX Data
TXB
To Physical Interface
Figure 1-2 BDLC Block Diagram
16
RXB
Block Guide — S12BDLC_BG V01.03
Figure 1-2 shows the organization of the BDLC module. The Buffers provide storage for data received
and data to be transmitted onto the J1850 bus. The Protocol Handler is responsible for the encoding and
decoding of data bits and special message symbols during transmission and reception. The MUX Interface
provides the link between the BDLC digital section and the analog Physical Interface. The wave shaping,
driving and digitizing of data is performed by the Physical Interface.
NOTE:
The Physical Interface is not implemented in the BDLC module and must be
provided externally.
The main functional blocks of the BDLC module are explained in greater detail in
the following sections.
Use of the BDLC module in message networking fully implements the “SAE
Standard J1850 Class B Data Communication Network Interface” specification.
17
Block Guide — S12BDLC_BG V01.03
18
Block Guide — S12BDLC_BG V01.03
Section 2 Signal Description
2.1 Overview
The BDLC module has a total of 2 external pins.
2.2 Detailed Signal Descriptions
2.2.1 TXB - BDLC Transmit Pin
The TXB pin serves as the transmit output channel for the BDLC module.
2.2.2 RXB - BDLC Receive Pin
The RXB pin serves as the receive input channel for the BDLC module.
19
Block Guide — S12BDLC_BG V01.03
20
Block Guide — S12BDLC_BG V01.03
Section 3 Memory Map and Registers
3.1 Overview
This section provides a detailed description of all memory and registers accessible to the end user.
3.2 Module Memory Map
Table 3-1 Module Memory Map
Address
Base + $_00
Base + $_01
Base + $_02
Base + $_03
Base + $_04
Base + $_05
Base + $_06
Base + $_07
Use
Access
BDLC Control Register 1 (DLCBCR1)
R/W
BDLC State Vector Register (DLCBSVR)
R/W
BDLC Control Register 2 (DLCBCR2)
R/W
BDLC Data Register (DLCBDR)
R/W
BDLC Analog RoundTrip Delay Register (DLCBARD)
R/W
BDLC Rate Select Register (DLCBRSR)
R/W
BDLC Control Register (DLCSCR)
R/W
BDLC Status Register (DLCBSTAT)
R/W
3.3 Register Descriptions
3.3.1 BDLC Control Register 1 (DLCBCR1)
This register is used to configure and control the BDLC module.
Register Offset: $_00
7
R
W
RESET:
6
IMSG
CLKS
1
1
5
4
3
2
0
0
0
0
0
0
0
0
1
0
IE
WCM
0
0
= Unimplemented or Reserved
Figure 3-1 BDLC Control Register 1
READ: any time
WRITE: IMSG, IE, and WCM any time.
CLKS write once in normal and emulation modes.
CLKS bit has modified functionality in special test mode.
Writes to unimplemented bits 5-2 are ignored.
21
Block Guide — S12BDLC_BG V01.03
IMSG — Ignore Message (Bit 7)
This bit allows the CPU to ignore messages by disabling updates of the DLCBSVR register until a new
Start of Frame (SOF) or a BREAK symbol is detected. BDLC module transmitter and receiver
operation are unaffected by the state of the IMSG bit.
1 = Disable DLCBSVR Updates. When set, all BDLC interrupt sources (exceptions are described
below) will be prevented from updating DLCBSVR status bits. Setting IMSG does not clear
pending interrupt flags, the behavior of which will still be as described in Section BDLC State
Vector Register (DLCBSVR). If this bit is set while the BDLC is receiving or transmitting a
message, state vector register updates will be inhibited for the rest of the message.
0 = Enable DLCBSVR Updates. This bit is automatically cleared by the reception of a SOF symbol
or a BREAK symbol. It will then allow updates of the state vector register to occur.
There are two situations in which interrupts will not be masked by the IMSG bit: when a wakeup
interrupt occurs; and when a receiver error occurs which causes a byte pending transmission to be
flushed from the transmit shadow register. See Section 3.3.4 BDLC Data Register (DLCBDR) for a
description of the conditions which cause a pending transmission to be flushed.
CLKS — Clock Select (Bit 6)
The nominal BDLC operating frequency (mux interface clock frequency - fbdlc) must always be
1.048576 MHz or 1 MHz in order for J1850 bus communications to take place properly. The CLKS
register bit is provided to allow the user to indicate to the BDLC module which frequency (1.048576
MHz or 1 MHz) is used so that each symbol time can be automatically adjusted.
The CLKS bit is a write once bit. All writes to this bit will be ignored after the first one.
1 = Binary frequency (1.048576 MHz) is used for fbdlc.
0 = Integer frequency (1 MHz) is used. for fbdlc
Section 4.1.3 J1850 VPW Valid/Invalid Bits & Symbols on page 41 describes the transmitter and
receiver VPW symbol timing for integer and binary frequencies.
IE — Interrupt Enable (Bit 1)
This bit determines whether the BDLC module will generate CPU interrupt requests. It does not affect
CPU interrupt requests when exiting the BDLC module Stop or Wait modes. Interrupt requests will be
maintained until all of the interrupt request sources are cleared, by performing the specified actions
upon the BDLC module’s registers. Interrupts that were pending at the time that this bit is cleared may
be lost.
1 = Enable interrupt requests from BDLC module
0 = Disable interrupt requests from BDLC module
If the programmer does not wish to use the interrupt capability of the BDLC module, the BDLC State
Vector Register (DLCBSVR) can be polled periodically by the programmer to determine BDLC
module states. Refer to Section 3.3.2 BDLC State Vector Register (DLCBSVR) on page 23 for a
description of DLCBSVR register and how to clear interrupt requests.
22
Block Guide — S12BDLC_BG V01.03
WCM — Wait Clock Mode (Bit 0) (Provided CPU has Low Power Mode Options)
This bit determines how the BDLC module responds when the CPU enters WAIT mode. As described
in Section 1.3 Modes of Operation on page 11, the BDLC module can respond by either entering
BDLC_STOP mode, where all internal clocks are stopped, or entering BDLC_WAIT mode where
internal clocks are allowed to run.
1 = Stop BDLC internal clocks during CPU wait mode (BDLC_STOP)
0 = Run BDLC internal clocks during CPU wait mode (BDLC_WAIT)
3.3.2 BDLC State Vector Register (DLCBSVR)
This register is provided to substantially decrease the CPU overhead associated with servicing interrupts
while under operation of a MUX protocol. It provides a index offset that is directly related to the BDLC
module’s current state, which can be used with a user supplied jump table to rapidly enter an interrupt
service routine. This eliminates the need for the user to maintain a duplicate state machine in software.
Register Offset: $_01
R
W
RESET:
7
6
5
4
3
2
1
0
0
0
I3
I2
I1
I0
0
0
0
0
0
0
0
0
0
0
= Unimplemented or Reserved
Figure 3-2 BDLC State Vector Register
READ: any time
WRITE: ignored
I[3:0] — Interrupt State Vector (Bits 5- 2)
These bits indicate the source of the interrupt request that is currently pending.
Table 3-2 Interrupt Summary
BSVR
I3
I2
I1
I0
Interrupt Source
Priority
$00
0
0
0
0
No Interrupts Pending
0 (Lowest)
$04
0
0
0
1
Received EOF
1
$08
0
0
1
0
Received IFR byte
2
$0C
0
0
1
1
Rx data register full
3
$10
0
1
0
0
Tx data register empty
4
$14
0
1
0
1
Loss of arbitration
5
$18
0
1
1
0
CRC error
6
$1C
0
1
1
1
Symbol invalid or out of range
7
$20
1
0
0
0
Wakeup
8 (Highest)
23
Block Guide — S12BDLC_BG V01.03
The state encoding of the interrupt sources mean that only one interrupt source is dealt with at a time. Once
the highest priority interrupt source is dealt with, if another interrupt event of a lower priority has also
occurred, the value corresponding to that interrupt source appears in the BSVR. This continues until all
BDLC interrupt sources have been dealt with and all bits in the BSVR are cleared.
•
Wakeup
The BDLC has two different power-conserving modes, stop and wait. Wakeup from these modes
is described below.
•
Wakeup from BDLC Wait with CPU in Wait
If the CPU executes a WAIT instruction and the BDLC enters the BDLC wait mode, the clocks to
the BDLC as well as the clocks in the MCU continue to run. The message which generates a
Wake-up interrupt of the BDLC and the CPU will be received correctly.
•
Wakeup from BDLC Stop with CPU in Wait
If the CPU executes a WAIT instruction and the BDLC enters the BDLC stop mode, the clocks to
the BDLC are turned off, but the clocks in the MCU continue to run. The message which generates
a Wake-up interrupt of the BDLC and the CPU will be received correctly. To ensure this, the EOF
following the last message appearing on the bus must be received; otherwise, the message will not
be received correctly.
•
Wakeup from BDLC Stop with CPU in Stop
If the CPU executes a STOP all clocks to the BDLC as well as the clocks in the MCU are turned
off including clocks to the BDLC. The message which generates a Wake-up interrupt of the BDLC
and the CPU will not be received correctly.
•
Symbol Invalid or Out of Range
•
CRC Error
The Cyclical Redundancy Check Byte is used by the receiver(s) of each message to determine if
any errors have occurred during the transmission of the message. If the message is not error free,
the CRC error status is shown in the BSVR.
•
Loss of Arbitration
The Loss of Arbitration status is entered when a loss of arbitration occurs while the BDLC is
transmitting onto the bus.
•
Tx Data Register Empty
The Tx Data Register Empty (TDRE) Byte is used to tell when data has been unloaded from the
BDLC Data Register (BDR).
•
Rx Data Register Full
The Rx Data Register Full (RDRF) Byte is used to tell when data has been loaded in the BDLC Data
Register (BDR).
•
Received IFR Byte
The BDLC can transmit and receive all four types of in-frame responses. As each byte of an IFR is
received, the BSVR indicates this by setting this state.
24
Block Guide — S12BDLC_BG V01.03
•
Received EOF
When a 280us passive period on the bus is received, it signifies an EOF. Whenever this occurs, the
EOF flag is set.
•
No Interrupts Pending
This interrupt cannot generate an interrupt of the CPU.
3.3.3 BDLC Control Register 2 (DLCBCR2)
This register controls transmitter operations of the BDLC module.
Register Offset: $_02
R
W
RESET:
7
6
5
4
3
2
1
0
SMRST
DLOOP
RX4XE
NBFS
TEOD
TSIFR
TMIFR1
TMIFR0
0
1
0
0
0
0
0
0
Figure 3-3 BDLC Control Register 2
READ: any time
WRITE: any time
SMRST — State Machine Reset (Bit 7)
The programmer can use this bit to reset the BDLC state machines to an initial state after the user put
the off-chip analog transceiver in loop back mode.
1 = Setting SMRST arms the state machine reset generation logic. Setting SMRST does not affect
BDLC module behavior in any way.
0 = Clearing SMRST after it has been set will cause the generation of a state machine reset. After
SMRST is cleared, the BDLC requires the bus to be idle for a minimum of an End of Frame
symbol (EOF) time before allowing the reception of a message. The BDLC requires the bus to
be idle for a minimum of an Inter-Frame Separator symbol (IFS) time before allowing any
message to be transmitted.
DLOOP — Digital Loopback Mode (Bit 6)
This bit determines the source to which the input of the digital filter is connected and can be used to
isolate bus fault conditions. If a fault condition has been detected on the bus, this control bit allows the
programmer to disconnect the digital filter from input from the receive pin (RXB) and connect it to the
transmit output to the pin (TXB). In this configuration, data sent from the transmit buffer should be
reflected back into the receive buffer. If no faults exist in the digital block, the fault is in the physical
interface block or elsewhere on the J1850 bus.
25
Block Guide — S12BDLC_BG V01.03
1 = When set, digital filter input is connected to the transmitter output. The BDLC module is now
in Digital Loopback Mode of operation. The transmit pin (TXB) is driven low and not driven
by the transmitter output.
0 = When cleared, digital filter input is connected to receive pin (RXB) and the transmitter output
is connected to the transmit pin (TXB). The BDLC module is taken out of Digital Loopback
Mode and can now drive and receive from the J1850 bus normally. After writing DLOOP to
zero, the BDLC module requires the bus to be idle for a minimum of an End of Frame symbol
time before allowing a reception of a message. The BDLC module requires the bus to be idle
for a minimum of an Inter-Frame Separator symbol time before allowing any message to be
transmitted.
NOTE:
The DLOOP bit is a fault condition aid and should never be altered after the
DLCBDR is loaded for transmission. Changing DLOOP during a transmission may
cause corrupted data to be transmitted onto the J1850 network.
RX4XE — Receive 4X Enable (Bit 5)
This bit determines if the BDLC operates at normal transmit and receive speed (10.4 kbps) or receive
only at 41.6 kbps. This feature is useful for fast download of data into a J1850 node for diagnostic or
factory programming of the node.
1 = When set, the BDLC module is put in 4X (41.6 kbps) receive only operation.
0 = When cleared, the BDLC module transmits and receives at 10.4 kbps. Reception of a BREAK
symbol automatically clears this bit and sets the symbol invalid or out of range flag
(DLCBSVR = $1C).
The effect of 4X receive operation on receive symbol timing boundaries is described in Transmit and
Receive Symbol Timing Specifications.The RX4XE bit is not affected by entry or exit from BDLC
stop or wait modes.
NBFS — Normalization Bit Format Select (Bit 4)
This bit controls the format of the Normalization Bit (NB). SAE J1850 strongly encourages the use of
an active long: ‘0’ for In-Frame Responses containing CRC and active short, ‘1’ for In-Frame
Responses without CRC.
1 = NB that is received or transmitted is a ‘0’ when the response part of an In-Frame Response (IFR)
ends with a CRC byte. NB that is received or transmitted is a ‘1’ when the response part of an
In-Frame Response (IFR) does not end with a CRC byte.
0 = NB that is received or transmitted is a ‘1’ when the response part of an In-Frame Response (IFR)
ends with a CRC byte. NB that is received or transmitted is a ‘0’ when the response part of an
In-Frame Response (IFR) does not end with a CRC byte.
TEOD — Transmit End of Data (Bit 3)
This bit is set by the programmer to indicate the end of a message being sent by the BDLC. It will
append an 8-bit CRC after completing transmission of the current byte in the Tx Shift Register
followed by the EOD symbol. If the transmit shadow register (refer to Rx & Tx Shadow Registers for
a description of the transmit shadow register) is full when TEOD is set, the CRC byte and EOD will
be transmitted after the current byte in the Tx Shift Register and the byte in the Tx Shadow Register
have been transmitted. Once TEOD is set, the transmit data register empty flag (TDRE) in the BDLC
26
Block Guide — S12BDLC_BG V01.03
State Vector Register (DLCBSVR) is cleared to allow lower priority interrupts to occur. This bit is also
used to end an IFR. Bits TSIFR, TMIFR1, and TMIFR0 determine whether a CRC byte is appended
before EOD transmission for IFRs.
1 = Transmit EOD symbol.
0 = The TEOD bit will be automatically cleared after the first CRC bit is sent, or if an error or loss
of arbitration is detected on the bus. When TEOD is used to end an IFR transmission, TEOD
is cleared when the BDLC receives back a valid EOD symbol, or an error condition or loss of
arbitration occurs.
TSIFR, TMIFR1, TMIFR0 — Transmit In-Frame Response Control (Bits 2-0)
These three bits control the type of In-Frame Response being sent. The programmer should not set
more than one of these control bits to a one at any given time. However, if more than one of these three
control bits are set to one, the priority encoding logic will force the internal register bits to a known
value as shown in the following table. But, when these bits are read, they will be the same as written
earlier. For instance, if “011” is written to TSIFR, TMIFR1, TMIFR0, then internally, they’ll be
encoded as “010”. However, when these bits are later read back, it’ll still be “011”.
Table 3-3 Transmit In-Frame Response Control Bit Priority Encoding
WRITE
TSIFR
TMIFR1 TMIFR0
TSIFR
READ
ACTUAL (internal register)
TMIFR1 TMIFR0
TSIFR
TMIFR1 TMIFR0
0
0
0
0
0
0
0
0
0
1
X
X
1
X
X
1
0
0
0
1
X
0
1
X
0
1
0
0
0
1
0
0
1
0
0
1
The BDLC supports the In-frame Response (IFR) feature of J1850 by setting these bits correctly. The
four types of J1850 IFR are shown in Figure 3-4. The purpose of the in-frame response modes is to
allow single or multiple nodes to acknowledge receipt of the data by responding to a received message
after they have seen the EOD symbol. For VPW modulation, the first bit of the IFR is always passive;
therefore, an active normalization bit must be generated by the responder and sent prior to its
ID/address byte. When there are multiple responders on the J1850 bus, only one normalization bit is
sent which assists all other transmitting nodes to sync their responses.
27
Block Guide — S12BDLC_BG V01.03
CRC
CRC
EOD
Data Field
EOF
EOD
SOF
Header
Type 0 - No IFR
Data Field
NB
EOF
EOD
SOF
Header
ID
Type 1 - Single Byte From a Single Responder (without CRC)
CRC
NB
ID1
EOF
EOD
Data Field
EOD
SOF
Header
ID n
Type 2 - Single Byte From Multiple Responders (without CRC)
CRC
NB
IFR Data Field
CRC
EOF
EOD
Data Field
EOD
SOF
Header
Type 3 - Multiple Bytes From a Single Responder (with or without CRC)
Figure 3-4 Types of In-Frame Response
TSIFR — Transmit Single Byte IFR with no CRC (Type 1 or 2)
This bit is used to request the BDLC to transmit the byte in the BDLC Data Register (DLCBDR) as a
single byte IFR with no CRC. Typically, the byte transmitted is a unique identifier or address of the
transmitting (responding) node.
1 = If this bit is set prior to a valid EOD being received with no CRC error, once the EOD symbol
has been received the BDLC module will attempt to transmit the appropriate normalization bit
followed by the byte in the DLCBDR.
0 = The TSIFR bit will be automatically cleared once the EOD following one or more IFR bytes
has been received or an error is detected on the bus.
The user must set the TSIFR bit before the EOF following the main part of the message frame is
received, or no IFR transmit attempts will be made for the current message. If another node transmits
an IFR to this message, the user must set the TSIFR bit before the normalization bit is received or no
IFR transmit attempts will be made for the message. If another node does transmit a successful IFR or
a reception error occurs, the TSIFR bit will be cleared. If not, the IFR will be transmitted after the EOD
of the next received message.
If a loss of arbitration occurs when the BDLC module attempts transmission, after the IFR byte
winning arbitration completes transmission, the BDLC module will again attempt to transmit the byte
in the DLCBDR (with no normalization bit). The BDLC module will continue transmission attempts
until an error is detected on the bus, or TEOD is set by the CPU, or the BDLC transmission is
successful.
NOTE:
28
Setting the TEOD bit before transmission of the IFR byte will direct the BDLC to
make only one attempt at transmitting the byte.
Block Guide — S12BDLC_BG V01.03
If loss of arbitration occurs in the last bit of the IFR byte, two additional ‘1’ bits will not be sent out
because the BDLC will attempt to retransmit the byte in the transmit shift register after the IFR byte
winning arbitration completes transmission.
TMIFR1 — Transmit Multiple Byte IFR with CRC (Type 3)
This bit requests the BDLC module to transmit the byte in the BDLC Data Register (DLCBDR) as the
first byte of a multiple byte IFR with CRC or as a single byte IFR with CRC.Response IFR bytes are
still subject to J1850 message length maximums.
1 = If this bit is set prior to a valid EOD being received with no CRC error, once the EOD symbol
has been received, the BDLC module will attempt to transmit the appropriate normalization bit
followed by IFR bytes.The programmer should set TEOD after the last IFR byte has been
written into DLCBDR register. After TEOD has been set and the last IFR byte has been
transmitted, the CRC byte is transmitted.
0 = The TMIFR1 bit will be automatically cleared once the BDLC module has successfully
transmitted the CRC byte and EOD symbol, by the detection of an error on the multiplex bus,
a transmitter underrun, or loss of arbitration.
After the byte in the DLCBDR has been loaded into the transmit shift register, the TDRE flag will be
set in the DLCBSVR register, similar to the main message transmit sequence. If the interrupt enable
bit (IE in DLCBCR1) is set, an interrupt request from the BDLC module is generated.The programmer
should then load the next byte of the IFR into the DLCBDR for transmission. When the last byte of the
IFR has been loaded into the DLCBDR, the programmer should set the TEOD bit in the BDLC control
register 2 (DLCBCR2). This will instruct the BDLC module to transmit a CRC byte once the byte in
the DLCBDR is transmitted, and then transmit an EOD symbol, indicating the end of the IFR portion
of the message frame.
However, if the programmer wishes to transmit a single byte followed by a CRC byte, the programmer
should load the byte into the DLCBDR and then set the TMIFR1 bit before the EOD symbol has been
received. Once the TDRE flag is set and interrupt occurs (if enabled), the programmer should then set
the TEOD bit in DLCBCR2. This will result in the byte in the DLCBDR being the only byte
transmitted before the IFR CRC byte.
The user must set the TMIFR1 bit before the EOF following the main part of the message frame is
received, or no IFR transmit attempts will be made for the current message. If another node transmits
an IFR to this message, the user must set the TMIFR1 bit before the normalization bit is received or
no IFR transmit attempts will be made for the message. If another node does transmit a successful IFR
or a reception error occurs, the TMIFR1 bit will be cleared. If not, the IFR will be transmitted after the
EOD of the next received message.
If a transmitter underrun error occurs during transmission (caused by the programmer not writing
another byte to the DLCBDR following the TDRE flag being set) the BDLC module will automatically
disable the transmitter after the byte currently in the shifter plus two extra 1-bits have been transmitted.
The receiver will pick this up as an framing error and relay it in the State Vector Register as an invalid
symbol error. The TMIFR1 bit will also be cleared.
29
Block Guide — S12BDLC_BG V01.03
If a loss of arbitration occurs when the BDLC module is transmitting a multiple byte IFR with CRC,
the BDLC module will go to the loss of arbitration state, set the appropriate flag and cease
transmission. The TMIFR1 bit will be cleared and no attempt will be made to retransmit the byte in
the DLCBDR. If loss of arbitration occurs in the last bit of the IFR byte, two additional one bits (a
passive long followed by an active short) will be sent out.
NOTE:
The extra logic 1s are an enhancement to the J1850 protocol which forces a byte
boundary condition fault. This is helpful in preventing noise on the J1850 bus from
corrupting a message.
TMIFR0 — Transmit Multiple Byte IFR with no CRC (Type 3)
This bit is used to request the BDLC module to transmit the byte in the BDLC Data Register
(DLCBDR) as the first byte of a multiple byte IFR without CRC. Response IFR bytes are still subject
to J1850 message length maximums.
1 = If this bit is set prior to a valid EOD being received with no CRC error, once the EOD symbol
has been received the BDLC module will attempt to transmit the appropriate normalization bit
followed by IFR bytes. The programmer should set TEOD after the last IFR byte has been
written into DLCBDR register. After TEOD has been set, the last IFR byte to be transmitted
will be the last byte which was written into the DLCBDR register.
0 = The TMIFR0 bit will be automatically cleared once the BDLC module has successfully
transmitted the EOD symbol, by the detection of an error on the multiplex bus, a transmitter
underrun, or loss of arbitration.
After the byte in the DLCBDR has been loaded into the transmit shift register, the TDRE flag will be
set in the DLCBSVR register, similar to the main message transmit sequence. If the interrupt enable
bit (IE in DLCBCR1) is set, an interrupt request from the BDLC module is generated. The programmer
should then load the next byte of the IFR into the DLCBDR for transmission. When the last byte of the
IFR has been loaded into the DLCBDR, the programmer should set the TEOD bit in the DLCBCR2
register. This will instruct the BDLC to transmit an EOD symbol, indicating the end of the IFR portion
of the message frame. The BDLC module will not append a CRC.
However, if the programmer wishes to transmit a single byte, the programmer should load the byte into
the DLCBDR and then set the TMIFR0 bit before the EOD symbol has been received. Once the TDRE
flag is set and interrupt occurs (if enabled), the programmer should then set the TEOD bit in
DLCBCR2. This will result in the byte in the DLCBDR being the only byte transmitted.
The user must set the TMIFR0 bit before the EOF following the main part of the message frame is
received, or no IFR transmit attempts will be made for the current message. If another node transmits
an IFR to this message, the user must set the TMIFR0 bit before the normalization bit is received or
no IFR transmit attempts will be made for the message. If another node does transmit a successful IFR
or a reception error occurs, the TMIFR0 bit will be cleared. If not, the IFR will be transmitted after the
EOD of the next received message.
If a transmitter underrun error occurs during transmission (caused by the programmer not writing
another byte to the DLCBDR following the TDRE flag being set) the BDLC module will automatically
disable the transmitter after the byte currently in the shifter plus two extra 1-bits have been transmitted.
The receiver will pick this up as an framing error and relay it in the State Vector Register as an invalid
symbol error. The TMIFR0 bit will also be cleared.
30
Block Guide — S12BDLC_BG V01.03
If a loss of arbitration occurs when the BDLC module is transmitting a multiple byte IFR without CRC,
the BDLC module will go to the loss of arbitration state, set the appropriate flag and cease
transmission. The TMIFR0 bit will be cleared and no attempt will be made to retransmit the byte in
the DLCBDR. If loss of arbitration occurs in the last bit of the IFR byte, two additional one bits (a
passive long followed by an active short) will be sent out.
NOTE:
The extra logic 1s are an enhancement to the J1850 protocol which forces a byte
boundary condition fault. This is helpful in preventing noise on the J1850 bus from
corrupting a message.
3.3.4 BDLC Data Register (DLCBDR)
This register is used to pass the data to be transmitted to the J1850 bus from the CPU to the BDLC module.
It is also used to pass data received from the J1850 bus to the CPU.
Register Offset: $_03
R
W
RESET:
7
6
5
4
3
2
1
0
D7
D6
D5
D4
D3
D2
D1
D0
0
0
0
0
0
0
0
0
Figure 3-5 BDLC Data Register
READ: any time
WRITE: any time
D7:D0 — Receive/Transmit Data (Bits 7 - 0)
While transmitting, each data byte (after the first one) should be written only after a “Tx Data Register
Empty” (TDRE) interrupt has occurred, or the DLCBSVR register has been polled indicating this
condition.
Data read from this register will be the last data byte received from the J1850 bus. This received data
should only be read after a “Rx Data Register Full” (RDRF) or “Received IFR byte” (RXIFR) interrupt
has occurred or the DLCBSVR register has been polled indicating either of these two conditions.
The DLCBDR register is double buffered via a transmit shadow register and a receive shadow register.
After the byte in the transmit shift register has been transmitted, the byte currently stored in the
transmit shadow register is loaded into the transmit shift register. Once the transmit shift register has
shifted the first bit out, the TDRE flag is set, and the shadow register is ready to accept the next byte
of data.
The receive shadow register works similarly. Once a complete byte has been received, the receive shift
register stores the newly received byte into the receive shadow register. The RDRF flag (or RXIFR
flag if the received byte is part of an IFR) is set to indicate that a new byte of data has been received.
The programmer has one BDLC module byte reception time to read the shadow register and clear the
RDRF or RXIFR flag before the shadow register is overwritten by the newly received byte.
31
Block Guide — S12BDLC_BG V01.03
If the user writes the first byte of a message to be transmitted to the DLCBDR and then determines that
a different message should be transmitted, the user can write a new byte to the DLCBDR up until the
transmission begins.This new byte will replace the original byte in the DLCBDR.
From the time a byte is written to the DLCBDR until it is transferred to the transmit shift register, the
transmit shadow register is considered full and the byte pending transmission. If one of the IFR
transmission control bits (TSIFR, TMIFR1, or TMIFR0 in DLCBCR2) is also set, the byte is pending
transmission as an IFR. A byte pending transmission will be flushed from the transmit shadow register
and the transmission canceled if one of the following occurs: a loss of arbitration or transmitter error
on the byte currently being transmitted; a symbol error, framing error, bus fault, or BREAK symbol is
received. If the byte pending transmission is an IFR byte, the reception of a message with a CRC error
will also cause the byte in the transmit shadow register to be flushed.
To abort an in-progress transmission, the programmer should simply stop loading more data into the
BDR. This will cause a transmitter underrun error and the BDLC module will automatically disable
the transmitter on the next non-byte boundary. This means that the earliest a transmission can be halted
is after at least one byte (plus two extra 1-bits) has been transmitted. The receiver will pick this up as
an error and relay it in the State Vector Register as an invalid symbol error.
3.3.5 BDLC Analog Round Trip Delay Register (DLCBARD)
This register is used to program the BDLC module so that it compensates for the round trip delays of
different external transceivers. Also the polarity of the receive pin (RXB) is set in this register.
Register Offset: $_04
7
R
W
RESET:
0
0
6
RXPOL
1
5
4
0
0
0
0
3
2
1
0
BO3
BO2
BO1
BO0
0
1
1
1
= Unimplemented
Figure 3-6 BDLC Analog Round Trip Delay Register
READ: any time
WRITE: write once in normal and emulation modes.
Register functionality modified in special test mode.
Writes to unimplemented bits 7, 5, 4 are ignored.
RXPOL — Receive Pin Polarity (Bit 6)
The Receive pin Polarity bit is used to select the polarity of incoming signal on the receive pin. Some
external analog transceiver inverts the receive signal from the J1850 bus before feeding back to the
digital receive pin.
32
Block Guide — S12BDLC_BG V01.03
1 = Select normal/true polarity; true non-inverted signal from J1850 bus, i.e., the external
transceiver does not invert the receive signal.
0 = Select inverted polarity, where external transceiver inverts the receive signal.
BO3-BO0 — BDLC Analog Roundtrip Delay Offset Field (Bits 3-0)
BO[3:0] adjust the transmitted symbol timings to account for the differing roundtrip delays found in
different SAE J1850 analog transceivers. The allowable delay range is from 9 ms to 24 ms, with a
nominal target of 16 ms (reset value). Refer to Table 3-4 for the BO[3:0] values corresponding to the
expected transceiver delays and the resultant transmitter timing adjustment (in mux interface clock
periods (tbdlc)). Refer to the analog transceiver device specification for the expected roundtrip delay
through both the transmitter and the receiver. The sum of these two delays makes up the total roundtrip
delay value.
Table 3-4 BARD Values vs. Transceiver Delay and Transmitter Timing Adjustment
BARD Offset Bits
(BO3,BO2,BO1,BO0)
Corresponding Expected
Transceiver’s delays (µs)
Transmitter Symbol Timing
Adjustment (tbdlc)1
0000
9
9
0001
10
10
0010
11
11
0011
12
12
0100
13
13
0101
14
14
0110
15
15
0111
16
16
1000
17
17
1001
18
18
1010
19
19
1011
20
20
1100
21
21
1101
22
22
1110
23
23
1111
24
24
NOTE:
1. The transmitter symbol timing adjustment is the same for binary and integer bus frequencies.
3.3.6 BDLC Rate Select Register (DLCBRSR)
This register determines the divider prescaler value for the mux interface clock (fbdlc).
33
Block Guide — S12BDLC_BG V01.03
Register Offset: $_05
7
6
0
0
Unimplemented
0
0
R
W
RESET:
5
4
3
2
1
0
R5
R4
R3
R2
R1
R0
0
0
0
0
0
0
= Unimplemented
Figure 3-7 BDLC Rate Select Register
READ: any time
WRITE: write once in normal and emulation modes.
Register functionality modified in special test mode.
Writes to unimplemented bits 7, 6 are ignored.
NOTE:
After writing to the divide rate register, the divide counter will start counting ONLY
after the next access to the BDLC register space. E.g. write the module enable bit
after writing to the divide rate register.
R5-R0 — Rate Select (Bits 5-0)
These bits determine the amount by which the frequency of the system clock signal is divided to
generate the MUX Interface clock (fbdlc) which defines the basic timing resolution of the MUX
Interface. The value programmed into these bits is dependent on the chosen system clock frequency.
See Table 3-5 and Table 3-6 for example rate selects for different bus frequencies. All divisor values
from divide by 1 to divide by 64 are possible, but are not shown in the tables.
NOTE:
Although the maximum divider is 64, a divider which will generate a 1 MHz or
1.048576 MHz fbdlc must be selected in order for J1850 communications to occur.
Table 3-5 BDLC Rate Selection for Binary Frequencies [CLKS = 1]
34
IP bus clock frequency
R[5:0]
division
fbdlc
fCLOCK=1.048576 MHz
$00
1
1.048576 MHz
fCLOCK=2.09715 MHz
$01
2
1.048576 MHz
fCLOCK=3.14573 MHz
$02
3
1.048576 MHz
fCLOCK=4.19430 MHz
$03
4
1.048576 MHz
fCLOCK=8.38861 MHz
$07
8
1.048576 MHz
fCLOCK=10.48576 MHz
$09
10
1.048576 MHz
fCLOCK=67.10886 MHz
$3F
64
1.048576 MHz
Block Guide — S12BDLC_BG V01.03
Table 3-6 BDLC Rate Selection for Integer Frequencies [CLKS = 0]
IP bus clock frequency
R[5:0]
division
fbdlc
fCLOCK=1.00000 MHz
$00
1
1.000000 MHz
fCLOCK=2.00000 MHz
$01
2
1.000000 MHz
fCLOCK=3.00000 MHz
$02
3
1.000000 MHz
fCLOCK=4.00000 MHz
$03
4
1.000000 MHz
fCLOCK=8.00000 MHz
$07
8
1.000000 MHz
fCLOCK=10.00000 MHz
$09
10
1.000000 MHz
fCLOCK=64.00000 MHz
$3F
64
1.000000 MHz
3.3.7 BDLC Control Register (DLCSCR)
The following register enables the BLDC module.
Register Offset: $_06
R
W
RESET:
7
6
5
0
0
0
0
0
0
4
BDLCE
0
3
2
1
0
0
0
0
0
0
0
0
0
= Unimplemented
Figure 3-8 BDLC Control Register
READ: any time
WRITE: any time
BDLCE — BDLC Enable (Bit 4)
This bit serves as a mux interface clock (fbdlc) enable/disable for power savings.
1 = The mux interface clock (fbdlc) and BDLC module are enabled to allow J1850 communications
to take place.
0 = The mux interface clock (fbdlc) is disabled, shutting down the BDLC module for power saving.
Bus clocks are still running allowing registers to be accessed.
3.3.8 BDLC Status Register (DLCBSTAT)
This register Indicates the status of the BLDC module.
35
Block Guide — S12BDLC_BG V01.03
Register Offset: $_07
R
W
RESET:
7
6
5
4
3
2
0
0
0
0
0
0
0
Unimplemented
0
0
0
0
Reserved
0
1
0
0
IDLE
Unimplemented
0
0
= Unimplemented
Figure 3-9 BDLC Status Register
READ: any time
WRITE: ignored in normal and emulation modes
Register functionality is modified in special test mode.
IDLE Idle (Bit 0)
This bit indicates when the BDLC module is idle.
1 = BDLC module has received IFS and no data is being transmitted or received.
0 = BDLC module is either transmitting or receiving data.
NOTE:
36
BDLC module is only idle after receiving IFS. The IDLE bit is 0 during reset since
the BDLC module needs to wait for an IFS before becoming idle. Noise on the bus
will be filtered and the IDLE bit will remain unchanged.
Block Guide — S12BDLC_BG V01.03
Section 4 Functional Description
4.1 General
The BDLC module is a serial communication module which allows the user to send and receive messages
across a Society of Automotive Engineers (SAE) J1850 serial communication network. The user’s
software handles each transmitted or received message on a byte-by-byte basis, while the BDLC performs
all of the network access, arbitration, message framing and error detection duties.
4.1.1 J1850 Frame Format
As noted above and in Section 1.2 Features on page 11, the BDLC module communicates across an SAE
J1850 network. As such, all messages transmitted on the J1850 bus are structured using the format below.
The following sections describe this format and it’s meanings.
Idle
SOF
Priority Message
(Data0) ID (Data1)
Datan
CRC
E
O
D
Optional
IFR
I
F
EOF S Idle
Figure 4-1 J1850 Bus Message Format (VPW)
SAE J1850 states that each message has a maximum length of 101 bit times or 12 bytes (excluding SOF,
EOD, NB and EOF).
•
SOF - Start of Frame Symbol
All messages transmitted onto the J1850 bus must begin with an long active SOF symbol. This
indicates to any listeners on the J1850 bus the start of a new message transmission. The SOF symbol
is not used in the CRC calculation.
•
Data - In Message Data Bytes
The data bytes contained in the message include the message priority/type, message I.D. byte, and
any actual data being transmitted to the receiving node. See SAE J1850 - Class B Data
Communications Network Interface, for more information about 1 and 3 Byte Headers.
Messages transmitted by the BDLC module onto the J1850 bus must contain at least one data byte,
and therefore can be as short as one data byte and one CRC byte. Each data byte in the message is
8 bits in length, transmitted MSB to LSB.
•
CRC - Cyclical Redundancy Check Byte
37
Block Guide — S12BDLC_BG V01.03
This byte is used by the receiver(s) of each message to determine if any errors have occurred during
the transmission of the message. The BDLC calculates the CRC byte and appends it onto any
messages transmitted onto the J1850 bus, and also performs CRC detection on any messages it
receives from the J1850 bus.
CRC generation uses the divisor polynomial X8+X4+X3+X2+1. The remainder polynomial is
initially set to all ones, and then each byte in the message after the SOF symbol is serially processed
through the CRC generation circuitry. The one’s complement of the remainder then becomes the
8-bit CRC byte, which is appended to the message after the data bytes, in MSB to LSB order.
When receiving a message, the BDLC uses the same divisor polynomial. All data bytes, excluding
the SOF and EOD symbols, but including the CRC byte, are used to check the CRC. If the message
is error free, the remainder polynomial will equal X7+X6+X2 ($C4), regardless of the data
contained in the message. If the calculated CRC does not equal $C4, the BDLC will recognize this
as a CRC error and set the CRC error flag in the BSVR register.
•
EOD - End of Data Symbol
The EOD symbol is a long passive period on the J1850 bus used to signify to any recipients of a
message that the transmission by the originator has completed. No flag is set upon reception of the
EOD symbol.
•
IFR - In Frame Response Bytes
The IFR section of the J1850 message format is optional. Users desiring further definition of
in-frame response should review the “SAE J1850 Class B Data Communications Network
Interface” specification.
•
EOF - End of Frame Symbol
This symbol is a passive period on the J1850 bus, longer than an EOD symbol, which signifies the
end of a message. Since an EOF symbol is longer than an EOD symbol, if no response is transmitted
after an EOD symbol, it becomes an EOF, and the message is assumed to be completed. The EOF
flag is set upon receiving the EOF symbol.
•
IFS - Inter-Frame Separation Symbol
The IFS symbol is a passive period on the J1850 bus which allows proper synchronization between
nodes during continuous message transmission. The IFS symbol is transmitted by a node following
the completion of the EOF period.
When the last byte of a message has been transmitted onto the J1850 bus, and the EOF symbol time
has expired, all nodes must then wait for the IFS symbol time to expire before transmitting an SOF,
marking the beginning of another message.
However, if the BDLC module is waiting for the IFS period to expire before beginning a
transmission and a rising edge is detected before the IFS time has expired, it will internally
synchronize to that edge.
A rising edge may occur during the IFS period because of varying clock tolerances and loading of
the J1850 bus, causing different nodes to observe the completion of the IFS period at different
times. Receivers must synchronize to any SOF occurring during an IFS period to allow for
individual clock tolerances.
38
Block Guide — S12BDLC_BG V01.03
•
Break
If the BDLC module is transmitting at the time a BREAK is detected, it treats the BREAK as if a
transmission error had occurred, and halts transmission.The BDLC module cannot transmit a
BREAK symbol. If while receiving a message the BDLC module detects a BREAK symbol, it treats
the BREAK as a reception error and sets the invalid symbol flag. If while receiving a message in
4X mode, the BDLC module detects a BREAK symbol, it treats the BREAK as a reception error,
sets BSVR register to $1C, and exits 4X mode.The RX4XE bit in BCR2 is automatically cleared
upon reception of the BREAK symbol.
•
Idle Bus
An idle condition exists on the bus during any passive period after expiration of the IFS period. Any
node sensing an idle bus condition can begin transmission immediately.
4.1.2 J1850 VPW Symbols
Variable Pulse Width modulation (VPW) is an encoding technique in which each bit is defined by the time
between successive transitions, and by the level of the bus between transitions, active or passive. Active
and passive bits are used alternately. This encoding technique is used to reduced the number of bus
transitions for a given bit rate. See Section 1.2 Features on page 11.
The symbol values shown below are nominal values. Refer to the electrical specification for a more
complete description of symbol values. Each logic one or logic zero contains a single transition, and can
be at either the active or passive level and one of two lengths, either 64µs or 128µs (TNOM at 10.4kbps
baud rate), depending upon the encoding of the previous bit. The SOF, EOD, EOF and IFS symbols will
always be encoded at an assigned level and length. See Figure 4-2.
39
Block Guide — S12BDLC_BG V01.03
Active
128µs
OR
64µs
OR
64µs
Passive
Logic “0”
(a)
Active
128µs
Passive
Logic “1”
(b)
Active
200µs
200µs
Start of Frame
(c)
End of Data
(d)
Passive
Active
280µs
≥ 240µs
End of Frame
(e)
Break
(f)
Passive
Active
20µs
EOD
EOF
Passive
300µs
Inter-Frame Seperator (IFS)
(g)
Figure 4-2 J1850 VPW Symbols
Each message will begin with an SOF symbol, an active symbol, and therefore each data byte (including
the CRC byte) will begin with a passive bit, regardless of whether it is a logic one or a logic zero. All VPW
bit lengths stated in the following descriptions are typical values at a 10.4kbps bit rate.
•
40
Logic “0”
Block Guide — S12BDLC_BG V01.03
A logic zero is defined as either an active to passive transition followed by a passive period 64µs in
length, or a passive to active transition followed by an active period 128µs in length (Figure
4-2(a)).
•
Logic “1”
A logic one is defined as either an active to passive transition followed by a passive period 128µs
in length, or a passive to active transition followed by an active period 64µs in length (Figure
4-2(b)).
•
NB - Normalization Bit
The NB symbol has the same property as a logic “1” or a logic “0”.It is only used in IFR message
responses. This bit is defined as an active bit.
•
SOF - Start of Frame Symbol
The SOF symbol is defined as passive to active transition followed by an active period 200µs in
length (Figure 4-2(c)). This allows the data bytes which follow the SOF symbol to begin with a
passive bit, regardless of whether it is a logic one or a logic zero.
•
EOD - End of Data Symbol
The EOD symbol is defined as an active to passive transition followed by a passive period 200µs
in length (Figure 4-2(d)).
•
EOF - End of Frame Symbol
The EOF symbol is defined as an active to passive transition followed by a passive period 280µs in
length (Figure 4-2(e)). If there is no IFR byte transmitted after an EOD symbol is transmitted, after
another 80µs the EOD becomes an EOF, indicating the completion of the message.
•
IFS - Inter-Frame Separation Symbol
The IFS symbol is defined as a passive period 300µs in length. The IFS symbol contains no
transition, since when used it always follows an EOF symbol.(Figure 4-2(g))
•
BREAK - Break Signal
The BREAK signal is defined as a passive to active transition followed by an active period of at
least 240µs (Figure 4-2(f)).
•
IDLE
An IDLE is defined as a passive period greater than 300µs in length.
4.1.3 J1850 VPW Valid/Invalid Bits & Symbols
The timing tolerances for receiving data bits and symbols from the J1850 bus have been defined to allow
for variations in oscillator frequencies. In many cases the maximum time allowed to define a data bit or
symbol is equal to the minimum time allowed to define another data bit or symbol.
Since the minimum resolution of the BDLC module for determining what symbol is being received is
equal to a single period of the MUX Interface clock, (tbdlc). i.e. the receiver symbol timing boundaries are
subject to an uncertainty of 1 tbdlc due to sampling considerations.
41
Block Guide — S12BDLC_BG V01.03
This clock resolution of 1 tbdlc allows the BDLC module to properly differentiate between the different
bits and symbols, without reducing the valid window for receiving bits and symbols from transmitters onto
the J1850 bus having varying oscillator frequencies.
•
Transmit and Receive Symbol Timing Specifications
Tables 4-1 through 4-6 contain the SAE J1850 transmit and receive symbol timing specifications
for the BDLC module. The units used in these tables are mux interface clock periods (tbdlc). The
mux interface clock is a divided down version of the bus clock input to the module (see Section
3.3.6 BDLC Rate Select Register (DLCBRSR)). The mux interface clock drives the transmit and
receive counters which control symbol generation and identification. The symbol timing in effect
during J1850 operations is dependent the state of two control bits: the CLKS bit DLCBCR1, which
indicates whether the bus clock is an integer frequency or a binary frequency; the RX4XE bit in
DLCBCR2, which is used to select 4X receiver operation.
Tables 4-1 and 4-3 indicate the transmit and receive timing for integer bus frequencies (CLKS = 0) and
4X receive operation disabled (RX4XE = 0). It is assumed that for integer bus frequencies the divided
down mux interface clock frequency will be 1MHz (tbdlc = 1 ms).
Tables 4-2 and 4-4 indicated the transmit and receive timing for binary bus frequencies (CLKS = 1) and
4X receive operation disabled (RX4XE = 0). It is assumed that for binary bus frequencies the divided down
mux interface clock frequency will be 1.048576 MHz (tbdlc = 0.953674 ms). The symbol timing values are
adjusted to compensate for the shortening of the mux interface clock period.
Tables 4-5 and 4-6 show how the receive symbol timing values are adjusted when 4X receive operation
is enabled (RX4XE = 1) for both integer bus frequencies (CLKS = 0) and binary bus frequencies (CLKS
= 1), respectively.
The values specified in the tables are for the symbols appearing on the SAE J1850 bus. These values
assume the BDLC module is communicating on the SAE J1850 bus using an external analog transceiver,
and that the BDLC module analog roundtrip delay value programed into the DLCBARD register is the
appropriate value for the transceiver being used. If these conditions are not met, the symbol timings being
measured on the SAE J1850 bus will be significantly affected. For a detailed description of how symbol
timings are measured on the SAE J1850 bus, refer to the appropriate SAE documents.
Table 4-1 BDLC Transmitter VPW Symbol Timing for Integer Frequencies
Number
42
Characteristic
1
Passive Logic 0
Symbol
Ttvp1
Min
Typ
Max
62
64
66
Unit
tbdlc
2
Passive Logic 1
Ttvp2
126
128
130
tbdlc
3
Active Logic 0
Ttva1
126
128
130
tbdlc
4
Active Logic 1
Ttva2
62
64
66
tbdlc
5
Start of Frame (SOF)
Ttva3
198
200
202
tbdlc
6
End of Data (EOD)1
Ttvp3
162
164
166
tbdlc
7
End of Frame (EOF)1
Ttv4
238
240
242
tbdlc
8
Inter-Frame Separator (IFS)1
Ttv5
298
300
302
tbdlc
Block Guide — S12BDLC_BG V01.03
Table 4-1 BDLC Transmitter VPW Symbol Timing for Integer Frequencies
Number
Characteristic
Symbol
Min
Typ
Max
Unit
NOTE:
1. The transmitter timing for this symbol depends upon the minimum detection time of the symbol by the
receiver.
Table 4-2 BDLC Transmitter VPW Symbol Timing for Binary Frequencies
Number
Characteristic
1
Passive Logic 0
Symbol
Ttvp1
Min
Typ
Max
65
67
69
Unit
tbdlc
2
Passive Logic 1
Ttvp2
132
134
136
tbdlc
3
Active Logic 0
Ttva1
132
134
136
tbdlc
4
Active Logic 1
Ttva2
65
67
69
tbdlc
5
Start of Frame (SOF)
Ttva3
208
210
212
tbdlc
6
End of Data (EOD)1
Ttvp3
170
172
174
tbdlc
7
End of Frame (EOF)1
Ttv4
250
252
254
tbdlc
8
Inter-Frame Separator (IFS)1
Ttv5
313
315
317
tbdlc
NOTE:
1. The transmitter timing for this symbol depends upon the minimum detection time of the symbol by the
receiver.
Table 4-3 BDLC Receiver VPW Symbol Timing for Integer Frequencies
Number
Characteristic
1
Passive Logic 0
Symbol
Trvp1
Min
Typ
Max
32
64
95
Unit
tbdlc
2
Passive Logic 1
Trvp2
96
128
163
tbdlc
3
Active Logic 0
Trva1
96
128
163
tbdlc
4
Active Logic 1
Trva2
32
64
95
tbdlc
5
Start of Frame (SOF)
Trva3
164
200
239
tbdlc
6
End of Data (EOD)
Trvp3
164
200
239
tbdlc
7
End of Frame (EOF)
Trv4
240
280
299
tbdlc
8
Inter-Frame Separator (IFS)
Trv5
300
---
---
tbdlc
9
Break Signal (BREAK)
Trv6
240
---
---
tbdlc
NOTE:
The receiver symbol timing boundaries are subject to an uncertainty of 1 tbdlc due to sampling
considerations.
43
Block Guide — S12BDLC_BG V01.03
Table 4-4 BDLC Receiver VPW Symbol Timing for Binary Frequencies
Number
Characteristic
1
Passive Logic 0
Symbol
Trvp1
Min
Typ
Max
34
67
100
Unit
tbdlc
2
Passive Logic 1
Trvp2
101
134
171
tbdlc
3
Active Logic 0
Trva1
101
134
171
tbdlc
4
Active Logic 1
Trva2
34
67
100
tbdlc
5
Start of Frame (SOF)
Trva3
172
210
251
tbdlc
6
End of Data (EOD)
Trvp3
172
210
251
tbdlc
7
End of Frame (EOF)
Trv4
252
293
314
tbdlc
8
Inter-Frame Separator (IFS)
Trv5
315
---
---
tbdlc
9
Break Signal (BREAK)
Trv6
252
---
---
tbdlc
NOTE:
The receiver symbol timing boundaries are subject to an uncertainty of 1 tbdlc due to sampling
considerations.
Table 4-5 BDLC Receiver VPW 4X Symbol Timing for Integer Frequencies
Number
Characteristic
1
Passive Logic 0
Symbol
Trvp1
Min
Typ
Max
8
16
23
Unit
tbdlc
2
Passive Logic 1
Trvp2
24
32
40
tbdlc
3
Active Logic 0
Trva1
24
32
40
tbdlc
4
Active Logic 1
Trva2
8
16
23
tbdlc
5
Start of Frame (SOF)
Trva3
41
50
59
tbdlc
6
End of Data (EOD)
Trvp3
41
50
59
tbdlc
7
End of Frame (EOF)
Trv4
60
70
74
tbdlc
8
Inter-Frame Separator (IFS)
Trv5
75
---
---
tbdlc
9
Break Signal (BREAK)
Trv6
60
---
---
tbdlc
NOTE:
The receiver symbol timing boundaries are subject to an uncertainty of 1 tbdlc due to sampling
considerations.
Table 4-6 BDLC Receiver VPW 4X Symbol Timing for Binary Frequencies
Number
44
Characteristic
1
Passive Logic 0
Symbol
Trvp1
Min
Typ
Max
9
17
25
Unit
tbdlc
2
Passive Logic 1
Trvp2
26
34
42
tbdlc
3
Active Logic 0
Trva1
26
34
42
tbdlc
Block Guide — S12BDLC_BG V01.03
Table 4-6 BDLC Receiver VPW 4X Symbol Timing for Binary Frequencies
Number
Characteristic
Symbol
Trva2
Min
Typ
Max
9
17
25
Unit
tbdlc
4
Active Logic 1
5
Start of Frame (SOF)
Trva3
43
53
62
tbdlc
6
End of Data (EOD)
Trvp3
43
53
62
tbdlc
7
End of Frame (EOF)
Trv4
63
74
78
tbdlc
8
Inter-Frame Separator (IFS)
Trv5
79
---
---
tbdlc
9
Break Signal (BREAK)
Trv6
63
---
---
tbdlc
NOTE:
The receiver symbol timing boundaries are subject to an uncertainty of 1 tbdlc due to sampling
considerations.
The min and max symbol limits shown in the following sections (Invalid Passive Bit - Valid BREAK
Symbol) and figures (Figure 4-3 - Figure 4-6) refer to the values listed in Tables 4-1 through 4-6.
•
Invalid Passive Bit
If the passive to active transition beginning the next data bit or symbol occurs between the active to
passive transition beginning the current data bit or symbol and Trvp1(Min), the current bit would be
invalid. See Figure 4-3(1).
45
Block Guide — S12BDLC_BG V01.03
200µs
128µs
64µs
Active
(1) Invalid Passive
Bit
Passive
Active
Trvp1(Min)
(2) Valid Passive
Logic Zero
Passive
Active
Trvp1(Min)
Trvp1(Max)
(3) Valid Passive
Logic One
Passive
Trvp2(Min)
Active
Trvp2(Max)
(4) Valid EOD
Symbol
Passive
Trvp3(Min)
Trvp3(Max)
Figure 4-3 J1850 VPW Passive Symbols
•
Valid Passive Logic Zero
If the passive to active transition beginning the next data bit or symbol occurs between Trvp1(Min)
and Trvp1(Max), the current bit would be considered a logic zero. See Figure 4-3(2).
•
Valid Passive Logic One
If the passive to active transition beginning the next data bit or symbol occurs between Trvp2(Min)
and Trvp2(Max), the current bit would be considered a logic one. See Figure 4-3(3).
•
Valid EOD Symbol
If the passive to active transition beginning the next data bit or symbol occurs between Trvp3(Min)
and Trvp3(Max), the current symbol would be considered a valid EOD symbol. See Figure 4-3(4).
46
Block Guide — S12BDLC_BG V01.03
300µs
280µs
Active
(1) Valid EOF
Symbol
Passive
Trv4(Min)
Trv4(Max)
Active
(2) Valid EOF+
IFS Symbol
Passive
Trv5(Min)
Figure 4-4 J1850 VPW EOF and IFS Symbols
•
Valid EOF & IFS Symbol
In Figure 4-4(1), if the passive to active transition beginning the SOF symbol of the next message
occurs between Trv4(Min) and Trv4(Max), the current symbol will be considered a valid EOF symbol.
If the passive to active transition beginning the SOF symbol of the next message occurs after
Trv5(Min), the current symbol will be considered a valid EOF symbol followed by a valid IFS
symbol. See Figure 4-4(2). All nodes must wait until a valid IFS symbol time has expired before
beginning transmission. However, due to variations in clock frequencies and bus loading, some
nodes may recognize a valid IFS symbol before others, and immediately begin transmitting.
Therefore, anytime a node waiting to transmit detects a passive to active transition once a valid EOF
has been detected, it should immediately begin transmission, initiating the arbitration process.
•
Idle Bus
If the passive to active transition beginning the SOF symbol of the next message does not occur
before Ttv5(Min), the bus is considered to be idle, and any node wishing to transmit a message may
do so immediately.
47
Block Guide — S12BDLC_BG V01.03
200µs
128µs
64µs
Active
(1) Invalid Active
Bit
Passive
Active
Trva2(Min)
(2) Valid Active
Logic One
Passive
Active
Trva2(Min)
Trva2(Max)
(3) Valid Active
Logic Zero
Passive
Trva1(Min)
Active
Trva1(Max)
(4) Valid SOF
Symbol
Passive
Trva3(Min)
Trva3(Max)
Figure 4-5 J1850 VPW Active Symbols
•
Invalid Active Bit
If the active to passive transition beginning the next data bit or symbol occurs between the passive
to active transition beginning the current data bit or symbol and Trva2(Min), the current bit would be
invalid. See Figure 4-5(1).
•
Valid Active Logic One
If the active to passive transition beginning the next data bit or symbol occurs between Trva2(Min)
and Trva2(Max), the current bit would be considered a logic one. See Figure 4-5(2).
•
Valid Active Logic Zero
If the active to passive transition beginning the next data bit or symbol occurs between Trva1(Min)
and Trva1(Max), the current bit would be considered a logic zero. See Figure 4-5(3).
•
Valid SOF Symbol
If the active to passive transition beginning the next data bit or symbol occurs between Trva3(Min)
and Trva3(Max), the current symbol would be considered a valid SOF symbol. See Figure 4-5(4).
48
Block Guide — S12BDLC_BG V01.03
240µs
Active
(2) Valid BREAK
Symbol
Passive
Trv6(Min)
Figure 4-6 J1850 VPW BREAK Symbol
•
Valid BREAK Symbol
If the next active to passive transition does not occur until after Trv6(Min), the current symbol will
be considered a valid BREAK symbol. A BREAK symbol should be followed by a SOF symbol
beginning the next message to be transmitted onto the J1850 bus. See Figure 4-6.
•
Message Arbitration
Message arbitration on the J1850 bus is accomplished in a non-destructive manner, allowing the
message with the highest priority to be transmitted, while any transmitters which lose arbitration
simply stop transmitting and wait for an idle bus to begin transmitting again.
If the BDLC module wishes to transmit onto the J1850 bus, but detects that another message is in
progress, it automatically waits until the bus is idle. However, if multiple nodes begin to transmit
in the same synchronization window, message arbitration will occur beginning with the first bit
after the SOF symbol and continue with each bit thereafter.
The VPW symbols and J1850 bus electrical characteristics are carefully chosen so that a logic zero
(active or passive type) will always dominate over a logic one (active or passive type)
simultaneously transmitted. Hence logic zeroes are said to be ‘dominant’ and logic ones are said to
be ‘recessive’.
Whenever a node transmits a recessive bit and detects a dominant bit, it loses arbitration, and
immediately stops transmitting. This is known as ‘bitwise arbitration’.The loss of arbitration flag
(in DLCBSVR) is set when arbitration is lost. If the interrupt enable bit (IE in DLCBCR1) is set, an
interrupt request from the BDLC module is generated. Reading the DLCBSVR register will clear
this flag.
49
Block Guide — S12BDLC_BG V01.03
“0”
“1”
“1”
“0”
“1”
“1”
“1”
Transmitter A detects
an active state on
the bus, and stops
transmitting
Active
Transmitter A
Passive
“0”
“0”
Active
Transmitter B
Passive
“0”
“1”
“1”
“0”
“0”
Data
Bit 1
Data
Bit 2
Data
Bit 3
Data
Bit 4
Data
Bit 5
Transmitter B wins
arbitration and
continues
transmitting
Active
J1850 Bus
Passive
SOF
Figure 4-7 J1850 VPW Bitwise Arbitrations
During arbitration, or even throughout the transmitting message, when an opposite bit is detected,
transmission is immediately stopped unless it occurs on the 8th bit of a byte. In this case the BDLC
module will automatically append up to two extra 1 bits and then stop transmitting. These two extra
bits will be arbitrated normally and thus will not interfere with another message. The second 1 bit
will not be sent if the first loses arbitration. If the BDLC module has lost arbitration to another valid
message then the two extra ones will not corrupt the current message. However, if the BDLC
module has lost arbitration due to noise on the bus, then the two extra ones will ensure that the
current message will be detected and ignored as a noise-corrupted message.
Since a “0” dominates a “1”, the message with the lowest value will have the highest priority, and
will always win arbitration, i.e. a message with priority 000 will win arbitration over a message with
priority 011. This method of arbitration will work no matter how many bits of priority encoding are
contained in the message.
4.1.4 J1850 Bus Errors
The BDLC module detects several types of transmit and receive errors which can occur during the
transmission of a message onto the J1850 bus.
•
Transmission Error
If the BDLC module is transmitting a message and the message received contains a symbol error,
a framing error, a bus fault, a BREAK symbol, or a logic ‘1’ symbol when a logic “0” is being
transmitted, this constitutes a transmission error. Receiving a logic ‘0’ symbol when transmitting a
logic ‘1’ is considered a loss of arbitration condition (See Message Arbitration) and not a
transmission error. When a transmission error is detected, the BDLC module will immediately
cease transmitting. Further transmission or reception will be disabled until a valid EOF symbol is
50
Block Guide — S12BDLC_BG V01.03
detected on the J1850 bus. The error condition is reflected by setting the symbol invalid or out of
range flag in the DLCBSVR register. If the interrupt enable bit (IE in DLCBCR1) is set, an interrupt
request from the BDLC module is generated. Reading the DLCBSVR register will clear this flag.
•
CRC Error
A cyclical redundancy check (CRC) error is detected when the data bytes and CRC byte of a
received message are processed, and the CRC calculation result is not equal to $C4.The CRC code
should detect any single and 2 bit errors, as well as all 8 bit burst errors, and almost all other types
of errors. The CRC error flag (in DLCBSVR) is set when a CRC error is detected. If the interrupt
enable bit (IE in DLCBCR1) is set, an interrupt request from the BDLC module is generated.
Reading the DLCBSVR register will clear this flag.
•
Symbol Error
A symbol error is detected when an abnormal (invalid) symbol is detected in a message being
received from the J1850 bus. See sections Invalid Passive Bit and Invalid Active Bit which define
invalid symbols.The symbol invalid or out of range flag (in DLCBSVR) is set when a symbol error
is detected. If the interrupt enable bit (IE in DLCBCR1) is set, an interrupt request from the BDLC
module is generated. Reading the DLCBSVR register will clear this flag.
•
Framing Error
A framing error is detected when a received symbol occurs in an inappropriate location in the
message frame. The following situations result in framing errors:
–
An active logic “0” or logic “1” received as the first symbol of the frame.
–
An SOF symbol received in any location other than the first symbol of a frame. Erroneous
locations include: Within the data portion of a message or IFR; Immediately following the EOD
in a message or IFR.
–
An EOD symbol received on a non-byte boundary in a message or IFR.
–
An active logic “0” or logic “1” received immediately following the EOD at the end of an IFR.
The symbol invalid or out of range flag (in DLCBSVR) is set when a framing error is detected. If
the interrupt enable bit (IE in DLCBCR1) is set, an interrupt request from the BDLC module is
generated. Reading the DLCBSVR register will clear this flag.
•
Bus Fault
If a bus fault occurs, the response of the BDLC module will depend upon the type of bus fault.
If the bus is shorted to VDD, the BDLC module will wait for the bus to fall to a passive state before
it will attempt to transmit a message. As long as the short remains, the BDLC will never attempt to
transmit a message onto the J1850 bus.
If the bus is shorted to ground, the BDLC module will see an idle bus, begin to transmit the message,
and then detect a transmission error, since the short to ground would not allow the bus to be driven
to the active (dominant) state. The BDLC module will wait for assertion of the receive pin for (64
- analog round trip delay) tbdlc cycles, after assertion of the transmit pin, before detecting the error.
If the transmission is an IFR, the BDLC module will wait for (280 - analog round trip delay) tbdlc
cycles before detecting an error. The “analog round trip delay” is determined by the value stored in
the DLCBARD register. The BDLC module will set the symbol invalid or out of range flag (in
51
Block Guide — S12BDLC_BG V01.03
DLCBSVR), abort that transmission and wait for the next CPU command to transmit. In this case,
the transmitter does not have to wait for an EOF symbol to be received to be enabled. If the interrupt
enable bit (IE in DLCBCR1) is set, an interrupt request from the BDLC module is generated.
Reading the DLCBSVR register will clear this flag.
In any case, if the bus fault is temporary, as soon as the fault is cleared, the BDLC module will
resume normal operation. If the bus fault is permanent, it may result in permanent loss of
communication on the J1850 bus.
•
BREAK - Break
Any BDLC transmitting at the time a BREAK is detected will treat the BREAK as if a transmission
error had occurred, and halt transmission.
If while receiving a message the BDLC module detects a BREAK symbol, it will treat the BREAK
as a reception error.
If a BREAK symbol is received while the BDLC module is transmitting or receiving, the symbol
invalid or out of range flag (in DLCBSVR) is set. Further transmission/reception will be disabled
until the J1850 bus returns to the passive state and a valid EOF symbol is detected on the J1850 bus.
If the interrupt enable bit (IE in DLCBCR1) is set, an interrupt request from the BDLC module is
generated. Reading the DLCBSVR register will clear this flag.
The BDLC module cannot transmit a BREAK symbol. It can only receive a BREAK symbol from
the J1850 bus.
•
Bus Error Summary
The possible J1850 bus errors and the actions taken by the BDLC module are summarized in Table
4-7.
Table 4-7 BDLC module J1850 Error Summary
Error Condition
52
BDLC Module Function
Transmission Error
BDLC module will immediately cease transmitting. Further
transmission and reception will be disabled until a valid
EOF symbol is detected. The symbol invalid or out of
range flag will be set and interrupt generated if enabled.
Cyclical Redundancy Check
(CRC) Error
CRC error flag set and interrupt generated if enabled.
Symbol Error
The symbol invalid or out of range flag will be set and
interrupt generated if enabled. Transmission and
reception will be disabled until a valid EOF symbol is
detected.
Framing Error
The symbol invalid or out of range flag will be set and
interrupt generated if enabled. Transmission and
reception will be disabled until a valid EOF symbol is
detected.
Block Guide — S12BDLC_BG V01.03
Table 4-7 BDLC module J1850 Error Summary
Error Condition
BDLC Module Function
Bus short to VDD.
The BDLC module will not transmit until short is corrected
and a valid EOF is detected. Depending upon when short
occurs and is corrected, this error condition may set the
symbol invalid or out of range, crc error, or loss of
arbitration flags.
Bus short to GND.
Short will be seen as an idle bus by BDLC module. If a
transmission attempt is made before short is corrected,
the symbol invalid or out of range flag will be set and
interrupt generated if enabled. Another transmission can
be initiated as soon as short is corrected.
BREAK symbol reception
If doing so, the BDLC module will immediately cease
transmitting. Symbol invalid or out of range flag set and
interrupt generated if enabled.Transmission and reception
will be disabled until a valid EOF symbol is detected.
4.2 Mux Interface
The MUX Interface is responsible for bit encoding/decoding and digital noise filtering between the
Protocol Handler and the Physical Interface. Refer to Figure 1-2 BDLC Block Diagram on page 16.
4.2.1 Mux Interface - Rx Digital Filter
The Receiver section of the BDLC module includes a digital low pass filter to remove narrow noise pulses
from the incoming message. An outline of the digital filter is shown in Figure 4-8.
53
Block Guide — S12BDLC_BG V01.03
Input
Sync
Rx Data
from
RXB pad
Filtered
Rx Data Out
4-Bit Up/Down Counter
4
d
q
up/down
out
Edge &
Count
Comparator
d
q
MUX Interface Clock
Figure 4-8 BDLC Module Rx Digital Filter Block Diagram
•
Operation
The clock for the digital filter is provided by the MUX Interface clock.At each positive edge of the
clock signal, the current state of the Receiver input signal from the RXB pad is sampled.The RXB
signal state is used to determine whether the counter should increment or decrement at the next
positive edge of the clock signal.
The counter will increment if the input data sample is high but decrement if the input sample is
low.The counter will thus progress up towards ‘15’ if, on average, the RXB signal remains high or
progress down towards ‘0’ if, on average, the RXB signal remains low.
When the counter eventually reaches the value ‘15’, the digital filter decides that the condition of
the RXB signal is at a stable logic level one and the Data Latch is set, causing the Filtered Rx Data
signal to become a logic level one. Furthermore, the counter is prevented from overflowing and can
only be decremented from this state.
Alternatively, should the counter eventually reach the value ‘0’, the digital filter decides that the
condition of the RXB signal is at a stable logic level zero and the Data Latch is reset, causing the
Filtered Rx Data signal to become a logic level zero. Furthermore, the counter is prevented from
underflowing and can only be incremented from this state.
The Data Latch will retain its value until the counter next reaches the opposite end point, signifying
a definite transition of the RXB signal.
•
Performance
The performance of the digital filter is best described in the time domain rather than the frequency
domain.
54
Block Guide — S12BDLC_BG V01.03
If the signal on the RXB signal transitions, then there will be a delay before that transition appears
at the Filtered Rx Data output signal. This delay will be between 15 and 16 clock periods, depending
on where the transition occurs with respect to the sampling points. This ‘filter delay’ must be taken
into account when performing message arbitration.
For example, if the frequency of the MUX Interface clock (fbdlc) is 1.0486MHz, then the period
(tbdlc) is 954ns and the maximum filter delay in the absence of noise will be 15.259us.
The effect of random noise on the RXB signal depends on the characteristics of the noise itself.
Narrow noise pulses on the RXB signal will be completely ignored if they are shorter than the filter
delay. This provides a degree of low pass filtering.
If noise occurs during a symbol transition, the detection of that transition may be delayed by an
amount equal to the length of the noise burst. This is just a reflection of the uncertainty of where
the transition is truly occurring within the noise.
Noise pulses that are wider than the filter delay, but narrower than the shortest allowable symbol
length will be detected by the next stage of the BDLC module’s receiver as an invalid symbol.
Noise pulses that are longer than the shortest allowable symbol length will normally be detected as
an invalid symbol or as invalid data when the frame’s CRC is checked.
4.3 Protocol Handler
The Protocol Handler is responsible for framing, collision detection, arbitration, CRC
generation/checking, and error detection. The Protocol Handler conforms to SAE J1850 - Class B Data
Communications Network Interface. Refer to Figure 1-2 BDLC Block Diagram on page 16
4.3.1 Protocol Architecture
The Protocol Handler contains the State Machine, Rx Shadow Register, Tx Shadow Register, Rx Shift
Register, Tx Shift Register, and Loopback Multiplexer as shown in Figure 4-9 BDLC Protocol Handler
Outline. Each block will now be described in more detail.
55
Block Guide — S12BDLC_BG V01.03
To Pad Drivers
TXB
RXB
BDLC
TXB
DIGITAL FILTER IN
Control
Loopback
Multiplexer
DLOOP from BCR2
loopback control
State Machine
Tx Shadow Register
8
Tx Data
Rx Shadow Register
Control
Tx Shift Register
Rx Data
Rx Shift Register
8
To IP Bus Interface & Rx/Tx Buffer’s
Figure 4-9 BDLC Protocol Handler Outline
•
Rx & Tx Shift Registers
The Rx Shift Register gathers received serial data bits from the J1850 bus and makes them available
in parallel form to the Rx Shadow Register. The Tx Shift Register takes data, in parallel form, from
the Tx Shadow Register and presents it serially to the State Machine so that it can be transmitted
onto the J1850 bus.
•
56
Rx & Tx Shadow Registers
Block Guide — S12BDLC_BG V01.03
Immediately after the Rx Shift Register has completed shifting in a byte of data, this data is
transferred to the Rx Shadow Register and RDRF or RXIFR is set and interrupt is generated if the
interrupt enable bit (IE) in BCR1 is set. After the transfer takes place, this new data byte in the Rx
Shadow Register is available to the CPU, and the Rx Shift Register is ready to shift in the next byte
of data. Data in Rx Shadow Register must be retrieved by the CPU before it is overwritten by new
data from the Rx Shift Register.
Once the Tx Shift Register has completed its shifting operation for the current byte, the data byte
in the Tx Shadow Register is loaded into the Tx Shift Register. After this transfer takes place, the
Tx Shadow Register is ready to accept new data from the CPU.
•
Digital Loopback Multiplexer
The Digital Loopback Multiplexer connects the input of the receive digital filter (See Figure 4-9)
to either the transmit signal out to the pad (TXB) or the receive signal from the pad (RXB),
depending on the state of the DLOOP bit in DLCBCR2 register.
•
State Machine
All of the functions associated with performing the protocol are executed or controlled by the State
Machine. The State Machine is responsible for framing, collision detection, arbitration, CRC
generation/checking, and error detection. The following sections describe the BDLC module’s
actions in a variety of situations.
•
4X Mode
The BDLC module can exist on the same J1850 bus as modules which use a special 4X (41.6 kbps)
mode of J1850 VPW operation. The BDLC module cannot transmit in 4X mode, but can receive
messages in 4X mode, if the RX4X bit is set in BCR2 register. If the RX4X bit is not set in the BCR2
register, any 4X message on the J1850 bus is treated as noise by the BDLC module and is ignored.
Likewise, 4X messages transmitted on the SAE J1850 bus when the BDLC module is in normal
mode will be interpreted as noise on the network by the BDLC module.
•
Receiving a Message in Block Mode
Although not a part of the SAE J1850 protocol, the BDLC module does allow for a special “Block
Mode” of operation of the receiver. As far as the BDLC module is concerned, a Block Mode
message is simply a long J1850 frame that contains an indefinite number of data bytes. All of the
other features of the frame remain the same, including the SOF, CRC, and EOD symbols.
Another node wishing to send a Block Mode transmission must first inform all other nodes on the
network that this is about to happen. This is usually accomplished by sending a special predefined
message.
•
Transmitting a Message in Block Mode
A Block mode message is transmitted inherently by simply loading the bytes one by one into the
BDR register until the message is complete. The programmer should wait until the TDRE flag is set
prior to writing a new byte of data into the BDR register. The BDLC module does not contain any
predefined maximum J1850 message length requirement.
57
Block Guide — S12BDLC_BG V01.03
4.4 Transmitting A Message
The design of the BDLC module enables the user to easily handle message reception and message
transmission separately. This can greatly simplify the communication software, as all received messages
can be handled virtually the same, regardless of their origin.
This chapter will therefore describe only the steps necessary for transmitting a message, and will not
address the resulting reception of that message by the BDLC module. Message reception is described in
Section 4.5 Receiving A Message. Later sections will deal with transmitting and receiving In-Frame
Responses on the SAE J1850 bus.
4.4.1 BDLC Transmission Control Bits
There is only one BDLC module control bit which is used when transmitting a message onto the SAE
J1850 bus. This bit, the Transmit End of Data (TEOD) bit, is set by the user to indicate to the BDLC
module that the last byte of that part of the message frame has been loaded into the DLCBDR. The TEOD
bit, located in DLCBCR2, is also used when transmitting an In-Frame Response (IFR), but that usage is
described in Section 4.6 Transmitting An In-Frame Response (IFR) on page 67. Setting the TEOD bit
indicates to the BDLC module that the last byte written to the BDLC Data Register is the final byte to be
transmitted, and that following this byte a CRC byte and EOD symbol should be transmitted automatically.
Setting the TEOD bit will also inhibit any further TDRE interrupts until TEOD is cleared. The TEOD bit
will be cleared on the rising edge of the first bit of the transmitted CRC byte, or if an error or loss of
arbitration is detected on the bus.
•
BDLC Data Register
The BDLC Data Register is a double-buffered register which is used for handling the transmitted
and received message bytes.Bytes to be transmitted onto the SAE J1850 bus are written to the
DLCBDR, and bytes received from the bus by the BDLC module are read from the DLCBDR.
Since this register is double buffered, bytes written into it cannot be read by the CPU. If this is
attempted, the byte which is read will be the last byte placed in the DLCBDR by the BDLC module,
not the last byte written to the DLCBDR by the CPU. For an illustration of the DLCBDR, refer to
Section 3.3.4 BDLC Data Register (DLCBDR) on page 31.
•
Transmitting a Message with the BDLC
To transmit a message using the BDLC module, the user just writes the first byte of the message to
be transmitted into the DLCBDR, initiating the transmission process. When the TDRE status
appears in the DLCBSVR, the user writes the next byte into the DLCBDR. Once all of the bytes
have been loaded into the DLCBDR, the user sets the TEOD bit, and the BDLC module completes
the message transmission. What follows is an overview of the basic steps required to transmit a
message onto an SAE J1850 network using the BDLC module. For an illustration of this sequence,
refer to Figure 4-10 Basic BDLC Transmit Flowchart on page 62.
NOTE:
58
Due to the byte-level architecture of the BDLC module, the 12-byte limit on
message length as defined in SAE J1850 must be enforced by the user’s software.
The number of bytes in a message (transmitted or received) has no meaning to the
BDLC module.
Block Guide — S12BDLC_BG V01.03
–
Step 1: Write the First Byte into the DLCBDR
To initiate a message transmission, the CPU simply loads the first byte of the message to be
transmitted into the DLCBDR. The BDLC module will then perform the necessary bus
acquisition duties to determine when the message transmission can begin.
Once the BDLC module determines that the SAE J1850 bus is free, a Start of Frame (SOF)
symbol will be transmitted, followed by the byte written to the DLCBDR. Once the BDLC
module readies this byte for transmission, the DLCBSVR will reflect that the next byte can be
written to the DLCBDR (TDRE interrupt).
NOTE:
–
If the user writes the first byte of a message to be transmitted to the DLCBDR and
then determines that a different message should be transmitted, the user can write
a new byte to the DLCBDR up until the transmission begins. This new byte will
replace the original byte in the DLCBDR.
Step 2: When TDRE is Indicated, Write the Next Byte into the DLCBDR
When a TDRE state is reflected in the BSVR, the CPU writes the next byte to be transmitted
into the BDR. This step is repeated until the last byte to be transmitted is written to the
DLCBDR.
NOTE:
–
Due to the design and operation of the BDLC module, when transmitting a message
the user may write two, or possibly even three of the bytes to be transmitted into the
DLCBDR before the first RDRF interrupt occurs. For this reason, the user should
never use receive interrupts to control the sequencing of bytes to be transmitted.
Step 3: Write the Last Byte to the DLCBDR and Set TEOD
Once the user has written the last byte to be transmitted into the DLCBDR, the user then sets
the TEOD bit in DLCBCR2. When the TEOD bit is set, once the byte written to the DLCBDR
is transmitted onto the bus, the BDLC module will begin transmitting the 8-bit CRC byte, as
specified in SAE J1850. Following the CRC byte, the BDLC module will transmit an EOD
symbol onto the SAE J1850 bus, indicating that this part of the message has been completed. If
no IFR bytes are transmitted following the EOD, an EOF will be recognized and the message
will be complete.
Setting the TEOD bit is the last step the CPU needs to take to complete the message
transmission, and no further transmission-related interrupts will occur. Once the message has
been completely received by the BDLC module, an EOF interrupt will be generated. However,
this is technically a receive function which can be handled by the message reception routine.
NOTE:
While the TEOD bit is typically set immediately following the write of the last byte
to the BDR, it is also acceptable to wait until a TDRE interrupt is generated before
setting the TEOD bit. While the example flowchart in Figure 4-10 shows the TEOD
bit being set after the write to the BDR, either method is correct. If a TDRE interrupt
is pending, it will be cleared when the TEOD bit is set.
59
Block Guide — S12BDLC_BG V01.03
4.4.2 Transmitting Exceptions
While this is the basic transmit flow, at times the message transmit process will be interrupted. This can
be due to a loss of arbitration to a higher priority message or due to an error being detected on the network.
For the transmit routine, either of these events can be dealt with in a similar manner.
•
Loss of Arbitration
If a loss of arbitration (LOA) occurs while the BDLC module is transmitting onto the SAE J1850
bus, the BDLC module will immediately stop transmitting, and a LOA status will be reflected in
the DLCBSVR. If the loss of arbitration has occurred on a byte boundary, an RDRF interrupt may
also be pending once the LOA interrupt is cleared.
When a loss of arbitration occurs, the J1850 message handling software should immediately switch
into the receive mode. If the TEOD bit was set, it will be cleared automatically. If another attempt
is to be made to transmit the same message, the user must start the transmit sequence over
from the beginning of the message.
•
Error Detection
Similar to a loss of arbitration, if any error (except a CRC error) is detected on the SAE J1850 bus
during a transmission, the BDLC module will stop transmitting immediately. The byte which was
being transmitted will be discarded, and the “Symbol Invalid or Out of Range” status will be
reflected in the DLCBSVR. As with the loss of arbitration, if the TEOD bit was set, it will be cleared
automatically, and any attempt to transmit the same message will have to start from the beginning.
If a CRC error occurs following a transmission, this will also be reflected in the DLCBSVR.
However, since the CRC error is really a receive error based on the received CRC byte, at this point
all bytes of the message will have been transmitted. It is therefore up to the user’s software to
determine if another attempt should be made to transmit the message in which the error occurred.
•
Transmitter Underrun
A transmitter underrun can occur when a TDRE interrupt is not serviced in a timely fashion. If the
last byte loaded into the DLCBDR is completely transmitted onto the network before the next byte
is loaded into the BDR, a transmitter underrun will occur. If this does happen, the BDLC module
will transmit two additional logic ones to ensure that the partial message which was transmitted
onto the bus does not end on a byte boundary. This will be followed by an EOD and EOF symbol.
The only indication to the CPU that an underrun occurred is the Symbol Invalid or Out of Range
error which will be indicated in the DLCBSVR. As with the other errors, it is up to the user’s
software to determine if another transmission attempt should be made.
•
In-Frame Response to a Transmitted Message
If an In-Frame Response (IFR) is received following the transmission of a message, the status
indicating that an IFR byte has been received will be indicated in the DLCBSVR before an EOF is
indicated. Refer to Section 4.7 Receiving An In-Frame Response (IFR) on page 78 for a description
of how to handle the reception of IFR bytes.
60
Block Guide — S12BDLC_BG V01.03
4.4.3 Aborting a Transmission
The BDLC module does not have a mechanism designed specifically for aborting a transmission. Since
the module transmits each message on a byte-by-byte basis, there is little need to implement an abort
mechanism. If the user has loaded a byte into the DLCBDR to initiate a message transmission and decides
to send a different message, the byte in the DLCBDR can be replaced, right up to the point that the message
transmission begins.
If the user has loaded a byte into the DLCBDR and then decides not to send any message at all, the user
can let the byte transmit, and when the TDRE interrupt occurs let the transmitter underrun. This will cause
two extra logic ones followed by an EOF to be transmitted. While this method may require a small amount
of bus bandwidth, the need to do this should be very rare. Replacing the byte originally written to the BDR
with $FF will also increase the probability of the transmitter losing arbitration if another node begins
transmitting at the same time, also reducing the bus bandwidth needed.
61
Block Guide — S12BDLC_BG V01.03
Enter BDLC module Transmit
Routine
C
A
Write first message
byte to be transmitted
into DLCBDR
No
Is this the last
byte?
Yes
Go to BDLC module
BREAK/Error Handling
Routine
Yes
Is DLCBSVR = $00?
For interrupt driven systems,
this marks the beginning of the
transmit section of the BDLC
module interrupt service
routine
No
Yes
Set TEOD bit
in DLCBCR2
Is DLCBSVR = $1C?
(Invalid Symbol)
IFR Received?
No
Yes
Jump to Receive IFR
Handling Routine
No
B
B
Jump to BDLC module
Receive Routine
Yes
Once BDLC module detects
EOF, transmit
attempt is complete
Is DLCBSVR = $14?
(LOA)
No
Is DLCBSVR = $10?
(TDRE)
Yes
Load next byte to be
transmitted into BDR
(clears TDRE)
No
Attempt another
transmission?
Yes
C
No
Exit BDLC module Transmit
Routine
A
NOTE: The EOF and CRC Error interrupts
are handled in the BDLC module Receive
Routine
Figure 4-10 Basic BDLC Transmit Flowchart
4.5 Receiving A Message
The design of the BDLC module makes it especially easy to use for receiving messages off of the SAE
J1850 bus. When the first byte of a message comes in, the DLCBSVR will indicate to the CPU that a byte
62
Block Guide — S12BDLC_BG V01.03
has been received. As each successive byte is received, that will in turn be reflected in the DLCBSVR.
When the message is complete and the EOF has been detected on the bus, the DLCBSVR will reflect this,
indicating that the message is complete.
The basic steps required for receiving a message from the SAE J1850 bus are outlined below. For more
information on receiving IFR bytes, refer to Section 4.7 Receiving An In-Frame Response (IFR) on page
78.
4.5.1 BDLC Reception Control Bits
The only control bit which is used for message reception, the IMSG bit, is actually used to prevent message
reception. When the IMSG bit is set BDLC module interrupts of the CPU are inhibited until the next SOF
symbol is received. This allows the BDLC module to ignore the remainder of a message once the CPU has
determined that it is of no interest. This helps reduce the amount of CPU overhead used to service
messages received from the SAE J1850 network, since otherwise the BDLC module would require
attention from the CPU for each byte broadcast on the network. The IMSG bit is cleared when the BDLC
module receives an SOF symbol, or it can also be cleared by the CPU.
NOTE:
While the IMSG bit can be used to prevent the CPU from having to service the
BDLC module for every byte transmitted on the SAE J1850 bus, the IMSG bit
should never be used to ignore the BDLC module’s own transmission. Because
setting the IMSG bit prevents all DLCBSVR bits from being updated until an SOF
is received, the user would not receive any further transmit-related interrupts until
another SOF was received, making it very difficult for the CPU to complete the
transmission correctly.
4.5.2 Receiving a Message with the BDLC module
Receiving a message using the BDLC module is extremely straight-forward. As each byte of a message is
received and placed into the DLCBDR, the BDLC module will indicate this to the CPU with an Rx Data
Register Full (RDRF) status in the DLCBSVR. When an EOF symbol is received, indicating to the CPU
that the message is complete, this too will be reflected in the DLCBSVR.
Outlined below are the basic steps to be followed for receiving a message from the SAE J1850 bus with
the BDLC module. For an illustration of this sequence, refer to Basic BDLC Receive Flowchart on page
66.
•
Step 1: When RDRF Interrupt Occurs, Retrieve Data Byte
When the first byte of a message following a valid SOF symbol is received that byte is placed in the
DLCBDR, and an RDRF state is reflected in the DLCBSVR. No indication of the SOF reception is
made, since the end of the previous message is marked by an EOF indication. The first RDRF state
following this EOF indication should allow the user to determine when a new message begins.
The RDRF interrupt is cleared when the received byte is read from the DLCBDR. Once this is done,
no further CPU intervention is necessary until the next byte is received, and this step is repeated.
All bytes of the message, including the CRC byte, will be placed into the DLCBDR as they are
received for the CPU to retrieve.
63
Block Guide — S12BDLC_BG V01.03
•
Step 2: When an EOF is Received, the Message is Complete
Once all bytes (including the CRC byte) have been received from the bus, the bus will be idle for a
time period equal to an EOD symbol. Once the EOD symbol is received, the BDLC module will
verify that the CRC byte is correct. If the CRC byte is not correct, this will be reflected in the
DLCBSVR.
If no In-Frame Response bytes are transmitted following the EOD symbol, the EOD will transition
into an EOF symbol. When the EOF is received it will be reflected in the DLCBSVR, indicating to
the user that the message is complete. If IFR bytes do follow the first EOD symbol, once they are
complete another EOD will be transmitted, followed by an EOF.
Once the EOF state is reflected in the DLCBSVR, this indicates to the user that the message is
complete, and that when another byte is received it is the first byte of a new message.
4.5.3 Filtering Received Messages
No message filtering hardware is included on the BDLC module, so all message filtering functions must
be performed in software. Because the BDLC module handles each message on a byte-by-byte basis,
message filtering can be done as each byte is received, rather than after the entire message is complete.
This enables the CPU to decide while a message is still in progress whether or not that message is of any
interest.
At any point during a message, if the CPU determines that the message is of no interest the IMSG bit can
be set. Setting the IMSG bit commands the BDLC module not to update the DLCBSVR until the next valid
SOF is received. This prevents the CPU from having to service the BDLC module for each byte of every
message sent over the network.
4.5.4 Receiving Exceptions
As with a message transmission, this basic message reception flow can be interrupted if errors are detected
by the BDLC module. This can occur if an incorrect CRC is detected or if an invalid or out of range symbol
appears on the SAE J1850 bus. A problem can also arise if the CPU fails to service the DLCBDR in a
timely manner during a message reception.
•
Receiver Overrun
Once a message byte has been received, the CPU must service the DLCBDR before the next byte
is received, or the first byte will be lost. If the DLCBDR is not serviced quickly enough, the next
byte received will be written over the previous byte in the DLCBDR. No receiver overrun indication
is made to the CPU. If the CPU fails to service the BDLC module during the reception of an entire
message, the byte remaining in the DLCBDR will be last byte received (usually a CRC byte).
Once a receiver overrun occurs, there is no way for the CPU to recover the lost byte(s), so the entire
message should be discarded. To prevent receiver overrun, the user should ensure that a BDLC
RDRF interrupt will be serviced before the next byte can be received. When polling the DLCBSVR,
the user should select a polling interval which will provide timely monitoring of the BDLC module.
•
64
CRC Error
Block Guide — S12BDLC_BG V01.03
If a CRC error is detected during a message reception, this will be reflected in the BSVR once an
EOD time is recognized by the BDLC module. Since all bytes of the message will have been
received when this error is detected, it is up to the user to ensure that all the received message bytes
are discarded.
•
Invalid or Out of Range Symbol
If an invalid or out of range symbol, a framing error or a BREAK symbol is detected on the SAE
J1850 bus during the reception of a message, the BDLC module will immediately stop receiving
the message and discard any partially received byte. The “Symbol Invalid or Out of Range” status
will immediately be reflected in the DLCBSVR. Following this the BDLC module will wait until
the bus has been idle for a time period equal to an EOF symbol before receiving another message.
As with the CRC error, the user should discard any partially received message if this occurs.
•
In-Frame Response to a Received Message
As mentioned above, if one or more IFR bytes are received following the reception of a message,
the status indicating the reception of the IFR byte(s) will be indicated in the DLCBSVR before the
EOF is indicated. Refer to Receiving An In-Frame Response (IFR) on page 78 for a description of
how to deal with the reception of IFR bytes.
65
Block Guide — S12BDLC_BG V01.03
Enter BDLC module Receive
Routine
Is DLCBSVR
= $1C/$18?
(Error Detected)
Yes
Go to BDLC module
BREAK/Error Handling
Routine
B
No
Is DLCBSVR
= $0C?
(RDRF)
Yes
Read byte in DLCBDR
No
Is this a transmit
reflection?
Yes
Jump to Receive IFR
Handling Routine
Is this an IFR
reception?
No
Filter received byte
Yes
No
Store received byte
(in case of LOA)
B
Once BDLC module Detects
EOF, message
reception is complete
Yes
Is DLCBSVR = $04?
(EOF)
Yes
No
Is this message
of any interest?
A
No
Exit BDLC module Receive
Routine
Store received byte
Jump to Transmit IFR
Handling Routine
Yes
Is an IFR to
be transmitted?
No
B
Figure 4-11 Basic BDLC Receive Flowchart
66
Set IMSG bit in DLCBCR1
A
Block Guide — S12BDLC_BG V01.03
4.6 Transmitting An In-Frame Response (IFR)
The BDLC module can be used to transmit all four types of In-Frame Response (IFR) which are defined
in SAE J1850. A very brief definition of each IFR type is given below. For a more detailed description of
each, refer the SAE J1850 document.
The explanation regarding IFR support by the BDLC module which assumes the user is familiar with the
use of IFRs as defined in SAE J1850, and understands the message header bit encoding and normalization
bit formats which are used with the different types of IFRs. For more information on this, refer to the SAE
J1850 document.
4.6.1 IFR Types Supported by the BDLC module
SAE J1850 defines four distinct types of IFR. The first (and most basic) IFR is Type 0, or no IFR. IFR
types 1, 2 & 3 are each made up of one or more bytes and, depending upon the type used, may be followed
by a CRC byte. The BDLC module is designed to allow the user to transmit and receive all types of SAE
J1850 IFRs, but only the network framing/error checking/bus acquisition duties are performed by the
BDLC module. The user is responsible for determining the type of IFR to be transmitted, the number of
retries to be made (if allowed), and the allowable number of bytes to be transmitted.
•
IFR Type 0: No Response
The most basic type of IFR is no IFR. The Type 0 IFR, as defined in SAE J1850, is no response.
The EOD and EOF symbols follow directly after the CRC byte at the end of the message frame
being transmitted. This type of IFR is, of course, inherently supported by the BDLC module with
no additional user intervention required.
•
IFR Type 1: Single Byte from a Single Responder
SAE J1850 defines the Type 1 IFR as a single byte from a single receiver. This type of IFR is used
to acknowledge to the transmitter that the message frame was transmitted successfully on the
network, and that at least one receiver received it correctly. A Type 1 IFR generally consists of the
physical node ID of the receiver responding to the message, with no CRC byte appended. This type
of response is used for Broadcast-type messages, where there may be several intended receivers for
a message but the transmitter only wants to know that at least one node received it. In this case, all
receivers will begin transmitting their node ID following the EOD. Since all nodes on an SAE J1850
network have a unique node ID, if multiple nodes begin transmitting their node ID simultaneously,
arbitration takes place. The node with the highest priority (lowest value) ID wins this arbitration
process, and that node’s ID makes up the IFR. No retries are attempted by the nodes which lose
arbitration during a Type 1 IFR transmission.
A Type 1 IFR can also be used as a response to a physically addressed message, where the only
intended receiver is the one which responds. In this case, no arbitration would take place during the
IFR transmission, but the resulting IFR would still consist of a single byte.
•
IFR Type 2: Single Byte from Multiple Responders
67
Block Guide — S12BDLC_BG V01.03
The Type 2 IFR, as defined in SAE J1850, is a series of single bytes, each transmitted by a different
responder. This IFR type not only acknowledges to the transmitter that the message was transmitted
successfully, but also reveals which receivers actually received the message. As with the Type 1
IFR, no CRC byte is appended to the end of a Type 2 IFR.
This IFR type is typically used with Function-type messages, where the original transmitter may
need to know which nodes actually received the message. The basic difference between this type of
IFR and the Type 1 IFR is that the nodes which lose arbitration while attempting to transmit their
node ID during a Type 2 IFR wait until the byte which wins arbitration is transmitted and then again
attempt to transmit their node ID onto the bus. The result is a series of node IDs, one from each
receiver of the original message.
•
IFR Type 3: Multiple Bytes from a Single Responder
The last type of IFR defined by SAE J1850 is the Type 3 IFR. This IFR type consists of one or more
bytes from a single responder. This type of IFR is used to return data to the original transmitter
within the original message frame. This type of IFR may or may not have a CRC byte appended to
it.
The Type 3 IFR is typically used with Function Read-type or Function Query-type messages, where
the original transmitter is requesting data from the intended receiver. The node requesting the data
transmits the initial portion of the message, and the intended receiver responds by transmitting the
desired data in an IFR. In most cases, the original message requiring a Type 3 IFR is addressed to
one particular node, so no arbitration should take place during the IFR portion of the message.
4.6.2 BDLC IFR Transmit Control Bits
The BDLC module has three bits which are used to control the transmission of an In-Frame Response.
These bits, all located in DLCBCR2, are TSIFR, TMIFR1 and TMIFR0. Each is used in conjunction with
the TEOD bit to transmit one of three IFR types defined in SAE J1850. What follows is a brief description
of each bit.
Because each of the bits used for transmitting an IFR with the BDLC module is used to transmit a
particular type of IFR, only one bit should be set by the CPU at a time. However, should more than one of
these bits get set at one time, a priority encoding scheme is used to determine which type of IFR is sent.
This scheme prevents unpredictable operation caused by conflicting signals to the BDLC module. Table
4-8 illustrates which IFR bit will actually be acted upon by the BDLC module should multiple IFR bits get
set at the same time.
NOTE:
68
As with transmitted messages, IFRs transmitted by the BDLC module will also be
received by the BDLC module. For a description of how IFR bytes received by the
BDLC module should be handled, refer to Section 4.7 Receiving An In-Frame
Response (IFR) on page 78.
Block Guide — S12BDLC_BG V01.03
Table 4-8 IFR Control Bit Priority Encoding
READ/WRITE
ACTUAL
TSIFR
TMIFR1
TMIFR0
TSIFR
TMIFR1
TMIFR0
0
0
0
0
0
0
1
X
X
1
0
0
0
1
X
0
1
0
0
0
1
0
0
1
4.6.3 Transmit Single Byte IFR
The Transmit Single Byte IFR (TSIFR) bit in DLCBCR2 is used to transmit Type 1 and Type 2 IFRs onto
the SAE J1850 bus. If this bit is set after a byte is loaded into the BDR, the BDLC module will attempt to
send that byte, preceded by the appropriate Normalization Bit, as a single byte IFR without a CRC. If
arbitration is lost, the BDLC module will automatically attempt to transmit the byte again (without a
Normalization Bit) as soon as the byte winning arbitration completes transmission. Attempts to transmit
the byte will continue until either the byte is successfully transmitted, the TEOD bit is set by the user or
an error is detected on the bus.
The user must set the TSIFR bit before the EOD following the main part of the message frame is received,
or no IFR transmit attempts will be made for the current message. If another node does transmit an IFR to
this message or a reception error occurs, the TSIFR bit will be cleared. If not, the IFR will be transmitted
after the EOD of the next received message.
The TSIFR bit will be automatically cleared once the EOD following one or more IFR bytes has been
received or an error is detected on the bus.
4.6.4 Transmit Multi-Byte IFR 1
The Transmit Multi-Byte IFR 1 (TMIFR1) bit is used to transmit an SAE J1850 Type 3 IFR with a CRC
byte appended. If this bit is set after the user has loaded the first byte of a multi-byte IFR into the
DLCBDR, the BDLC module will begin transmitting that byte, preceded by the appropriate Normalization
Bit, onto the SAE J1850 bus. Once this happens a TDRE interrupt will occur, indicating to the user that
the next IFR byte should be loaded into the DLCBDR. When the last byte to be transmitted is written to
the DLCBDR, the user sets the TEOD bit. This will cause a CRC byte and an EOD symbol to be
transmitted following the last IFR byte.
As with the TSIFR bit, the TMIFR1 bit must be set before the EOD symbol is received, or it will remain
cleared and no IFR transmit attempt will be made. The TMIFR1 bit will be cleared once the CRC byte and
EOD are transmitted, if an error is detected on the bus, if a loss of arbitration occurs during the IFR
transmission or if a transmitter underrun occurs when the user fails to service the TDRE interrupt in a
timely manner. If a loss of arbitration occurs while the Type 3 IFR is being transmitted, transmission will
halt immediately and the loss of arbitration will be indicated in the DLCBSVR.
69
Block Guide — S12BDLC_BG V01.03
4.6.5 Transmit Multi-Byte IFR 0
The Transmit Multi-Byte IFR 0 (TMIFR0) bit is used to transmit an SAE J1850 Type 3 IFR without a CRC
byte appended. If this bit is set after the user has loaded the first byte of a multi-byte IFR into the
DLCBDR, the BDLC module will begin transmitting that byte, preceded by the appropriate Normalization
Bit, onto the SAE J1850 bus. Once this happens a TDRE interrupt will occur, indicating to the user that
the next IFR byte should be loaded into the DLCBDR. When the last byte to be transmitted is written to
the DLCBDR, the user sets the TEOD bit. This will cause an EOD symbol to be transmitted following the
last IFR byte.
As with the TSIFR and TMIFR1 bits, the TMIFR0 bit must be set before the EOD symbol is received, or
it will remain cleared and no IFR transmit attempt will be made. The TMIFR0 bit will be cleared once the
CRC byte and EOD are transmitted, if an error is detected on the bus, if a loss of arbitration occurs during
the IFR transmission or if a transmitter underrun occurs when the user fails to service the TDRE interrupt
in a timely manner. If a loss of arbitration occurs while the Type 3 IFR is being transmitted, transmission
will halt immediately and the loss of arbitration will be indicated in the DLCBSVR.
NOTE:
The TMIFR0 bit should not be used to transmit a Type 1 IFR. If a loss of arbitration
occurs on the last bit of a byte being transmitted using the TMIFR0 bit, two extra
logic ones will be transmitted to ensure that the IFR will not end on a byte
boundary. This can cause an error in a Type 1 IFR.
4.6.6 Transmitting An IFR with the BDLC module
While the design of the BDLC module makes the transmission of each type of IFR similar, the steps
necessary for sending each will be discussed. Again, a discussion of the bytes making up any particular
IFR is not within the scope of this document. For a more detailed description of the use of IFRs on an SAE
J1850 network, refer to the SAE J1850 document.
•
Transmitting a Type 1 IFR
To transmit a Type 1 IFR, the user loads the byte to be transmitted into the DLCBDR and sets both
the TSIFR bit and the TEOD bit. This will direct the BDLC module to attempt transmitting the byte
written to the DLCBDR one time, preceded by the appropriate Normalization Bit. If the
transmission is not successful, the byte will be discarded and no further transmission attempts will
be made. For an illustration of the steps described below, refer to Section 4-12 Transmitting A Type
1 IFR on page 72.
–
Step 1: Load the IFR Byte into the BDR
The user begins initiation of a Type 1 IFR by loading the desired IFR byte into the DLCBDR.
If a byte has already been written into the DLCBDR for transmission as a new message, the user
can simply write the IFR byte to the DLCBDR, replacing the previously written byte. This must
be done before the first EOD symbol is received.
–
70
Step 2: Set the TSIFR and TEOD Bits
Block Guide — S12BDLC_BG V01.03
The final step in transmitting a Type 1 IFR with the BDLC module is to set the TSIFR and
TEOD bits in DLCBCR2. Setting both bits will direct the BDLC module to make one attempt
at transmitting the byte in the DLCBDR as an IFR. If the byte is transmitted successfully, or if
an error or loss of arbitration occurs, TEOD and TSIFR will be cleared and no further transmit
attempts will be made.
•
Transmitting a Type 2 IFR
To transmit a Type 2 IFR, the user loads the byte to be transmitted into the DLCBDR and sets the
TSIFR bit. Once this is done, the BDLC module will attempt to transmit the byte in the DLCBDR
as a single byte IFR, preceded by the appropriate Normalization Bit. If the first BDLC module loses
arbitration on the first attempt, it will make repeated attempts to transmit this byte until it is
successful, an error occurs or the user sets the TEOD bit.
71
Block Guide — S12BDLC_BG V01.03
Enter Type 1 IFR
Transmit Routine
Load IFR byte
into DLCBDR
Set TSIFR and TEOD
No
Is DLCBSVR = $1C?
(Error Detected)
Is DLCBSVR = $14?
(LOA)
Yes
IFR byte is discarded
No
Yes
IFR byte is discarded
Jump to Receive IFR
Handling Routine
Once BDLC module detects,
or EOF, IFR transmit
attempt is complete
Exit Type 1 IFR
Transmit Routine
Figure 4-12 Transmitting A Type 1 IFR
–
Step 1: Load the IFR Byte into the BDR
As with the Type 1 IFR, the user begins initiation of a Type 2 IFR by loading the desired IFR
byte into the DLCBDR. If a byte has already been written into the DLCBDR for transmission
as a new message, the user can simply write the IFR byte to the DLCBDR, replacing the
previously written byte. This must be done before the first EOD symbol is received.
–
72
Step 2: Set the TSIFR Bit
Block Guide — S12BDLC_BG V01.03
The second step necessary for transmitting a Type 2 IFR is to set the TSIFR bit in DLCBCR2.
Setting this bit will direct the BDLC module to attempt to transmit the byte in the DLCBDR as
an IFR until it is successful. If the byte is transmitted successfully, or if an error or loss of
arbitration occurs, TSIFR will be cleared and no further transmit attempts will be made.
–
Step 3: If Necessary, Set the TEOD Bit
The third step in transmitting a Type 2 IFR is only necessary if the user wishes to halt the
transmission attempts. This may be necessary if the BDLC module’s attempt to transmit the
byte loaded into the DLCBDR continually loses arbitration, and the overall message length
approaches the 12-byte limit as defined in SAE J1850.
If it becomes necessary to halt the IFR transmission attempts, the user simply sets the TEOD bit
in BCR2. If the BDLC module is between transmission attempts, it will make one more attempt
to transmit the IFR byte. If it is transmitting the byte when TEOD is set, the BDLC module will
continue the transmission until it is successful or it loses arbitration to another transmitter. At
this point it will then discard the byte and make no more transmit attempts.
NOTE:
When transmitting a Type 2 IFR, the user should monitor the number of IFR bytes
received to ensure that the overall message length does not exceed the 12-byte limit
for the length of SAE J1850 messages. The user should set the TEOD bit when the
11th byte is received, which will prevent the 12-byte limit from being exceeded.
73
Block Guide — S12BDLC_BG V01.03
Enter Type 2 IFR
Transmit Routine
Load IFR byte
into DLCBDR
Set TSIFR in DLCBCR2
Jump to Receive IFR
Handling Routine
No
Is DLCBSVR = $1C?
(Error Detected)
Is DLCBSVR = $14?
(LOA)
Yes
No
Yes
IFR byte is discarded
Was this the last
transmit attempt?
No
Yes
IFR byte is discarded
Jump to Receive IFR
Handling Routine
Once BDLC module detects,
or EOF, IFR transmit
attempt is complete
Exit Type 1 IFR
Transmit Routine
Figure 4-13 Transmitting A Type 2 IFR
•
74
Transmitting a Type 3 IFR
No
Was the 11th
msg byte received?
Yes
Set TEOD in DLCBCR2
Block Guide — S12BDLC_BG V01.03
Transmitting a Type 3 IFR, with or without a CRC byte, is done in a fashion similar to transmitting
a message frame. The user loads the first byte to be transmitted into the DLCBDR and then sets the
appropriate TMIFR bit, depending upon whether a CRC byte is desired. When the last byte is
written to the BDR, the TEOD bit is set, and a CRC byte (if desired) and an EOD are then
transmitted. Because the two versions of the Type 3 IFR are transmitted identically, the description
which follows will discuss both. For an illustration of the Type 3 IFR transmit sequence, refer to
Figure 4-14 Transmitting A Type 3 IFR on page 77.
–
Step 1: Load the First IFR Byte into the DLCBDR
The user begins initiation of a Type 3 IFR, as with each of the other IFR types, by loading the
desired IFR byte into the DLCBDR. If a byte has already been written into the DLCBDR for
transmission as a new message, the user can simply write the first IFR byte to the DLCBDR,
replacing the previously written byte. This must be done before the first EOD symbol is
received.
–
Step 2: Set the TMIFR Bit
The second step necessary for transmitting a Type 3 IFR is to set the desired TMIFR bit in
DLCBCR2, depending upon whether or not a CRC is desired. As previously described in
Section 4.6.2 BDLC IFR Transmit Control Bits on page 68, the TMIFR1 bit should be set if the
user requires a CRC byte to be appended following the last byte of the Type 3 IFR, and TMIFR0
if no CRC byte is required.
Setting the TMIFR1 or TMIFR0 bit will direct the BDLC module to transmit the byte in the
BDR as the first byte of a single or multi-byte IFR preceded by the appropriate Normalization
Bit. Once this has occurred, the DLCBSVR will reflect that the next byte of the IFR can be
written to the DLCBDR (TDRE interrupt).
NOTE:
–
The user must set the TMIFR1 or TMIFR0 bit before the EOD following the main
part of the message frame is received, or no IFR transmit attempts will be made for
the current message. If another node does transmit an IFR to this message or a
reception error occurs, the TMIFR1 or TMIFR0 bit will be cleared. If not, the IFR
will be transmitted after the EOD of the next received message.
Step 3: When TDRE is Indicated, Write the Next IFR Byte into the DLCBDR
When a TDRE state is reflected in the DLCBSVR, the CPU writes the next IFR byte to be
transmitted into the DLCBDR, clearing the TDRE interrupt. This step is repeated until the last
IFR byte to be transmitted is written to the DLCBDR.
NOTE:
–
As when transmitting a message, when transmitting a Type 3 IFR the user may write
two, or possibly even three of the bytes to be transmitted into the DLCBDR before
the first RxIFR interrupt occurs. For this reason, the user should never use receive
IFR byte interrupts to control the sequencing of IFR bytes to be transmitted.
Step 4: Write the Last IFR Byte into the DLCBDR and Set TEOD
Once the last IFR byte to be transmitted is written to the DLCBDR, the CPU then sets the TEOD
bit in DLCBCR2. Once the TEOD bit is set, after the last IFR byte written to the DLCBDR is
transmitted onto the bus, if the TMIFR1 bit has been set the BDLC module will begin
75
Block Guide — S12BDLC_BG V01.03
transmitting the CRC byte, followed by an EOD. If the TMIFR0 bit has been set, the last IFR
byte will immediately be followed by the transmission of an EOD. Following the EOD, and
EOF will be recognized and the message will be complete.
If at any time during the transmission of a Type 3 IFR a loss of arbitration occurs, the TMIFR
bit which is set and the TEOD bit (if set) will be cleared, any IFR byte being transmitted will be
discarded and the loss of arbitration state will be reflected in the DLCBSVR. Likewise, if an
error is detected during the transmission of a Type 3 IFR the IFR control bits will be cleared,
the byte being transmitted will be discarded and the DLCBSVR will reflect the detected error.
NOTE:
If the Type 3 IFR being transmitted is made up of a single byte, the appropriate
TMIFR bit and the TEOD bit can be set at the same time. The BDLC module will
then treat that byte as both the first and last IFR byte to be sent.
4.6.7 Transmitting IFR Exceptions
This basic IFR transmitting flow can be interrupted for the same reasons as a normal message
transmission. The IFR transmit process can be adversely affected due to a loss of arbitration, an Invalid or
Out of Range Symbol, or due to a transmitter underrun caused by the CPU failing to service a TDRE
interrupt in a timely fashion. For a description of how these exceptions can affect the IFR transmit process,
refer to Section 4.4.2 Transmitting Exceptions on page 60.
76
Block Guide — S12BDLC_BG V01.03
Enter Type 3 IFR
Transmit Routine
Write first IFR
byte to be transmitted
into DLCBDR
A
Set desired
TMIFR bit in DLCBCR2
Load next byte to be
transmitted into DLCBDR
(clears TDRE)
Set TEOD bit in
DLCBCR2
Yes
Only one byte to
transmit?
No
No
Is this the last
byte?
Yes
Yes
Is DLCBSVR = $00?
For interrupt driven systems,
this marks the beginning of the
transmit Type 3 IFR section of
the BDLC module interrupt
service routine
Abandon IFR
transmit attempt
No
Yes
Set TEOD bit
in DLCBCR2
B
Is DLCBSVR = $1C?
(Invalid Symbol)
Once BDLC module detects
EOF, IFR transmit
attempt is complete
No
B
Jump to IFR
Receive Routine
Exit Type 3 IFR
Transmit Routine
Yes
Is DLCBSVR = $14?
(LOA)
No
Is DLCBSVR = $10?
(TDRE)
No
Yes
NOTE: The EOF and CRC Error interrupts
are handled in the IFR Receive Routine
A
Figure 4-14 Transmitting A Type 3 IFR
77
Block Guide — S12BDLC_BG V01.03
4.7 Receiving An In-Frame Response (IFR)
Receiving an In-Frame Response with the BDLC module is very similar to receiving a message frame. As
each byte of an IFR is received, the DLCBSVR will indicate this to the CPU. An EOF indication in the
DLCBSVR indicates that the IFR (and message) is complete. Also, the IMSG bit can also be used to
command the BDLC module to mask any further network activity from the CPU, including IFR bytes
being received, until the next valid SOF is received.
NOTE:
As with a message transmission, the IMSG bit should never be used to ignore the
BDLC module’s own IFR transmissions. This is again due to the DLCBSVR bits
being inhibited from updating until IMSG is cleared, preventing the CPU from
detecting any IFR-related state changes which may be of interest.
4.7.1 Receiving an IFR with the BDLC module
Receiving an IFR from the SAE J1850 bus requires the same procedure that receiving a message does,
except that as each byte is received the Received IFR Byte (RxIFR) state is indicated in the DLCBSVR.
All other actions are the same. For an illustration of the steps described below, refer to Figure 4-15
Receiving An IFR With the BDLC module on page 79.
•
Step 1: When RxIFR Interrupt Occurs, Retrieve IFR Byte
When the first byte of an IFR following a valid EOD symbol is received that byte is placed in the
DLCBDR, and an RxIFR state is reflected in the DLCBSVR. No indication of the EOD reception
in made, since the RxIFR state will indicate that the main portion of the message has ended and the
IFR portion has begun.
The RxIFR interrupt is cleared when the received IFR byte is read from the DLCBDR. Once this is
done, no further CPU intervention is necessary until the next IFR byte is received, and this step is
repeated. As with a message reception, all bytes of the IFR, including the CRC byte, will be placed
into the DLCBDR as they are received for the CPU to retrieve.
•
When an EOF is Received, the IFR (and Message) is Complete
Once all IFR bytes (including the possible CRC byte) have been received from the bus, the bus will
again be idle for a time period equal to an EOD symbol. Following this, the BDLC module will
determine whether or not the last byte of the IFR is a CRC byte, and if so verify that the CRC byte
is correct. If the CRC byte is not correct, this will be reflected in the DLCBSVR.
After an additional period of time the EOD symbol will transition into an EOF symbol. When the
EOF is received it will be reflected in the DLCBSVR, indicating to the user that the IFR, and the
message, is complete.
78
Block Guide — S12BDLC_BG V01.03
.
Enter IFR Receive
Routine
Yes
Is DLCBSVR = $1C/$18?
(Error Detected)
Discard received
IFR bytes
B
No
Is DLCBSVR = $08?
(RxIFR)
Yes
Read byte in DLCBDR
No
Is this an IFR
xmit reflection?
No
Filter received IFR byte
Yes
Store received IFR byte
(in case of LOA)
B
Once BDLC module Detects
EOF, IFR
reception is complete
Yes
Is DLCBSVR = $04?
(EOF)
Yes
Store received IFR byte
No
A
Is this IFR
of any interest?
No
Exit IFR Receive
Routine
B
Set IMSG bit in DLCBCR1
A
Figure 4-15 Receiving An IFR With the BDLC module
4.7.2 Receiving IFR Exceptions
This basic IFR receiving flow can be interrupted for the same reasons as a normal message reception. The
IFR receiving process can be adversely affected due to a CRC error, an Invalid or Out of Range Symbol
or due to a receiver overrun caused by the CPU failing to service an RxIFR interrupt in a timely fashion.
79
Block Guide — S12BDLC_BG V01.03
For a description of how these exceptions can affect the IFR receiving process, refer to Section 4.5.4
Receiving Exceptions on page 64.
4.8 Special BDLC Module Operations
There are a few special operations which the BDLC module can perform. What follows is a brief
description of each of these functions and when they might be used.
4.8.1 Transmitting Or Receiving A Block Mode Message
The BDLC module, because it handles each message on a byte-by-byte basis, has the inherent capability
of handling messages any number of bytes in length. While during normal operation this requires the user
to carefully monitor message lengths to ensure compliance with SAE J1850 message limits, often in a
production or diagnostic environment messages which exceed the SAE J1850 limits can be beneficial.
This is especially true when large amounts of configuration data need to be downloaded over the SAE
J1850 network.
Because of the BDLC module’s architecture, it can both transmit and receive messages of unlimited
length. The CRC calculations, both for transmitting and receiving, are not limited to eight bytes, but will
instead be calculated and verified using all bytes in the message, regardless of the number. All control bits,
including TEOD and IMSG, also work in an identical manner, regardless of the length of the message.
To transmit or receive these “Block Mode” messages, no extra BDLC module control functions must be
performed. The user simply transmits or receives as many bytes as desired in one message frame, and the
BDLC module will operate just as if a message of normal length was being used.
4.8.2 Receiving A Message In 4X Mode
In a diagnostic or production environment large amounts of data may need to be downloaded across the
network to a component or module. This data is often sent in a large “Block Mode” message (see above)
which violates the SAE J1850 limit for message length. In order to speed up the downloading of these large
blocks of data, they are sometimes transmitted at four times (4X) the normal bit rate for the Variable Pulse
Width modulation version of SAE J1850. This higher speed transmission, nominally 41.6kbps, allows
these large blocks to be transmitted much more quickly.
The BDLC module is designed to receive (but not transmit) messages transmitted at this higher speed. By
setting the RX4XE bit in DLCBCR2, the user can command the BDLC module to receive any message
sent over the network at a 4X rate.
If the BDLC module is placed in this 4X mode, messages transmitted at the normal bit rate will not be
received correctly. Likewise, 4X messages transmitted on the SAE J1850 bus when the BDLC module is
in normal mode will be interpreted as noise on the network by the BDLC module. The RX4XE bit is not
affected by entry or exit from BDLC module stop or wait modes. For more information on the RX4XE bit,
refer to Section • 4X Mode on page 57.
80
Block Guide — S12BDLC_BG V01.03
Enter BDLC module Transmit
Routine
C
A
Write first message
byte to be transmitted
into DLCBDR
No
Is this the last
byte?
Yes
For interrupt driven systems,
this marks the beginning of the
transmit section of the BDLC
module interrupt service
routine
Go to BDLC module
BREAK/Error Handling
Routine
Yes
Is DLCBSVR = $00?
No
Yes
Set TEOD bit
in DLCBCR2
Is DLCBSVR = $1C?
(Invalid Symbol)
IFR Received?
No
Yes
Jump to Receive IFR
Handling Routine
No
B
B
Jump to BDLC module
Receive Routine
Yes
Once BDLC module detects
EOF, transmit
attempt is complete
Is DLCBSVR = $14?
(LOA)
No
Is DLCBSVR = $10?
(TDRE)
No
Yes
Load next byte to be
transmitted into BDR
(clears TDRE)
Attempt another
transmission?
Yes
C
No
Exit BDLC module Transmit
Routine
A
NOTE: The EOF and CRC Error interrupts
are handled in the BDLC module Receive
Routine
Figure 4-16 Basic BDLC Module Transmit Flowchart
4.9 BDLC Module Initialization
This section includes sample flows for initializing the BDLC module and using it to transmit and receive
messages.
81
Block Guide — S12BDLC_BG V01.03
4.9.1 Initialization Sequence
To initialize the BDLC module, the user should first write the desired data to the configuration bits. The
BDLC module should then be taken out of digital and analog loopback mode and enabled. Exiting from
loopback mode will entail change of state indications in the DLCBSVR which must be dealt with. Once
this is complete, CPU interrupts can be enabled (if desired), and then the BDLC module is capable of SAE
J1850 serial network communication. For an illustration of the sequence necessary for initializing the
BDLC module, refer to Figure 4-17 Basic BDLC Module Initialization Flowchart on page 85.
4.9.2 Initializing the Configuration Bits
The first step necessary for initializing the BDLC module following an MCU reset is to write the desired
values to each of the BDLC module control registers. This is best done by storing predetermined
initialization values directly into these registers. The following description outlines a basic flow for
initializing the BDLC module. This basic flow does not detail more elaborate initialization routines, such
as performing digital and analog loopback tests before enabling the BDLC module for SAE J1850
communication. However, from the following descriptions and the BDLC module specification, the user
should be able to develop routines for performing various diagnostic procedures such as loopback tests.
•
Step 1 - Initialize DLCBARD
Begin initialization of the configuration bits by writing the desired analog transceiver configuration
data into the DLCBARD register. Following this write to DLCBARD, all of these bits will become
read only.
•
Step 2- Initialize DLCBRSR
The next step in BDLC module initialization is to write the desired bus clock divisor minus one into
the DLCBRSR register. The divisor should be chosen to generate a 1 MHz or 1.048576 MHz mux
interface clock (fbdlc). Following this write to DLCBRSR, all of these bits will become read only.
•
Step 3- Initialize DLCBCR2
The next step in BDLC module initialization should be writing the configuration bits into the
DLCBCR2 register. This initialization description assumes that the BDLC module will be put into
normal mode (not 4X mode), and that the BDLC module should not yet exit either digital or analog
loopback mode. Therefore, this step should write SMRST and DLOOP as logic ones, RX4XE as a
logic zero, write NBFS to the desired level, and write TEOD, TSIFR, TMIFR1 and TMIFR0 as
logic zeros. These last four bits MUST be written as logic zeros in order to prevent undesired
operation of the BDLC module.
•
Step 4- Initialize DLCBCR1
The next step in BDLC module initialization is to write the configuration bits in DLCBCR1. The
CLKS bit should be written to its desired values at this time, following which it will become
read-only. The IE bit should be written as a logic zero at this time so BDLC module interrupts of
the CPU will remain masked for the time being. The IMSG bit should be written as a logic one to
prevent any receive events from setting the DLCBSVR until a valid SOF (or BREAK) symbol has
been received by the BDLC module.
82
Block Guide — S12BDLC_BG V01.03
4.9.3 Exiting Loopback Mode and Enabling the BDLC module
Once the configuration bits have been written to the desired values, the BDLC module should be taken out
of loopback and connected to the SAE J1850 bus. This is done by clearing the DLOOP bit and then setting
the BDLCE bit in the DLCSCR.
•
Step 5- Perform Loopback Tests (optional)
Once the BDLC module is configured for desired operation, the user may wish to perform digital
and/or analog loopback tests to determine the integrity of the link to the SAE J1850 network. This
would involve leaving the DLOOP bit (DLCBCR2) set, setting the BDLCE bit, preforming the
desired loopback tests and finally exiting digital loopback mode by clearing DLOOP in the
DLCBCR2.
•
Step 6- Exit Loopback Mode and enable the BDLC module
If loopback mode tests are not to be preformed the BDLC module can be removed from digital
loopback mode by clearing the DLOOP bit. The BDLC module can then be enabled by setting the
BDLCE bit in the DLCSCR.
Once DLOOP is cleared and BDLCE is set, the BDLC module is ready for SAE J1850
communication. However, to ensure that the BDLC module does not attempt to receive a message
already in progress or to transmit a message while another device is transmitting, the BDLC module
must first observe an EOF symbol on the bus before the receiver will be activated. To activate the
transmitter, the BDLC module will need to observe an Inter-Frame Separator symbol.
4.9.4 Enabling BDLC Interrupts
The final step in readying the BDLC module for proper communication is to clear any pending interrupt
sources and then, if desired, enable BDLC module interrupts of the CPU.
•
Step 7- Clear Pending BDLC Interrupts
In order to ensure that the BDLC module does not immediately generate a CPU interrupt when
interrupts are enabled, the user should read the DLCBSVR to determine if any BDLC module
interrupt sources are pending before setting the IE bit in the BCR1. If the BSVR reads as a
%00000000, no interrupts are pending and the user is free to enable BDLC interrupts, if desired.
If the DLCBSVR indicates that an interrupt is pending, the user should perform whatever actions
are necessary to clear the interrupt source before enabling the interrupts. Whether any interrupts are
pending will depend primarily upon how much time passes between the exit from loopback modes
and enabling the BDLC module and the enabling of interrupts. It is a good practice to always clear
any source of interrupts before enabling interrupts on any MCU subsystem.
If any interrupts are pending (DLCBSVR not %00000000), then each interrupt source should be
dealt with accordingly. Once all of the interrupt sources have been dealt with, the DLCBSVR
should read %00000000, and the user is then free to enable BDLC interrupts.
•
Step 8- Enable BDLC Interrupts
83
Block Guide — S12BDLC_BG V01.03
The last step in initializing the BDLC module is to enable interrupts to the CPU, if so desired. This
is done by simply setting the IE bit in the DLCBCR1. Following this, the BDLC module is ready
for operating in interrupt mode. If the user chooses not to enable interrupts, the DLCBSVR must be
polled periodically to ensure that state changes in the BDLC module are detected and dealt with
appropriately.
84
Block Guide — S12BDLC_BG V01.03
BDLC module enters Run mode
from Reset mode
Write desired config.
data into DLCBARD
Write desired divisor - 1
into DLCBRSR
Write desired config.
data into DLCBCR2
Write desired config.
data into DLCBCR1
Preform
Loopback Tests Enable BDLC module by
setting BDLCE bit in
DLCSCR
Exit Loopback mode
by clearing
DLOOP
Perform Digital and
Analog Loopback mode
tests
Enable BDLC module by
setting BDLCE bit in
DLCSCR
Exit Loopback mode
by clearing
DLOOP
Read DLCBSVR
Process pending
BDLC interrupt
No
Is DLCBSVR = $00?
Yes
Set IE bit in DLCBCR1
to enable interrupts
Proceed to remaining
MCU initialization
Figure 4-17 Basic BDLC Module Initialization Flowchart
85
Block Guide — S12BDLC_BG V01.03
86
Block Guide — S12BDLC_BG V01.03
Section 5 Resets
5.1 General
The reset state of each individual bit is listed within Section 3 Memory Map and Registers which details
the registers and their bit-fields.
87
Block Guide — S12BDLC_BG V01.03
88
Block Guide — S12BDLC_BG V01.03
Section 6 Interrupts
6.1 General
Each change in status of the BDLC is encoded into the BDLC state vector register, (BSVR). Each state
reflected in the BSVR can generate a CPU interrupt through the ipi_bdlc_int output, if the BDLC
interrupts are enabled (IE = 1 in BCR1 Control register)
Table 6-1 shows this interrupt information for ipi_bdlc_int.
Table 6-1 Interrupt Summary
Interrupt
Interrupt Source
Priority
ipi_bdlc_int
Refer to table below
determined at chip-level
Refer to 3.3.2 for a listing of the interrupt sources.
89
Block Guide — S12BDLC_BG V01.03
90
Block Guide — S12BDLC_BG V01.03
Appendix A Electrical Specifications
N/A
91
Block Guide — S12BDLC_BG V01.03
92
Block Guide — S12BDLC_BG V01.03
User Guide End Sheet
93
Block Guide — S12BDLC_BG V01.03
FINAL PAGE OF
94
PAGES
94
Background Debug
Module (BDM) V4
HCS12
Microcontrollers
S12BDMV4/D
Rev. 4.05
10/2004
MOTOROLA.COM/SEMICONDUCTORS
Block Guide — S12BDM V4
Revision History
Version
Number
Revision
Date
Effective
Date
4.05
10/04/2004
10/04/2004
Added information for reserved register, which was added to
solve MUCts entry "Possible manipulation of return address
when exiting BDM active mode.".
+.1
11/15/2002
11/15/2002
A soft reset of the BDM and disable of the ACK function has
been added during low power modes.
10/31/2002
10/31/2002
Creation of block user guide from core user guide version 1.5
(Feb. 28, 2002). Changes include: updating format and adding
a clock source table. The feature bullets were updated to more
clearly show the differences from BDM2 - the predecessor of
BDM3. Spell check now passes if conditional tags are turned
off.
2/4/2003
2/4/2003
Original release
4.02
Author
Description of Changes
Motorola and the Stylized M Logo are registered trademarks of Motorola, Inc.
DigitalDNA is a trademark of Motorola, Inc.
This product incorporates SuperFlash® technology licensed from SST.
2
© Motorola, Inc., 2003
Block Guide — S12BDM V4
Table of Contents
List of Figures
Figure 1-1
Figure 3-1
Figure 3-2
Figure 3-3
Figure 4-1
Figure 4-2
Figure 4-3
Figure 4-4
Figure 4-5
Figure 4-6
Figure 4-7
Figure 4-8
BDM Block Diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5
BDM Status Register (BDMSTS). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
BDM CCR Holding Register (BDMCCR) . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
BDM Internal Register Position (BDMINR) . . . . . . . . . . . . . . . . . . . . . . . . . . 15
BDM Command Structure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
BDM Host-to-Target Serial Bit Timing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
BDM Target-to-Host Serial Bit Timing (Logic 1) . . . . . . . . . . . . . . . . . . . . . . 24
BDM Target-to-Host Serial Bit Timing (Logic 0) . . . . . . . . . . . . . . . . . . . . . . 25
Target Acknowledge Pulse (ACK) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Handshake Protocol at Command Level . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
ACK Abort Procedure at the Command Level . . . . . . . . . . . . . . . . . . . . . . . . 28
ACK Pulse and SYNC Request Conflict . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
List of Tables
Table 3-1
Table 3-2
Table 4-1
Table 4-2
Table 4-3
BDM Register Map Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
BDM Clock Sources. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
Hardware Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Firmware Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Tag Pin Function . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Section 1 Introduction to Background Debug Module V4 (BDMV4)
1.1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5
1.2
Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5
1.3
Modes of Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
1.3.1
Regular Run Modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
1.3.2
Secure Mode Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
1.3.3
Low-Power Modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Section 2 External Signal Description
2.1
2.2
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Detailed Signal Descriptions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
3
Block Guide — S12BDM V4
2.2.1
2.2.2
2.2.3
Background Interface Pin (BKGD) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
High Byte Instruction Tagging Pin (TAGHI) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Low Byte Instruction Tagging Pin (TAGLO) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Section 3 Memory Map/Register Definition
3.1
3.2
3.3
BDM Status Register . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
BDM CCR Holding Register . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
BDM Internal Register Position Register . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Section 4 Functional Description
4.1
4.2
4.3
4.4
4.5
4.6
4.7
4.8
4.9
4.10
4.11
4.12
4
Security. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
Enabling and Activating BDM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
BDM Hardware Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
Standard BDM Firmware Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
BDM Command Structure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
BDM Serial Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Serial Interface Hardware Handshake Protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Hardware Handshake Abort Procedure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
SYNC — Request Timed Reference Pulse . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Instruction Tracing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Instruction Tagging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Serial Communication Time-out . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Block Guide — S12BDM V4
Section 1 Introduction to Background Debug Module V4
(BDMV4)
This section describes the functionality of the Background Debug Module (BDM) sub-block of the HCS12
Core Platform.
A block diagram of the BDM is shown in Figure 1-1.
HOST
SYSTEM
BKGD
16-BIT SHIFT REGISTER
ADDRESS
ENTAG
BDMACT
INSTRUCTION DECODE
AND EXECUTION
TRACE
SDV
ENBDM
BUS INTERFACE
AND
CONTROL LOGIC
DATA
CLOCKS
STANDARD BDM
FIRMWARE
LOOKUP TABLE
CLKSW
Figure 1-1 BDM Block Diagram
1.1 Overview
The Background Debug Module (BDM) sub-block is a single-wire, background debug system
implemented in on-chip hardware for minimal CPU intervention. All interfacing with the BDM is done
via the BKGD pin.
BDMV4 has enhanced capability for maintaining synchronization between the target and host while
allowing more flexibility in clock rates. This includes a sync signal to show the clock rate and a handshake
signal to indicate when an operation is complete. The system is backwards compatible with older external
interfaces.
1.2 Features
•
Single-wire communication with host development system
•
BDMV4 (and BDM2): Enhanced capability for allowing more flexibility in clock rates
•
BDMV4: SYNC command to determine communication rate
•
BDMV4: GO_UNTIL command
•
BDMV4: Hardware handshake protocol to increase the performance of the serial communication
•
Active out of reset in special single-chip mode
5
Block Guide — S12BDM V4
•
Nine hardware commands using free cycles, if available, for minimal CPU intervention
•
Hardware commands not requiring active BDM
•
15 firmware commands execute from the standard BDM firmware lookup table
•
Instruction tagging capability
•
Software control of BDM operation during wait mode
•
Software selectable clocks
•
When secured, hardware commands are allowed to access the register space in Special Single-Chip
mode, if the FLASH and EEPROM erase tests fail.
1.3 Modes of Operation
BDM is available in all operating modes but must be enabled before firmware commands are executed.
Some system peripherals may have a control bit which allows suspending the peripheral function during
background debug mode.
1.3.1 Regular Run Modes
All of these operations refer to the part in run mode. The BDM does not provide controls to conserve power
during run mode.
•
Normal Operation
General operation of the BDM is available and operates the same in all normal modes.
•
Special single-chip mode
In special single-chip mode, background operation is enabled and active out of reset. This allows
programming a system with blank memory.
•
Special peripheral mode
BDM is enabled and active immediately out of reset. BDM can be disabled by clearing the
BDMACT bit in the BDM status (BDMSTS) register. The BDM serial system should not be used
in special peripheral mode.
•
Emulation Modes
General operation of the BDM is available and operates the same as in normal modes.
1.3.2 Secure Mode Operation
If the part is in secure mode, the operation of the BDM is reduced to a small subset of it’s regular
run mode operation. Secure operation prevents access to FLASH or EEPROM other than allowing
erasure.
6
Block Guide — S12BDM V4
1.3.3 Low-Power Modes
•
Wait Mode
The BDM cannot be used in wait mode if the system disables the clocks to the BDM.
There is a clearing mechanism associated with the WAIT instruction when the clocks to the BDM
(CPU core platform) are disabled. As the clocks restart from wait mode, the BDM receives a soft
reset (clearing any command in progress) and the ACK function will be disabled. This is a change
from previous BDM modules.
•
Stop Mode
The BDM is completely shutdown in stop mode.
There is a clearing mechanism associated with the STOP instruction. STOP must be enabled and
the part must go into stop mode for this to occur. As the clocks restart from stop mode, the BDM
receives a soft reset (clearing any command in progress) and the ACK function will be disabled.
This is a change from previous BDM modules.
7
Block Guide — S12BDM V4
8
Block Guide — S12BDM V4
Section 2 External Signal Description
2.1 Overview
A single-wire interface pin is used to communicate with the BDM system. Two additional pins are used
for instruction tagging. These pins are part of the Multiplexed External Bus Interface (MEBI) sub-block
and all interfacing between the MEBI and BDM is done within the Core interface boundary. Functional
descriptions of the pins are provided below for completeness.
•
BKGD — Background interface pin
•
TAGHI — High byte instruction tagging pin
•
TAGLO — Low byte instruction tagging pin
•
BKGD and TAGHI share the same pin.
•
TAGLO and LSTRB share the same pin.
NOTE:
Generally these pins are shared as described, but it is best to check the chip
description to make certain. All chips at the time of this writing have followed this
pin sharing scheme.
2.2 Detailed Signal Descriptions
2.2.1 Background Interface Pin (BKGD)
Debugging control logic communicates with external devices serially via the single-wire background
interface pin (BKGD). During reset, this pin is a mode select input which selects between normal and
special modes of operation. After reset, this pin becomes the dedicated serial interface pin for the
background debug mode.
2.2.2 High Byte Instruction Tagging Pin (TAGHI)
This pin is used to tag the high byte of an instruction. When instruction tagging is on, a logic 0 at the falling
edge of the external clock (ECLK) tags the high half of the instruction word being read into the instruction
queue.
2.2.3 Low Byte Instruction Tagging Pin (TAGLO)
This pin is used to tag the low byte of an instruction. When instruction tagging is on and low strobe is
enabled, a logic 0 at the falling edge of the external clock (ECLK) tags the low half of the instruction word
being read into the instruction queue.
9
Block Guide — S12BDM V4
10
Block Guide — S12BDM V4
Section 3 Memory Map/Register Definition
A summary of the registers associated with the BDM is shown in Table 3-1. Registers are accessed by
host-driven communications to the BDM hardware using READ_BD and WRITE_BD commands.
Detailed descriptions of the registers and associated bits are given in the subsections that follow..
Table 3-1 BDM Register Map Summary
Address
Register
Name
$FF00
Reserved
$FF01
BDMSTS
$FF02
Reserved
$FF03
Reserved
$FF04
Reserved
$FF05
Reserved
$FF06
BDMCCR
$FF07
BDMINR
$FF08
Reserved
$FF09
Reserved
Read:
Bit 7
6
5
4
3
2
1
Bit 0
X
X
X
X
X
X
0
0
SDV
TRACE
UNSEC
0
Write:
Read:
Write:
Read:
ENBDM
BDMACT
ENTAG
CLKSW
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
CCR7
CCR6
CCR5
CCR4
CCR3
CCR2
CCR1
CCR0
0
REG14
REG13
REG12
REG11
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
0
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
Read:
Write:
= Unimplemented, Reserved
X
= Indeterminate
= Implemented (do not alter)
0
= Always read zero
11
Block Guide — S12BDM V4
Table 3-1 BDM Register Map Summary
Address
Register
Name
$FF0A
Reserved
$FF0B
Reserved
Read:
Bit 7
6
5
4
3
2
1
Bit 0
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
X
Write:
Read:
Write:
= Unimplemented, Reserved
X
= Implemented (do not alter)
= Indeterminate
0
= Always read zero
3.1 BDM Status Register
Register address $FF01
7
R
W
ENBDM
6
BDMACT
5
ENTAG
4
3
SDV
TRACE
2
CLKSW
1
0
UNSEC
0
Reset:
Special single-chip mode:
1
1
0
0
0
0
0
0
Special peripheral mode:
0
1
0
0
0
0
0
0
All other modes:
0
0
0
0
0
0
0
0
= Unimplemented or Reserved
= Implemented (do not alter)
Figure 3-1 BDM Status Register (BDMSTS)
Read: All modes through BDM operation
Write: All modes but subject to the following:
12
–
BDMACT can only be set by BDM hardware upon entry into BDM. It can only be cleared by
the standard BDM firmware lookup table upon exit from BDM active mode.
–
CLKSW can only be written via BDM hardware or standard BDM firmware write commands.
–
All other bits, while writable via BDM hardware or standard BDM firmware write commands,
should only be altered by the BDM hardware or standard firmware lookup table as part of BDM
command execution.
–
ENBDM should only be set via a BDM hardware command if the BDM firmware commands
are needed. (This does not apply in Special Single-Chip Mode).
Block Guide — S12BDM V4
ENBDM — Enable BDM
This bit controls whether the BDM is enabled or disabled. When enabled, BDM can be made active to
allow firmware commands to be executed. When disabled, BDM cannot be made active but BDM
hardware commands are still allowed.
1 = BDM enabled
0 = BDM disabled
NOTE:
ENBDM is set by the firmware immediately out of reset in special single-chip mode.
In secure mode, this bit will not be set by the firmware until after the EEPROM and
FLASH erase verify tests are complete.
BDMACT — BDM active status
This bit becomes set upon entering BDM. The standard BDM firmware lookup table is then enabled
and put into the memory map. BDMACT is cleared by a carefully timed store instruction in the
standard BDM firmware as part of the exit sequence to return to user code and remove the BDM
memory from the map.
1 = BDM active
0 = BDM not active
ENTAG — Tagging enable
This bit indicates whether instruction tagging in enabled or disabled. It is set when the TAGGO
command is executed and cleared when BDM is entered. The serial system is disabled and the tag
function enabled 16 cycles after this bit is written. BDM cannot process serial commands while
tagging is active.
1 = Tagging enabled
0 = Tagging not enabled or BDM active
SDV — Shift data valid
This bit is set and cleared by the BDM hardware. It is set after data has been transmitted as part of a
firmware read command or after data has been received as part of a firmware write command. It is
cleared when the next BDM command has been received or BDM is exited. SDV is used by the
standard BDM firmware to control program flow execution.
1 = Data phase of command is complete
0 = Data phase of command not complete
TRACE — TRACE1 BDM firmware command is being executed
This bit gets set when a BDM TRACE1 firmware command is first recognized. It will stay set as long
as continuous back-to-back TRACE1 commands are executed. This bit will get cleared when the next
command that is not a TRACE1 command is recognized.
1 = TRACE1 command is being executed
0 = TRACE1 command is not being executed
13
Block Guide — S12BDM V4
CLKSW — Clock switch
The CLKSW bit controls which clock the BDM operates with. It is only writable from a hardware
BDM command. A 150 cycle delay at the clock speed that is active during the data portion of the
command will occur before the new clock source is guaranteed to be active. The start of the next BDM
command uses the new clock for timing subsequent BDM communications.
Table 3-2 shows the resulting BDM clock source based on the CLKSW and the PLLSEL (Pll select
from the clock and reset generator) bits.
Table 3-2 BDM Clock Sources
PLLSEL
CLKSW
BDMCLK
0
0
Bus clock
0
1
Bus clock
1
0
Alternate clock (refer to the device specification to determine
the alternate clock source)
1
1
Bus clock dependent on the PLL
NOTE:
The BDM alternate clock source can only be selected when CLKSW = 0 and
PLLSEL = 1. The BDM serial interface is now fully synchronized to the alternate
clock source, when enabled. This eliminates frequency restriction on the alternate
clock which was required on previous versions. Refer to the device specification to
determine which clock connects to the alternate clock source input.
NOTE:
If the acknowledge function is turned on, changing the CLKSW bit will cause the
ACK to be at the new rate for the write command which changes it.
UNSEC — Unsecure
This bit is only writable in special single-chip mode from the BDM secure firmware and always gets
reset to zero. It is in a zero state as secure mode is entered so that the secure BDM firmware lookup
table is enabled and put into the memory map along with the standard BDM firmware lookup table.
The secure BDM firmware lookup table verifies that the on-chip EEPROM and FLASH EEPROM are
erased. This being the case, the UNSEC bit is set and the BDM program jumps to the start of the
standard BDM firmware lookup table and the secure BDM firmware lookup table is turned off. If the
erase test fails, the UNSEC bit will not be asserted.
1 = System is in a unsecured mode
0 = System is in a secured mode
NOTE:
14
When UNSEC is set, security is off and the user can change the state of the secure
bits in the on-chip FLASH EEPROM. Note that if the user does not change the state
of the bits to “unsecured” mode, the system will be secured again when it is next
taken out of reset.
Block Guide — S12BDM V4
3.2 BDM CCR Holding Register
Register address $FF06
R
W
Reset:
7
6
5
4
3
2
1
0
CCR7
CCR6
CCR5
CCR4
CCR3
CCR2
CCR1
CCR0
0
0
0
0
0
0
0
0
Figure 3-2 BDM CCR Holding Register (BDMCCR)
Read: All modes
Write: All modes
NOTE:
When BDM is made active, the CPU stores the value of the CCR register in the
BDMCCR register. However, out of special single-chip reset, the BDMCCR is set
to $D8 and not $D0 which is the reset value of the CCR register.
When entering background debug mode, the BDM CCR holding register is used to save the contents of
the condition code register of the user’s program. It is also used for temporary storage in the standard BDM
firmware mode. The BDM CCR holding register can be written to modify the CCR value.
3.3 BDM Internal Register Position Register
Register address $FF07
R
7
6
5
4
3
2
1
0
0
REG14
REG13
REG12
REG11
0
0
0
0
0
0
0
0
0
0
0
W
Reset:
= Unimplemented or Reserved
Figure 3-3 BDM Internal Register Position (BDMINR)
Read: All modes
Write: Never
REG14–REG11 — Internal register map position
These four bits show the state of the upper five bits of the base address for the system’s relocatable
register block. BDMINR is a shadow of the INITRG register which maps the register block to any
2K byte space within the first 32K bytes of the 64K byte address space.
15
Block Guide — S12BDM V4
16
Block Guide — S12BDM V4
Section 4 Functional Description
The BDM receives and executes commands from a host via a single wire serial interface. There are two
types of BDM commands, namely, hardware commands and firmware commands.
Hardware commands are used to read and write target system memory locations and to enter active
background debug mode, see 4.3 BDM Hardware Commands. Target system memory includes all
memory that is accessible by the CPU.
Firmware commands are used to read and write CPU resources and to exit from active background debug
mode, see 4.4 Standard BDM Firmware Commands. The CPU resources referred to are the
accumulator (D), X index register (X), Y index register (Y), stack pointer (SP), and program counter (PC).
Hardware commands can be executed at any time and in any mode excluding a few exceptions as
highlighted, see 4.3 BDM Hardware Commands. Firmware commands can only be executed when the
system is in active background debug mode (BDM).
4.1 Security
If the user resets into special single-chip mode with the system secured, a secured mode BDM firmware
lookup table is brought into the map overlapping a portion of the standard BDM firmware lookup table.
The secure BDM firmware verifies that the on-chip EEPROM and FLASH EEPROM are erased. This
being the case, the UNSEC bit will get set. The BDM program jumps to the start of the standard BDM
firmware and the secured mode BDM firmware is turned off and all BDM commands are allowed. If the
EEPROM or FLASH do not verify as erased, the BDM firmware sets the ENBDM bit, without asserting
UNSEC, and the firmware enters a loop. This causes the BDM hardware commands to become enabled,
but does not enable the firmware commands. This allows the BDM hardware to be used to erase the
EEPROM and FLASH. After execution of the secure firmware, regardless of the results of the erase tests,
the CPU registers, INITEE and PPAGE, will no longer be in their reset state.
4.2 Enabling and Activating BDM
The system must be in active BDM to execute standard BDM firmware commands. BDM can be activated
only after being enabled. BDM is enabled by setting the ENBDM bit in the BDM status (BDMSTS)
register. The ENBDM bit is set by writing to the BDM status (BDMSTS) register, via the single-wire
interface, using a hardware command such as WRITE_BD_BYTE.
17
Block Guide — S12BDM V4
After being enabled, BDM is activated by one of the following(1):
•
Hardware BACKGROUND command
•
BDM external instruction tagging mechanism
•
CPU BGND instruction
•
Breakpoint sub-block’s force or tag mechanism(2)
When BDM is activated, the CPU finishes executing the current instruction and then begins executing the
firmware in the standard BDM firmware lookup table. When BDM is activated by the breakpoint
sub-block, the type of breakpoint used determines if BDM becomes active before or after execution of the
next instruction.
NOTE:
If an attempt is made to activate BDM before being enabled, the CPU resumes
normal instruction execution after a brief delay. If BDM is not enabled, any
hardware BACKGROUND commands issued are ignored by the BDM and the CPU
is not delayed.
In active BDM, the BDM registers and standard BDM firmware lookup table are mapped to addresses
$FF00 to $FFFF. BDM registers are mapped to addresses $FF00 to $FF07. The BDM uses these registers
which are readable anytime by the BDM. However, these registers are not readable by user programs.
4.3 BDM Hardware Commands
Hardware commands are used to read and write target system memory locations and to enter active
background debug mode. Target system memory includes all memory that is accessible by the CPU such
as on-chip RAM, EEPROM, FLASH EEPROM, I/O and control registers, and all external memory.
Hardware commands are executed with minimal or no CPU intervention and do not require the system to
be in active BDM for execution, although, they can still be executed in this mode. When executing a
hardware command, the BDM sub-block waits for a free CPU bus cycle so that the background access does
not disturb the running application program. If a free cycle is not found within 128 clock cycles, the CPU
is momentarily frozen so that the BDM can steal a cycle. When the BDM finds a free cycle, the operation
does not intrude on normal CPU operation provided that it can be completed in a single cycle. However,
if an operation requires multiple cycles the CPU is frozen until the operation is complete, even though the
BDM found a free cycle.
The BDM hardware commands are listed in Table 4-1.
NOTES:
1. BDM is enabled and active immediately out of special single-chip reset.
2. This method is only available on systems that have a a Breakpoint or a Debug sub-block.
18
Block Guide — S12BDM V4
Table 4-1 Hardware Commands
Opcode
(hex)
Data
Description
BACKGROUND
90
None
Enter background mode if firmware is enabled. If enabled,
an ACK will be issued when the part enters active background
mode.
ACK_ENABLE
D5
None
Enable Handshake. Issues an ACK pulse after the command
is executed.
ACK_DISABLE
D6
None
Disable Handshake. This command does not issue an
ACK pulse.
READ_BD_BYTE
E4
Read from memory with standard BDM firmware lookup table
16-bit address
in map. Odd address data on low byte; even address data on
16-bit data out
high byte.
READ_BD_WORD
EC
16-bit address Read from memory with standard BDM firmware lookup table
16-bit data out in map. Must be aligned access.
READ_BYTE
E0
Read from memory with standard BDM firmware lookup table
16-bit address
out of map. Odd address data on low byte; even address data
16-bit data out
on high byte.
READ_WORD
E8
16-bit address Read from memory with standard BDM firmware lookup table
16-bit data out out of map. Must be aligned access.
WRITE_BD_BYTE
C4
Write to memory with standard BDM firmware lookup table in
16-bit address
map. Odd address data on low byte; even address data on
16-bit data in
high byte.
WRITE_BD_WORD
CC
16-bit address Write to memory with standard BDM firmware lookup table in
16-bit data in map. Must be aligned access.
WRITE_BYTE
C0
Write to memory with standard BDM firmware lookup table out
16-bit address
of map. Odd address data on low byte; even address data on
16-bit data in
high byte.
WRITE_WORD
C8
16-bit address Write to memory with standard BDM firmware lookup table out
16-bit data in of map. Must be aligned access.
Command
NOTE:
If enabled, ACK will occur when data is ready for transmission for all BDM READ commands and will occur after the write
is complete for all BDM WRITE commands.
The READ_BD and WRITE_BD commands allow access to the BDM register locations. These locations
are not normally in the system memory map but share addresses with the application in memory. To
distinguish between physical memory locations that share the same address, BDM memory resources are
enabled just for the READ_BD and WRITE_BD access cycle. This allows the BDM to access BDM
locations unobtrusively, even if the addresses conflict with the application memory map.
19
Block Guide — S12BDM V4
4.4 Standard BDM Firmware Commands
Firmware commands are used to access and manipulate CPU resources. The system must be in active
BDM to execute standard BDM firmware commands, see 4.2 Enabling and Activating BDM. Normal
instruction execution is suspended while the CPU executes the firmware located in the standard BDM
firmware lookup table. The hardware command BACKGROUND is the usual way to activate BDM.
As the system enters active BDM, the standard BDM firmware lookup table and BDM registers become
visible in the on-chip memory map at $FF00–$FFFF, and the CPU begins executing the standard BDM
firmware. The standard BDM firmware watches for serial commands and executes them as they are
received.
The firmware commands are shown in Table 4-2.
Table 4-2 Firmware Commands
Opcode
(hex)
Data
Description
READ_NEXT
62
16-bit data out
Increment X by 2 (X = X + 2), then read word X points to.
READ_PC
63
16-bit data out
Read program counter.
READ_D
64
16-bit data out
Read D accumulator.
READ_X
65
16-bit data out
Read X index register.
READ_Y
66
16-bit data out
Read Y index register.
READ_SP
67
16-bit data out
Read stack pointer.
WRITE_NEXT
42
16-bit data in
Increment X by 2 (X = X + 2), then write word to location
pointed to by X.
WRITE_PC
43
16-bit data in
Write program counter.
WRITE_D
44
16-bit data in
Write D accumulator.
WRITE_X
45
16-bit data in
Write X index register.
WRITE_Y
46
16-bit data in
Write Y index register.
WRITE_SP
47
16-bit data in
Write stack pointer.
GO
08
none
Go to user program. If enabled, ACK will occur when
leaving active background mode.
GO_UNTIL2
0C
none
Go to user program. If enabled, ACK will occur upon
returning to active background mode.
TRACE1
10
none
Execute one user instruction then return to active BDM. If
enabled, ACK will occur upon returning to active
background mode.
TAGGO
18
none
Enable tagging and go to user program. There is no ACK
pulse related to this command.
Command1
NOTES:
1. If enabled, ACK will occur when data is ready for transmission for all BDM READ commands and will occur after the write
is complete for all BDM WRITE commands.
2. Both WAIT (with clocks to the S12 CPU core disabled) and STOP disable the ACK function. The GO_UNTIL command
will not get an Acknowledge if one of these two CPU instructions occurs before the "UNTIL" instruction. This can be a problem for any instruction that uses ACK, but GO_UNTIL is a lot more difficult for the development tool to time-out.
20
Block Guide — S12BDM V4
4.5 BDM Command Structure
Hardware and firmware BDM commands start with an 8-bit opcode followed by a 16-bit address and/or a
16-bit data word depending on the command. All the read commands return 16 bits of data despite the byte
or word implication in the command name.
NOTE:
8-bit reads return 16-bits of data, of which, only one byte will contain valid data. If
reading an even address, the valid data will appear in the MSB. If reading an odd
address, the valid data will appear in the LSB.
NOTE:
16-bit misaligned reads and writes are not allowed. If attempted, the BDM will
ignore the least significant bit of the address and will assume an even address from
the remaining bits.
For hardware data read commands, the external host must wait 150 bus clock cycles after sending the
address before attempting to obtain the read data. This is to be certain that valid data is available in the
BDM shift register, ready to be shifted out. For hardware write commands, the external host must wait
150 bus clock cycles after sending the data to be written before attempting to send a new command. This
is to avoid disturbing the BDM shift register before the write has been completed. The 150 bus clock cycle
delay in both cases includes the maximum 128 cycle delay that can be incurred as the BDM waits for a
free cycle before stealing a cycle.
For firmware read commands, the external host should wait 44 bus clock cycles after sending the
command opcode and before attempting to obtain the read data. This includes the potential of an extra 7
cycles when the access is external with a narrow bus access (+1 cycle) and / or a stretch (+1, 2, or 3 cycles),
(7 cycles could be needed if both occur). The 44 cycle wait allows enough time for the requested data to
be made available in the BDM shift register, ready to be shifted out.
NOTE:
This timing has increased from previous BDM modules due to the new capability in
which the BDM serial interface can potentially run faster than the bus. On previous
BDM modules this extra time could be hidden within the serial time.
For firmware write commands, the external host must wait 32 bus clock cycles after sending the data to be
written before attempting to send a new command. This is to avoid disturbing the BDM shift register
before the write has been completed.
The external host should wait 64 bus clock cycles after a TRACE1 or GO command before starting any
new serial command. This is to allow the CPU to exit gracefully from the standard BDM firmware lookup
table and resume execution of the user code. Disturbing the BDM shift register prematurely may adversely
affect the exit from the standard BDM firmware lookup table.
NOTE:
If the bus rate of the target processor is unknown or could be changing, it is
recommended that the ACK (acknowledge function) be used to indicate when an
operation is complete. When using ACK, the delay times are automated.
21
Block Guide — S12BDM V4
Figure 4-1 represents the BDM command structure. The command blocks illustrate a series of eight bit
times starting with a falling edge. The bar across the top of the blocks indicates that the BKGD line idles
in the high state. The time for an 8-bit command is 8 × 16 target clock cycles.(1)
HARDWARE
READ
8 BITS
AT ∼16 TC/BIT
16 BITS
AT ∼16 TC/BIT
COMMAND
ADDRESS
150-BC
DELAY
16 BITS
AT ∼16 TC/BIT
DATA
NEXT
COMMAND
150-BC
DELAY
HARDWARE
WRITE
COMMAND
ADDRESS
DATA
NEXT
COMMAND
44-BC
DELAY
FIRMWARE
READ
COMMAND
NEXT
COMMAND
DATA
32-BC
DELAY
FIRMWARE
WRITE
COMMAND
DATA
NEXT
COMMAND
64-BC
DELAY
GO,
TRACE
NEXT
COMMAND
COMMAND
BC = BUS CLOCK CYCLES
TC = TARGET CLOCK CYCLES
Figure 4-1 BDM Command Structure
4.6 BDM Serial Interface
The BDM communicates with external devices serially via the BKGD pin. During reset, this pin is a mode
select input which selects between normal and special modes of operation. After reset, this pin becomes
the dedicated serial interface pin for the BDM.
The BDM serial interface is timed using the clock selected by the CLKSW bit in the status register see
3.1 BDM Status Register. This clock will be referred to as the target clock in the following explanation.
The BDM serial interface uses a clocking scheme in which the external host generates a falling edge on
the BKGD pin to indicate the start of each bit time. This falling edge is sent for every bit whether data is
transmitted or received. Data is transferred most significant bit (MSB) first at 16 target clock cycles per
bit. The interface times out if 512 clock cycles occur between falling edges from the host.
The BKGD pin is a pseudo open-drain pin and has an weak on-chip active pull-up that is enabled at all
times. It is assumed that there is an external pull-up and that drivers connected to BKGD do not typically
drive the high level. Since R-C rise time could be unacceptably long, the target system and host provide
NOTES:
1. Target clock cycles are cycles measured using the target MCU’s serial clock rate. See 4.6 BDM Serial Interface and
3.1 BDM Status Register for information on how serial clock rate is selected.
22
Block Guide — S12BDM V4
brief driven-high (speedup) pulses to drive BKGD to a logic 1. The source of this speedup pulse is the host
for transmit cases and the target for receive cases.
The timing for host-to-target is shown in Figure 4-2 and that of target-to-host in Figure 4-3 and
Figure 4-4. All four cases begin when the host drives the BKGD pin low to generate a falling edge. Since
the host and target are operating from separate clocks, it can take the target system up to one full clock
cycle to recognize this edge. The target measures delays from this perceived start of the bit time while the
host measures delays from the point it actually drove BKGD low to start the bit up to one target clock cycle
earlier. Synchronization between the host and target is established in this manner at the start of every bit
time.
Figure 4-2 shows an external host transmitting a logic 1 and transmitting a logic 0 to the BKGD pin of a
target system. The host is asynchronous to the target, so there is up to a one clock-cycle delay from the
host-generated falling edge to where the target recognizes this edge as the beginning of the bit time. Ten
target clock cycles later, the target senses the bit level on the BKGD pin. Internal glitch detect logic
requires the pin be driven high no later that eight target clock cycles after the falling edge for a logic 1
transmission.
Since the host drives the high speedup pulses in these two cases, the rising edges look like digitally driven
signals.
CLOCK
TARGET SYSTEM
HOST
TRANSMIT 1
HOST
TRANSMIT 0
PERCEIVED
START OF BIT TIME
TARGET SENSES BIT
10 CYCLES
SYNCHRONIZATION
UNCERTAINTY
EARLIEST
START OF
NEXT BIT
Figure 4-2 BDM Host-to-Target Serial Bit Timing
23
Block Guide — S12BDM V4
The receive cases are more complicated. Figure 4-3 shows the host receiving a logic 1 from the target
system. Since the host is asynchronous to the target, there is up to one clock-cycle delay from the
host-generated falling edge on BKGD to the perceived start of the bit time in the target. The host holds the
BKGD pin low long enough for the target to recognize it (at least two target clock cycles). The host must
release the low drive before the target drives a brief high speedup pulse seven target clock cycles after the
perceived start of the bit time. The host should sample the bit level about 10 target clock cycles after it
started the bit time.
CLOCK
TARGET SYSTEM
HOST
DRIVE TO
BKGD PIN
HIGH-IMPEDANCE
TARGET SYSTEM
SPEEDUP
PULSE
HIGH-IMPEDANCE
HIGH-IMPEDANCE
PERCEIVED
START OF BIT TIME
R-C RISE
BKGD PIN
10 CYCLES
10 CYCLES
HOST SAMPLES
BKGD PIN
Figure 4-3 BDM Target-to-Host Serial Bit Timing (Logic 1)
24
EARLIEST
START OF
NEXT BIT
Block Guide — S12BDM V4
Figure 4-4 shows the host receiving a logic 0 from the target. Since the host is asynchronous to the target,
there is up to a one clock-cycle delay from the host-generated falling edge on BKGD to the start of the bit
time as perceived by the target. The host initiates the bit time but the target finishes it. Since the target
wants the host to receive a logic 0, it drives the BKGD pin low for 13 target clock cycles then briefly drives
it high to speed up the rising edge. The host samples the bit level about 10 target clock cycles after starting
the bit time.
CLOCK
TARGET SYS.
HOST
DRIVE TO
BKGD PIN
HIGH-IMPEDANCE
SPEEDUP PULSE
TARGET SYS.
DRIVE AND
SPEEDUP PULSE
PERCEIVED
START OF BIT TIME
BKGD PIN
10 CYCLES
10 CYCLES
HOST SAMPLES
BKGD PIN
EARLIEST
START OF
NEXT BIT
Figure 4-4 BDM Target-to-Host Serial Bit Timing (Logic 0)
4.7 Serial Interface Hardware Handshake Protocol
BDM commands that require CPU execution are ultimately treated at the MCU bus rate. Since the BDM
clock source can be asynchronously related to the bus frequency, when CLKSW = 0, it is very helpful to
provide a handshake protocol in which the host could determine when an issued command is executed by
the CPU. The alternative is to always wait the amount of time equal to the appropriate number of cycles
at the slowest possible rate the clock could be running. This sub-section will describe the hardware
handshake protocol.
The hardware handshake protocol signals to the host controller when an issued command was successfully
executed by the target. This protocol is implemented by a 16 serial clock cycle low pulse followed by a
brief speedup pulse in the BKGD pin. This pulse is generated by the target MCU when a command, issued
by the host, has been successfully executed (see Figure 4-5). This pulse is referred to as the ACK pulse.
After the ACK pulse has finished: the host can start the bit retrieval if the last issued command was a read
command, or start a new command if the last command was a write command or a control command
(BACKGROUND, GO, GO_UNTIL or TRACE1). The ACK pulse is not issued earlier than 32 serial
clock cycles after the BDM command was issued. The end of the BDM command is assumed to be the
16th tick of the last bit. This minimum delay assures enough time for the host to perceive the ACK pulse.
Note also that, there is no upper limit for the delay between the command and the related ACK pulse, since
the command execution depends upon the CPU bus frequency, which in some cases could be very slow
25
Block Guide — S12BDM V4
compared to the serial communication rate. This protocol allows a great flexibility for the POD designers,
since it does not rely on any accurate time measurement or short response time to any event in the serial
communication.
BDM CLOCK
(TARGET MCU)
16 CYCLES
TARGET
TRANSMITS
ACK PULSE
HIGH-IMPEDANCE
HIGH-IMPEDANCE
32 CYCLES
SPEEDUP PULSE
MINIMUM DELAY
FROM THE BDM COMMAND
BKGD PIN
EARLIEST
START OF
NEXT BIT
16th TICK OF THE
LAST COMMAD BIT
Figure 4-5 Target Acknowledge Pulse (ACK)
NOTE:
If the ACK pulse was issued by the target, the host assumes the previous command
was executed. If the CPU enters WAIT or STOP prior to executing a hardware
command, the ACK pulse will not be issued meaning that the BDM command was
not executed. After entering wait or stop mode, the BDM command is no longer
pending.
Figure 4-6 shows the ACK handshake protocol in a command level timing diagram. The READ_BYTE
instruction is used as an example. First, the 8-bit instruction opcode is sent by the host, followed by the
address of the memory location to be read. The target BDM decodes the instruction. A bus cycle is grabbed
(free or stolen) by the BDM and it executes the READ_BYTE operation. Having retrieved the data, the
BDM issues an ACK pulse to the host controller, indicating that the addressed byte is ready to be retrieved.
After detecting the ACK pulse, the host initiates the byte retrieval process. Note that data is sent in the
form of a word and the host needs to determine which is the appropriate byte based on whether the address
was odd or even.
TARGET
BKGD PIN
READ_BYTE
BYTE ADDRESS
HOST
HOST
(2) BYTES ARE
RETRIEVED
HOST
TARGET
BDM ISSUES THE
ACK PULSE (OUT OF SCALE)
BDM DECODES
THE COMMAND
BDM EXECUTES THE
READ_BYTE COMMAND
Figure 4-6 Handshake Protocol at Command Level
26
NEW BDM
COMMAND
TARGET
Block Guide — S12BDM V4
Differently from the normal bit transfer (where the host initiates the transmission), the serial interface
ACK handshake pulse is initiated by the target MCU by issuing a negedge in the BKGD pin. The hardware
handshake protocol in Figure 4-5 specifies the timing when the BKGD pin is being driven, so the host
should follow this timing constraint in order to avoid the risk of an electrical conflict in the BKGD pin.
NOTE:
The only place the BKGD pin can have an electrical conflict is when one side is
driving low and the other side is issuing a speedup pulse (high). Other “highs” are
pulled rather than driven. However, at low rates the time of the speedup pulse can
become lengthy and so the potential conflict time becomes longer as well.
The ACK handshake protocol does not support nested ACK pulses. If a BDM command is not
acknowledge by an ACK pulse, the host needs to abort the pending command first in order to be able to
issue a new BDM command. When the CPU enters WAIT or STOP while the host issues a command that
requires CPU execution (e.g., WRITE_BYTE), the target discards the incoming command due to the
WAIT or STOP being detected. Therefore, the command is not acknowledged by the target, which means
that the ACK pulse will not be issued in this case. After a certain time the host should decide to abort the
ACK sequence in order to be free to issue a new command. Therefore, the protocol should provide a
mechanism in which a command, and therefore a pending ACK, could be aborted.
NOTE:
Differently from a regular BDM command, the ACK pulse does not provide a time
out. This means that in the case of a WAIT or STOP instruction being executed, the
ACK would be prevented from being issued. If not aborted, the ACK would remain
pending indefinitely. See the handshake abort procedure described in
4.8 Hardware Handshake Abort Procedure.
4.8 Hardware Handshake Abort Procedure
The abort procedure is based on the SYNC command. In order to abort a command, which had not issued
the corresponding ACK pulse, the host controller should generate a low pulse in the BKGD pin by driving
it low for at least 128 serial clock cycles and then driving it high for one serial clock cycle, providing a
speedup pulse. By detecting this long low pulse in the BKGD pin, the target executes the SYNC protocol,
see 4.9 SYNC — Request Timed Reference Pulse, and assumes that the pending command and
therefore the related ACK pulse, are being aborted. Therefore, after the SYNC protocol has been
completed the host is free to issue new BDM commands.
Although it is not recommended, the host could abort a pending BDM command by issuing a low pulse in
the BKGD pin shorter than 128 serial clock cycles, which will not be interpreted as the SYNC command.
The ACK is actually aborted when a negedge is perceived by the target in the BKGD pin. The short abort
pulse should have at least 4 clock cycles keeping the BKGD pin low, in order to allow the negedge to be
detected by the target. In this case, the target will not execute the SYNC protocol but the pending command
will be aborted along with the ACK pulse. The potential problem with this abort procedure is when there
is a conflict between the ACK pulse and the short abort pulse. In this case, the target may not perceive the
abort pulse. The worst case is when the pending command is a read command (i.e., READ_BYTE). If the
abort pulse is not perceived by the target the host will attempt to send a new command after the abort pulse
was issued, while the target expects the host to retrieve the accessed memory byte. In this case, host and
target will run out of synchronism. However, if the command to be aborted is not a read command the short
27
Block Guide — S12BDM V4
abort pulse could be used. After a command is aborted the target assumes the next negedge, after the abort
pulse, is the first bit of a new BDM command.
NOTE:
The details about the short abort pulse are being provided only as a reference for
the reader to better understand the BDM internal behavior. It is not recommended
that this procedure be used in a real application.
Since the host knows the target serial clock frequency, the SYNC command (used to abort a command)
does not need to consider the lower possible target frequency. In this case, the host could issue a SYNC
very close to the 128 serial clock cycles length. Providing a small overhead on the pulse length in order to
assure the SYNC pulse will not be misinterpreted by the target. See 4.9 SYNC — Request Timed
Reference Pulse.
Figure 4-7 shows a SYNC command being issued after a READ_BYTE, which aborts the READ_BYTE
command. Note that, after the command is aborted a new command could be issued by the host computer.
BKGD PIN
READ_BYTE CMD IS ABORTED
BY THE SYNC REQUEST
(OUT OF SCALE)
SYNC RESPONSE
FROM THE TARGET
(OUT OF SCALE)
MEMORY ADDRESS
READ_STATUS
READ_BYTE
HOST
TARGET
BDM DECODE
AND STARTS TO EXECUTES
THE READ_BYTE CMD
HOST
TARGET
NEW BDM COMMAND
HOST
TARGET
NEW BDM COMMAND
Figure 4-7 ACK Abort Procedure at the Command Level
NOTE:
Figure 4-7 does not represent the signals in a true timing scale
Figure 4-8 shows a conflict between the ACK pulse and the SYNC request pulse. This conflict could
occur if a POD device is connected to the target BKGD pin and the target is already in debug active mode.
Consider that the target CPU is executing a pending BDM command at the exact moment the POD is being
connected to the BKGD pin. In this case, an ACK pulse is issued along with the SYNC command. In this
case, there is an electrical conflict between the ACK speedup pulse and the SYNC pulse. Since this is not
a probable situation, the protocol does not prevent this conflict from happening.
28
Block Guide — S12BDM V4
AT LEAST 128 CYCLES
BDM CLOCK
(TARGET MCU)
ACK PULSE
TARGET MCU
DRIVES TO
BKGD PIN
HIGH-IMPEDANCE
ELECTRICAL CONFLICT
HOST
DRIVES SYNC
TO BKGD PIN
HOST AND
TARGET DRIVE
TO BKGD PIN
SPEEDUP PULSE
HOST SYNC REQUEST PULSE
BKGD PIN
16 CYCLES
Figure 4-8 ACK Pulse and SYNC Request Conflict
NOTE:
This information is being provided so that the MCU integrator will be aware that
such a conflict could eventually occur.
The hardware handshake protocol is enabled by the ACK_ENABLE and disabled by the ACK_DISABLE
BDM commands. This provides backwards compatibility with the existing POD devices which are not
able to execute the hardware handshake protocol. It also allows for new POD devices, that support the
hardware handshake protocol, to freely communicate with the target device. If desired, without the need
for waiting for the ACK pulse.
The commands are described as follows:
•
ACK_ENABLE — enables the hardware handshake protocol. The target will issue the ACK pulse
when a CPU command is executed by the CPU. The ACK_ENABLE command itself also has the
ACK pulse as a response.
•
ACK_DISABLE — disables the ACK pulse protocol. In this case, the host needs to use the worst
case delay time at the appropriate places in the protocol.
The default state of the BDM after reset is hardware handshake protocol disabled.
All the read commands will ACK (if enabled) when the data bus cycle has completed and the data is then
ready for reading out by the BKGD serial pin. All the write commands will ACK (if enabled) after the data
has been received by the BDM through the BKGD serial pin and when the data bus cycle is complete. See
4.3 BDM Hardware Commands and 4.4 Standard BDM Firmware Commands for more
information on the BDM commands.
29
Block Guide — S12BDM V4
The ACK_ENABLE sends an ACK pulse when the command has been completed. This feature could be
used by the host to evaluate if the target supports the hardware handshake protocol. If an ACK pulse is
issued in response to this command, the host knows that the target supports the hardware handshake
protocol. If the target does not support the hardware handshake protocol the ACK pulse is not issued. In
this case, the ACK_ENABLE command is ignored by the target since it is not recognized as a valid
command.
The BACKGROUND command will issue an ACK pulse when the CPU changes from normal to
background mode. The ACK pulse related to this command could be aborted using the SYNC command.
The GO command will issue an ACK pulse when the CPU exits from background mode. The ACK pulse
related to this command could be aborted using the SYNC command.
The GO_UNTIL command is equivalent to a GO command with exception that the ACK pulse, in this
case, is issued when the CPU enters into background mode. This command is an alternative to the GO
command and should be used when the host wants to trace if a breakpoint match occurs and causes the
CPU to enter active background mode. Note that the ACK is issued whenever the CPU enters BDM, which
could be caused by a Breakpoint match or by a BGND instruction being executed. The ACK pulse related
to this command could be aborted using the SYNC command.
The TRACE1 command has the related ACK pulse issued when the CPU enters background active mode
after one instruction of the application program is executed. The ACK pulse related to this command could
be aborted using the SYNC command.
The TAGGO command will not issue an ACK pulse since this would interfere with the tagging function
shared on the same pin.
4.9 SYNC — Request Timed Reference Pulse
The SYNC command is unlike other BDM commands because the host does not necessarily know the
correct communication speed to use for BDM communications until after it has analyzed the response to
the SYNC command. To issue a SYNC command, the host should perform the following steps:
1. Drive the BKGD pin low for at least 128 cycles at the lowest possible BDM serial communication
frequency (the lowest serial communication frequency is determined by the crystal oscillator or the
clock chosen by CLKSW.)
2. Drive BKGD high for a brief speedup pulse to get a fast rise time (this speedup pulse is typically
one cycle of the host clock.)
3. Remove all drive to the BKGD pin so it reverts to high impedance.
4. Listen to the BKGD pin for the sync response pulse.
30
Block Guide — S12BDM V4
Upon detecting the SYNC request from the host, the target performs the following steps:
1. Discards any incomplete command received or bit retrieved.
2. Waits for BKGD to return to a logic one.
3. Delays 16 cycles to allow the host to stop driving the high speedup pulse.
4. Drives BKGD low for 128 cycles at the current BDM serial communication frequency.
5. Drives a one-cycle high speedup pulse to force a fast rise time on BKGD.
6. Removes all drive to the BKGD pin so it reverts to high impedance.
The host measures the low time of this 128 cycle SYNC response pulse and determines the correct speed
for subsequent BDM communications. Typically, the host can determine the correct communication speed
within a few percent of the actual target speed and the communication protocol can easily tolerate speed
errors of several percent.
As soon as the SYNC request is detected by the target, any partially received command or bit retrieved is
discarded. This is referred to as a soft-reset, equivalent to a time-out in the serial communication. After the
SYNC response, the target will consider the next negedge (issued by the host) as the start of a new BDM
command or the start of new SYNC request.
Another use of the SYNC command pulse is to abort a pending ACK pulse. The behavior is exactly the
same as in a regular SYNC command. Note that one of the possible causes for a command to not be
acknowledged by the target is a host-target synchronization problem. In this case, the command may not
have been understood by the target and so an ACK response pulse will not be issued.
4.10 Instruction Tracing
When a TRACE1 command is issued to the BDM in active BDM, the CPU exits the standard BDM
firmware and executes a single instruction in the user code. Once this has occurred, the CPU is forced to
return to the standard BDM firmware and the BDM is active and ready to receive a new command. If the
TRACE1 command is issued again, the next user instruction will be executed. This facilitates stepping or
tracing through the user code one instruction at a time.
If an interrupt is pending when a TRACE1 command is issued, the interrupt stacking operation occurs but
no user instruction is executed. Once back in standard BDM firmware execution, the program counter
points to the first instruction in the interrupt service routine.
31
Block Guide — S12BDM V4
4.11 Instruction Tagging
The instruction queue and cycle-by-cycle CPU activity are reconstructible in real time or from trace
history that is captured by a logic analyzer. However, the reconstructed queue cannot be used to stop the
CPU at a specific instruction. This is because execution already has begun by the time an operation is
visible outside the system. A separate instruction tagging mechanism is provided for this purpose.
The tag follows program information as it advances through the instruction queue. When a tagged
instruction reaches the head of the queue, the CPU enters active BDM rather than executing the instruction.
NOTE:
Tagging is disabled when BDM becomes active and BDM serial commands are not
processed while tagging is active.
Executing the BDM TAGGO command configures two system pins for tagging. The TAGLO signal
shares a pin with the LSTRB signal, and the TAGHI signal shares a pin with the BKGD signal.
Table 4-3 shows the functions of the two tagging pins. The pins operate independently, that is the state
of one pin does not affect the function of the other. The presence of logic level 0 on either pin at the fall
of the external clock (ECLK) performs the indicated function. High tagging is allowed in all modes. Low
tagging is allowed only when low strobe is enabled (LSTRB is allowed only in wide expanded modes and
emulation expanded narrow mode).
Table 4-3 Tag Pin Function
TAGHI
TAGLO
Tag
1
1
No tag
1
0
Low byte
0
1
High byte
0
0
Both bytes
4.12 Serial Communication Time-out
The host initiates a host-to-target serial transmission by generating a falling edge on the BKGD pin. If
BKGD is kept low for more than 128 target clock cycles, the target understands that a SYNC command
was issued. In this case, the target will keep waiting for a rising edge on BKGD in order to answer the
SYNC request pulse. If the rising edge is not detected, the target will keep waiting forever without any
time-out limit.
Consider now the case where the host returns BKGD to logic one before 128 cycles. This is interpreted as
a valid bit transmission, and not as a SYNC request. The target will keep waiting for another falling edge
marking the start of a new bit. If, however, a new falling edge is not detected by the target within 512 clock
cycles since the last falling edge, a time-out occurs and the current command is discarded without affecting
memory or the operating mode of the MCU. This is referred to as a soft-reset.
32
Block Guide — S12BDM V4
If a read command is issued but the data is not retrieved within 512 serial clock cycles, a soft-reset will
occur causing the command to be disregarded. The data is not available for retrieval after the time-out has
occurred. This is the expected behavior if the handshake protocol is not enabled. However, consider the
behavior where the BDC is running in a frequency much greater than the CPU frequency. In this case, the
command could time out before the data is ready to be retrieved. In order to allow the data to be retrieved
even with a large clock frequency mismatch (between BDC and CPU) when the hardware handshake
protocol is enabled, the time out between a read command and the data retrieval is disabled. Therefore, the
host could wait for more then 512 serial clock cycles and still be able to retrieve the data from an issued
read command. However, once the handshake pulse (ACK pulse) is issued, the time-out feature is
re-activated, meaning that the target will time out after 512 clock cycles. Therefore, the host needs to
retrieve the data within a 512 serial clock cycles time frame after the ACK pulse had been issued. After
that period, the read command is discarded and the data is no longer available for retrieval. Any negedge
in the BKGD pin after the time-out period is considered to be a new command or a SYNC request.
Note that whenever a partially issued command, or partially retrieved data, has occurred the time out in
the serial communication is active. This means that if a time frame higher than 512 serial clock cycles is
observed between two consecutive negative edges and the command being issued or data being retrieved
is not complete, a soft-reset will occur causing the partially received command or data retrieved to be
disregarded. The next negedge in the BKGD pin, after a soft-reset has occurred, is considered by the target
as the start of a new BDC command, or the start of a SYNC request pulse.
33
Block Guide — S12BDM V4
S12BDMV4/D
Rev. 4.02
34
Block Guide — S12BDM V4
2/2003
35
HOW TO REACH US:
USA/EUROPE/LOCATIONS NOT LISTED:
Motorola Literature Distribution;
P.O. Box 5405, Denver, Colorado 80217
1-303-675-2140 or 1-800-441-2447
JAPAN:
Motorola Japan Ltd.; SPS, Technical Information Center,
3-20-1, Minami-Azabu Minato-ku, Tokyo 106-8573 Japan
81-3-3440-3569
ASIA/PACIFIC:
Motorola Semiconductors H.K. Ltd.;
Silicon Harbour Centre, 2 Dai King Street,
Tai Po Industrial Estate, Tai Po, N.T., Hong Kong
852-26668334
TECHNICAL INFORMATION CENTER:
1-800-521-6274
Information in this document is provided solely to enable system and software
implementers to use Motorola products. There are no express or implied copyright
licenses granted hereunder to design or fabricate any integrated circuits or
integrated circuits based on the information in this document.
Motorola reserves the right to make changes without further notice to any products
herein. Motorola makes no warranty, representation or guarantee regarding the
HOME PAGE:
suitability of its products for any particular purpose, nor does Motorola assume any
http://motorola.com/semiconductors
liability arising out of the application or use of any product or circuit, and specifically
disclaims any and all liability, including without limitation consequential or incidental
damages. “Typical” parameters which may be provided in Motorola data sheets
and/or specifications can and do vary in different applications and actual
performance may vary over time. All operating parameters, including “Typicals”
must be validated for each customer application by customer’s technical experts.
Motorola does not convey any license under its patent rights nor the rights of
others. Motorola products are not designed, intended, or authorized for use as
components in systems intended for surgical implant into the body, or other
applications intended to support or sustain life, or for any other application in which
the failure of the Motorola product could create a situation where personal injury or
death may occur. Should Buyer purchase or use Motorola products for any such
unintended or unauthorized application, Buyer shall indemnify and hold Motorola
and its officers, employees, subsidiaries, affiliates, and distributors harmless
against all claims, costs, damages, and expenses, and reasonable attorney fees
arising out of, directly or indirectly, any claim of personal injury or death associated
with such unintended or unauthorized use, even if such claim alleges that Motorola
was negligent regarding the design or manufacture of the part.
Motorola and the Stylized M Logo are registered in the U.S. Patent and Trademark
Office. digital dna is a trademark of Motorola, Inc. All other product or service
names are the property of their respective owners. Motorola, Inc. is an Equal
Opportunity/Affirmative Action Employer.
© Motorola, Inc. 2003
Block Guide — S12BDM V4
37
Block Guide — S12BDM V4
38
Block Guide — S12BDM V4
39
Block Guide — S12BDM V4
40
Block Guide — S12BDM V4
41
Block Guide — S12BDM V4
42
Block Guide — S12BDM V4
43
Block Guide — S12BDM V4
44
Block Guide — S12BDM V4
45
Block Guide — S12BDM V4
46
Block Guide — S12BDM V4
47
Block Guide — S12BDM V4
48
Block Guide — S12BDM V4
49
Block Guide — S12BDM V4
50
Block Guide — S12BDM V4
51
Block Guide — S12BDM V4
52
Block Guide — S12BDM V4
53
Block Guide — S12BDM V4
54
Block Guide — S12BDM V4
55
Block Guide — S12BDM V4
56
Block User Guide
HCS12
Microcontrollers
S12BKPV1/D
Rev. 1.02
5/2003
MOTOROLA.COM/SEMICONDUCTORS
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Breakpoint (BKP)
Module V1
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Block Guide — S12BKP V1
Revision History
Version
Number
Revision
Date
Effective
Date
Author
1.02
5/1/2003
5/1/2003
John Langan
Description of Changes
Original release
Motorola and the Stylized M Logo are registered trademarks of Motorola, Inc.
DigitalDNA is a trademark of Motorola, Inc.
This product incorporates SuperFlash® technology licensed from SST.
2
© Motorola, Inc., 2003
Table of Contents
Block Guide — S12BKP V1
3
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Block Guide — S12BKP V1
List of Figures
Figure 1-1
Figure 3-1
Figure 3-2
Figure 3-3
Figure 3-4
Figure 3-5
Figure 3-6
Figure 3-7
Figure 3-8
Figure 3-9
Breakpoint Block Diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
Breakpoint Register Summary. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Breakpoint Control Register 0 (BKPCT0) . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Breakpoint Control Register 1 (BKPCT1) . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
Breakpoint First Address Expansion Register (BKP0X) . . . . . . . . . . . . . . . . 15
Breakpoint First Address High Byte Register (BKP0H) . . . . . . . . . . . . . . . . . 16
Breakpoint First Address Low Byte Register (BKP0L). . . . . . . . . . . . . . . . . . 16
Breakpoint Second Address Expansion Register (BKP1X) . . . . . . . . . . . . . . 17
Breakpoint Data High Byte Register (BKP1H). . . . . . . . . . . . . . . . . . . . . . . . 17
Breakpoint Data Low Byte Register (BKP1L) . . . . . . . . . . . . . . . . . . . . . . . . 18
List of Tables
Table 2-1
Table 3-1
Table 3-2
Table 3-3
External System Pins Associated With Breakpoint and MEBI. . . . . . . . . . . . . 9
Breakpoint Mask Bits for First Address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
Breakpoint Mask Bits for Second Address (Dual Mode) . . . . . . . . . . . . . . . . 14
Breakpoint Mask Bits for Data Breakpoints (Full Mode) . . . . . . . . . . . . . . . . 14
Section 1 Introduction: Breakpoint (BKP) Module
1.1
1.2
1.3
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
Modes of Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
Section 2 External Signal Description
Section 3 Memory Map/Register Definition
3.1
3.2
3.3
3.4
3.5
3.6
3.7
3.8
4
Breakpoint Control Register 0 (BKPCT0) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Breakpoint Control Register 1 (BKPCT1) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Breakpoint First Address Expansion Register (BKP0X) . . . . . . . . . . . . . . . . . . . . . . 11
Breakpoint First Address High Byte Register (BKP0H) . . . . . . . . . . . . . . . . . . . . . . 12
Breakpoint First Address Low Byte Register (BKP0L) . . . . . . . . . . . . . . . . . . . . . . . 12
Breakpoint Second Address Expansion Register (BKP1X) . . . . . . . . . . . . . . . . . . . 13
Breakpoint Data (Second Address) High Byte Register (BKP1H) . . . . . . . . . . . . . . 13
Breakpoint Data (Second Address) Low Byte Register (BKP1L) . . . . . . . . . . . . . . . 14
Block Guide — S12BKP V1
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Section 4 Functional Description
4.1
Modes of Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
4.1.1
Dual Address Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
4.1.2
Full Breakpoint Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
4.2
Breakpoint Priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
5
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Block Guide — S12BKP V1
6
Section 1 Introduction: Breakpoint (BKP) Module
This section describes the functionality of the Breakpoint (BKP) sub-block of the HCS12 Core Platform.
A block diagram of the Breakpoint sub-block is shown in Figure 1-1. The Breakpoint contains three main
sub-blocks: the Register Block, the Compare Block, and the Control Block. The Register Block consists
of the eight registers that make up the Breakpoint register space. The Compare Block performs all required
address and data signal comparisons. The Control Block generates the signals for the CPU for the tag high,
tag low, force SWI, and force BDM functions. In addition, it generates the register read and write signals
and the comparator block enable signals.
NOTE:
There is a two-cycle latency for address compares and for forces, a two-cycle
latency for write data compares, and a three-cycle latency for read data compares.
1.1 Overview
The Breakpoint sub-block of the Core Platform provides for hardware breakpoints that are used to debug
software on the CPU by comparing actual address and data values to predetermine data in setup registers.
A successful comparison will place the CPU in Background Debug Mode or initiate a software interrupt
(SWI). The choice between Background Debug Mode and SWI is software selectable.
There are two types of breakpoints, forced and tagged. Forced breakpoints occur at the next instruction
boundary if a match occurs and tagged breakpoints allow for breaking just before a specific instruction
executes. Tagged breakpoints will only occur on addresses of program fetches. Tagging on data is not
allowed; however, if this occurs nothing will happen within the BKP.
The range function of the BKP allows breaking within a 256-byte address range. The page function allows
breaking within expanded memory. In data matching operations, 8-bit or 16-bit data can be matched.
Forced breakpoints are mainly used on a read or a write cycle, but can be used on any bus cycle.
1
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Block Guide — S12BKP V1
Block Guide — S12BKP V1
BKP CONTROL
SIGNALS
CONTROL BLOCK
BREAKPOINT MODES
AND GENERATION OF SWI,
FORCE BDM, AND TAGS
CONTROL SIGNALS
CONTROL BITS
READ/WRITE
CONTROL
......
......
RESULTS SIGNALS
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
CLOCKS AND
CONTROL SIGNALS
EXPANSION ADDRESS
ADDRESS
WRITE DATA
READ DATA
REGISTER BLOCK
BKPCT0
BKPCT1
COMPARE BLOCK
BKP READ
DATA BUS
WRITE
DATA BUS
BKP0X
COMPARATOR
BKP0H
COMPARATOR
BKP0L
COMPARATOR
BKP1X
COMPARATOR
EXPANSION ADDRESSES
ADDRESS HIGH
ADDRESS LOW
EXPANSION ADDRESSES
DATA HIGH
BKP1H
BKP1L
COMPARATOR
DATA/ADDRESS
HIGH MUX
COMPARATOR
DATA/ADDRESS
LOW MUX
READ DATA HIGH
COMPARATOR
READ DATA LOW
COMPARATOR
Figure 1-1 Breakpoint Block Diagram
2
ADDRESS HIGH
DATA LOW
ADDRESS LOW
Block Guide — S12BKP V1
•
•
•
•
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
1.2 Features
Full or Dual Breakpoint Mode
–
Compare on address and data (Full)
–
Compare on either of two addresses (Dual)
BDM or SWI Breakpoint
–
Enter BDM on breakpoint (BDM)
–
Execute SWI on breakpoint (SWI)
Tagged or Forced Breakpoint
–
Break just before a specific instruction will begin execution (TAG)
–
Break on the first instruction boundary after a match occurs (Force)
Single, Range, or Page address compares
–
Compare on address (Single)
–
Compare on address 256 byte (Range)
–
Compare on any 16K Page (Page)
•
Compare address on read or write on forced breakpoints
•
High and/or low byte data compares
1.3 Modes of Operation
The Breakpoint sub-block contains two modes of operation:
1. Dual Address Mode, where a match on either of two addresses will cause the system to enter
Background Debug Mode or initiate a Software Interrupt (SWI).
2. Full Breakpoint Mode, where a match on address and data will cause the system to enter
Background Debug Mode or initiate a Software Interrupt (SWI).
3
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Block Guide — S12BKP V1
4
Section 2 External Signal Description
The breakpoint sub-module relies on the external bus interface (generally the MEBI) when the breakpoint
is matching on the external bus.
The tag pins in Table 2-1 (part of the MEBI) may also be a part of the breakpoint operation.
Table 2-1 External System Pins Associated With Breakpoint and MEBI
Pin Name
Pin Functions
Description
BKGD/MODC/
TAGHI
TAGHI
When instruction tagging is on, a 0 at the falling edge of PE4/ECLK tags the high
half of the instruction word being read into the instruction queue.
PE3/LSTRB/
TAGLO
TAGLO
In expanded wide mode or emulation narrow modes, when instruction tagging is
on and low strobe is enabled, a 0 at the falling edge of PE4/ECLK tags the low
half of the instruction word being read into the instruction queue.
5
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Block Guide — S12BKP V1
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Block Guide — S12BKP V1
6
Block Guide — S12BKP V1
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Section 3 Memory Map/Register Definition
A summary of the registers associated with the Breakpoint sub-block is shown in Figure 3-1. Detailed
descriptions of the registers and bits are given in the subsections that follow.
Address
Name
$0028
BKPCT0
$0029
BKPCT1
$002A
BKP0X
$002B
BKP0H
$002C
BKP0L
$002D
BKP1X
$002E
BKP1H
$002F
BKP1L
Read
Write
Read
Write
Read
Bit 7
6
5
4
3
2
1
Bit 0
BKEN
BKFULL
BKBDM
BKTAG
0
0
0
0
BK0MBH
BK0MBL
BK1MBH
BK1MBL
BK0RWE
BK0RW
BK1RWE
BK1RW
0
0
BK0V5
BK0V4
BK0V3
BK0V2
BK0V1
BK0V0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
0
0
BK1V5
BK1V4
BK1V3
BK1V2
BK1V1
BK1V0
Bit 15
14
13
12
11
10
9
Bit 8
Bit 7
6
5
4
3
2
1
Bit 0
Write
Read
Write
Read
Write
Read
Write
Read
Write
Read
Write
= Unimplemented
X = Indeterminate
Figure 3-1 Breakpoint Register Summary
7
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Block Guide — S12BKP V1
3.1 Breakpoint Control Register 0 (BKPCT0)
Read: anytime
Write: anytime
Register address $0028
R
W
Reset:
7
6
5
4
BKEN
BKFULL
BKBDM
BKTAG
0
0
0
0
3
0
2
0
1
0
0
0
0
0
0
0
= Unimplemented or Reserved
Figure 3-2 Breakpoint Control Register 0 (BKPCT0)
This register is used to set the breakpoint modes.
BKEN — Breakpoint Enable
This bit enables the module
0 = Breakpoints disabled
1 = Breakpoints enabled, breakpoint mode is determined by bits BKFULL, BKBDM, and BKTAG
BKFULL — Full Breakpoint Mode Enable
This bit controls whether the breakpoint module is in Dual Mode or Full Mode
0 = Dual Address Mode enabled
1 = Full Breakpoint Mode enabled
BKBDM — Breakpoint Background Debug Mode Enable
This bit determines if the breakpoint causes the system to enter Background Debug Mode (BDM) or
initiate a Software Interrupt (SWI)
0 = Go to Software Interrupt on a compare
1 = Go to BDM on a compare
BKTAG — Breakpoint on Tag
This bit controls whether the breakpoint will cause a break on the next instruction boundary (force) or
on a match that will be an executable opcode (tagged). Non-executed opcodes cannot cause a tagged
breakpoint
0 = On match, break at the next instruction boundary (force)
1 = On match, break if the match is an instruction that will be executed (tagged)
8
3.2 Breakpoint Control Register 1 (BKPCT1)
Read: anytime
Write: anytime
Register address $0029
R
W
Reset:
7
6
5
4
3
2
1
0
BK0MBH
BK0MBL
BK1MBH
BK1MBL
BK0RWE
BK0RW
BK1RWE
BK1RW
0
0
0
0
0
0
0
0
Figure 3-3 Breakpoint Control Register 1 (BKPCT1)
This register is used to configure the functionality of the Breakpoint sub-block within the Core.
BK0MBH:BK0MBL — Breakpoint Mask High Byte and Low Byte for First Address
In Dual or Full Mode, these bits may be used to mask (disable) the comparison of the high and low
bytes of the first address breakpoint. The functionality is as given in Table 3-1 below
Table 3-1 Breakpoint Mask Bits for First Address
BK0MBH:BK0MBL
Address Compare
BKP0X
BKP0H
BKP0L
x:0
Full address compare
Yes(1)
Yes
Yes
0:1
256 byte address range
Yes(1)
Yes
No
1:1
16K byte address range
Yes(1)
No
No
NOTES:
1. If page is selected.
The x:0 case is for a Full Address Compare. When a program page is selected, the full address compare
will be based on bits for a 20-bit compare. The registers used for the compare are {BKP0X[5:0],
BKP0H[5:0], BKP0L[7:0]}. When a program page is not selected, the full address compare will be based
on bits for a 16-bit compare. The registers used for the compare are {BKP0H[7:0], BKP0L[7:0]}.
The 1:0 case is not sensible because it would ignore the high order address and compare the low order and
expansion addresses. Logic forces this case to compare all address lines (effectively ignoring the
BK0MBH control bit).
The 1:1 case is useful for triggering a breakpoint on any access to a particular expansion page. This only
makes sense if a program page is being accessed so that the breakpoint trigger will occur only if BKP0X
compares.
9
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Block Guide — S12BKP V1
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Block Guide — S12BKP V1
BK1MBH:BK1MBL — Breakpoint Mask High Byte and Low Byte of Data (Second Address)
In Dual Mode, these bits may be used to mask (disable) the comparison of the high and/or low bytes
of the second address breakpoint. The functionality is as given in Table 3-2.
Table 3-2 Breakpoint Mask Bits for Second Address (Dual Mode)
BK1MBH:BK1MBL
Address Compare
BKP1X
BKP1H
BKP1L
x:0
Full address compare
Yes(1)
Yes
Yes
0:1
256 byte address range
Yes(1)
Yes
No
1:1
16K byte address range
Yes(1)
No
No
NOTES:
1. If page is selected.
The x:0 case is for a Full Address Compare. When a program page is selected, the full address compare
will be based on bits for a 20-bit compare. The registers used for the compare are {BKP1X[5:0],
BKP1H[5:0], BKP1L[7:0]}. When a program page is not selected, the full address compare will be based
on bits for a 16-bit compare. The registers used for the compare are {BKP1H[7:0], BKP1L[7:0]}.
The 1:0 case is not sensible because it would ignore the high order address and compare the low order and
expansion addresses. Logic forces this case to compare all address lines (effectively ignoring the
BK1MBH control bit).
The 1:1 case is useful for triggering a breakpoint on any access to a particular expansion page. This only
makes sense if a program page is being accessed so that the breakpoint trigger will occur only if BKP1X
compares.
In Full Mode, these bits may be used to mask (disable) the comparison of the high and/or low bytes of the
data breakpoint. The functionality is as given in Table 3-3.
Table 3-3 Breakpoint Mask Bits for Data Breakpoints (Full Mode)
BK1MBH:BK1MBL
Data Compare
BKP1X
BKP1H
BKP1L
0:0
High and low byte compare
No(1)
Yes
Yes
0:1
High byte
No(1)
Yes
No
1:0
Low byte
No(1)
No
Yes
1:1
No compare
No(1)
No
No
NOTES:
1. Expansion addresses for breakpoint 1 are not available in this mode.
10
BK0RWE — R/W Compare Enable
Enables the comparison of the R/W signal for first address breakpoint. This bit is not useful in tagged
breakpoints.
0 = R/W is not used in the comparisons
1 = R/W is used in comparisons
BK0RW — R/W Compare Value
When BK0RWE = 1, this bit determines the type of bus cycle to match on first address breakpoint.
When BK0RWE = 0, this bit has no effect.
0 = Write cycle will be matched
1 = Read cycle will be matched
BK1RWE — R/W Compare Enable
In Dual Mode, this bit enables the comparison of the R/W signal to further specify what causes a match
for the second address breakpoint. This bit is not useful on tagged breakpoints or in Full Mode and is
therefore a don’t care.
0 = R/W is not used in comparisons
1 = R/W is used in comparisons
BK1RW — R/W Compare Value
When BK1RWE = 1, this bit determines the type of bus cycle to match on the second address
breakpoint.When BK1RWE = 0, this bit has no effect.
0 = Write cycle will be matched
1 = Read cycle will be matched
3.3 Breakpoint First Address Expansion Register (BKP0X)
Read: anytime
Write: anytime
Register address $002A
R
W
Reset:
7
0
6
0
0
0
5
4
3
2
1
0
BK0V5
BK0V4
BK0V3
BK0V2
BK0V1
BK0V0
0
0
0
0
0
0
= Unimplemented or Reserved
Figure 3-4 Breakpoint First Address Expansion Register (BKP0X)
This register contains the data to be matched against expansion address lines for the first address
breakpoint when a page is selected.
BK0V[5:0] — Value of first breakpoint address to be matched in memory expansion space.
11
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Block Guide — S12BKP V1
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Block Guide — S12BKP V1
3.4 Breakpoint First Address High Byte Register (BKP0H)
Read: anytime
Write: anytime
Register address $002B
R
W
Reset:
7
6
5
4
3
2
1
0
Bit 15
14
13
12
11
10
9
Bit 8
0
0
0
0
0
0
0
0
Figure 3-5 Breakpoint First Address High Byte Register (BKP0H)
This register is used to set the breakpoint when compared against the high byte of the address.
3.5 Breakpoint First Address Low Byte Register (BKP0L)
Read: anytime
Write: anytime
Register address $002C
R
W
Reset:
7
6
5
4
3
2
1
0
Bit 7
6
5
4
3
2
1
Bit 0
0
0
0
0
0
0
0
0
Figure 3-6 Breakpoint First Address Low Byte Register (BKP0L)
This register is used to set the breakpoint when compared against the low byte of the address.
12
3.6 Breakpoint Second Address Expansion Register (BKP1X)
Read: anytime
Write: anytime
Register address $002D
R
W
Reset:
7
0
6
0
0
0
5
4
3
2
1
0
BK1V5
BK1V4
BK1V3
BK1V2
BK1V1
BK1V0
0
0
0
0
0
0
= Unimplemented or Reserved
Figure 3-7 Breakpoint Second Address Expansion Register (BKP1X)
In Dual Mode, this register contains the data to be matched against expansion address lines for the second
address breakpoint when a page is selected. In Full Mode, this register is not used.
BK1V[5:0] — Value of first breakpoint address to be matched in memory expansion space.
3.7 Breakpoint Data (Second Address) High Byte Register (BKP1H)
Read: anytime
Write: anytime
Register address $002E
R
W
Reset:
7
6
5
4
3
2
1
0
Bit 15
14
13
12
11
10
9
Bit 8
0
0
0
0
0
0
0
0
Figure 3-8 Breakpoint Data High Byte Register (BKP1H)
In Dual Mode, this register is used to compare against the high order address lines. In Full Mode, this
register is used to compare against the high order data lines.
13
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Block Guide — S12BKP V1
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Block Guide — S12BKP V1
3.8 Breakpoint Data (Second Address) Low Byte Register (BKP1L)
Read: anytime
Write: anytime
Register address $002F
R
W
Reset:
7
6
5
4
3
2
1
0
Bit 7
6
5
4
3
2
1
Bit 0
0
0
0
0
0
0
0
0
Figure 3-9 Breakpoint Data Low Byte Register (BKP1L)
In Dual Mode, this register is used to compare against the low order address lines. In Full Mode, this
register is used to compare against the low order data lines.
14
Section 4 Functional Description
The Breakpoint sub-block supports two modes of operation: Dual Address Mode and Full Breakpoint
Mode. Within each of these modes, forced or tagged breakpoint types can be used. Forced breakpoints
occur at the next instruction boundary if a match occurs and tagged breakpoints allow for breaking just
before a specific instruction executes. The action taken upon a successful match can be to either place the
CPU in Background Debug Mode or to initiate a software interrupt.
4.1 Modes of Operation
The Breakpoint can operate in Dual Address Mode or Full Breakpoint Mode. Each of these modes is
discussed in the subsections below.
4.1.1 Dual Address Mode
When Dual Address Mode is enabled, two address breakpoints can be set. Each breakpoint can cause the
system to enter Background Debug Mode or to initiate a software interrupt based upon the state of the
BKBDM bit in the BKPCT0 Register being logic one or logic zero, respectively. BDM requests have a
higher priority than SWI requests. No data breakpoints are allowed in this mode.
The BKTAG bit in the BKPCT0 register selects whether the breakpoint mode is forced or tagged. The
BKxMBH:L bits in the BKPCT1 register select whether or not the breakpoint is matched exactly or is a
range breakpoint. They also select whether the address is matched on the high byte, low byte, both bytes,
and/or memory expansion. The BKxRW and BKxRWE bits in the BKPCT1 register select whether the
type of bus cycle to match is a read, write, or both when performing forced breakpoints.
4.1.2 Full Breakpoint Mode
Full Breakpoint Mode requires a match on address and data for a breakpoint to occur. Upon a successful
match, the system will enter Background Debug Mode or initiate a software interrupt based upon the state
of the BKBDM bit in the BKPCT0 Register being logic one or logic zero, respectively. BDM requests
have a higher priority than SWI requests. R/W matches are also allowed in this mode.
The BKTAG bit in the BKPCT0 register selects whether the breakpoint mode is forced or tagged. If the
BKTAG bit is set in BKPCT0, then only address is matched, and data is ignored. The BK0MBH:L bits in
the BKPCT1 register select whether or not the breakpoint is matched exactly, is a range breakpoint, or is
in page space. The BK1MBH:L bits in the BKPCT1 register select whether the data is matched on the high
byte, low byte, or both bytes. The BK0RW and BK0RWE bits in the BKPCT1 register select whether the
type of bus cycle to match is a read or a write when performing forced breakpoints. BK1RW and
BK1RWE bits in the BKPCT1 register are not used in Full Breakpoint Mode.
15
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Block Guide — S12BKP V1
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
Block Guide — S12BKP V1
4.2 Breakpoint Priority
Breakpoint operation is first determined by the state of BDM. If BDM is already active, meaning the CPU
is executing out of BDM firmware, Breakpoints are not allowed. In addition, while in BDM trace mode,
tagging into BDM is not allowed. If BDM is not active, the Breakpoint will give priority to BDM requests
over SWI requests. This condition applies to both forced and tagged breakpoints.
In all cases, BDM related breakpoints will have priority over those generated by the Breakpoint sub-block.
This priority includes breakpoints enabled by the TAGLO and TAGHI external pins of the system that
interface with the BDM directly and whose signal information passes through and is used by the
Breakpoint sub-block.
NOTE:
BDM should not be entered from a breakpoint unless the BKEN bit is set in the
BDM. Even if the ENABLE bit in the BDM is negated, the CPU actually executes
the BDM firmware code. It checks the ENABLE and returns if enable is not set. If
the BDM is not serviced by the monitor then the breakpoint would be re-asserted
when the BDM returns to normal CPU flow.
There is no hardware to enforce restriction of breakpoint operation if the BDM is
not enabled.
16
Block Guide — S12BKP V1
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
PRINTED VERSIONS ARE UNCONTROLLED EXCEPT WHEN STAMPED "CONTROLLED COPY" IN RED
HOW TO REACH US:
USA/EUROPE/LOCATIONS NOT LISTED:
Motorola Literature Distribution
P.O. Box 5405
Denver, Colorado 80217
1-800-521-6274 or 480-768-2130
JAPAN:
Motorola Japan Ltd.
SPS, Technical Information Center
3-20-1, Minami-Azabu, Minato-ku
Tokyo 106-8573, Japan
81-3-3440-3569
ASIA/PACIFIC:
Motorola Semiconductors H.K. Ltd.
Silicon Harbour Centre
2 Dai King Street
Tai Po Industrial Estate
Tai Po, N.T., Hong Kong
852-26668334
HOME PAGE:
http://motorola.com/semiconductors
Information in this document is provided solely to enable system and software implementers to use Motorola products.
There are no express or implied copyright licenses granted hereunder to design or fabricate any integrated circuits or
integrated circuits based on the information in this document.
Motorola reserves the right to make changes without further notice to any products herein. Motorola makes no warranty,
representation or guarantee regarding the suitability of its products for any particular purpose, nor does Motorola assume
any liability arising out of the application or use of any product or circuit, and specifically disclaims any and all liability,
including without limitation consequential or incidental damages. “Typical” parameters that may be provided in Motorola
data sheets and/or specifications can and do vary in different applications and actual performance may vary over time. All
operating parameters, including “Typicals”, must be validated for each customer application by customer’s technical
experts. Motorola does not convey any license under its patent rights nor the rights of others. Motorola products are not
designed, intended, or authorized for use as components in systems intended for surgical implant into the body, or other
applications intended to support or sustain life, or for any other application in which the failure of the Motorola product could
create a situation where personal injury or death may occur. Should Buyer purchase or use Motorola products for any such
unintended or unauthorized application, Buyer shall indemnify and hold Motorola and its officers, employees, subsidiaries,
affiliates, and distributors harmless against all claims, costs, damages, and expenses, and reasonable attorney fees arising
out of, directly or indirectly, any claim of personal injury or death associated with such unintended or unauthorized use, even
if such claim alleges that Motorola was negligent regarding the design or manufacture of the part.
MOTOROLA and the Stylized M Logo are registered in the US Patent and Trademark Office. All other product or service
names are the property of their respective owners. Motorola, Inc. is an Equal Opportunity/Affirmative Action Employer.
© Motorola Inc. 2003
S12BKPV1/D
Rev. 1.02
5/2003
S12CPUV2
Reference Manual
HCS12
Microcontrollers
S12CPUV2/D
Rev. 0
7/2003
MOTOROLA.COM/SEMICONDUCTORS
S12CPUV2
Reference Manual
To provide the most up-to-date information, the revision of our documents on the
World Wide Web will be the most current. Your printed copy may be an earlier
revision. To verify you have the latest information available, refer to:
http://motorola.com/semiconductors
The following revision history table summarizes changes contained in this
document. For your convenience, the page number designators have been linked
to the appropriate location.
Motorola and the Stylized M Logo are registered trademarks of Motorola, Inc.
DigitalDNA is a trademark of Motorola, Inc.
This product incorporates SuperFlash® technology licensed from SST.
© Motorola, Inc., 2003
S12CPUV2
Reference Manual
MOTOROLA
3
Revision History
Revision History
Date
Revision
Level
July,
2003
0
Description
Initial release
N/A
Reference Manual
4
Page
Number(s)
S12CPUV2
Revision History
MOTOROLA
Reference Manual — S12CPUV2
List of Sections
Revision History 4
List of Sections 5
Table of Contents 7
List of Figures 15
List of Tables 17
Section 1. Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Section 2. Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Section 3. Addressing Modes . . . . . . . . . . . . . . . . . . . . . 33
Section 4. Instruction Queue . . . . . . . . . . . . . . . . . . . . . . 51
Section 5. Instruction Set Overview . . . . . . . . . . . . . . . . 59
Section 6. Instruction Glossary . . . . . . . . . . . . . . . . . . . . 91
Section 7. Exception Processing. . . . . . . . . . . . . . . . . . 315
Section 8. Instruction Queue . . . . . . . . . . . . . . . . . . . . 327
Section 9. Fuzzy Logic Support . . . . . . . . . . . . . . . . . . . 341
Appendix A. Instruction Reference . . . . . . . . . . . . . . . . 381
Appendix B. M68HC11 to CPU12 Upgrade Path. . . . . . 409
Appendix C. High-Level Language Support . . . . . . . . . 431
Index 439
S12CPUV2
MOTOROLA
Reference Manual
List of Sections
5
List of Sections
Reference Manual
6
S12CPUV2
List of Sections
MOTOROLA
Reference Manual — S12CPUV2
Table of Contents
Revision History 4
List of Sections 5
Table of Contents 7
List of Figures 15
List of Tables 17
Section 1. Introduction
1.1
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .19
1.2
Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .19
1.3
Symbols and Notation. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .20
1.3.1
Abbreviations for System Resources . . . . . . . . . . . . . . . . . .20
1.3.2
Memory and Addressing . . . . . . . . . . . . . . . . . . . . . . . . . . .21
1.3.3
Operators . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .22
1.3.4
Definitions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .23
Section 2. Overview
2.1
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .25
2.2
Programming Model . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .25
2.2.1
Accumulators . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .26
2.2.2
Index Registers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .26
2.2.3
Stack Pointer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .26
2.2.4
Program Counter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .27
2.2.5
Condition Code Register . . . . . . . . . . . . . . . . . . . . . . . . . . .27
2.2.5.1
S Control Bit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .28
2.2.5.2
X Mask Bit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .29
2.2.5.3
H Status Bit. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .29
2.2.5.4
I Mask Bit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .30
2.2.5.5
N Status Bit. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .30
2.2.5.6
Z Status Bit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .30
2.2.5.7
V Status Bit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31
S12CPUV2
MOTOROLA
Reference Manual
Table of Contents
7
Table of Contents
2.2.5.8
C Status Bit. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31
2.3
Data Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31
2.4
Memory Organization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .32
2.5
Instruction Queue . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .32
Section 3. Addressing Modes
3.1
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .33
3.2
Mode Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .33
3.3
Effective Address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .33
3.4
Inherent Addressing Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . .35
3.5
Immediate Addressing Mode . . . . . . . . . . . . . . . . . . . . . . . . . .35
3.6
Direct Addressing Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .36
3.7
Extended Addressing Mode . . . . . . . . . . . . . . . . . . . . . . . . . . .37
3.8
Relative Addressing Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . .37
3.9
Indexed Addressing Modes . . . . . . . . . . . . . . . . . . . . . . . . . . .38
3.9.1
5-Bit Constant Offset Indexed Addressing . . . . . . . . . . . . . .41
3.9.2
9-Bit Constant Offset Indexed Addressing . . . . . . . . . . . . . .41
3.9.3
16-Bit Constant Offset Indexed Addressing . . . . . . . . . . . . .42
3.9.4
16-Bit Constant Indirect Indexed Addressing . . . . . . . . . . . .42
3.9.5
Auto Pre/Post Decrement/Increment Indexed Addressing . .43
3.9.6
Accumulator Offset Indexed Addressing . . . . . . . . . . . . . . .44
3.9.7
Accumulator D Indirect Indexed Addressing . . . . . . . . . . . .45
3.10 Instructions Using Multiple Modes . . . . . . . . . . . . . . . . . . . . . .45
3.10.1 Move Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .45
3.10.2 Bit Manipulation Instructions . . . . . . . . . . . . . . . . . . . . . . . .47
3.11
Addressing More than 64 Kbytes . . . . . . . . . . . . . . . . . . . . . . .48
Section 4. Instruction Queue
4.1
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .51
4.2
Queue Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .51
4.2.1
Original M68HC12 Queue Implementation . . . . . . . . . . . . .52
4.2.2
HCS12 Queue Implementation . . . . . . . . . . . . . . . . . . . . . .52
4.3
Data Movement in the Queue. . . . . . . . . . . . . . . . . . . . . . . . . .52
4.3.1
No Movement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .53
Reference Manual
8
S12CPUV2
Table of Contents
MOTOROLA
Table of Contents
4.3.2
Latch Data from Bus (Applies Only to the M68HC12 Queue
Implementation)53
4.3.3
Advance and Load from Data Bus . . . . . . . . . . . . . . . . . .53
4.3.4
Advance and Load from Buffer (Applies Only to M68HC12
Queue Implementation)53
4.4
Changes in Execution Flow . . . . . . . . . . . . . . . . . . . . . . . . . . .53
4.4.1
Exceptions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .54
4.4.2
Subroutines . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .54
4.4.3
Branches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .55
4.4.3.1
Short Branches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .56
4.4.3.2
Long Branches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .56
4.4.3.3
Bit Condition Branches. . . . . . . . . . . . . . . . . . . . . . . . . . .57
4.4.3.4
Loop Primitives. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .57
4.4.4
Jumps. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .58
Section 5. Instruction Set Overview
5.1
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .59
5.2
Instruction Set Description . . . . . . . . . . . . . . . . . . . . . . . . . . . .59
5.3
Load and Store Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . .60
5.4
Transfer and Exchange Instructions . . . . . . . . . . . . . . . . . . . . .61
5.5
Move Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62
5.6
Addition and Subtraction Instructions . . . . . . . . . . . . . . . . . . . .63
5.7
Binary-Coded Decimal Instructions . . . . . . . . . . . . . . . . . . . . .64
5.8
Decrement and Increment Instructions. . . . . . . . . . . . . . . . . . .65
5.9
Compare and Test Instructions. . . . . . . . . . . . . . . . . . . . . . . . .66
5.10
Boolean Logic Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . .67
5.11
Clear, Complement, and Negate Instructions. . . . . . . . . . . . . .68
5.12
Multiplication and Division Instructions . . . . . . . . . . . . . . . . . . .69
5.13
Bit Test and Manipulation Instructions . . . . . . . . . . . . . . . . . . .70
5.14
Shift and Rotate Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . .71
5.15 Fuzzy Logic Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .72
5.15.1 Fuzzy Logic Membership Instruction . . . . . . . . . . . . . . . . . .72
5.15.2 Fuzzy Logic Rule Evaluation Instructions. . . . . . . . . . . . . . .72
5.15.3 Fuzzy Logic Weighted Average Instruction . . . . . . . . . . . . .73
S12CPUV2
MOTOROLA
Reference Manual
Table of Contents
9
Table of Contents
5.16
Maximum and Minimum Instructions . . . . . . . . . . . . . . . . . . . .75
5.17
Multiply and Accumulate Instruction . . . . . . . . . . . . . . . . . . . . .76
5.18
Table Interpolation Instructions. . . . . . . . . . . . . . . . . . . . . . . . .76
5.19 Branch Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .77
5.19.1 Short Branch Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . .78
5.19.2 Long Branch Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . .79
5.19.3 Bit Condition Branch Instructions . . . . . . . . . . . . . . . . . . . . .80
5.20
Loop Primitive Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . .81
5.21
Jump and Subroutine Instructions . . . . . . . . . . . . . . . . . . . . . .82
5.22
Interrupt Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .83
5.23
Index Manipulation Instructions . . . . . . . . . . . . . . . . . . . . . . . .85
5.24
Stacking Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .86
5.25
Pointer and Index Calculation Instructions . . . . . . . . . . . . . . . .87
5.26
Condition Code Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . .88
5.27
Stop and Wait Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . .89
5.28
Background Mode and Null Operations . . . . . . . . . . . . . . . . . .90
Section 6. Instruction Glossary
6.1
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .91
6.2
Glossary Information. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .92
6.3
Condition Code Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . .93
6.4
Object Code Notation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .94
6.5
Source Forms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .95
6.6
Cycle-by-Cycle Execution. . . . . . . . . . . . . . . . . . . . . . . . . . . . .98
6.7
Glossary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .103
Section 7. Exception Processing
7.1
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .315
7.2
Types of Exceptions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .315
7.3
Exception Priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .316
7.4
Resets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .318
7.4.1
Power-On Reset. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .318
Reference Manual
10
S12CPUV2
Table of Contents
MOTOROLA
Table of Contents
7.4.2
7.4.3
7.4.4
External Reset . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .318
COP Reset . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .319
Clock Monitor Reset . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .319
7.5
Interrupts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .319
7.5.1
Non-Maskable Interrupt Request (XIRQ) . . . . . . . . . . . . . .319
7.5.2
Maskable Interrupts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .320
7.5.3
Interrupt Recognition . . . . . . . . . . . . . . . . . . . . . . . . . . . . .320
7.5.4
External Interrupts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .321
7.5.5
Return-from-Interrupt Instruction (RTI) . . . . . . . . . . . . . . . .321
7.6
Unimplemented Opcode Trap. . . . . . . . . . . . . . . . . . . . . . . . .322
7.7
Software Interrupt Instruction (SWI) . . . . . . . . . . . . . . . . . . . .322
7.8
Exception Processing Flow. . . . . . . . . . . . . . . . . . . . . . . . . . .323
7.8.1
Vector Fetch . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .323
7.8.2
Reset Exception Processing . . . . . . . . . . . . . . . . . . . . . . .323
7.8.3
Interrupt and Unimplemented Opcode Trap Exception Processing 325
Section 8. Instruction Queue
8.1
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .327
8.2
External Reconstruction of the Queue . . . . . . . . . . . . . . . . . .327
8.3
Instruction Queue Status Signals . . . . . . . . . . . . . . . . . . . . . .328
8.3.1
HCS12 Timing Detail . . . . . . . . . . . . . . . . . . . . . . . . . . . . .329
8.3.2
M68HC12 Timing Detail . . . . . . . . . . . . . . . . . . . . . . . . . . .329
8.3.3
Null (Code 0:0). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .331
8.3.4
LAT — Latch Data from Bus (Code 0:1) . . . . . . . . . . . . .331
8.3.5
ALD — Advance and Load from Data Bus (Code 1:0) .331
8.3.6
ALL — Advance and Load from Latch (Code 1:1). . . . .331
8.3.7
INT — Interrupt Sequence Start (Code 0:1) . . . . . . . . . . .331
8.3.8
SEV — Start Instruction on Even Address (Code 1:0) .332
8.3.9
SOD — Start Instruction on Odd Address (Code 1:1). .332
8.4
Queue Reconstruction (for HCS12) . . . . . . . . . . . . . . . . . . . .332
8.4.1
Queue Reconstruction Registers (for HCS12) . . . . . . . . . .333
8.4.1.1
fetch_add Register. . . . . . . . . . . . . . . . . . . . . . . . . . . .333
8.4.1.2
st1_add, st1_dat Registers . . . . . . . . . . . . . . . . . . . . .333
8.4.1.3
st2_add, st2_dat Registers . . . . . . . . . . . . . . . . . . . . . .333
8.4.1.4
st3_add, st3_dat Registers . . . . . . . . . . . . . . . . . . . . .334
S12CPUV2
MOTOROLA
Reference Manual
Table of Contents
11
Table of Contents
8.4.2
Reconstruction Algorithm (for HCS12) . . . . . . . . . . . . . . . .334
8.5
Queue Reconstruction (for M68HC12) . . . . . . . . . . . . . . . . . .335
8.5.1
Queue Reconstruction Registers (for M68HC12). . . . . . . .336
8.5.1.1
in_add, in_dat Registers . . . . . . . . . . . . . . . . . . . . . . .336
8.5.1.2
fetch_add, fetch_dat Registers. . . . . . . . . . . . . . . . . .336
8.5.1.3
st1_add, st1_dat Registers . . . . . . . . . . . . . . . . . . . . .336
8.5.1.4
st2_add, st2_dat Registers . . . . . . . . . . . . . . . . . . . . .336
8.5.2
Reconstruction Algorithm (for M68HC12) . . . . . . . . . . . . .337
8.5.2.1
LAT Decoding. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .337
8.5.2.2
ALD Decoding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .338
8.5.2.3
ALL Decoding. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .338
8.6
Instruction Tagging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .339
Section 9. Fuzzy Logic Support
9.1
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .341
9.2
Fuzzy Logic Basics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .342
9.2.1
Fuzzification (MEM) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .344
9.2.2
Rule Evaluation (REV and REVW). . . . . . . . . . . . . . . . . . .346
9.2.3
Defuzzification (WAV) . . . . . . . . . . . . . . . . . . . . . . . . . . . .348
9.3
Example Inference Kernel . . . . . . . . . . . . . . . . . . . . . . . . . . .349
9.4
MEM Instruction Details . . . . . . . . . . . . . . . . . . . . . . . . . . . . .351
9.4.1
Membership Function Definitions . . . . . . . . . . . . . . . . . . . .351
9.4.2
Abnormal Membership Function Definitions. . . . . . . . . . . .353
9.4.2.1
Abnormal Membership Function Case 1 . . . . . . . . . . . .355
9.4.2.2
Abnormal Membership Function Case 2 . . . . . . . . . . . .356
9.4.2.3
Abnormal Membership Function Case 3 . . . . . . . . . . . .356
9.5
REV and REVW Instruction Details . . . . . . . . . . . . . . . . . . . .357
9.5.1
Unweighted Rule Evaluation (REV) . . . . . . . . . . . . . . . . . .357
9.5.1.1
Set Up Prior to Executing REV . . . . . . . . . . . . . . . . . . .357
9.5.1.2
Interrupt Details . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .359
9.5.1.3
Cycle-by-Cycle Details for REV . . . . . . . . . . . . . . . . . . .359
9.5.2
Weighted Rule Evaluation (REVW) . . . . . . . . . . . . . . . . . .363
9.5.2.1
Set Up Prior to Executing REVW . . . . . . . . . . . . . . . . . .363
9.5.2.2
Interrupt Details . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .365
9.5.2.3
Cycle-by-Cycle Details for REVW . . . . . . . . . . . . . . . . .365
9.6
WAV Instruction Details . . . . . . . . . . . . . . . . . . . . . . . . . . . . .368
Reference Manual
12
S12CPUV2
Table of Contents
MOTOROLA
Table of Contents
9.6.1
9.6.2
9.6.3
Set Up Prior to Executing WAV . . . . . . . . . . . . . . . . . . . . .369
WAV Interrupt Details. . . . . . . . . . . . . . . . . . . . . . . . . . . . .369
Cycle-by-Cycle Details for WAV and wavr . . . . . . . . . . . . .370
9.7
Custom Fuzzy Logic Programming. . . . . . . . . . . . . . . . . . . . .374
9.7.1
Fuzzification Variations . . . . . . . . . . . . . . . . . . . . . . . . . . .374
9.7.2
Rule Evaluation Variations . . . . . . . . . . . . . . . . . . . . . . . . .377
9.7.3
Defuzzification Variations . . . . . . . . . . . . . . . . . . . . . . . . . .378
Appendix A. Instruction Reference
A.1
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .381
A.2
Stack and Memory Layout . . . . . . . . . . . . . . . . . . . . . . . . . . .382
A.3
Interrupt Vector Locations. . . . . . . . . . . . . . . . . . . . . . . . . . . .382
A.4
Notation Used in Instruction Set Summary. . . . . . . . . . . . . . .383
A.5
Hexadecimal to Decimal Conversion . . . . . . . . . . . . . . . . . . .408
A.6
Decimal to Hexadecimal Conversion . . . . . . . . . . . . . . . . . . .408
Appendix B. M68HC11 to CPU12 Upgrade Path
B.1
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .409
B.2
CPU12 Design Goals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .409
B.3
Source Code Compatibility . . . . . . . . . . . . . . . . . . . . . . . . . . .410
B.4
Programmer’s Model and Stacking. . . . . . . . . . . . . . . . . . . . .413
B.5 True 16-Bit Architecture . . . . . . . . . . . . . . . . . . . . . . . . . . . . .413
B.5.1
Bus Structures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .413
B.5.2
Instruction Queue . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .414
B.5.3
Stack Function . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .415
B.6 Improved Indexing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .417
B.6.1
Constant Offset Indexing . . . . . . . . . . . . . . . . . . . . . . . . . .418
B.6.2
Auto-Increment Indexing . . . . . . . . . . . . . . . . . . . . . . . . . .419
B.6.3
Accumulator Offset Indexing . . . . . . . . . . . . . . . . . . . . . . .420
B.6.4
Indirect Indexing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .420
B.7 Improved Performance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .421
B.7.1
Reduced Cycle Counts. . . . . . . . . . . . . . . . . . . . . . . . . . . .421
B.7.2
Fast Math . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .421
B.7.3
Code Size Reduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . .422
S12CPUV2
MOTOROLA
Reference Manual
Table of Contents
13
Table of Contents
B.8 Additional Functions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .423
B.8.1
Memory-to-Memory Moves . . . . . . . . . . . . . . . . . . . . . . . .426
B.8.2
Universal Transfer and Exchange . . . . . . . . . . . . . . . . . . .426
B.8.3
Loop Construct . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .427
B.8.4
Long Branches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .427
B.8.5
Minimum and Maximum Instructions . . . . . . . . . . . . . . . . .427
B.8.6
Fuzzy Logic Support. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .428
B.8.7
Table Lookup and Interpolation . . . . . . . . . . . . . . . . . . . . .428
B.8.8
Extended Bit Manipulation . . . . . . . . . . . . . . . . . . . . . . . . .429
B.8.9
Push and Pull D and CCR . . . . . . . . . . . . . . . . . . . . . . . . .429
B.8.10 Compare SP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .429
B.8.11 Support for Memory Expansion . . . . . . . . . . . . . . . . . . . . .430
Appendix C. High-Level Language Support
C.1
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .431
C.2
Data Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .431
C.3 Parameters and Variables . . . . . . . . . . . . . . . . . . . . . . . . . . .432
C.3.1
Register Pushes and Pulls . . . . . . . . . . . . . . . . . . . . . . . . .432
C.3.2
Allocating and Deallocating Stack Space. . . . . . . . . . . . . .433
C.3.3
Frame Pointer. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .433
C.4
Increment and Decrement Operators . . . . . . . . . . . . . . . . . . .434
C.5
Higher Math Functions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .434
C.6
Conditional If Constructs. . . . . . . . . . . . . . . . . . . . . . . . . . . . .435
C.7
Case and Switch Statements . . . . . . . . . . . . . . . . . . . . . . . . .435
C.8
Pointers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .436
C.9
Function Calls . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .436
C.10 Instruction Set Orthogonality . . . . . . . . . . . . . . . . . . . . . . . . .437
Index 439
Reference Manual
14
S12CPUV2
Table of Contents
MOTOROLA
Reference Manual — S12CPUV2
List of Figures
Figure
2-1
6-1
7-1
8-1
8-2
8-3
8-4
8-5
9-1
9-2
9-3
9-4
9-5
9-6
9-7
9-8
9-9
9-10
9-11
9-12
9-13
A-1
Title
. Programming Model . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .25
. Example Glossary Page . . . . . . . . . . . . . . . . . . . . . . . . . . . . .92
. Exception Processing Flow Diagram . . . . . . . . . . . . . . . . . .324
. Queue Status Signal Timing (HCS12) . . . . . . . . . . . . . . . . .329
. Queue Status Signal Timing (M68HC12) . . . . . . . . . . . . . . .330
. Reset Sequence for HCS12 . . . . . . . . . . . . . . . . . . . . . . . . .335
. Reset Sequence for M68HC12. . . . . . . . . . . . . . . . . . . . . . .338
. Tag Input Timing. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .339
. Block Diagram of a Fuzzy Logic System . . . . . . . . . . . . . . .343
. Fuzzification Using Membership Functions . . . . . . . . . . . . .345
. Fuzzy Inference Engine . . . . . . . . . . . . . . . . . . . . . . . . . . . .349
. Defining a Normal Membership Function . . . . . . . . . . . . . . .352
. MEM Instruction Flow Diagram. . . . . . . . . . . . . . . . . . . . . . .354
. Abnormal Membership Function Case 1 . . . . . . . . . . . . . . .355
. Abnormal Membership Function Case 2 . . . . . . . . . . . . . . .356
. Abnormal Membership Function Case 3 . . . . . . . . . . . . . . .356
. REV Instruction Flow Diagram . . . . . . . . . . . . . . . . . . . . . . .360
. REVW Instruction Flow Diagram . . . . . . . . . . . . . . . . . . . . .367
. WAV and wavr Instruction Flow Diagram (for HCS12) . . . . .372
. WAV and wavr Instruction Flow Diagram (for M68HC12) . .373
. Endpoint Table Handling . . . . . . . . . . . . . . . . . . . . . . . . . . .376
. Programming Model . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .381
S12CPUV2
MOTOROLA
Page
Reference Manual
List of Figures
15
List of Figures
Reference Manual
16
S12CPUV2
List of Figures
MOTOROLA
Reference Manual — S12CPUV2
List of Tables
Table
Title
Page
Table
Title
Page
3-1
3-2
3-3
5-1
5-2
5-3
5-4
5-5
5-6
5-7
5-8
5-9
5-10
5-11
5-12
5-13
5-14
5-15
5-16
5-17
5-18
5-19
5-20
5-21
5-22
5-23
5-24
5-25
. M68HC12 Addressing Mode Summary . . . . . . . . . . . . . . . .34
. Summary of Indexed Operations . . . . . . . . . . . . . . . . . . . . .40
. PC Offsets for MOVE Instructions (M68HC12 Only) . . . . . .46
. Load and Store Instructions . . . . . . . . . . . . . . . . . . . . . . . . .60
. Transfer and Exchange Instructions. . . . . . . . . . . . . . . . . . .62
. Move Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62
. Addition and Subtraction Instructions . . . . . . . . . . . . . . . . . .63
. BCD Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .64
. Decrement and Increment Instructions. . . . . . . . . . . . . . . . .65
. Compare and Test Instructions . . . . . . . . . . . . . . . . . . . . . .66
. Boolean Logic Instructions . . . . . . . . . . . . . . . . . . . . . . . . . .67
. Clear, Complement, and Negate Instructions. . . . . . . . . . . .68
. Multiplication and Division Instructions. . . . . . . . . . . . . . . . .69
. Bit Test and Manipulation Instructions . . . . . . . . . . . . . . . . .70
. Shift and Rotate Instructions . . . . . . . . . . . . . . . . . . . . . . . .71
. Fuzzy Logic Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . .73
. Minimum and Maximum Instructions . . . . . . . . . . . . . . . . . .75
. Multiply and Accumulate Instructions . . . . . . . . . . . . . . . . . .76
. Table Interpolation Instructions . . . . . . . . . . . . . . . . . . . . . .77
. Short Branch Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . .78
. Long Branch Instructions . . . . . . . . . . . . . . . . . . . . . . . . . .79
. Bit Condition Branch Instructions . . . . . . . . . . . . . . . . . . . . .80
. Loop Primitive Instructions . . . . . . . . . . . . . . . . . . . . . . . . . .81
. Jump and Subroutine Instructions . . . . . . . . . . . . . . . . . . . .83
. Interrupt Instructions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .84
. Index Manipulation Instructions . . . . . . . . . . . . . . . . . . . . . .85
. Stacking Instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .86
. Pointer and Index Calculation Instructions . . . . . . . . . . . . . .87
S12CPUV2
MOTOROLA
Reference Manual
List of Tables
17
List of Tables
5-26
5-27
5-28
7-1
7-2
8-1
8-2
A-1
A-2
A-3
A-4
A-5
A-6
A-7
A-8
A-9
B-1
B-2
B-3
B-4
. Condition Code Instructions . . . . . . . . . . . . . . . . . . . . . . . . .88
. Stop and Wait Instructions . . . . . . . . . . . . . . . . . . . . . . . . . .89
. Background Mode and Null Operation Instructions . . . . . . .90
. CPU12 Exception Vector Map . . . . . . . . . . . . . . . . . . . . . .316
. Stacking Order on Entry to Interrupts . . . . . . . . . . . . . . . . .321
. IPIPE1 and IPIPE0 Decoding (HCS12 and M68HC12) . . .330
. Tag Pin Function . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .339
. Instruction Set Summary . . . . . . . . . . . . . . . . . . . . . . . . . .387
. CPU12 Opcode Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . .401
. Indexed Addressing Mode Postbyte Encoding (xb) . . . . . .403
. Indexed Addressing Mode Summary . . . . . . . . . . . . . . . . .404
. Transfer and Exchange Postbyte Encoding . . . . . . . . . . . .405
. Loop Primitive Postbyte Encoding (lb) . . . . . . . . . . . . . . . .406
. Branch/Complementary Branch . . . . . . . . . . . . . . . . . . . . .406
. Hexadecimal to ASCII Conversion . . . . . . . . . . . . . . . . . . .407
. Hexadecimal to/from Decimal Conversion . . . . . . . . . . . . .408
. Translated M68HC11 Mnemonics . . . . . . . . . . . . . . . . . . .410
. Instructions with Smaller Object Code . . . . . . . . . . . . . . . .412
. Comparison of Math Instruction Speeds . . . . . . . . . . . . . .422
. New M68HC12 Instructions . . . . . . . . . . . . . . . . . . . . . . . .424
Reference Manual
18
S12CPUV2
List of Tables
MOTOROLA
Reference Manual — S12CPUV2
Section 1. Introduction
1.1 Introduction
This manual describes the features and operation of the core (central
processing unit, or CPU, and development support functions) used in all
HCS12 microcontrollers. For reference, information is provided for the
M68HC12.
1.2 Features
The CPU12 is a high-speed, 16-bit processing unit that has a
programming model identical to that of the industry standard M68HC11
central processor unit (CPU). The CPU12 instruction set is a proper
superset of the M68HC11 instruction set, and M68HC11 source code is
accepted by CPU12 assemblers with no changes.
•
Full 16-bit data paths supports efficient arithmetic operation and
high-speed math execution
•
Supports instructions with odd byte counts, including many
single-byte instructions. This allows much more efficient use of
ROM space.
•
An instruction queue buffers program information so the CPU has
immediate access to at least three bytes of machine code at the
start of every instruction.
•
Extensive set of indexed addressing capabilities, including:
– Using the stack pointer as an indexing register in all indexed
operations
– Using the program counter as an indexing register in all but
auto increment/decrement mode
– Accumulator offsets using A, B, or D accumulators
– Automatic index predecrement, preincrement, postdecrement,
and postincrement (by –8 to +8)
S12CPUV2
MOTOROLA
Reference Manual
Introduction
19
Introduction
1.3 Symbols and Notation
The symbols and notation shown here are used throughout the manual.
More specialized notation that applies only to the instruction glossary or
instruction set summary are described at the beginning of those
sections.
1.3.1 Abbreviations for System Resources
A
— Accumulator A
B
— Accumulator B
D
— Double accumulator D (A : B)
X
— Index register X
Y
— Index register Y
SP — Stack pointer
PC — Program counter
CCR — Condition code register
S — STOP instruction control bit
X — Non-maskable interrupt control bit
H — Half-carry status bit
I — Maskable interrupt control bit
N — Negative status bit
Z — Zero status bit
V — Two’s complement overflow status bit
C — Carry/Borrow status bit
Reference Manual
20
S12CPUV2
Introduction
MOTOROLA
Introduction
Symbols and Notation
1.3.2 Memory and Addressing
M
— 8-bit memory location pointed to by the effective
address of the instruction
M : M+1
— 16-bit memory location. Consists of the contents of the
location pointed to by the effective address
concatenated with the contents of the location at the
next higher memory address. The most significant byte
is at location M.
— 32-bit memory location. Consists of the contents of the
M~M+3
effective address of the instruction concatenated with
M(Y)~M(Y+3)
the contents of the next three higher memory locations.
The most significant byte is at location M or M(Y).
M(X)
— Memory locations pointed to by index register X
M(SP)
— Memory locations pointed to by the stack pointer
M(Y+3)
— Memory locations pointed to by index register Y plus 3
PPAGE
— Program overlay page (bank) number for extended
memory (>64 Kbytes).
Page
— Program overlay page
XH
— High-order byte
XL
— Low-order byte
()
— Content of register or memory location
$
— Hexadecimal value
%
— Binary value
S12CPUV2
MOTOROLA
Reference Manual
Introduction
21
Introduction
1.3.3 Operators
+ — Addition
– — Subtraction
• — Logical AND
+ — Logical OR (inclusive)
⊕ — Logical exclusive OR
× — Multiplication
÷ — Division
M — Negation. One’s complement (invert each bit of M)
: — Concatenate
Example: A : B means the 16-bit value formed by concatenating 8-bit accumulator A with 8-bit accumulator B.
A is in the high-order position.
⇒ — Transfer
Example: (A) ⇒ M means the content of accumulator A is
transferred to memory location M.
⇔ — Exchange
Example: D ⇔ X means exchange the contents of D with
those of X.
Reference Manual
22
S12CPUV2
Introduction
MOTOROLA
Introduction
Symbols and Notation
1.3.4 Definitions
Logic level 1 is the voltage that corresponds to the true (1) state.
Logic level 0 is the voltage that corresponds to the false (0) state.
Set refers specifically to establishing logic level 1 on a bit or bits.
Cleared refers specifically to establishing logic level 0 on a bit or bits.
Asserted means that a signal is in active logic state. An active low signal
changes from logic level 1 to logic level 0 when asserted, and an
active high signal changes from logic level 0 to logic level 1.
Negated means that an asserted signal changes logic state. An active
low signal changes from logic level 0 to logic level 1 when negated,
and an active high signal changes from logic level 1 to logic level 0.
ADDR is the mnemonic for address bus.
DATA is the mnemonic for data bus.
LSB means least significant bit or bits.
MSB means most significant bit or bits.
LSW means least significant word or words.
MSW means most significant word or words.
A specific bit location within a range is referred to by mnemonic and
number. For example, A7 is bit 7 of accumulator A.
A range of bit locations is referred to by mnemonic and the numbers
that define the range. For example, DATA[15:8] form the high byte of
the data bus.
S12CPUV2
MOTOROLA
Reference Manual
Introduction
23
Introduction
Reference Manual
24
S12CPUV2
Introduction
MOTOROLA
Reference Manual — S12CPUV2
Section 2. Overview
2.1 Introduction
This section describes the CPU12 programming model, register set, the
data types used, and basic memory organization.
2.2 Programming Model
The CPU12 programming model, shown in Figure 2-1, is the same as
that of the M68HC11 CPU. The CPU has two 8-bit general-purpose
accumulators (A and B) that can be concatenated into a single 16-bit
accumulator (D) for certain instructions. It also has:
•
Two index registers (X and Y)
•
16-bit stack pointer (SP)
•
16-bit program counter (PC)
•
8-bit condition code register (CCR)
A
0
B
15
D
0
8-BIT ACCUMULATORS A AND B
OR
16-BIT DOUBLE ACCUMULATOR D
15
IX
0
INDEX REGISTER X
15
IY
0
INDEX REGISTER Y
15
SP
0
STACK POINTER
15
PC
0
PROGRAM COUNTER
7
7
S
X
H
I
0
N
Z
V
C
CONDITION CODE REGISTER
Figure 2-1. Programming Model
S12CPUV2
MOTOROLA
Reference Manual
Overview
25
Overview
2.2.1 Accumulators
General-purpose 8-bit accumulators A and B are used to hold operands
and results of operations. Some instructions treat the combination of
these two 8-bit accumulators (A : B) as a 16-bit double accumulator (D).
Most operations can use accumulator A or B interchangeably. However,
there are a few exceptions. Add, subtract, and compare instructions
involving both A and B (ABA, SBA, and CBA) only operate in one
direction, so it is important to make certain the correct operand is in the
correct accumulator. The decimal adjust accumulator A (DAA)
instruction is used after binary-coded decimal (BCD) arithmetic
operations. There is no equivalent instruction to adjust accumulator B.
2.2.2 Index Registers
16-bit index registers X and Y are used for indexed addressing. In the
indexed addressing modes, the contents of an index register are added
to 5-bit, 9-bit, or 16-bit constants or to the content of an accumulator to
form the effective address of the instruction operand. The second index
register is especially useful for moves and in cases where operands from
two separate tables are used in a calculation.
2.2.3 Stack Pointer
The CPU12 supports an automatic program stack. The stack is used to
save system context during subroutine calls and interrupts and can also
be used for temporary data storage. The stack can be located anywhere
in the standard 64-Kbyte address space and can grow to any size up to
the total amount of memory available in the system.
The stack pointer (SP) holds the 16-bit address of the last stack location
used. Normally, the SP is initialized by one of the first instructions in an
application program. The stack grows downward from the address
pointed to by the SP. Each time a byte is pushed onto the stack, the
stack pointer is automatically decremented, and each time a byte is
pulled from the stack, the stack pointer is automatically incremented.
When a subroutine is called, the address of the instruction following the
calling instruction is automatically calculated and pushed onto the stack.
Normally, a return-from-subroutine (RTS) or a return-from-call (RTC)
Reference Manual
26
S12CPUV2
Overview
MOTOROLA
Overview
Programming Model
instruction is executed at the end of a subroutine. The return instruction
loads the program counter with the previously stacked return address
and execution continues at that address.
When an interrupt occurs, the current instruction finishes execution. The
address of the next instruction is calculated and pushed onto the stack,
all the CPU registers are pushed onto the stack, the program counter is
loaded with the address pointed to by the interrupt vector, and execution
continues at that address. The stacked registers are referred to as an
interrupt stack frame. The CPU12 stack frame is the same as that of the
M68HC11.
NOTE:
These instructions can be interrupted, and they resume execution once
the interrupt has been serviced:
• REV (fuzzy logic rule evaluation)
• REVW (fuzzy logic rule evaluation (weighted))
• WAV (weighted average)
2.2.4 Program Counter
The program counter (PC) is a 16-bit register that holds the address of
the next instruction to be executed. It is automatically incremented each
time an instruction is fetched.
2.2.5 Condition Code Register
The condition code register (CCR), named for its five status indicators,
contains:
•
Five status indicators
•
Two interrupt masking bits
•
STOP instruction control bit
S12CPUV2
MOTOROLA
Reference Manual
Overview
27
Overview
The status bits reflect the results of CPU operation as it executes
instructions. The five flags are:
•
Half carry (H)
•
Negative (N)
•
Zero (Z)
•
Overflow (V)
•
Carry/borrow (C)
The half-carry flag is used only for BCD arithmetic operations. The N, Z,
V, and C status bits allow for branching based on the results of a
previous operation.
In some architectures, only a few instructions affect condition codes, so
that multiple instructions must be executed in order to load and test a
variable. Since most CPU12 instructions automatically update condition
codes, it is rarely necessary to execute an extra instruction for this
purpose. The challenge in using the CPU12 lies in finding instructions
that do not alter the condition codes. The most important of these
instructions are pushes, pulls, transfers, and exchanges.
It is always a good idea to refer to an instruction set summary (see
Appendix A. Instruction Reference) to check which condition codes
are affected by a particular instruction.
The following paragraphs describe normal uses of the condition codes.
There are other, more specialized uses. For instance, the C status bit is
used to enable weighted fuzzy logic rule evaluation. Specialized usages
are described in the relevant portions of this manual and in Section 6.
Instruction Glossary.
2.2.5.1 S Control Bit
Clearing the S bit enables the STOP instruction. Execution of a STOP
instruction normally causes the on-chip oscillator to stop. This may be
undesirable in some applications. If the CPU encounters a STOP
instruction while the S bit is set, it is treated like a no-operation (NOP)
instruction and continues to the next instruction. Reset sets the S bit.
Reference Manual
28
S12CPUV2
Overview
MOTOROLA
Overview
Programming Model
2.2.5.2 X Mask Bit
The XIRQ input is an updated version of the NMI input found on earlier
generations of MCUs. Non-maskable interrupts are typically used to deal
with major system failures, such as loss of power. However, enabling
non-maskable interrupts before a system is fully powered and initialized
can lead to spurious interrupts. The X bit provides a mechanism for
enabling non-maskable interrupts after a system is stable.
By default, the X bit is set to 1 during reset. As long as the X bit remains
set, interrupt service requests made via the XIRQ pin are not
recognized. An instruction must clear the X bit to enable non-maskable
interrupt service requests made via the XIRQ pin. Once the X bit has
been cleared to 0, software cannot reset it to 1 by writing to the CCR.
The X bit is not affected by maskable interrupts.
When an XIRQ interrupt occurs after non-maskable interrupts are
enabled, both the X bit and the I bit are set automatically to prevent other
interrupts from being recognized during the interrupt service routine. The
mask bits are set after the registers are stacked, but before the interrupt
vector is fetched.
Normally, a return-from-interrupt (RTI) instruction at the end of the
interrupt service routine restores register values that were present
before the interrupt occurred. Since the CCR is stacked before the X bit
is set, the RTI normally clears the X bit, and thus re-enables
non-maskable interrupts. While it is possible to manipulate the stacked
value of X so that X is set after an RTI, there is no software method to
reset X (and disable XIRQ) once X has been cleared.
2.2.5.3 H Status Bit
The H bit indicates a carry from accumulator A bit 3 during an addition
operation. The DAA instruction uses the value of the H bit to adjust a
result in accumulator A to correct BCD format. H is updated only by the
add accumulator A to accumulator B (ABA), add without carry (ADD),
and add with carry (ADC) instructions.
S12CPUV2
MOTOROLA
Reference Manual
Overview
29
Overview
2.2.5.4 I Mask Bit
The I bit enables and disables maskable interrupt sources. By default,
the I bit is set to 1 during reset. An instruction must clear the I bit to
enable maskable interrupts. While the I bit is set, maskable interrupts
can become pending and are remembered, but operation continues
uninterrupted until the I bit is cleared.
When an interrupt occurs after interrupts are enabled, the I bit is
automatically set to prevent other maskable interrupts during the
interrupt service routine. The I bit is set after the registers are stacked,
but before the first instruction in the interrupt service routine is executed.
Normally, an RTI instruction at the end of the interrupt service routine
restores register values that were present before the interrupt occurred.
Since the CCR is stacked before the I bit is set, the RTI normally clears
the I bit, and thus re-enables interrupts. Interrupts can be re-enabled by
clearing the I bit within the service routine, but implementing a nested
interrupt management scheme requires great care and seldom improves
system performance.
2.2.5.5 N Status Bit
The N bit shows the state of the MSB of the result. N is most commonly
used in two’s complement arithmetic, where the MSB of a negative
number is 1 and the MSB of a positive number is 0, but it has other uses.
For instance, if the MSB of a register or memory location is used as a
status flag, the user can test status by loading an accumulator.
2.2.5.6 Z Status Bit
The Z bit is set when all the bits of the result are 0s. Compare
instructions perform an internal implied subtraction, and the condition
codes, including Z, reflect the results of that subtraction. The increment
index register X (INX), decrement index register X (DEX), increment
index register Y (INY), and decrement index register Y (DEY)
instructions affect the Z bit and no other condition flags. These
operations can only determine = (equal) and ≠ (not equal).
Reference Manual
30
S12CPUV2
Overview
MOTOROLA
Overview
Data Types
2.2.5.7 V Status Bit
The V bit is set when two’s complement overflow occurs as a result of an
operation.
2.2.5.8 C Status Bit
The C bit is set when a carry occurs during addition or a borrow occurs
during subtraction. The C bit also acts as an error flag for multiply and
divide operations. Shift and rotate instructions operate through the C bit
to facilitate multiple-word shifts.
2.3 Data Types
The CPU12 uses these types of data:
•
Bits
•
5-bit signed integers
•
8-bit signed and unsigned integers
•
8-bit, 2-digit binary-coded decimal numbers
•
9-bit signed integers
•
16-bit signed and unsigned integers
•
16-bit effective addresses
•
32-bit signed and unsigned integers
Negative integers are represented in two’s complement form.
Five-bit and 9-bit signed integers are used only as offsets for indexed
addressing modes.
Sixteen-bit effective addresses are formed during addressing mode
computations.
Thirty-two-bit integer dividends are used by extended division
instructions. Extended multiply and extended multiply-and-accumulate
instructions produce 32-bit products.
S12CPUV2
MOTOROLA
Reference Manual
Overview
31
Overview
2.4 Memory Organization
The standard CPU12 address space is 64 Kbytes. Some M68HC12
devices support a paged memory expansion scheme that increases the
standard space by means of predefined windows in address space. The
CPU12 has special instructions that support use of expanded memory.
Eight-bit values can be stored at any odd or even byte address in
available memory.
Sixteen-bit values are stored in memory as two consecutive bytes; the
high byte occupies the lowest address, but need not be aligned to an
even boundary.
Thirty-two-bit values are stored in memory as four consecutive bytes; the
high byte occupies the lowest address, but need not be aligned to an
even boundary.
All input/output (I/O) and all on-chip peripherals are memory-mapped.
No special instruction syntax is required to access these addresses.
On-chip registers and memory typically are grouped in blocks which can
be relocated within the standard 64-Kbyte address space. Refer to
device documentation for specific information.
2.5 Instruction Queue
The CPU12 uses an instruction queue to buffer program information.
The mechanism is called a queue rather than a pipeline because a
typical pipelined CPU executes more than one instruction at the same
time, while the CPU12 always finishes executing an instruction before
beginning to execute another. Refer to Section 4. Instruction Queue
for more information.
Reference Manual
32
S12CPUV2
Overview
MOTOROLA
Reference Manual — S12CPUV2
Section 3. Addressing Modes
3.1 Introduction
Addressing modes determine how the central processor unit (CPU)
accesses memory locations to be operated upon. This section discusses
the various modes and how they are used.
3.2 Mode Summary
Addressing modes are an implicit part of CPU12 instructions. Refer to
Appendix A. Instruction Reference for the modes used by each
instruction. All CPU12 addressing modes are shown in Table 3-1.
The CPU12 uses all M68HC11 modes as well as new forms of indexed
addressing. Differences between M68HC11 and M68HC12 indexed
modes are described in 3.9 Indexed Addressing Modes. Instructions
that use more than one mode are discussed in 3.10 Instructions Using
Multiple Modes.
3.3 Effective Address
Each addressing mode except inherent mode generates a 16-bit
effective address which is used during the memory reference portion of
the instruction. Effective address computations do not require extra
execution cycles.
S12CPUV2
MOTOROLA
Reference Manual
Addressing Modes
33
Addressing Modes
Table 3-1. M68HC12 Addressing Mode Summary
Addressing Mode
Source Format
Abbreviation
Description
Inherent
INST
(no externally
supplied operands)
INH
Operands (if any) are in CPU registers
Immediate
INST #opr8i
or
INST #opr16i
IMM
Operand is included in instruction stream
8- or 16-bit size implied by context
Direct
INST opr8a
DIR
Operand is the lower 8 bits of an address
in the range $0000–$00FF
Extended
INST opr16a
EXT
Operand is a 16-bit address
Relative
INST rel8
or
INST rel16
REL
An 8-bit or 16-bit relative offset from the current pc
is supplied in the instruction
Indexed
(5-bit offset)
INST oprx5,xysp
IDX
5-bit signed constant offset
from X, Y, SP, or PC
Indexed
(pre-decrement)
INST oprx3,–xys
IDX
Auto pre-decrement x, y, or sp by 1 ~ 8
Indexed
(pre-increment)
INST oprx3,+xys
IDX
Auto pre-increment x, y, or sp by 1 ~ 8
Indexed
(post-decrement)
INST oprx3,xys–
IDX
Auto post-decrement x, y, or sp by 1 ~ 8
Indexed
(post-increment)
INST oprx3,xys+
IDX
Auto post-increment x, y, or sp by 1 ~ 8
Indexed
(accumulator offset)
INST abd,xysp
IDX
Indexed with 8-bit (A or B) or 16-bit (D)
accumulator offset from X, Y, SP, or PC
Indexed
(9-bit offset)
INST oprx9,xysp
IDX1
9-bit signed constant offset from X, Y, SP, or PC
(lower 8 bits of offset in one extension byte)
Indexed
(16-bit offset)
INST oprx16,xysp
IDX2
16-bit constant offset from X, Y, SP, or PC
(16-bit offset in two extension bytes)
Indexed-Indirect
(16-bit offset)
INST [oprx16,xysp]
[IDX2]
Pointer to operand is found at...
16-bit constant offset from X, Y, SP, or PC
(16-bit offset in two extension bytes)
Indexed-Indirect
(D accumulator offset)
INST [D,xysp]
[D,IDX]
Pointer to operand is found at...
X, Y, SP, or PC plus the value in D
Reference Manual
34
S12CPUV2
Addressing Modes
MOTOROLA
Addressing Modes
Inherent Addressing Mode
3.4 Inherent Addressing Mode
Instructions that use this addressing mode either have no operands or
all operands are in internal CPU registers. In either case, the CPU does
not need to access any memory locations to complete the instruction.
Examples:
NOP
INX
;this instruction has no operands
;operand is a CPU register
3.5 Immediate Addressing Mode
Operands for immediate mode instructions are included in the instruction
stream and are fetched into the instruction queue one 16-bit word at a
time during normal program fetch cycles. Since program data is read into
the instruction queue several cycles before it is needed, when an
immediate addressing mode operand is called for by an instruction, it is
already present in the instruction queue.
The pound symbol (#) is used to indicate an immediate addressing mode
operand. One common programming error is to accidentally omit the #
symbol. This causes the assembler to misinterpret the expression that
follows it as an address rather than explicitly provided data. For
example, LDAA #$55 means to load the immediate value $55 into the A
accumulator, while LDAA $55 means to load the value from address
$0055 into the A accumulator. Without the # symbol, the instruction is
erroneously interpreted as a direct addressing mode instruction.
Examples:
LDAA
LDX
LDY
#$55
#$1234
#$67
These are common examples of 8-bit and 16-bit immediate addressing
modes. The size of the immediate operand is implied by the instruction
context. In the third example, the instruction implies a 16-bit immediate
value but only an 8-bit value is supplied. In this case the assembler will
generate the 16-bit value $0067 because the CPU expects a 16-bit value
in the instruction stream.
Example:
BRSET
FOO,#$03,THERE
S12CPUV2
MOTOROLA
Reference Manual
Addressing Modes
35
Addressing Modes
In this example, extended addressing mode is used to access the
operand FOO, immediate addressing mode is used to access the mask
value $03, and relative addressing mode is used to identify the
destination address of a branch in case the branch-taken conditions are
met. BRSET is listed as an extended mode instruction even though
immediate and relative modes are also used.
3.6 Direct Addressing Mode
This addressing mode is sometimes called zero-page addressing
because it is used to access operands in the address range $0000
through $00FF. Since these addresses always begin with $00, only the
eight low-order bits of the address need to be included in the instruction,
which saves program space and execution time. A system can be
optimized by placing the most commonly accessed data in this area of
memory. The eight low-order bits of the operand address are supplied
with the instruction, and the eight high-order bits of the address are
assumed to be 0.
Example:
LDAA
$55
This is a basic example of direct addressing. The value $55 is taken to
be the low-order half of an address in the range $0000 through $00FF.
The high order half of the address is assumed to be 0. During execution
of this instruction, the CPU combines the value $55 from the instruction
with the assumed value of $00 to form the address $0055, which is then
used to access the data to be loaded into accumulator A.
Example:
LDX
$20
In this example, the value $20 is combined with the assumed value of
$00 to form the address $0020. Since the LDX instruction requires a
16-bit value, a 16-bit word of data is read from addresses $0020 and
$0021. After execution of this instruction, the X index register will have
the value from address $0020 in its high-order half and the value from
address $0021 in its low-order half.
Reference Manual
36
S12CPUV2
Addressing Modes
MOTOROLA
Addressing Modes
Extended Addressing Mode
3.7 Extended Addressing Mode
In this addressing mode, the full 16-bit address of the memory location
to be operated on is provided in the instruction. This addressing mode
can be used to access any location in the 64-Kbyte memory map.
Example:
LDAA
$F03B
This is a basic example of extended addressing. The value from address
$F03B is loaded into the A accumulator.
3.8 Relative Addressing Mode
The relative addressing mode is used only by branch instructions. Short
and long conditional branch instructions use relative addressing mode
exclusively, but branching versions of bit manipulation instructions
(branch if bits set (BRSET) and branch if bits cleared (BRCLR)) use
multiple addressing modes, including relative mode. Refer to
3.10 Instructions Using Multiple Modes for more information.
Short branch instructions consist of an 8-bit opcode and a signed 8-bit
offset contained in the byte that follows the opcode. Long branch
instructions consist of an 8-bit prebyte, an 8-bit opcode, and a signed
16-bit offset contained in the two bytes that follow the opcode.
Each conditional branch instruction tests certain status bits in the
condition code register. If the bits are in a specified state, the offset is
added to the address of the next memory location after the offset to form
an effective address, and execution continues at that address. If the bits
are not in the specified state, execution continues with the instruction
immediately following the branch instruction.
Bit-condition branches test whether bits in a memory byte are in a
specific state. Various addressing modes can be used to access the
memory location. An 8-bit mask operand is used to test the bits. If each
bit in memory that corresponds to a 1 in the mask is either set (BRSET)
or clear (BRCLR), an 8-bit offset is added to the address of the next
memory location after the offset to form an effective address, and
execution continues at that address. If all the bits in memory that
correspond to a 1 in the mask are not in the specified state, execution
S12CPUV2
MOTOROLA
Reference Manual
Addressing Modes
37
Addressing Modes
continues with the instruction immediately following the branch
instruction.
8-bit, 9-bit, and 16-bit offsets are signed two’s complement numbers to
support branching upward and downward in memory. The numeric
range of short branch offset values is $80 (–128) to $7F (127). Loop
primitive instructions support a 9-bit offset which allows a range of
$100 (–256) to $0FF (255). The numeric range of long branch offset
values is $8000 (–32,768) to $7FFF (32,767). If the offset is 0, the CPU
executes the instruction immediately following the branch instruction,
regardless of the test involved.
Since the offset is at the end of a branch instruction, using a negative
offset value can cause the program counter (PC) to point to the opcode
and initiate a loop. For instance, a branch always (BRA) instruction
consists of two bytes, so using an offset of $FE sets up an infinite loop;
the same is true of a long branch always (LBRA) instruction with an
offset of $FFFC.
An offset that points to the opcode can cause a bit-condition branch to
repeat execution until the specified bit condition is satisfied. Since
bit-condition branches can consist of four, five, or six bytes depending
on the addressing mode used to access the byte in memory, the offset
value that sets up a loop can vary. For instance, using an offset of $FC
with a BRCLR that accesses memory using an 8-bit indexed postbyte
sets up a loop that executes until all the bits in the specified memory byte
that correspond to 1s in the mask byte are cleared.
3.9 Indexed Addressing Modes
The CPU12 uses redefined versions of M68HC11 indexed modes that
reduce execution time and eliminate code size penalties for using the Y
index register. In most cases, CPU12 code size for indexed operations
is the same or is smaller than that for the M68HC11. Execution time is
shorter in all cases. Execution time improvements are due to both a
reduced number of cycles for all indexed instructions and to faster
system clock speed.
Reference Manual
38
S12CPUV2
Addressing Modes
MOTOROLA
Addressing Modes
Indexed Addressing Modes
The indexed addressing scheme uses a postbyte plus zero, one, or two
extension bytes after the instruction opcode. The postbyte and
extensions do the following tasks:
1. Specify which index register is used
2. Determine whether a value in an accumulator is used as an offset
3. Enable automatic pre- or post-increment or pre- or
post-decrement
4. Specify size of increment or decrement
5. Specify use of 5-, 9-, or 16-bit signed offsets
This approach eliminates the differences between X and Y register use
while dramatically enhancing the indexed addressing capabilities.
Major advantages of the CPU12 indexed addressing scheme are:
•
The stack pointer can be used as an index register in all indexed
operations.
•
The program counter can be used as an index register in all but
autoincrement and autodecrement modes.
•
A, B, or D accumulators can be used for accumulator offsets.
•
Automatic pre- or post-increment or pre- or post-decrement by –8
to +8
•
A choice of 5-, 9-, or 16-bit signed constant offsets
•
Use of two new indexed-indirect modes:
– Indexed-indirect mode with 16-bit offset
– Indexed-indirect mode with accumulator D offset
Table 3-2 is a summary of indexed addressing mode capabilities and a
description of postbyte encoding. The postbyte is noted as xb in
instruction descriptions. Detailed descriptions of the indexed addressing
mode variations follow the table.
All indexed addressing modes use a 16-bit CPU register and additional
information to create an effective address. In most cases the effective
address specifies the memory location affected by the operation. In
some variations of indexed addressing, the effective address specifies
the location of a value that points to the memory location affected by the
operation.
S12CPUV2
MOTOROLA
Reference Manual
Addressing Modes
39
Addressing Modes
Table 3-2. Summary of Indexed Operations
Postbyte
Code (xb)
Source
Code
Syntax
rr0nnnnn
,r
n,r
–n,r
5-bit constant offset n = –16 to +15
r can specify X, Y, SP, or PC
111rr0zs
n,r
–n,r
Constant offset (9- or 16-bit signed)
z- 0 = 9-bit with sign in LSB of postbyte(s)
1 = 16-bit
if z = s = 1, 16-bit offset indexed-indirect (see below)
r can specify X, Y, SP, or PC
111rr011
[n,r]
16-bit offset indexed-indirect
rr can specify X, Y, SP, or PC
rr1pnnnn
n,–r n,+r
n,r–
n,r+
Comments
rr; 00 = X, 01 = Y, 10 = SP, 11 = PC
–256 ≤ n ≤ 255
–32,768 ≤ n ≤ 65,535
–32,768 ≤ n ≤ 65,535
Auto predecrement, preincrement, postdecrement, or postincrement;
p = pre-(0) or post-(1), n = –8 to –1, +1 to +8
r can specify X, Y, or SP (PC not a valid choice)
+8 = 0111
…
+1 = 0000
–1 = 1111
…
–8 = 1000
111rr1aa
A,r
B,r
D,r
Accumulator offset (unsigned 8-bit or 16-bit)
aa-00 = A
01 = B
10 = D (16-bit)
11 = see accumulator D offset indexed-indirect
r can specify X, Y, SP, or PC
111rr111
[D,r]
Accumulator D offset indexed-indirect
r can specify X, Y, SP, or PC
Indexed addressing mode instructions use a postbyte to specify index
registers (X and Y), stack pointer (SP), or program counter (PC) as the
base index register and to further classify the way the effective address
is formed. A special group of instructions cause this calculated effective
address to be loaded into an index register for further calculations:
•
Load stack pointer with effective address (LEAS)
•
Load X with effective address (LEAX)
•
Load Y with effective address (LEAY)
Reference Manual
40
S12CPUV2
Addressing Modes
MOTOROLA
Addressing Modes
Indexed Addressing Modes
3.9.1 5-Bit Constant Offset Indexed Addressing
This indexed addressing mode uses a 5-bit signed offset which is
included in the instruction postbyte. This short offset is added to the base
index register (X, Y, SP, or PC) to form the effective address of the
memory location that will be affected by the instruction. This gives a
range of –16 through +15 from the value in the base index register.
Although other indexed addressing modes allow 9- or 16-bit offsets,
those modes also require additional extension bytes in the instruction for
this extra information. The majority of indexed instructions in real
programs use offsets that fit in the shortest 5-bit form of indexed
addressing.
Examples:
LDAA
STAB
0,X
–8,Y
For these examples, assume X has a value of $1000 and Y has a value
of $2000 before execution. The 5-bit constant offset mode does not
change the value in the index register, so X will still be $1000 and Y will
still be $2000 after execution of these instructions. In the first example,
A will be loaded with the value from address $1000. In the second
example, the value from the B accumulator will be stored at address
$1FF8 ($2000 –$8).
3.9.2 9-Bit Constant Offset Indexed Addressing
This indexed addressing mode uses a 9-bit signed offset which is added
to the base index register (X, Y, SP, or PC) to form the effective address
of the memory location affected by the instruction. This gives a range of
–256 through +255 from the value in the base index register. The most
significant bit (sign bit) of the offset is included in the instruction postbyte
and the remaining eight bits are provided as an extension byte after the
instruction postbyte in the instruction flow.
Examples:
LDAA
LDAB
$FF,X
–20,Y
For these examples, assume X is $1000 and Y is $2000 before
execution of these instructions.
NOTE:
These instructions do not alter the index registers so they will still be
$1000 and $2000, respectively, after the instructions.
S12CPUV2
MOTOROLA
Reference Manual
Addressing Modes
41
Addressing Modes
The first instruction will load A with the value from address $10FF and
the second instruction will load B with the value from address $1FEC.
This variation of the indexed addressing mode in the CPU12 is similar to
the M68HC11 indexed addressing mode, but is functionally enhanced.
The M68HC11 CPU provides for unsigned 8-bit constant offset indexing
from X or Y, and use of Y requires an extra instruction byte and thus, an
extra execution cycle. The 9-bit signed offset used in the CPU12 covers
the same range of positive offsets as the M68HC11, and adds negative
offset capability. The CPU12 can use X, Y, SP, or PC as the base index
register.
3.9.3 16-Bit Constant Offset Indexed Addressing
This indexed addressing mode uses a 16-bit offset which is added to the
base index register (X, Y, SP, or PC) to form the effective address of the
memory location affected by the instruction. This allows access to any
address in the 64-Kbyte address space. Since the address bus and the
offset are both 16 bits, it does not matter whether the offset value is
considered to be a signed or an unsigned value ($FFFF may be thought
of as +65,535 or as –1). The 16-bit offset is provided as two extension
bytes after the instruction postbyte in the instruction flow.
3.9.4 16-Bit Constant Indirect Indexed Addressing
This indexed addressing mode adds a 16-bit instruction-supplied offset
to the base index register to form the address of a memory location that
contains a pointer to the memory location affected by the instruction. The
instruction itself does not point to the address of the memory location to
be acted upon, but rather to the location of a pointer to the address to be
acted on. The square brackets distinguish this addressing mode from
16-bit constant offset indexing.
Example:
LDAA
[10,X]
In this example, X holds the base address of a table of pointers. Assume
that X has an initial value of $1000, and that the value $2000 is stored at
addresses $100A and $100B. The instruction first adds the value 10 to
the value in X to form the address $100A. Next, an address pointer
($2000) is fetched from memory at $100A. Then, the value stored in
location $2000 is read and loaded into the A accumulator.
Reference Manual
42
S12CPUV2
Addressing Modes
MOTOROLA
Addressing Modes
Indexed Addressing Modes
3.9.5 Auto Pre/Post Decrement/Increment Indexed Addressing
This indexed addressing mode provides four ways to automatically
change the value in a base index register as a part of instruction
execution. The index register can be incremented or decremented by an
integer value either before or after indexing takes place. The base index
register may be X, Y, or SP. (Auto-modify modes would not make sense
on PC.)
Pre-decrement and pre-increment versions of the addressing mode
adjust the value of the index register before accessing the memory
location affected by the instruction — the index register retains the
changed value after the instruction executes. Post-decrement and
post-increment versions of the addressing mode use the initial value in
the index register to access the memory location affected by the
instruction, then change the value of the index register.
The CPU12 allows the index register to be incremented or decremented
by any integer value in the ranges –8 through –1 or 1 through 8. The
value need not be related to the size of the operand for the current
instruction. These instructions can be used to incorporate an index
adjustment into an existing instruction rather than using an additional
instruction and increasing execution time. This addressing mode is also
used to perform operations on a series of data structures in memory.
When an LEAS, LEAX, or LEAY instruction is executed using this
addressing mode, and the operation modifies the index register that is
being loaded, the final value in the register is the value that would have
been used to access a memory operand. (Premodification is seen in the
result but postmodification is not.)
Examples:
STAA
STX
LDX
LDAA
1,–SP
2,–SP
2,SP+
1,SP+
;equivalent to PSHA
;equivalent to PSHX
;equivalent to PULX
;equivalent to PULA
For a “last-used” type of stack like the CPU12 stack, these four
examples are equivalent to common push and pull instructions.
For a “next-available” stack like the M68HC11 stack, push A onto stack
(PSHA) is equivalent to store accumulator A (STAA) 1,SP– and pull A
from stack (PULA) is equivalent to load accumulator A (LDAA) 1,+SP.
However, in the M68HC11, 16-bit operations like push register X onto
S12CPUV2
MOTOROLA
Reference Manual
Addressing Modes
43
Addressing Modes
stack (PSHX) and pull register X from stack (PULX) require multiple
instructions to decrement the SP by one, then store X, then decrement
SP by one again.
In the STAA 1,–SP example, the stack pointer is pre-decremented by
one and then A is stored to the address contained in the stack pointer.
Similarly the LDX 2,SP+ first loads X from the address in the stack
pointer, then post-increments SP by two.
Example:
MOVW
2,X+,4,+Y
This example demonstrates how to work with data structures larger than
bytes and words. With this instruction in a program loop, it is possible to
move words of data from a list having one word per entry into a second
table that has four bytes per table element. In this example the source
pointer is updated after the data is read from memory (post-increment)
while the destination pointer is updated before it is used to access
memory (pre-increment).
3.9.6 Accumulator Offset Indexed Addressing
In this indexed addressing mode, the effective address is the sum of the
values in the base index register and an unsigned offset in one of the
accumulators. The value in the index register itself is not changed. The
index register can be X, Y, SP, or PC and the accumulator can be either
of the 8-bit accumulators (A or B) or the 16-bit D accumulator.
Example:
LDAA
B,X
This instruction internally adds B to X to form the address from which A
will be loaded. B and X are not changed by this instruction. This example
is similar to the following 2-instruction combination in an M68HC11.
Examples:
ABX
LDAA
0,X
However, this 2-instruction sequence alters the index register. If this
sequence was part of a loop where B changed on each pass, the index
register would have to be reloaded with the reference value on each loop
pass. The use of LDAA B,X is more efficient in the CPU12.
Reference Manual
44
S12CPUV2
Addressing Modes
MOTOROLA
Addressing Modes
Instructions Using Multiple Modes
3.9.7 Accumulator D Indirect Indexed Addressing
This indexed addressing mode adds the value in the D accumulator to
the value in the base index register to form the address of a memory
location that contains a pointer to the memory location affected by the
instruction. The instruction operand does not point to the address of the
memory location to be acted upon, but rather to the location of a pointer
to the address to be acted upon. The square brackets distinguish this
addressing mode from D accumulator offset indexing.
Examples:
JMP
GO1
GO2
GO3
[D,PC]
DC.W
DC.W
DC.W
PLACE1
PLACE2
PLACE3
This example is a computed GOTO. The values beginning at GO1 are
addresses of potential destinations of the jump (JMP) instruction. At the
time the JMP [D,PC] instruction is executed, PC points to the address
GO1, and D holds one of the values $0000, $0002, or $0004
(determined by the program some time before the JMP).
Assume that the value in D is $0002. The JMP instruction adds the
values in D and PC to form the address of GO2. Next the CPU reads the
address PLACE2 from memory at GO2 and jumps to PLACE2. The
locations of PLACE1 through PLACE3 were known at the time of
program assembly but the destination of the JMP depends upon the
value in D computed during program execution.
3.10 Instructions Using Multiple Modes
Several CPU12 instructions use more than one addressing mode in the
course of execution.
3.10.1 Move Instructions
Move instructions use separate addressing modes to access the source
and destination of a move. There are move variations for all practical
combinations of immediate, extended, and indexed addressing modes.
The only combinations of addressing modes that are not allowed are
those with an immediate mode destination (the operand of an immediate
mode instruction is data, not an address). For indexed moves, the
reference index register may be X, Y, SP, or PC.
S12CPUV2
MOTOROLA
Reference Manual
Addressing Modes
45
Addressing Modes
Move instructions do not support indirect modes, 9-bit, or 16-bit offset
modes requiring extra extension bytes. There are special considerations
when using PC-relative addressing with move instructions. The original
M68HC12 implemented the instruction queue slightly differently than the
newer HCS12. In the older M68HC12 implementation, the CPU did not
maintain a pointer to the start of the instruction after the current
instruction (what the user thinks of as the PC value during execution).
This caused an offset for PC-relative move instructions.
PC-relative addressing uses the address of the location immediately
following the last byte of object code for the current instruction as a
reference point. The CPU12 normally corrects for queue offset and for
instruction alignment so that queue operation is transparent to the user.
However, in the original M68HC12, move instructions pose three special
problems:
•
Some moves use an indexed source and an indexed destination.
•
Some moves have object code that is too long to fit in the queue
all at one time, so the PC value changes during execution.
•
All moves do not have the indexed postbyte as the last byte of
object code.
These cases are not handled by automatic queue pointer maintenance,
but it is still possible to use PC-relative indexing with move instructions
by providing for PC offsets in source code.
Table 3-3 shows PC offsets from the location immediately following the
current instruction by addressing mode.
Table 3-3. PC Offsets for MOVE Instructions (M68HC12 Only)
MOVE Instruction
MOVB
MOVW
Addressing Modes
Offset Value
IMM ⇒ IDX
+1
EXT ⇒ IDX
+2
IDX ⇒ EXT
–2
IDX ⇒ IDX
–1 for first operand
+1 for second operand
IMM ⇒ IDX
+2
EXT ⇒ IDX
+2
IDX ⇒ EXT
–2
IDX ⇒ IDX
–1 for first operand
+1 for second operand
Reference Manual
46
S12CPUV2
Addressing Modes
MOTOROLA
Addressing Modes
Instructions Using Multiple Modes
Example:
1000
18 09 C2 20 00
MOVB
$2000 2,PC
Moves a byte of data from $2000 to $1009
The expected location of the PC = $1005. The offset = +2.
[1005 + 2 (for 2,PC) + 2 (for correction) = 1009]
$18 is the page pre-byte, 09 is the MOVB opcode for ext-idx, C2 is the
indexed postbyte for 2,PC (without correction).
The Motorola MCUasm assembler produces corrected object code for
PC-relative moves (18 09 C0 20 00 for the example shown).
NOTE:
Instead of assembling the 2,PC as C2, the correction has been applied
to make it C0. Check whether an assembler makes the correction before
using PC-relative moves.
On the newer HCS12, the instruction queue was implemented such that
an internal pointer, to the start of the next instruction, is always available.
On the HCS12, PC-relative move instructions work as expected without
any offset adjustment. Although this is different from the original
M68HC12, it is unlikely to be a problem because PC-relative indexing is
rarely, if ever, used with move instructions.
3.10.2 Bit Manipulation Instructions
Bit manipulation instructions use either a combination of two or a
combination of three addressing modes.
The clear bits in memory (BCLR) and set bits in memory (BSET)
instructions use an 8-bit mask to determine which bits in a memory byte
are to be changed. The mask must be supplied with the instruction as an
immediate mode value. The memory location to be modified can be
specified by means of direct, extended, or indexed addressing modes.
The branch if bits cleared (BRCLR) and branch if bits set (BRSET)
instructions use an 8-bit mask to test the states of bits in a memory byte.
The mask is supplied with the instruction as an immediate mode value.
The memory location to be tested is specified by means of direct,
extended, or indexed addressing modes. Relative addressing mode is
used to determine the branch address. A signed 8-bit offset must be
supplied with the instruction.
S12CPUV2
MOTOROLA
Reference Manual
Addressing Modes
47
Addressing Modes
3.11 Addressing More than 64 Kbytes
Some M68HC12 devices incorporate hardware that supports
addressing a larger memory space than the standard 64 Kbytes. The
expanded memory system uses fast on-chip logic to implement a
transparent bank-switching scheme.
Increased code efficiency is the greatest advantage of using a switching
scheme instead of a large linear address space. In systems with large
linear address spaces, instructions require more bits of information to
address a memory location, and CPU overhead is greater. Other
advantages include the ability to change the size of system memory and
the ability to use various types of external memory.
However, the add-on bank switching schemes used in other
microcontrollers have known weaknesses. These include the cost of
external glue logic, increased programming overhead to change banks,
and the need to disable interrupts while banks are switched.
The M68HC12 system requires no external glue logic. Bank switching
overhead is reduced by implementing control logic in the MCU.
Interrupts do not need to be disabled during switching because switching
tasks are incorporated in special instructions that greatly simplify
program access to extended memory.
MCUs with expanded memory treat the 16 Kbytes of memory space
from $8000 to $BFFF as a program memory window.
Expanded-memory architecture includes an 8-bit program page register
(PPAGE), which allows up to 256 16-Kbyte program memory pages to
be switched into and out of the program memory window. This provides
for up to 4 Megabytes of paged program memory.
The CPU12 instruction set includes call subroutine in expanded memory
(CALL) and return from call (RTC) instructions, which greatly simplify the
use of expanded memory space. These instructions also execute
correctly on devices that do not have expanded-memory addressing
capability, thus providing for portable code.
The CALL instruction is similar to the jump-to-subroutine (JSR)
instruction. When CALL is executed, the current value in PPAGE is
pushed onto the stack with a return address, and a new
instruction-supplied value is written to PPAGE. This value selects the
page the called subroutine resides upon and can be considered part of
Reference Manual
48
S12CPUV2
Addressing Modes
MOTOROLA
Addressing Modes
Addressing More than 64 Kbytes
the effective address. For all addressing mode variations except indexed
indirect modes, the new page value is provided by an immediate
operand in the instruction. For indexed indirect variations of CALL, a
pointer specifies memory locations where the new page value and the
address of the called subroutine are stored. Use of indirect addressing
for both the page value and the address within the page frees the
program from keeping track of explicit values for either address.
The RTC instruction restores the saved program page value and the
return address from the stack. This causes execution to resume at the
next instruction after the original CALL instruction.
S12CPUV2
MOTOROLA
Reference Manual
Addressing Modes
49
Addressing Modes
Reference Manual
50
S12CPUV2
Addressing Modes
MOTOROLA
Reference Manual — S12CPUV2
Section 4. Instruction Queue
4.1 Introduction
The CPU12 uses an instruction queue to increase execution speed.
This section describes queue operation during normal program
execution and changes in execution flow. These concepts augment the
descriptions of instructions and cycle-by-cycle instruction execution in
subsequent sections, but it is important to note that queue operation is
automatic, and generally transparent to the user.
The material in this section is general. Section 6. Instruction Glossary
contains detailed information concerning cycle-by-cycle execution of
each instruction. Section 8. Instruction Queue contains detailed
information about tracking queue operation and instruction execution.
4.2 Queue Description
The fetching mechanism in the CPU12 is best described as a queue
rather than as a pipeline. Queue logic fetches program information and
positions it for execution, but instructions are executed sequentially. A
typical pipelined central processor unit (CPU) can execute more than
one instruction at the same time, but interactions between the prefetch
and execution mechanisms can make tracking and debugging difficult.
The CPU12 thus gains the advantages of independent fetches, yet
maintains a straightforward relationship between bus and execution
cycles.
Each instruction refills the queue by fetching the same number of bytes
that the instruction uses. Program information is fetched in aligned 16-bit
words. Each program fetch (P) indicates that two bytes need to be
replaced in the instruction queue. Each optional fetch (O) indicates that
only one byte needs to be replaced. For example, an instruction
composed of five bytes does two program fetches and one optional
fetch. If the first byte of the five-byte instruction was even-aligned, the
S12CPUV2
MOTOROLA
Reference Manual
Instruction Queue
51
Instruction Queue
optional fetch is converted into a free cycle. If the first byte was
odd-aligned, the optional fetch is executed as a program fetch.
Two external pins, IPIPE[1:0], provide time-multiplexed information
about data movement in the queue and instruction execution. Decoding
and use of these signals is discussed in Section 8. Instruction Queue.
4.2.1 Original M68HC12 Queue Implementation
There are two 16-bit queue stages and one 16-bit buffer. Program
information is fetched in aligned 16-bit words. Unless buffering is
required, program information is first queued into stage 1, then
advanced to stage 2 for execution.
At least two words of program information are available to the CPU when
execution begins. The first byte of object code is in either the even or odd
half of the word in stage 2, and at least two more bytes of object code
are in the queue.
The buffer is used when a program word arrives before the queue can
advance. This occurs during execution of single-byte and odd-aligned
instructions. For instance, the queue cannot advance after an aligned,
single-byte instruction is executed, because the first byte of the next
instruction is also in stage 2. In these cases, information is latched into
the buffer until the queue can advance.
4.2.2 HCS12 Queue Implementation
There are three 16-bit stages in the instruction queue. Instructions enter
the queue at stage 1 and shift out of stage 3 as the CPU executes
instructions and fetches new ones into stage 1. Each byte in the queue
is selectable. An opcode prediction algorithm determines the location of
the next opcode in the instruction queue.
4.3 Data Movement in the Queue
All queue operations are combinations of four basic queue movement
cycles. Descriptions of each of these cycles follows. Queue movement
cycles are only one factor in instruction execution time and should not be
confused with bus cycles.
Reference Manual
52
S12CPUV2
Instruction Queue
MOTOROLA
Instruction Queue
Changes in Execution Flow
4.3.1 No Movement
There is no data movement in the instruction queue during the cycle.
This occurs during execution of instructions that must perform a number
of internal operations, such as division instructions.
4.3.2 Latch Data from Bus (Applies Only to the M68HC12 Queue Implementation)
All instructions initiate fetches to refill the queue as execution proceeds.
However, a number of conditions, including instruction alignment and
the length of previous instructions, affect when the queue advances. If
the queue is not ready to advance when fetched information arrives, the
information is latched into the buffer. Later, when the queue does
advance, stage 1 is refilled from the buffer. If more than one latch cycle
occurs before the queue advances, the buffer is filled on the first latch
event and subsequent latch events are ignored until the queue
advances.
4.3.3 Advance and Load from Data Bus
The content of queue is advanced by one stage, and stage 1 is loaded
with a word of program information from the data bus. The information
was requested two bus cycles earlier but has only become available this
cycle, due to access delay.
4.3.4 Advance and Load from Buffer (Applies Only to M68HC12 Queue Implementation)
The content of queue stage 1 advances to stage 2, and stage 1 is loaded
with a word of program information from the buffer. The information in
the buffer was latched from the data bus during a previous cycle
because the queue was not ready to advance when it arrived.
4.4 Changes in Execution Flow
During normal instruction execution, queue operations proceed as a
continuous sequence of queue movement cycles. However, situations
arise which call for changes in flow. These changes are categorized as
resets, interrupts, subroutine calls, conditional branches, and jumps.
Generally speaking, resets and interrupts are considered to be related
to events outside the current program context that require special
S12CPUV2
MOTOROLA
Reference Manual
Instruction Queue
53
Instruction Queue
processing, while subroutine calls, branches, and jumps are considered
to be elements of program structure.
During design, great care is taken to assure that the mechanism that
increases instruction throughput during normal program execution does
not cause bottlenecks during changes of program flow, but internal
queue operation is largely transparent to the user. The following
information is provided to enhance subsequent descriptions of
instruction execution.
4.4.1 Exceptions
Exceptions are events that require processing outside the normal flow of
instruction execution. CPU12 exceptions include five types of
exceptions:
•
Reset (including COP, clock monitor, and pin)
•
Unimplemented opcode trap
•
Software interrupt instruction
•
X-bit interrupts
•
I-bit interrupts
All exceptions use the same microcode, but the CPU follows different
execution paths for each type of exception.
CPU12 exception handling is designed to minimize the effect of queue
operation on context switching. Thus, an exception vector fetch is the
first part of exception processing, and fetches to refill the queue from the
address pointed to by the vector are interleaved with the stacking
operations that preserve context, so that program access time does not
delay the switch. Refer to Section 7. Exception Processing for detailed
information.
4.4.2 Subroutines
The CPU12 can branch to (BSR), jump to (JSR), or call (CALL)
subroutines. BSR and JSR are used to access subroutines in the normal
64-Kbyte address space. The CALL instruction is intended for use in
MCUs with expanded memory capability.
Reference Manual
54
S12CPUV2
Instruction Queue
MOTOROLA
Instruction Queue
Changes in Execution Flow
BSR uses relative addressing mode to generate the effective address of
the subroutine, while JSR can use various other addressing modes.
Both instructions calculate a return address, stack the address, then
perform three program word fetches to refill the queue.
Subroutines in the normal 64-Kbyte address space are terminated with
a return-from-subroutine (RTS) instruction. RTS unstacks the return
address, then performs three program word fetches from that address to
refill the queue.
CALL is similar to JSR. MCUs with expanded memory treat 16 Kbytes of
addresses from $8000 to $BFFF as a memory window. An 8-bit PPAGE
register switches memory pages into and out of the window. When CALL
is executed, a return address is calculated, then it and the current
PPAGE value are stacked, and a new instruction-supplied value is
written to PPAGE. The subroutine address is calculated, then three
program word fetches are made from that address to refill the instruction
queue.
The return-from-call (RTC) instruction is used to terminate subroutines
in expanded memory. RTC unstacks the PPAGE value and the return
address, then performs three program word fetches from that address to
refill the queue.
CALL and RTC execute correctly in the normal 64-Kbyte address space,
thus providing for portable code. However, since extra execution cycles
are required, routinely substituting CALL/RTC for JSR/RTS is not
recommended.
4.4.3 Branches
Branch instructions cause execution flow to change when specific
pre-conditions exist. The CPU12 instruction set includes:
•
Short conditional branches
•
Long conditional branches
•
Bit-condition branches
Types and conditions of branch instructions are described in
5.19 Branch Instructions. All branch instructions affect the queue
similarly, but there are differences in overall cycle counts between the
S12CPUV2
MOTOROLA
Reference Manual
Instruction Queue
55
Instruction Queue
various types. Loop primitive instructions are a special type of branch
instruction used to implement counter-based loops.
Branch instructions have two execution cases:
•
The branch condition is satisfied, and a change of flow takes
place.
•
The branch condition is not satisfied, and no change of flow
occurs.
4.4.3.1 Short Branches
The “not-taken” case for short branches is simple. Since the instruction
consists of a single word containing both an opcode and an 8-bit offset,
the queue advances, another program word is fetched, and execution
continues with the next instruction.
The “taken” case for short branches requires that the queue be refilled
so that execution can continue at a new address. First, the effective
address of the destination is calculated using the relative offset in the
instruction. Then, the address is loaded into the program counter, and
the CPU performs three program word fetches at the new address to
refill the instruction queue.
4.4.3.2 Long Branches
The “not-taken” case for all long branches requires three cycles, while
the “taken” case requires four cycles. This is due to differences in the
amount of program information needed to fill the queue.
Long branch instructions begin with a $18 prebyte which indicates that
the opcode is on page 2 of the opcode map. The CPU12 treats the
prebyte as a special one-byte instruction. If the prebyte is not aligned,
the first cycle is used to perform a program word access; if the prebyte
is aligned, the first cycle is used to perform a free cycle. The first cycle
for the prebyte is executed whether or not the branch is taken.
The first cycle of the branch instruction is an optional cycle. Optional
cycles make the effects of byte-sized and misaligned instructions
consistent with those of aligned word-length instructions. Program
information is always fetched as aligned 16-bit words. When an
instruction has an odd number of bytes, and the first byte is not aligned
with an even byte boundary, the optional cycle makes an additional
Reference Manual
56
S12CPUV2
Instruction Queue
MOTOROLA
Instruction Queue
Changes in Execution Flow
program word access that maintains queue order. In all other cases, the
optional cycle is a free cycle.
In the “not-taken” case, the queue must advance so that execution can
continue with the next instruction. Two cycles are used to refill the
queue. Alignment determines how the second of these cycles is used.
In the “taken” case, the effective address of the branch is calculated
using the 16-bit relative offset contained in the second word of the
instruction. This address is loaded into the program counter, then the
CPU performs three program word fetches at the new address.
4.4.3.3 Bit Condition Branches
Bit condition branch instructions read a location in memory, and branch
if the bits in that location are in a certain state. These instructions can
use direct, extended, or indexed addressing modes. Indexed operations
require varying amounts of information to determine the effective
address, so instruction length varies according to the mode used, which
in turn affects the amount of program information fetched. To shorten
execution time, these branches perform one program word fetch in
anticipation of the “taken” case. The data from this fetch is ignored in the
“not-taken” case. If the branch is taken, the CPU fetches three program
word fetches at the new address to fill the instruction queue.
4.4.3.4 Loop Primitives
The loop primitive instructions test a counter value in a register or
accumulator and branch to an address specified by a 9-bit relative offset
contained in the instruction if a specified condition is met. There are
auto-increment and auto-decrement versions of these instructions. The
test and increment/decrement operations are performed on internal
CPU registers, and require no additional program information. To
shorten execution time, these branches perform one program word fetch
in anticipation of the “taken” case. The data from this fetch is ignored if
the branch is not taken, and the CPU does one program fetch and one
optional fetch to refill the queue1. If the branch is taken, the CPU finishes
refilling the queue with two additional program word fetches at the new
address.
1. In the original M68HC12, the implementation of these two cycles are both program
word fetches.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Queue
57
Instruction Queue
4.4.4 Jumps
Jump (JMP) is the simplest change of flow instruction. JMP can use
extended or indexed addressing. Indexed operations require varying
amounts of information to determine the effective address, so instruction
length varies according to the mode used, which in turn affects the
amount of program information fetched. All forms of JMP perform three
program word fetches at the new address to refill the instruction queue.
Reference Manual
58
S12CPUV2
Instruction Queue
MOTOROLA
Reference Manual — S12CPUV2
Section 5. Instruction Set Overview
5.1 Introduction
This section contains general information about the central processor
unit (CPU12) instruction set. It is organized into instruction categories
grouped by function.
5.2 Instruction Set Description
CPU12 instructions are a superset of the M68HC11 instruction set. Code
written for an M68HC11 can be reassembled and run on a CPU12 with
no changes. The CPU12 provides expanded functionality and increased
code efficiency. There are two implementations of the CPU12, the
original M68HC12 and the newer HCS12. Both implementations have
the same instruction set, although there are small differences in
cycle-by-cycle access details (the order of some bus cycles changed to
accommodate differences in the way the instruction queue was
implemented). These minor differences are transparent for most users.
In the M68HC12 and HCS12 architecture, all memory and input/output
(I/O) are mapped in a common 64-Kbyte address space
(memory-mapped I/O). This allows the same set of instructions to be
used to access memory, I/O, and control registers. General-purpose
load, store, transfer, exchange, and move instructions facilitate
movement of data to and from memory and peripherals.
The CPU12 has a full set of 8-bit and 16-bit mathematical instructions.
There are instructions for signed and unsigned arithmetic, division, and
multiplication with 8-bit, 16-bit, and some larger operands.
Special arithmetic and logic instructions aid stacking operations,
indexing, binary-coded decimal (BCD) calculation, and condition code
register manipulation. There are also dedicated instructions for multiply
and accumulate operations, table interpolation, and specialized fuzzy
logic operations that involve mathematical calculations.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Set Overview
59
Instruction Set Overview
Refer to Section 6. Instruction Glossary for detailed information about
individual instructions. Appendix A. Instruction Reference contains
quick-reference material, including an opcode map and postbyte
encoding for indexed addressing, transfer/exchange instructions, and
loop primitive instructions.
5.3 Load and Store Instructions
Load instructions copy memory content into an accumulator or register.
Memory content is not changed by the operation. Load instructions (but
not LEA_ instructions) affect condition code bits so no separate test
instructions are needed to check the loaded values for negative or 0
conditions.
Store instructions copy the content of a CPU register to memory.
Register/accumulator content is not changed by the operation. Store
instructions automatically update the N and Z condition code bits, which
can eliminate the need for a separate test instruction in some programs.
Table 5-1 is a summary of load and store instructions.
Table 5-1. Load and Store Instructions
Mnemonic
Function
Operation
Load Instructions
LDAA
Load A
(M) ⇒ A
LDAB
Load B
(M) ⇒ B
LDD
Load D
(M : M + 1) ⇒ (A:B)
LDS
Load SP
(M : M + 1) ⇒ SPH:SPL
LDX
Load index register X
(M : M + 1) ⇒ XH:XL
LDY
Load index register Y
(M : M + 1) ⇒ YH:YL
LEAS
Load effective address into SP
Effective address ⇒ SP
LEAX
Load effective address into X
Effective address ⇒ X
LEAY
Load effective address into Y
Effective address ⇒ Y
Continued on next page
Reference Manual
60
S12CPUV2
Instruction Set Overview
MOTOROLA
Instruction Set Overview
Transfer and Exchange Instructions
Table 5-1. Load and Store Instructions (Continued)
Store Instructions
STAA
Store A
(A) ⇒ M
STAB
Store B
(B) ⇒ M
STD
Store D
(A) ⇒ M, (B) ⇒ M + 1
STS
Store SP
(SPH:SPL) ⇒ M : M + 1
STX
Store X
(XH:XL) ⇒ M : M + 1
STY
Store Y
(YH:YL) ⇒ M : M + 1
5.4 Transfer and Exchange Instructions
Transfer instructions copy the content of a register or accumulator into
another register or accumulator. Source content is not changed by the
operation. Transfer register to register (TFR) is a universal transfer
instruction, but other mnemonics are accepted for compatibility with the
M68HC11. The transfer A to B (TAB) and transfer B to A (TBA)
instructions affect the N, Z, and V condition code bits in the same way
as M68HC11 instructions. The TFR instruction does not affect the
condition code bits.
The sign extend 8-bit operand (SEX) instruction is a special case of the
universal transfer instruction that is used to sign extend 8-bit two’s
complement numbers so that they can be used in 16-bit operations. The
8-bit number is copied from accumulator A, accumulator B, or the
condition code register to accumulator D, the X index register, the Y
index register, or the stack pointer. All the bits in the upper byte of the
16-bit result are given the value of the most-significant bit (MSB) of the
8-bit number.
Exchange instructions exchange the contents of pairs of registers or
accumulators. When the first operand in an EXG instruction is 8-bits and
the second operand is 16 bits, a zero-extend operation is performed on
the 8-bit register as it is copied into the 16-bit register.
Section 6. Instruction Glossary contains information concerning other
transfers and exchanges between 8- and 16-bit registers.
Table 5-2 is a summary of transfer and exchange instructions.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Set Overview
61
Instruction Set Overview
Table 5-2. Transfer and Exchange Instructions
Mnemonic
Function
Operation
Transfer Instructions
TAB
Transfer A to B
(A) ⇒ B
TAP
Transfer A to CCR
(A) ⇒ CCR
TBA
Transfer B to A
(B) ⇒ A
TFR
Transfer register
to register
(A, B, CCR, D, X, Y, or SP) ⇒
A, B, CCR, D, X, Y, or SP
TPA
Transfer CCR to A
(CCR) ⇒ A
TSX
Transfer SP to X
(SP) ⇒ X
TSY
Transfer SP to Y
(SP) ⇒ Y
TXS
Transfer X to SP
(X) ⇒ SP
TYS
Transfer Y to SP
(Y) ⇒ SP
Exchange Instructions
EXG
Exchange register
to register
(A, B, CCR, D, X, Y, or SP) ⇔
(A, B, CCR, D, X, Y, or SP)
XGDX
Exchange D with X
(D) ⇔ (X)
XGDY
Exchange D with Y
(D) ⇔ (Y)
Sign Extension Instruction
SEX
Sign extend
8-Bit operand
Sign-extended (A, B, or CCR) ⇒
D, X, Y, or SP
5.5 Move Instructions
Move instructions move (copy) data bytes or words from a source
(M1 or M : M +11) to a destination (M2 or M : M +12) in memory. Six
combinations of immediate, extended, and indexed addressing are
allowed to specify source and destination addresses (IMM ⇒ EXT,
IMM ⇒ IDX, EXT ⇒ EXT, EXT ⇒ IDX, IDX ⇒ EXT, IDX ⇒ IDX).
Addressing mode combinations with immediate for the destination would
not be useful.
Table 5-3 shows byte and word move instructions.
Table 5-3. Move Instructions
Mnemonic
Function
Operation
MOVB
Move byte (8-bit)
(M1) ⇒ M2
MOVW
Move word (16-bit)
(M : M + 11) ⇒ M : M + 12
Reference Manual
62
S12CPUV2
Instruction Set Overview
MOTOROLA
Instruction Set Overview
Addition and Subtraction Instructions
5.6 Addition and Subtraction Instructions
Signed and unsigned 8- and 16-bit addition can be performed between
registers or between registers and memory. Special instructions support
index calculation. Instructions that add the carry bit in the condition code
register (CCR) facilitate multiple precision computation.
Signed and unsigned 8- and 16-bit subtraction can be performed
between registers or between registers and memory. Special
instructions support index calculation. Instructions that subtract the carry
bit in the CCR facilitate multiple precision computation. Refer to
Table 5-4 for addition and subtraction instructions.
Load effective address (LEAS, LEAX, and LEAY) instructions could also
be considered as specialized addition and subtraction instructions. See
5.25 Pointer and Index Calculation Instructions for more information.
Table 5-4. Addition and Subtraction Instructions
Mnemonic
Function
Operation
Addition Instructions
ABA
Add B to A
(A) + (B) ⇒ A
ABX
Add B to X
(B) + (X) ⇒ X
ABY
Add B to Y
(B) + (Y) ⇒ Y
ADCA
Add with carry to A
(A) + (M) + C ⇒ A
ADCB
Add with carry to B
(B) + (M) + C ⇒ B
ADDA
Add without carry to A
(A) + (M) ⇒ A
ADDB
Add without carry to B
(B) + (M) ⇒ B
ADDD
Add to D
(A:B) + (M : M + 1) ⇒ A : B
Subtraction Instructions
SBA
Subtract B from A
(A) – (B) ⇒ A
SBCA
Subtract with borrow from A
(A) – (M) – C ⇒ A
SBCB
Subtract with borrow from B
(B) – (M) – C ⇒ B
SUBA
Subtract memory from A
(A) – (M) ⇒ A
SUBB
Subtract memory from B
(B) – (M) ⇒ B
SUBD
Subtract memory from D (A:B)
(D) – (M : M + 1) ⇒ D
S12CPUV2
MOTOROLA
Reference Manual
Instruction Set Overview
63
Instruction Set Overview
5.7 Binary-Coded Decimal Instructions
To add binary-coded decimal (BCD) operands, use addition instructions
that set the half-carry bit in the CCR, then adjust the result with the
decimal adjust A (DAA) instruction. Table 5-5 is a summary of
instructions that can be used to perform BCD operations.
Table 5-5. BCD Instructions
Mnemonic
Function
Operation
ABA
Add B to A
(A) + (B) ⇒ A
ADCA
Add with carry to A
(A) + (M) + C ⇒ A
ADCB(1)
Add with carry to B
(B) + (M) + C ⇒ B
ADDA(1)
Add memory to A
(A) + (M) ⇒ A
ADDB
Add memory to B
(B) + (M) ⇒ B
DAA
Decimal adjust A
(A)10
1. These instructions are not normally used for BCD operations because, although they affect
H correctly, they do not leave the result in the correct accumulator (A) to be used with the
DAA instruction. Thus additional steps would be needed to adjust the result to correct BCD
form.
Reference Manual
64
S12CPUV2
Instruction Set Overview
MOTOROLA
Instruction Set Overview
Decrement and Increment Instructions
5.8 Decrement and Increment Instructions
The decrement and increment instructions are optimized 8- and 16-bit
addition and subtraction operations. They are generally used to
implement counters. Because they do not affect the carry bit in the CCR,
they are particularly well suited for loop counters in multiple-precision
computation routines. Refer to 5.20 Loop Primitive Instructions for
information concerning automatic counter branches. Table 5-6 is a
summary of decrement and increment instructions.
Table 5-6. Decrement and Increment Instructions
Mnemonic
Function
Operation
Decrement Instructions
DEC
Decrement memory
(M) – $01 ⇒ M
DECA
Decrement A
(A) – $01 ⇒ A
DECB
Decrement B
(B) – $01 ⇒ B
DES
Decrement SP
(SP) – $0001 ⇒ SP
DEX
Decrement X
(X) – $0001 ⇒ X
DEY
Decrement Y
(Y) – $0001 ⇒ Y
Increment Instructions
INC
Increment memory
(M) + $01 ⇒ M
INCA
Increment A
(A) + $01 ⇒ A
INCB
Increment B
(B) + $01 ⇒ B
INS
Increment SP
(SP) + $0001 ⇒ SP
INX
Increment X
(X) + $0001 ⇒ X
INY
Increment Y
(Y) + $0001 ⇒ Y
S12CPUV2
MOTOROLA
Reference Manual
Instruction Set Overview
65
Instruction Set Overview
5.9 Compare and Test Instructions
Compare and test instructions perform subtraction between a pair of
registers or between a register and memory. The result is not stored, but
condition codes are set by the operation. These instructions are
generally used to establish conditions for branch instructions. In this
architecture, most instructions update condition code bits automatically,
so it is often unnecessary to include separate test or compare
instructions. Table 5-7 is a summary of compare and test instructions.
Table 5-7. Compare and Test Instructions
Mnemonic
Function
Operation
Compare Instructions
CBA
Compare A to B
(A) – (B)
CMPA
Compare A to memory
(A) – (M)
CMPB
Compare B to memory
(B) – (M)
CPD
Compare D to memory (16-bit)
(A : B) – (M : M + 1)
CPS
Compare SP to memory (16-bit)
(SP) – (M : M + 1)
CPX
Compare X to memory (16-bit)
(X) – (M : M + 1)
CPY
Compare Y to memory (16-bit)
(Y) – (M : M + 1)
Test Instructions
TST
Test memory for zero or minus
(M) – $00
TSTA
Test A for zero or minus
(A) – $00
TSTB
Test B for zero or minus
(B) – $00
Reference Manual
66
S12CPUV2
Instruction Set Overview
MOTOROLA
Instruction Set Overview
Boolean Logic Instructions
5.10 Boolean Logic Instructions
The Boolean logic instructions perform a logic operation between an
8-bit accumulator or the CCR and a memory value. AND, OR, and
exclusive OR functions are supported. Table 5-8 summarizes logic
instructions.
Table 5-8. Boolean Logic Instructions
Mnemonic
Function
Operation
ANDA
AND A with memory
(A) • (M) ⇒ A
ANDB
AND B with memory
(B) • (M) ⇒ B
ANDCC
AND CCR with memory (clear CCR bits)
(CCR) • (M) ⇒ CCR
EORA
Exclusive OR A with memory
(A) ⊕ (M) ⇒ A
EORB
Exclusive OR B with memory
(B) ⊕ (M) ⇒ B
ORAA
OR A with memory
(A) + (M) ⇒ A
ORAB
OR B with memory
(B) + (M) ⇒ B
ORCC
OR CCR with memory (set CCR bits)
(CCR) + (M) ⇒ CCR
S12CPUV2
MOTOROLA
Reference Manual
Instruction Set Overview
67
Instruction Set Overview
5.11 Clear, Complement, and Negate Instructions
Each of the clear, complement, and negate instructions performs a
specific binary operation on a value in an accumulator or in memory.
Clear operations clear the value to 0, complement operations replace
the value with its one’s complement, and negate operations replace the
value with its two’s complement. Table 5-9 is a summary of clear,
complement, and negate instructions.
Table 5-9. Clear, Complement, and Negate Instructions
Mnemonic
Function
Operation
CLC
Clear C bit in CCR
0⇒C
CLI
Clear I bit in CCR
0⇒I
CLR
Clear memory
$00 ⇒ M
CLRA
Clear A
$00 ⇒ A
CLRB
Clear B
$00 ⇒ B
CLV
Clear V bit in CCR
0⇒V
COM
One’s complement memory
$FF – (M) ⇒ M or (M) ⇒ M
COMA
One’s complement A
$FF – (A) ⇒ A or (A) ⇒ A
COMB
One’s complement B
$FF – (B) ⇒ B or (B) ⇒ B
NEG
Two’s complement memory
$00 – (M) ⇒ M or (M) + 1 ⇒ M
NEGA
Two’s complement A
$00 – (A) ⇒ A or (A) + 1 ⇒ A
NEGB
Two’s complement B
$00 – (B) ⇒ B or (B) + 1 ⇒ B
Reference Manual
68
S12CPUV2
Instruction Set Overview
MOTOROLA
Instruction Set Overview
Multiplication and Division Instructions
5.12 Multiplication and Division Instructions
There are instructions for signed and unsigned 8- and 16-bit
multiplication. Eight-bit multiplication operations have a 16-bit product.
Sixteen-bit multiplication operations have 32-bit products.
Integer and fractional division instructions have 16-bit dividend, divisor,
quotient, and remainder. Extended division instructions use a 32-bit
dividend and a 16-bit divisor to produce a 16-bit quotient and a 16-bit
remainder.
Table 5-10 is a summary of multiplication and division instructions.
Table 5-10. Multiplication and Division Instructions
Mnemonic
Function
Operation
Multiplication Instructions
EMUL
16 by 16 multiply (unsigned)
(D) × (Y) ⇒ Y : D
EMULS
16 by 16 multiply (signed)
(D) × (Y) ⇒ Y : D
MUL
8 by 8 multiply (unsigned)
(A) × (B) ⇒ A : B
Division Instructions
EDIV
32 by 16 divide (unsigned)
(Y : D) ÷ (X) ⇒ Y
Remainder ⇒ D
EDIVS
32 by 16 divide (signed)
(Y : D) ÷ (X) ⇒ Y
Remainder ⇒ D
FDIV
16 by 16 fractional divide
(D) ÷ (X) ⇒ X
Remainder ⇒ D
IDIV
16 by 16 integer divide (unsigned)
(D) ÷ (X) ⇒ X
Remainder ⇒ D
IDIVS
16 by 16 integer divide (signed)
(D) ÷ (X) ⇒ X
Remainder ⇒ D
S12CPUV2
MOTOROLA
Reference Manual
Instruction Set Overview
69
Instruction Set Overview
5.13 Bit Test and Manipulation Instructions
The bit test and manipulation operations use a mask value to test or
change the value of individual bits in an accumulator or in memory. Bit
test A (BITA) and bit test B (BITB) provide a convenient means of testing
bits without altering the value of either operand. Table 5-11 is a
summary of bit test and manipulation instructions.
Table 5-11. Bit Test and Manipulation Instructions
Mnemonic
Function
Operation
BCLR
Clear bits in memory
(M) • (mm) ⇒ M
BITA
Bit test A
(A) • (M)
BITB
Bit test B
(B) • (M)
BSET
Set bits in memory
(M) + (mm) ⇒ M
Reference Manual
70
S12CPUV2
Instruction Set Overview
MOTOROLA
Instruction Set Overview
Shift and Rotate Instructions
5.14 Shift and Rotate Instructions
There are shifts and rotates for all accumulators and for memory bytes.
All pass the shifted-out bit through the C status bit to facilitate
multiple-byte operations. Because logical and arithmetic left shifts are
identical, there are no separate logical left shift operations. Logic shift left
(LSL) mnemonics are assembled as arithmetic shift left memory (ASL)
operations. Table 5-12 shows shift and rotate instructions.
Table 5-12. Shift and Rotate Instructions
Mnemonic
Function
Operation
Logical Shifts
LSL
LSLA
LSLB
Logic shift left memory
Logic shift left A
Logic shift left B
LSLD
Logic shift left D
LSR
LSRA
LSRB
Logic shift right memory
Logic shift right A
Logic shift right B
LSRD
Logic shift right D
0
C
b7
b7
A
b0
0
C
b0
B
b0
b0
C
b7
0
b7
0
b0
A
b7
b7
b0
B
C
Arithmetic Shifts
ASL
ASLA
ASLB
Arithmetic shift left memory
Arithmetic shift left A
Arithmetic shift left B
ASLD
Arithmetic shift left D
ASR
ASRA
ASRB
Arithmetic shift right memory
Arithmetic shift right A
Arithmetic shift right B
0
b0
b7
C
0
C
b0
b7 A
b7
B
b0
b0
C
b7
Rotates
ROL
ROLA
ROLB
Rotate left memory through carry
Rotate left A through carry
Rotate left B through carry
ROR
RORA
RORB
Rotate right memory through carry
Rotate right A through carry
Rotate right B through carry
S12CPUV2
MOTOROLA
b0
b7
C
b7
b0
C
Reference Manual
Instruction Set Overview
71
Instruction Set Overview
5.15 Fuzzy Logic Instructions
The CPU12 instruction set includes instructions that support efficient
processing of fuzzy logic operations. The descriptions of fuzzy logic
instructions given here are functional overviews. Table 5-13
summarizes the fuzzy logic instructions. Refer to Section 9. Fuzzy
Logic Support for detailed discussion.
5.15.1 Fuzzy Logic Membership Instruction
The membership function (MEM) instruction is used during the
fuzzification process. During fuzzification, current system input values
are compared against stored input membership functions to determine
the degree to which each label of each system input is true. This is
accomplished by finding the y value for the current input on a trapezoidal
membership function for each label of each system input. The MEM
instruction performs this calculation for one label of one system input. To
perform the complete fuzzification task for a system, several MEM
instructions must be executed, usually in a program loop structure.
5.15.2 Fuzzy Logic Rule Evaluation Instructions
The MIN-MAX rule evaluation (REV and REVW) instructions perform
MIN-MAX rule evaluations that are central elements of a fuzzy logic
inference program. Fuzzy input values are processed using a list of rules
from the knowledge base to produce a list of fuzzy outputs. The REV
instruction treats all rules as equally important. The REVW instruction
allows each rule to have a separate weighting factor. The two rule
evaluation instructions also differ in the way rules are encoded into the
knowledge base. Because they require a number of cycles to execute,
rule evaluation instructions can be interrupted. Once the interrupt has
been serviced, instruction execution resumes at the point the interrupt
occurred.
Reference Manual
72
S12CPUV2
Instruction Set Overview
MOTOROLA
Instruction Set Overview
Fuzzy Logic Instructions
5.15.3 Fuzzy Logic Weighted Average Instruction
The weighted average (WAV) instruction computes a sum-of-products
and a sum-of-weights used for defuzzification. To be usable, the fuzzy
outputs produced by rule evaluation must be defuzzified to produce a
single output value which represents the combined effect of all of the
fuzzy outputs. Fuzzy outputs correspond to the labels of a system output
and each is defined by a membership function in the knowledge base.
The CPU12 typically uses singletons for output membership functions
rather than the trapezoidal shapes used for inputs. As with inputs, the
x-axis represents the range of possible values for a system output.
Singleton membership functions consist of the x-axis position for a label
of the system output. Fuzzy outputs correspond to the y-axis height of
the corresponding output membership function. The WAV instruction
calculates the numerator and denominator sums for a weighted average
of the fuzzy outputs. Because WAV requires a number of cycles to
execute, it can be interrupted. The WAVR pseudo-instruction causes
execution to resume at the point where it was interrupted.
Table 5-13. Fuzzy Logic Instructions
Mnemonic
Function
Operation
µ (grade) ⇒ M(Y)
(X) + 4 ⇒ X; (Y) + 1 ⇒ Y; A unchanged
MEM
Membership
function
if (A) < P1 or (A) > P2, then µ = 0, else
µ = MIN [((A) – P1) × S1, (P2 – (A)) × S2, $FF]
where:
A = current crisp input value
X points to a 4-byte data structure
that describes a trapezoidal membership
function as base intercept
points and slopes (P1, P2, S1, S2)
Y points at fuzzy input (RAM location)
Continued on next page
S12CPUV2
MOTOROLA
Reference Manual
Instruction Set Overview
73
Instruction Set Overview
Table 5-13. Fuzzy Logic Instructions (Continued)
Mnemonic
Function
Operation
Find smallest rule input (MIN)
Store to rule outputs unless fuzzy output is
larger (MAX)
Rules are unweighted
REV
MIN-MAX rule
evaluation
Each rule input is an 8-bit offset
from a base address in Y
Each rule output is an 8-bit offset
from a base address in Y
$FE separates rule inputs from rule outputs
$FF terminates the rule list
REV can be interrupted
Find smallest rule input (MIN)
Multiply by a rule weighting factor (optional)
Store to rule outputs unless fuzzy output is
larger (MAX)
REVW
MIN-MAX rule
evaluation
Each rule input is the 16-bit address
of a fuzzy input
Each rule output is the 16-bit address
of a fuzzy output
Address $FFFE separates rule inputs
from rule outputs
$FFFF terminates the rule list
Weights are 8-bit values in a separate table
REVW can be interrupted
WAV
WAVR
Calculates numerator
(sum of products)
and denominator
(sum of weights)
for weighted average
calculation
Results are placed in
correct registers
for EDIV immediately
after WAV
Resumes execution
of interrupted WAV
instruction
Reference Manual
74
B
∑ Si Fi ⇒ Y:D
i=1
B
∑ Fi ⇒ X
i=1
Recover immediate results from stack
rather than initializing them to 0.
S12CPUV2
Instruction Set Overview
MOTOROLA
Instruction Set Overview
Maximum and Minimum Instructions
5.16 Maximum and Minimum Instructions
The maximum (MAX) and minimum (MIN) instructions are used to make
comparisons between an accumulator and a memory location. These
instructions can be used for linear programming operations, such as
simplex-method optimization, or for fuzzification.
MAX and MIN instructions use accumulator A to perform 8-bit
comparisons, while EMAX and EMIN instructions use accumulator D to
perform 16-bit comparisons. The result (maximum or minimum value)
can be stored in the accumulator (EMAXD, EMIND, MAXA, MINA) or the
memory address (EMAXM, EMINM, MAXM, MINM).
Table 5-14 is a summary of minimum and maximum instructions.
Table 5-14. Minimum and Maximum Instructions
Mnemonic
Function
Operation
Minimum Instructions
EMIND
MIN of two unsigned 16-bit values
result to accumulator
MIN ((D), (M : M + 1)) ⇒ D
EMINM
MIN of two unsigned 16-bit values
result to memory
MIN ((D), (M : M + 1)) ⇒ M : M+1
MINA
MIN of two unsigned 8-bit values
result to accumulator
MIN ((A), (M)) ⇒ A
MINM
MIN of two unsigned 8-bit values
result to memory
MIN ((A), (M)) ⇒ M
Maximum Instructions
EMAXD
MAX of two unsigned 16-bit values
result to accumulator
EMAXM
MAX of two unsigned 16-bit values
MAX ((D), (M : M + 1)) ⇒ M : M + 1
result to memory
MAXA
MAX of two unsigned 8-bit values
result to accumulator
MAX ((A), (M)) ⇒ A
MAXM
MAX of two unsigned 8-bit values
result to memory
MAX ((A), (M)) ⇒ M
S12CPUV2
MOTOROLA
MAX ((D), (M : M + 1)) ⇒ D
Reference Manual
Instruction Set Overview
75
Instruction Set Overview
5.17 Multiply and Accumulate Instruction
The multiply and accumulate (EMACS) instruction multiplies two 16-bit
operands stored in memory and accumulates the 32-bit result in a third
memory location. EMACS can be used to implement simple digital filters
and defuzzification routines that use 16-bit operands. The WAV
instruction incorporates an 8- to 16-bit multiply and accumulate
operation that obtains a numerator for the weighted average calculation.
The EMACS instruction can automate this portion of the averaging
operation when 16-bit operands are used. Table 5-15 shows the
EMACS instruction.
Table 5-15. Multiply and Accumulate Instructions
Mnemonic
Function
Operation
EMACS
Multiply and accumulate (signed)
16 bit by 16 bit ⇒ 32 bit
((M(X):M(X+1)) × (M(Y):M(Y+1)))
+ (M ~ M + 3) ⇒ M ~ M + 3
5.18 Table Interpolation Instructions
The table interpolation instructions (TBL and ETBL) interpolate values
from tables stored in memory. Any function that can be represented as
a series of linear equations can be represented by a table of appropriate
size. Interpolation can be used for many purposes, including tabular
fuzzy logic membership functions. TBL uses 8-bit table entries and
returns an 8-bit result; ETBL uses 16-bit table entries and returns a
16-bit result. Use of indexed addressing mode provides great flexibility
in structuring tables.
Consider each of the successive values stored in a table to be y-values
for the endpoint of a line segment. The value in the B accumulator before
instruction execution begins represents the change in x from the
beginning of the line segment to the lookup point divided by total change
in x from the beginning to the end of the line segment. B is treated as an
8-bit binary fraction with radix point left of the MSB, so each line segment
is effectively divided into 256 smaller segments. During instruction
execution, the change in y between the beginning and end of the
segment (a signed byte for TBL or a signed word for ETBL) is multiplied
by the content of the B accumulator to obtain an intermediate delta-y
term. The result (stored in the A accumulator by TBL, and in the D
Reference Manual
76
S12CPUV2
Instruction Set Overview
MOTOROLA
Instruction Set Overview
Branch Instructions
accumulator by ETBL) is the y-value of the beginning point plus the
signed intermediate delta-y value. Table 5-16 shows the table
interpolation instructions.
Table 5-16. Table Interpolation Instructions
Mnemonic
Function
Operation
ETBL
16-bit table lookup
and interpolate
(no indirect addressing
modes allowed)
(M : M + 1) + [(B) × ((M + 2 : M + 3)
– (M : M + 1))] ⇒ D
Initialize B, and index before ETBL.
<ea> points to the first table entry (M : M + 1)
B is fractional part of lookup value
TBL
8-bit table lookup
and interpolate
(no indirect addressing
modes allowed)
(M) + [(B) × ((M + 1) – (M))] ⇒ A
Initialize B, and index before TBL.
<ea> points to the first 8-bit table entry (M)
B is fractional part of lookup value.
5.19 Branch Instructions
Branch instructions cause a sequence to change when specific
conditions exist. The CPU12 uses three kinds of branch instructions.
These are short branches, long branches, and bit condition branches.
Branch instructions can also be classified by the type of condition that
must be satisfied in order for a branch to be taken. Some instructions
belong to more than one classification. For example:
•
Unary branch instructions always execute.
•
Simple branches are taken when a specific bit in the condition
code register is in a specific state as a result of a previous
operation.
•
Unsigned branches are taken when comparison or test of
unsigned quantities results in a specific combination of condition
code register bits.
•
Signed branches are taken when comparison or test of signed
quantities results in a specific combination of condition code
register bits.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Set Overview
77
Instruction Set Overview
5.19.1 Short Branch Instructions
Short branch instructions operate this way: When a specified condition
is met, a signed 8-bit offset is added to the value in the program counter.
Program execution continues at the new address.
The numeric range of short branch offset values is $80 (–128) to $7F
(127) from the address of the next memory location after the offset value.
Table 5-17 is a summary of the short branch instructions.
Table 5-17. Short Branch Instructions
Mnemonic
Function
Equation or Operation
Unary Branches
BRA
Branch always
1=1
BRN
Branch never
1=0
Simple Branches
BCC
Branch if carry clear
C=0
BCS
Branch if carry set
C=1
BEQ
Branch if equal
Z=1
BMI
Branch if minus
N=1
BNE
Branch if not equal
Z=0
BPL
Branch if plus
N=0
BVC
Branch if overflow clear
V=0
BVS
Branch if overflow set
V=1
Unsigned Branches
Relation
BHI
Branch if higher
R>M
C+Z=0
BHS
Branch if higher or same
R≥M
C=0
BLO
Branch if lower
R<M
C=1
BLS
Branch if lower or same
R≤M
C+Z=1
Signed Branches
BGE
Branch if greater than or equal
R≥M
N⊕V=0
BGT
Branch if greater than
R>M
Z + (N ⊕ V) = 0
BLE
Branch if less than or equal
R≤M
Z + (N ⊕ V) = 1
BLT
Branch if less than
R<M
N⊕V=1
Reference Manual
78
S12CPUV2
Instruction Set Overview
MOTOROLA
Instruction Set Overview
Branch Instructions
5.19.2 Long Branch Instructions
Long branch instructions operate this way: When a specified condition is
met, a signed 16-bit offset is added to the value in the program counter.
Program execution continues at the new address. Long branches are
used when large displacements between decision-making steps are
necessary.
The numeric range of long branch offset values is $8000 (–32,768) to
$7FFF (32,767) from the address of the next memory location after the
offset value. This permits branching from any location in the standard
64-Kbyte address map to any other location in the 64-Kbyte map.
Table 5-18 is a summary of the long branch instructions.
Table 5-18. Long Branch Instructions
Mnemonic
Function
Equation or Operation
Unary Branches
LBRA
Long branch always
1=1
LBRN
Long branch never
1=0
Simple Branches
LBCC
Long branch if carry clear
C=0
LBCS
Long branch if carry set
C=1
LBEQ
Long branch if equal
Z=1
LBMI
Long branch if minus
N=1
LBNE
Long branch if not equal
Z=0
LBPL
Long branch if plus
N=0
LBVC
Long branch if overflow clear
V=0
LBVS
Long branch if overflow set
V=1
Unsigned Branches
LBHI
Long branch if higher
C+Z=0
LBHS
Long branch if higher or same
C=0
LBLO
Long branch if lower
Z=1
LBLS
Long branch if lower or same
C+Z=1
Signed Branches
LBGE
Long branch if greater than or equal
N⊕V=0
LBGT
Long branch if greater than
Z + (N ⊕ V) = 0
LBLE
Long branch if less than or equal
Z + (N ⊕ V) = 1
LBLT
Long branch if less than
N⊕V=1
S12CPUV2
MOTOROLA
Reference Manual
Instruction Set Overview
79
Instruction Set Overview
5.19.3 Bit Condition Branch Instructions
The bit condition branches are taken when bits in a memory byte are in
a specific state. A mask operand is used to test the location. If all bits in
that location that correspond to ones in the mask are set (BRSET) or
cleared (BRCLR), the branch is taken.
The numeric range of 8-bit offset values is $80 (–128) to $7F (127)
from the address of the next memory location after the offset value.
Table 5-19 is a summary of bit condition branches.
Table 5-19. Bit Condition Branch Instructions
Mnemonic
Function
Equation or Operation
BRCLR
Branch if selected bits clear
(M) • (mm) = 0
BRSET
Branch if selected bits set
(M) • (mm) = 0
Reference Manual
80
S12CPUV2
Instruction Set Overview
MOTOROLA
Instruction Set Overview
Loop Primitive Instructions
5.20 Loop Primitive Instructions
The loop primitives can also be thought of as counter branches. The
instructions test a counter value in a register or accumulator (A, B, D, X,
Y, or SP) for zero or non-zero value as a branch condition. There are
predecrement, preincrement, and test-only versions of these
instructions.
The numeric range of 9-bit offset values is $100 (–256) to $0FF (255)
from the address of the next memory location after the offset value.
Table 5-20 is a summary of loop primitive branches.
Table 5-20. Loop Primitive Instructions
Mnemonic
Function
Equation or Operation
DBEQ
Decrement counter and branch if = 0
(counter = A, B, D, X, Y, or SP)
(counter) – 1⇒ counter
If (counter) = 0, then branch;
else continue to next instruction
DBNE
(counter) – 1⇒ counter
Decrement counter and branch if ≠ 0
If (counter) not = 0, then branch;
(counter = A, B, D, X, Y, or SP)
else continue to next instruction
IBEQ
Increment counter and branch if = 0
(counter = A, B, D, X, Y, or SP)
(counter) + 1⇒ counter
If (counter) = 0, then branch;
else continue to next instruction
IBNE
Increment counter and branch if ≠ 0
(counter = A, B, D, X, Y, or SP)
(counter) + 1⇒ counter
If (counter) not = 0, then branch;
else continue to next instruction
TBEQ
Test counter and branch if = 0
(counter = A, B, D, X,Y, or SP)
If (counter) = 0, then branch;
else continue to next instruction
TBNE
Test counter and branch if ≠ 0
(counter = A, B, D, X,Y, or SP)
If (counter) not = 0, then branch;
else continue to next instruction
S12CPUV2
MOTOROLA
Reference Manual
Instruction Set Overview
81
Instruction Set Overview
5.21 Jump and Subroutine Instructions
Jump (JMP) instructions cause immediate changes in sequence. The
JMP instruction loads the PC with an address in the 64-Kbyte memory
map, and program execution continues at that address. The address can
be provided as an absolute 16-bit address or determined by various
forms of indexed addressing.
Subroutine instructions optimize the process of transferring control to a
code segment that performs a particular task. A short branch (BSR),
a jump to subroutine (JSR), or an expanded-memory call (CALL) can be
used to initiate subroutines. There is no LBSR instruction, but a
PC-relative JSR performs the same function. A return address is
stacked, then execution begins at the subroutine address. Subroutines
in the normal 64-Kbyte address space are terminated with a
return-from-subroutine (RTS) instruction. RTS unstacks the return
address so that execution resumes with the instruction after BSR
or JSR.
The call subroutine in expanded memory (CALL) instruction is intended
for use with expanded memory. CALL stacks the value in the PPAGE
register and the return address, then writes a new value to PPAGE to
select the memory page where the subroutine resides. The page value
is an immediate operand in all addressing modes except indexed
indirect modes; in these modes, an operand points to locations in
memory where the new page value and subroutine address are stored.
The return from call (RTC) instruction is used to terminate subroutines in
expanded memory. RTC unstacks the PPAGE value and the return
address so that execution resumes with the next instruction after CALL.
For software compatibility, CALL and RTC execute correctly on devices
that do not have expanded addressing capability. Table 5-21
summarizes the jump and subroutine instructions.
Reference Manual
82
S12CPUV2
Instruction Set Overview
MOTOROLA
Instruction Set Overview
Interrupt Instructions
Table 5-21. Jump and Subroutine Instructions
Mnemonic
Function
Operation
Branch to subroutine
SP – 2 ⇒ SP
RTNH : RTNL ⇒ M(SP) : M(SP+1)
Subroutine address ⇒ PC
CALL
Call subroutine
in expanded memory
SP – 2 ⇒ SP
RTNH:RTNL⇒ M(SP) : M(SP+1)
SP – 1 ⇒ SP
(PPAGE) ⇒ M(SP)
Page ⇒ PPAGE
Subroutine address ⇒ PC
JMP
Jump
Address ⇒ PC
Jump to subroutine
SP – 2 ⇒ SP
RTNH : RTNL⇒ M(SP) : M(SP+1)
Subroutine address ⇒ PC
RTC
Return from call
M(SP) ⇒ PPAGE
SP + 1 ⇒ SP
M(SP) : M(SP+1) ⇒ PCH : PCL
SP + 2 ⇒ SP
RTS
Return from subroutine
M(SP) : M(SP+1) ⇒ PCH : PCL
SP + 2 ⇒ SP
BSR
JSR
5.22 Interrupt Instructions
Interrupt instructions handle transfer of control to a routine that performs
a critical task. Software interrupts are a type of exception. Section 7.
Exception Processing covers interrupt exception processing in detail.
The software interrupt (SWI) instruction initiates synchronous exception
processing. First, the return PC value is stacked. After CPU context is
stacked, execution continues at the address pointed to by the SWI
vector.
Execution of the SWI instruction causes an interrupt without an interrupt
service request. SWI is not inhibited by global mask bits I and X in the
CCR, and execution of SWI sets the I mask bit. Once an SWI interrupt
begins, maskable interrupts are inhibited until the I bit in the CCR is
cleared. This typically occurs when a return from interrupt (RTI)
instruction at the end of the SWI service routine restores context.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Set Overview
83
Instruction Set Overview
The CPU12 uses a variation of the software interrupt for unimplemented
opcode trapping. There are opcodes in all 256 positions in the page 1
opcode map, but only 54 of the 256 positions on page 2 of the opcode
map are used. If the CPU attempts to execute one of the unimplemented
opcodes on page 2, an opcode trap interrupt occurs. Traps are
essentially interrupts that share the $FFF8:$FFF9 interrupt vector.
The RTI instruction is used to terminate all exception handlers, including
interrupt service routines. RTI first restores the CCR, B:A, X, Y, and the
return address from the stack. If no other interrupt is pending, normal
execution resumes with the instruction following the last instruction that
executed prior to interrupt.
Table 5-22 is a summary of interrupt instructions.
Table 5-22. Interrupt Instructions
Mnemonic
RTI
SWI
TRAP
Function
Operation
Return
from interrupt
(M(SP)) ⇒ CCR; (SP) + $0001 ⇒ SP
(M(SP) : M(SP+1)) ⇒ B : A; (SP) + $0002 ⇒ SP
(M(SP) : M(SP+1)) ⇒ XH : XL; (SP) + $0004 ⇒ SP
(M(SP) : M(SP+1)) ⇒ PCH : PCL; (SP) + $0002 ⇒ SP
(M(SP) : M(SP+1)) ⇒ YH : YL; (SP) + $0004 ⇒ SP
Software interrupt
SP – 2 ⇒ SP; RTNH : RTNL ⇒ M(SP) : M(SP+1)
SP – 2 ⇒ SP; YH : YL ⇒ M(SP) : M(SP+1)
SP – 2 ⇒ SP; XH : XL ⇒ M(SP) : M(SP+1)
SP – 2 ⇒ SP; B : A ⇒ M(SP) : M(SP+1)
SP – 1 ⇒ SP; CCR ⇒ M(SP)
Unimplemented
opcode interrupt
SP – 2 ⇒ SP; RTNH : RTNL ⇒ M(SP) : M(SP+1)
SP – 2 ⇒ SP; YH : YL ⇒ M(SP) : M(SP+1)
SP – 2 ⇒ SP; XH : XL ⇒ M(SP) : M(SP+1)
SP – 2 ⇒ SP; B : A ⇒ M(SP) : M(SP+1)
SP – 1 ⇒ SP; CCR ⇒ M(SP)
Reference Manual
84
S12CPUV2
Instruction Set Overview
MOTOROLA
Instruction Set Overview
Index Manipulation Instructions
5.23 Index Manipulation Instructions
The index manipulation instructions perform 8- and 16-bit operations on
the three index registers and accumulators, other registers, or memory,
as shown in Table 5-23.
Table 5-23. Index Manipulation Instructions
Mnemonic
Function
Operation
Addition Instructions
ABX
Add B to X
(B) + (X) ⇒ X
ABY
Add B to Y
(B) + (Y) ⇒ Y
Compare Instructions
CPS
Compare SP to memory
(SP) – (M : M + 1)
CPX
Compare X to memory
(X) – (M : M + 1)
CPY
Compare Y to memory
(Y) – (M : M + 1)
Load Instructions
LDS
Load SP from memory
M : M+1 ⇒ SP
LDX
Load X from memory
(M : M + 1) ⇒ X
LDY
Load Y from memory
(M : M + 1) ⇒ Y
LEAS
Load effective address into SP
Effective address ⇒ SP
LEAX
Load effective address into X
Effective address ⇒ X
LEAY
Load effective address into Y
Effective address ⇒ Y
Store Instructions
STS
Store SP in memory
(SP) ⇒ M:M+1
STX
Store X in memory
(X) ⇒ M : M + 1
STY
Store Y in memory
(Y) ⇒ M : M + 1
Transfer Instructions
TFR
Transfer register to register
(A, B, CCR, D, X, Y, or SP)
⇒ A, B, CCR, D, X, Y, or SP
TSX
Transfer SP to X
(SP) ⇒ X
TSY
Transfer SP to Y
(SP) ⇒ Y
TXS
transfer X to SP
(X) ⇒ SP
TYS
transfer Y to SP
(Y) ⇒ SP
Exchange Instructions
EXG
Exchange register to register
(A, B, CCR, D, X, Y, or SP)
⇔ (A, B, CCR, D, X, Y, or SP)
XGDX
EXchange D with X
(D) ⇔ (X)
XGDY
EXchange D with Y
(D) ⇔ (Y)
S12CPUV2
MOTOROLA
Reference Manual
Instruction Set Overview
85
Instruction Set Overview
5.24 Stacking Instructions
The two types of stacking instructions, are shown in Table 5-24. Stack
pointer instructions use specialized forms of mathematical and data
transfer instructions to perform stack pointer manipulation. Stack
operation instructions save information on and retrieve information from
the system stack.
Table 5-24. Stacking Instructions
Mnemonic
Function
Operation
Stack Pointer Instructions
CPS
Compare SP to memory
(SP) – (M : M + 1)
DES
Decrement SP
(SP) – 1 ⇒ SP
INS
Increment SP
(SP) + 1 ⇒ SP
LDS
Load SP
(M : M + 1) ⇒ SP
LEAS
Load effective address
into SP
Effective address ⇒ SP
STS
Store SP
(SP) ⇒ M : M + 1
TSX
Transfer SP to X
(SP) ⇒ X
TSY
Transfer SP to Y
(SP) ⇒ Y
TXS
Transfer X to SP
(X) ⇒ SP
TYS
Transfer Y to SP
(Y) ⇒ SP
Stack Operation Instructions
PSHA
Push A
(SP) – 1 ⇒ SP; (A) ⇒ M(SP)
PSHB
Push B
(SP) – 1 ⇒ SP; (B) ⇒ M(SP)
PSHC
Push CCR
(SP) – 1 ⇒ SP; (A) ⇒ M(SP)
PSHD
Push D
(SP) – 2 ⇒ SP; (A : B) ⇒ M(SP) : M(SP+1)
PSHX
Push X
(SP) – 2 ⇒ SP; (X) ⇒ M(SP) : M(SP+1)
PSHY
Push Y
(SP) – 2 ⇒ SP; (Y) ⇒ M(SP) : M(SP+1)
PULA
Pull A
(M(SP)) ⇒ A; (SP) + 1 ⇒ SP
PULB
Pull B
(M(SP)) ⇒ B; (SP) + 1 ⇒ SP
PULC
Pull CCR
(M(SP)) ⇒ CCR; (SP) + 1 ⇒ SP
PULD
Pull D
(M(SP) : M(SP+1)) ⇒ A : B; (SP) + 2 ⇒ SP
PULX
Pull X
(M(SP) : M(SP+1)) ⇒ X; (SP) + 2 ⇒ SP
PULY
Pull Y
(M(SP) : M(SP+1)) ⇒ Y; (SP) + 2 ⇒ SP
Reference Manual
86
S12CPUV2
Instruction Set Overview
MOTOROLA
Instruction Set Overview
Pointer and Index Calculation Instructions
5.25 Pointer and Index Calculation Instructions
The load effective address instructions allow 5-, 8-, or 16-bit constants
or the contents of 8-bit accumulators A and B or 16-bit accumulator D to
be added to the contents of the X and Y index registers, or to the SP.
Table 5-25 is a summary of pointer and index instructions.
Table 5-25. Pointer and Index Calculation Instructions
Mnemonic
Function
Operation
LEAS
Load result of indexed addressing mode
effective address calculation
into stack pointer
r ± constant ⇒ SP or
(r) + (accumulator) ⇒ SP
r = X, Y, SP, or PC
LEAX
Load result of indexed addressing mode
effective address calculation
into x index register
r ± constant ⇒X or
(r) + (accumulator) ⇒X
r = X, Y, SP, or PC
LEAY
Load result of indexed addressing mode
effective address calculation
into y index register
r ± constant ⇒Y or
(r) + (accumulator) ⇒ Y
r = X, Y, SP, or PC
S12CPUV2
MOTOROLA
Reference Manual
Instruction Set Overview
87
Instruction Set Overview
5.26 Condition Code Instructions
Condition code instructions are special forms of mathematical and data
transfer instructions that can be used to change the condition code
register. Table 5-26 shows instructions that can be used to manipulate
the CCR.
Table 5-26. Condition Code Instructions
Mnemonic
Function
Operation
ANDCC
Logical AND CCR with memory
(CCR) • (M) ⇒ CCR
CLC
Clear C bit
0⇒C
CLI
Clear I bit
0⇒I
CLV
Clear V bit
0⇒V
ORCC
Logical OR CCR with memory
(CCR) + (M) ⇒ CCR
PSHC
Push CCR onto stack
(SP) – 1 ⇒ SP; (CCR) ⇒ M(SP)
PULC
Pull CCR from stack
(M(SP)) ⇒ CCR; (SP) + 1 ⇒ SP
SEC
Set C bit
1⇒C
SEI
Set I bit
1⇒I
SEV
Set V bit
1⇒V
TAP
Transfer A to CCR
(A) ⇒ CCR
TPA
Transfer CCR to A
(CCR) ⇒ A
Reference Manual
88
S12CPUV2
Instruction Set Overview
MOTOROLA
Instruction Set Overview
Stop and Wait Instructions
5.27 Stop and Wait Instructions
As shown in Table 5-27, two instructions put the CPU12 in an inactive
state that reduces power consumption.
The stop instruction (STOP) stacks a return address and the contents of
CPU registers and accumulators, then halts all system clocks.
The wait instruction (WAI) stacks a return address and the contents of
CPU registers and accumulators, then waits for an interrupt service
request; however, system clock signals continue to run.
Both STOP and WAI require that either an interrupt or a reset exception
occur before normal execution of instructions resumes. Although both
instructions require the same number of clock cycles to resume normal
program execution after an interrupt service request is made, restarting
after a STOP requires extra time for the oscillator to reach operating
speed.
Table 5-27. Stop and Wait Instructions
Mnemonic
STOP
WAI
Function
Operation
Stop
SP – 2 ⇒ SP; RTNH : RTNL ⇒ M(SP) : M(SP+1)
SP – 2 ⇒ SP; YH : YL ⇒ M(SP) : M(SP+1)
SP – 2 ⇒ SP; XH : XL ⇒ M(SP) : M(SP+1)
SP – 2 ⇒ SP; B : A ⇒ M(SP) : M(SP+1)
SP – 1 ⇒ SP; CCR ⇒ M(SP)
Stop CPU clocks
Wait for interrupt
SP – 2 ⇒ SP; RTNH : RTNL ⇒ M(SP) : M(SP+1)
SP – 2 ⇒ SP; YH : YL ⇒ M(SP) : M(SP+1)
SP – 2 ⇒ SP; XH : XL ⇒ M(SP) : M(SP+1)
SP – 2 ⇒ SP; B : A ⇒ M(SP) : M(SP+1)
SP – 1 ⇒ SP; CCR ⇒ M(SP)
S12CPUV2
MOTOROLA
Reference Manual
Instruction Set Overview
89
Instruction Set Overview
5.28 Background Mode and Null Operations
Background debug mode (BDM) is a special CPU12 operating mode
that is used for system development and debugging. Executing enter
background debug mode (BGND) when BDM is enabled puts the
CPU12 in this mode. For complete information, refer to Section 8.
Instruction Queue.
Null operations are often used to replace other instructions during
software debugging. Replacing conditional branch instructions with
branch never (BRN), for instance, permits testing a decision-making
routine by disabling the conditional branch without disturbing the offset
value.
Null operations can also be used in software delay programs to consume
execution time without disturbing the contents of other CPU registers or
memory.
Table 5-28 shows the BGND and null operation (NOP) instructions.
Table 5-28. Background Mode and Null Operation Instructions
Mnemonic
Function
Operation
BGND
Enter background debug mode
If BDM enabled, enter BDM;
else resume normal processing
BRN
Branch never
Does not branch
LBRN
Long branch never
Does not branch
NOP
Null operation
—
Reference Manual
90
S12CPUV2
Instruction Set Overview
MOTOROLA
Reference Manual — S12CPUV2
Section 6. Instruction Glossary
6.1 Introduction
This section is a comprehensive reference to the CPU12 instruction set.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
91
Instruction Glossary
6.2 Glossary Information
The glossary contains an entry for each assembler mnemonic, in
alphabetic order. Figure 6-1 is a representation of a glossary page.
MNEMONIC
LDX
Operation:
SYMBOLIC DESCRIPTION
OF OPERATION
Description:
DETAILED DESCRIPTION
OF OPERATION
CCR Details:
Load Index Regi
(M : M+1) ⇒ X
Loads the most significa
memory at the addres
content of the next b
S
X
H
—
—
—
N: Set if MSB of resu
Z: Set if result is $00
V: 0; Cleared.
EFFECT ON
CONDITION CODE REGISTER
STATUS BITS
Source Form
DETAILED SYNTAX
AND CYCLE-BY-CYCLE
OPERATION
LDX #opr16i
LDX opr8a
LDX opr16a
LDX oprx0_xysp
LDX oprx9,xysp
LDX oprx16,xysp
LDX [D,xysp]
LDX [oprx16,xysp]
Address Mode
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
CE jj
DE dd
FE hh
EE xb
EE xb
EE xb
EE xb
EE xb
Figure 6-1. Example Glossary Page
Each entry contains symbolic and textual descriptions of operation,
information concerning the effect of operation on status bits in the
condition code register, and a table that describes assembler syntax,
address mode variations, and cycle-by-cycle execution of the
instruction.
Reference Manual
92
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Condition Code Changes
6.3 Condition Code Changes
The following special characters are used to describe the effects of
instruction execution on the status bits in the condition code register.
– — Status bit not affected by operation
0 — Status bit cleared by operation
1 — Status bit set by operation
∆ — Status bit affected by operation
⇓ — Status bit may be cleared or remain set, but is not set
by operation.
⇑ — Status bit may be set or remain cleared, but is not
cleared by operation.
? — Status bit may be changed by operation, but the final
state is not defined.
! — Status bit used for a special purpose
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
93
Instruction Glossary
6.4 Object Code Notation
The digits 0 to 9 and the uppercase letters A to F are used to express
hexadecimal values. Pairs of lowercase letters represent the 8-bit values
as described here.
dd — 8-bit direct address $0000 to $00FF; high byte
assumed to be $00
ee — High-order byte of a 16-bit constant offset for indexed
addressing
eb — Exchange/transfer post-byte
ff — Low-order eight bits of a 9-bit signed constant offset
for indexed addressing, or low-order byte of a 16-bit
constant offset for indexed addressing
hh — High-order byte of a 16-bit extended address
ii — 8-bit immediate data value
jj — High-order byte of a 16-bit immediate data value
kk — Low-order byte of a 16-bit immediate data value
lb — Loop primitive (DBNE) post-byte
ll — Low-order byte of a 16-bit extended address
mm — 8-bit immediate mask value for bit manipulation
instructions; set bits indicate bits to be affected
pg — Program overlay page (bank) number used in CALL
instruction
qq — High-order byte of a 16-bit relative offset for long
branches
tn — Trap number $30–$39 or $40–$FF
rr — Signed relative offset $80 (–128) to $7F (+127)
offset relative to the byte following the relative offset
byte, or low-order byte of a 16-bit relative offset for
long branches
xb — Indexed addressing post-byte
Reference Manual
94
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Source Forms
6.5 Source Forms
The glossary pages provide only essential information about assembler
source forms. Assemblers generally support a number of assembler
directives, allow definition of program labels, and have special
conventions for comments. For complete information about writing
source files for a particular assembler, refer to the documentation
provided by the assembler vendor.
Assemblers are typically flexible about the use of spaces and tabs.
Often, any number of spaces or tabs can be used where a single space
is shown on the glossary pages. Spaces and tabs are also normally
allowed before and after commas. When program labels are used, there
must also be at least one tab or space before all instruction mnemonics.
This required space is not apparent in the source forms.
Everything in the source forms columns, except expressions in italic
characters, is literal information which must appear in the assembly
source file exactly as shown. The initial 3- to 5-letter mnemonic is always
a literal expression. All commas, pound signs (#), parentheses, square
brackets ( [ or ] ), plus signs (+), minus signs (–), and the register
designation D (as in [D,... ), are literal characters.
Groups of italic characters in the columns represent variable information
to be supplied by the programmer. These groups can include any
alphanumeric character or the underscore character, but cannot include
a space or comma. For example, the groups xysp and oprx0_xysp are
both valid, but the two groups oprx0 xysp are not valid because there is
a space between them. Permitted syntax is described here.
The definition of a legal label or expression varies from assembler to
assembler. Assemblers also vary in the way CPU registers are specified.
Refer to assembler documentation for detailed information.
Recommended register designators are a, A, b, B, ccr, CCR, d, D, x, X,
y, Y, sp, SP, pc, and PC.
abc — Any one legal register designator for accumulators A or
B or the CCR
abcdxys — Any one legal register designator for accumulators A or
B, the CCR, the double accumulator D, index registers X
or Y, or the SP. Some assemblers may accept t2, T2, t3,
or T3 codes in certain cases of transfer and exchange
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
95
Instruction Glossary
instructions, but these forms are intended for Motorola
use only.
abd — Any one legal register designator for accumulators A or
B or the double accumulator D
abdxys — Any one legal register designator for accumulators A or
B, the double accumulator D, index register X or Y, or the
SP
dxys — Any one legal register designation for the double
accumulator D, index registers X or Y, or the SP
msk8 — Any label or expression that evaluates to an 8-bit value.
Some assemblers require a # symbol before this value.
opr8i — Any label or expression that evaluates to an 8-bit
immediate value
opr16i — Any label or expression that evaluates to a 16-bit
immediate value
opr8a — Any label or expression that evaluates to an 8-bit value.
The instruction treats this 8-bit value as the low-order 8
bits of an address in the direct page of the 64-Kbyte
address space ($00xx).
opr16a — Any label or expression that evaluates to a 16-bit value.
The instruction treats this value as an address in the
64-Kbyte address space.
oprx0_xysp — This word breaks down into one of the following
alternative forms that assemble to an 8-bit indexed
addressing postbyte code. These forms generate the
same object code except for the value of the postbyte
code, which is designated as xb in the object code
columns of the glossary pages. As with the source
forms, treat all commas, plus signs, and minus signs as
literal syntax elements. The italicized words used in
these forms are included in this key.
oprx5,xysp
oprx3,–xys
oprx3,+xys
oprx3,xys–
oprx3,xys+
abd,xysp
Reference Manual
96
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Source Forms
oprx3 — Any label or expression that evaluates to a value in the
range +1 to +8
oprx5 — Any label or expression that evaluates to a 5-bit value in
the range –16 to +15
oprx9 — Any label or expression that evaluates to a 9-bit value in
the range –256 to +255
oprx16 — Any label or expression that evaluates to a 16-bit value.
Since the CPU12 has a 16-bit address bus, this can be
either a signed or an unsigned value.
page — Any label or expression that evaluates to an 8-bit value.
The CPU12 recognizes up to an 8-bit page value for
memory expansion but not all MCUs that include the
CPU12 implement all of these bits. It is the
programmer’s responsibility to limit the page value to
legal values for the intended MCU system. Some
assemblers require a # symbol before this value.
rel8 — Any label or expression that refers to an address that is
within –128 to +127 locations from the next address after
the last byte of object code for the current instruction.
The assembler will calculate the 8-bit signed offset and
include it in the object code for this instruction.
rel9 — Any label or expression that refers to an address that is
within –256 to +255 locations from the next address after
the last byte of object code for the current instruction.
The assembler will calculate the 9-bit signed offset and
include it in the object code for this instruction. The sign
bit for this 9-bit value is encoded by the assembler as a
bit in the looping postbyte (lb) of one of the loop control
instructions DBEQ, DBNE, IBEQ, IBNE, TBEQ, or
TBNE. The remaining eight bits of the offset are included
as an extra byte of object code.
rel16 — Any label or expression that refers to an address
anywhere in the 64-Kbyte address space. The
assembler will calculate the 16-bit signed offset between
this address and the next address after the last byte of
object code for this instruction and include it in the object
code for this instruction.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
97
Instruction Glossary
trapnum — Any label or expression that evaluates to an 8-bit
number in the range $30–$39 or $40–$FF. Used for
TRAP instruction.
xys — Any one legal register designation for index registers X
or Y or the SP
xysp — Any one legal register designation for index registers X
or Y, the SP, or the PC. The reference point for
PC-relative instructions is the next address after the last
byte of object code for the current instruction.
6.6 Cycle-by-Cycle Execution
This information is found in the tables at the bottom of each instruction
glossary page. Entries show how many bytes of information are
accessed from different areas of memory during the course of instruction
execution. With this information and knowledge of the type and speed of
memory in the system, a user can determine the execution time for any
instruction in any system.
A single letter code in the column represents a single CPU cycle.
Uppercase letters indicate 16-bit access cycles. There are cycle codes
for each addressing mode variation of each instruction. Simply count
code letters to determine the execution time of an instruction in a
best-case system. An example of a best-case system is a single-chip
16-bit system with no 16-bit off-boundary data accesses to any locations
other than on-chip RAM.
Many conditions can cause one or more instruction cycles to be
stretched, but the CPU is not aware of the stretch delays because the
clock to the CPU is temporarily stopped during these delays.
The following paragraphs explain the cycle code letters used and note
conditions that can cause each type of cycle to be stretched.
f — Free cycle. This indicates a cycle where the CPU
does not require use of the system buses. An f cycle
is always one cycle of the system bus clock. These
cycles can be used by a queue controller or the
background debug system to perform single cycle
accesses without disturbing the CPU.
Reference Manual
98
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Cycle-by-Cycle Execution
g — Read 8-bit PPAGE register. These cycles are used
only with the CALL instruction to read the current
value of the PPAGE register and are not visible on the
external bus. Since the PPAGE register is an internal
8-bit register, these cycles are never stretched.
I — Read indirect pointer. Indexed indirect instructions
use this 16-bit pointer from memory to address the
operand for the instruction. These are always 16-bit
reads but they can be either aligned or misaligned.
These cycles are extended to two bus cycles if the
MCU is operating with an 8-bit external data bus and
the corresponding data is stored in external memory.
There can be additional stretching when the address
space is assigned to a chip-select circuit programmed
for slow memory. These cycles are also stretched if
they correspond to misaligned access to a memory
that is not designed for single-cycle misaligned
access.
i — Read indirect PPAGE value. These cycles are only
used with indexed indirect versions of the CALL
instruction, where the 8-bit value for the memory
expansion page register of the CALL destination is
fetched from an indirect memory location. These
cycles are stretched only when controlled by a
chip-select circuit that is programmed for slow
memory.
n — Write 8-bit PPAGE register. These cycles are used
only with the CALL and RTC instructions to write the
destination value of the PPAGE register and are not
visible on the external bus. Since the PPAGE register
is an internal 8-bit register, these cycles are never
stretched.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
99
Instruction Glossary
O — Optional cycle. Program information is always fetched
as aligned 16-bit words. When an instruction consists
of an odd number of bytes, and the first byte is
misaligned, an O cycle is used to make an additional
program word access (P) cycle that maintains queue
order. In all other cases, the O cycle appears as a free
(f) cycle. The $18 prebyte for page two opcodes is
treated as a special 1-byte instruction. If the prebyte is
misaligned, the O cycle is used as a program word
access for the prebyte; if the prebyte is aligned, the O
cycle appears as a free cycle. If the remainder of the
instruction consists of an odd number of bytes,
another O cycle is required some time before the
instruction is completed. If the O cycle for the prebyte
is treated as a P cycle, any subsequent O cycle in the
same instruction is treated as an f cycle; if the O cycle
for the prebyte is treated as an f cycle, any
subsequent O cycle in the same instruction is treated
as a P cycle. Optional cycles used for program word
accesses can be extended to two bus cycles if the
MCU is operating with an 8-bit external data bus and
the program is stored in external memory. There can
be additional stretching when the address space is
assigned to a chip-select circuit programmed for slow
memory. Optional cycles used as free cycles are
never stretched.
P — Program word access. Program information is fetched
as aligned 16-bit words. These cycles are extended to
two bus cycles if the MCU is operating with an 8-bit
external data bus and the program is stored
externally. There can be additional stretching when
the address space is assigned to a chip-select circuit
programmed for slow memory.
r — 8-bit data read. These cycles are stretched only when
controlled by a chip-select circuit programmed for
slow memory.
Reference Manual
100
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Cycle-by-Cycle Execution
R — 16-bit data read. These cycles are extended to two
bus cycles if the MCU is operating with an 8-bit
external data bus and the corresponding data is
stored in external memory. There can be additional
stretching when the address space is assigned to a
chip-select circuit programmed for slow memory.
These cycles are also stretched if they correspond to
misaligned accesses to memory that is not designed
for single-cycle misaligned access.
s — Stack 8-bit data. These cycles are stretched only
when controlled by a chip-select circuit programmed
for slow memory.
S — Stack 16-bit data. These cycles are extended to two
bus cycles if the MCU is operating with an 8-bit
external data bus and the SP is pointing to external
memory. There can be additional stretching if the
address space is assigned to a chip-select circuit
programmed for slow memory. These cycles are also
stretched if they correspond to misaligned accesses
to a memory that is not designed for single cycle
misaligned access. The internal RAM is designed to
allow single cycle misaligned word access.
w — 8-bit data write. These cycles are stretched only when
controlled by a chip-select circuit programmed for
slow memory.
W — 16-bit data write. These cycles are extended to two
bus cycles if the MCU is operating with an 8-bit
external data bus and the corresponding data is
stored in external memory. There can be additional
stretching when the address space is assigned to a
chip-select circuit programmed for slow memory.
These cycles are also stretched if they correspond to
misaligned access to a memory that is not designed
for single-cycle misaligned access.
u — Unstack 8-bit data. These cycles are stretched only
when controlled by a chip-select circuit programmed
for slow memory.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
101
Instruction Glossary
U — Unstack 16-bit data. These cycles are extended to
two bus cycles if the MCU is operating with an 8-bit
external data bus and the SP is pointing to external
memory. There can be additional stretching when the
address space is assigned to a chip-select circuit
programmed for slow memory. These cycles are also
stretched if they correspond to misaligned accesses
to a memory that is not designed for single-cycle
misaligned access. The internal RAM is designed to
allow single-cycle misaligned word access.
V — Vector fetch. Vectors are always aligned 16-bit words.
These cycles are extended to two bus cycles if the
MCU is operating with an 8-bit external data bus and
the program is stored in external memory. There can
be additional stretching when the address space is
assigned to a chip-select circuit programmed for slow
memory.
t — 8-bit conditional read. These cycles are either data
read cycles or unused cycles, depending on the data
and flow of the REVW instruction. These cycles are
stretched only when controlled by a chip-select circuit
programmed for slow memory.
T — 16-bit conditional read. These cycles are either data
read cycles or free cycles, depending on the data and
flow of the REV or REVW instruction. These cycles
are extended to two bus cycles if the MCU is operating
with an 8-bit external data bus and the corresponding
data is stored in external memory. There can be
additional stretching when the address space is
assigned to a chip-select circuit programmed for slow
memory. These cycles are also stretched if they
correspond to misaligned accesses to a memory that
is not designed for single-cycle misaligned access.
x — 8-bit conditional write. These cycles are either data
write cycles or free cycles, depending on the data and
flow of the REV or REVW instruction. These cycles
are only stretched when controlled by a chip-select
circuit programmed for slow memory.
Reference Manual
102
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
Special Notation for Branch Taken/Not Taken Cases
PPP/P — Short branches require three cycles if taken, one
cycle if not taken. Since the instruction consists of a
single word containing both an opcode and an 8-bit
offset, the not-taken case is simple — the queue
advances, another program word fetch is made, and
execution continues with the next instruction. The
taken case requires that the queue be refilled so that
execution can continue at a new address. First, the
effective address of the destination is determined,
then the CPU performs three program word fetches
from that address.
OPPP/OPO — Long branches require four cycles if taken, three
cycles if not taken. Optional cycles are required
because all long branches are page two opcodes, and
thus include the $18 prebyte. The CPU12 treats the
prebyte as a special 1-byte instruction. If the prebyte
is misaligned, the optional cycle is used to perform a
program word access; if the prebyte is aligned, the
optional cycle is used to perform a free cycle. As a
result, both the taken and not-taken cases use one
optional cycle for the prebyte. In the not-taken case,
the queue must advance so that execution can
continue with the next instruction, and another
optional cycle is required to maintain the queue. The
taken case requires that the queue be refilled so that
execution can continue at a new address. First, the
effective address of the destination is determined,
then the CPU performs three program word fetches
from that address.
6.7 Glossary
This subsection contains an entry for each assembler mnemonic, in
alphabetic order.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
103
Instruction Glossary
ABA
Operation:
Description:
CCR Details:
Add Accumulator B to Accumulator A
ABA
(A) + (B) ⇒ A
Adds the content of accumulator B to the content of accumulator A and
places the result in A. The content of B is not changed. This instruction
affects the H status bit so it is suitable for use in BCD arithmetic
operations. See DAA instruction for additional information.
S
X
H
I
N
Z
V
C
–
–
∆
–
∆
∆
∆
∆
H: A3 • B3 + B3 • R3 + R3 • A3
Set if there was a carry from bit 3; cleared otherwise
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: A7 • B7 • R7 + A7 • B7 • R7
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: A7 • B7 + B7 • R7 + R7 • A7
Set if there was a carry from the MSB of the result; cleared
otherwise
Source Form
ABA
Address
Mode
INH
Access Detail
Object Code
HCS12
18 06
OO
Reference Manual
104
M68HC12
OO
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
ABX
Operation:
Description:
Add Accumulator B to Index Register X
ABX
(B) + (X) ⇒ X
Adds the 8-bit unsigned content of accumulator B to the content of index
register X considering the possible carry out of the low-order byte of X;
places the result in X. The content of B is not changed.
This mnemonic is implemented by the LEAX B,X instruction. The LEAX
instruction allows A, B, D, or a constant to be added to X. For
compatibility with the M68HC11, the mnemonic ABX is translated into
the LEAX B,X instruction by the assembler.
CCR Details:
Source Form
ABX
translates to... LEAX B,X
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
IDX
Access Detail
Object Code
HCS12
1A E5
Pf
M68HC12
PP(1)
1. Due to internal M68HC12 CPU requirements, the program word fetch is performed twice to the same address during this
instruction.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
105
Instruction Glossary
ABY
Operation:
Description:
Add Accumulator B to Index Register Y
ABY
(B) + (Y) ⇒ Y
Adds the 8-bit unsigned content of accumulator B to the content of index
register Y considering the possible carry out of the low-order byte of Y;
places the result in Y. The content of B is not changed.
This mnemonic is implemented by the LEAY B,Y instruction. The LEAY
instruction allows A, B, D, or a constant to be added to Y. For
compatibility with the M68HC11, the mnemonic ABY is translated into
the LEAY B,Y instruction by the assembler.
CCR Details:
Source Form
ABY
translates to... LEAY B,Y
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
IDX
Access Detail
Object Code
HCS12
19 ED
Pf
M68HC12
PP(1)
1. Due to internal M68HC12CPU requirements, the program word fetch is performed twice to the same address during this
instruction.
Reference Manual
106
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
ADCA
Operation:
Description:
CCR Details:
Add with Carry to A
ADCA
(A) + (M) + C ⇒ A
Adds the content of accumulator A to the content of memory location M,
then adds the value of the C bit and places the result in A. This
instruction affects the H status bit, so it is suitable for use in BCD
arithmetic operations. See DAA instruction for additional information.
S
X
H
I
N
Z
V
C
–
–
∆
–
∆
∆
∆
∆
H: A3 • M3 + M3 • R3 + R3 • A3
Set if there was a carry from bit 3; cleared otherwise
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: A7 • M7 • R7 + A7 • M7 • R7
Set if two’s complement overflow resulted from the operation;
cleared otherwise
C: A7 • M7 + M7 • R7 + R7 • A7
Set if there was a carry from the MSB of the result; cleared
otherwise
Source Form
ADCA #opr8i
ADCA opr8a
ADCA opr16a
ADCA oprx0_xysp
ADCA oprx9,xysp
ADCA oprx16,xysp
ADCA [D,xysp]
ADCA [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
89 ii
99 dd
B9 hh ll
A9 xb
A9 xb ff
A9 xb ee ff
A9 xb
A9 xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
107
Instruction Glossary
ADCB
Operation:
Description:
CCR Details:
Add with Carry to B
ADCB
(B) + (M) + C ⇒ B
Adds the content of accumulator B to the content of memory location M,
then adds the value of the C bit and places the result in B. This
instruction affects the H status bit, so it is suitable for use in BCD
arithmetic operations. See DAA instruction for additional information.
S
X
H
I
N
Z
V
C
–
–
∆
–
∆
∆
∆
∆
H: X3 • M3 + M3 • R3 + R3 • X3
Set if there was a carry from bit 3; cleared otherwise
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: X7 • M7 • R7 + X7 • M7 • R7
Set if two’s complement overflow resulted from the operation;
cleared otherwise
C: X7 • M7 + M7 • R7 + R7 • X7
Set if there was a carry from the MSB of the result; cleared
otherwise
Source Form
ADCB #opr8i
ADCB opr8a
ADCB opr16a
ADCB oprx0_xysp
ADCB oprx9,xysp
ADCB oprx16,xysp
ADCB [D,xysp]
ADCB [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
C9 ii
D9 dd
F9 hh ll
E9 xb
E9 xb ff
E9 xb ee ff
E9 xb
E9 xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
Reference Manual
108
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
ADDA
Operation:
Description:
CCR Details:
Add without Carry to A
ADDA
(A) + (M) ⇒ A
Adds the content of memory location M to accumulator A and places the
result in A. This instruction affects the H status bit, so it is suitable for use
in BCD arithmetic operations. See DAA instruction for additional
information.
S
X
H
I
N
Z
V
C
–
–
∆
–
∆
∆
∆
∆
H: A3 • M3 + M3 • R3 + R3 • A3
Set if there was a carry from bit 3; cleared otherwise
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: A7 • M7 • R7 + A7 • M7 • R7
Set if two’s complement overflow resulted from the operation;
cleared otherwise
C: A7 • M7 + M7 • R7 + R7 • A7
Set if there was a carry from the MSB of the result; cleared
otherwise
Source Form
ADDA #opr8i
ADDA opr8a
ADDA opr16a
ADDA oprx0_xysp
ADDA oprx9,xysp
ADDA oprx16,xysp
ADDA [D,xysp]
ADDA [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
8B ii
9B dd
BB hh ll
AB xb
AB xb ff
AB xb ee ff
AB xb
AB xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
109
Instruction Glossary
ADDB
Operation:
Description:
CCR Details:
Add without Carry to B
ADDB
(B) + (M) ⇒ B
Adds the content of memory location M to accumulator B and places the
result in B. This instruction affects the H status bit, so it is suitable for use
in BCD arithmetic operations. See DAA instruction for additional
information.
S
X
H
I
N
Z
V
C
–
–
∆
–
∆
∆
∆
∆
H: B3 • M3 + M3 • R3 + R3 • B3
Set if there was a carry from bit 3; cleared otherwise
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: B7 • M7 • R7 + B7 • M7 • R7
Set if two’s complement overflow resulted from the operation;
cleared otherwise
C: B7 • M7 + M7 • R7 + R7 • B7
Set if there was a carry from the MSB of the result; cleared
otherwise
Source Form
ADDB #opr8i
ADDB opr8a
ADDB opr16a
ADDB oprx0_xysp
ADDB oprx9,xysp
ADDB oprx16,xysp
ADDB [D,xysp]
ADDB [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
CB ii
DB dd
FB hh ll
EB xb
EB xb ff
EB xb ee ff
EB xb
EB xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
Reference Manual
110
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
ADDD
Operation:
Description:
CCR Details:
Add Double Accumulator
ADDD
(A : B) + (M : M+1) ⇒ A : B
Adds the content of memory location M concatenated with the content of
memory location M +1 to the content of double accumulator D and
places the result in D. Accumulator A forms the high-order half of 16-bit
double accumulator D; accumulator B forms the low-order half.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: D15 • M15 • R15 + D15 • M15 • R15
Set if two’s complement overflow resulted from the operation;
cleared otherwise
C: D15 • M15 + M15 • R15 + R15 • D15
Set if there was a carry from the MSB of the result; cleared
otherwise
Source Form
ADDD #opr16i
ADDD opr8a
ADDD opr16a
ADDD oprx0_xysp
ADDD oprx9,xysp
ADDD oprx16,xysp
ADDD [D,xysp]
ADDD [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
C3 jj kk
D3 dd
F3 hh ll
E3 xb
E3 xb ff
E3 xb ee ff
E3 xb
E3 xb ee ff
HCS12
M68HC12
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPF
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
111
Instruction Glossary
ANDA
Operation:
Description:
CCR Details:
ANDA
Logical AND A
(A) • (M) ⇒ A
Performs logical AND between the content of memory location M and
the content of accumulator A. The result is placed in A. After the
operation is performed, each bit of A is the logical AND of the
corresponding bits of M and of A before the operation began.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: 0; cleared.
Source Form
ANDA #opr8i
ANDA opr8a
ANDA opr16a
ANDA oprx0_xysp
ANDA oprx9,xysp
ANDA oprx16,xysp
ANDA [D,xysp]
ANDA [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
84 ii
94 dd
B4 hh ll
A4 xb
A4 xb ff
A4 xb ee ff
A4 xb
A4 xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
Reference Manual
112
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
ANDB
Operation:
Description:
CCR Details:
ANDB
Logical AND B
(B) • (M) ⇒ B
Performs logical AND between the content of memory location M and
the content of accumulator B. The result is placed in B. After the
operation is performed, each bit of B is the logical AND of the
corresponding bits of M and of B before the operation began.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: 0; cleared
Source Form
ANDB #opr8i
ANDB opr8a
ANDB opr16a
ANDB oprx0_xysp
ANDB oprx9,xysp
ANDB oprx16,xysp
ANDB [D,xysp]
ANDB [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
C4 ii
D4 dd
F4 hh ll
E4 xb
E4 xb ff
E4 xb ee ff
E4 xb
E4 xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
113
Instruction Glossary
ANDCC
Operation:
Description:
Logical AND CCR with Mask
ANDCC
(CCR) • (Mask) ⇒ CCR
Performs bitwise logical AND between the content of a mask operand
and the content of the CCR. The result is placed in the CCR. After the
operation is performed, each bit of the CCR is the result of a logical AND
with the corresponding bits of the mask. To clear CCR bits, clear the
corresponding mask bits. CCR bits that correspond to ones in the mask
are not changed by the ANDCC operation.
If the I mask bit is cleared, there is a 1-cycle delay before the system
allows interrupt requests. This prevents interrupts from occurring
between instructions in the sequences CLI, WAI and CLI, SEI (CLI is
equivalent to ANDCC #$EF).
CCR Details:
S
X
H
I
N
Z
V
C
⇓
⇓
⇓
⇓
⇓
⇓
⇓
⇓
Condition code bits are cleared if the corresponding bit was 0 before the
operation or if the corresponding bit in the mask is 0.
Source Form
ANDCC #opr8i
Address
Mode
IMM
Access Detail
Object Code
HCS12
10 ii
P
Reference Manual
114
M68HC12
P
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
ASL
ASL
Arithmetic Shift Left Memory
(same as LSL)
Operation:
C
Description:
CCR Details:
b7 – – – – – – b0
0
Shifts all bits of memory location M one bit position to the left. Bit 0 is
loaded with a 0. The C status bit is loaded from the most significant bit
of M.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: M7
Set if the MSB of M was set before the shift; cleared otherwise
Source Form
ASL opr16a
ASL oprx0_xysp
ASL oprx9,xysp
ASL oprx16,xysp
ASL [D,xysp]
ASL [oprx16,xysp]
Access Detail
Address
Mode
Object Code
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
78 hh ll
68 xb
68 xb ff
68 xb ee ff
68 xb
68 xb ee ff
HCS12
M68HC12
rPwO
rPw
rPwO
frPwP
fIfrPw
fIPrPw
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
115
Instruction Glossary
ASLA
ASLA
Arithmetic Shift Left A
(same as LSLA)
Operation:
C
Description:
CCR Details:
b7 – – – – – – b0
0
Shifts all bits of accumulator A one bit position to the left. Bit 0 is loaded
with a 0. TheC status bit is loaded from the most significant bit of A.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: A7
Set if the MSB of A was set before the shift; cleared otherwise
Source Form
ASLA
Address
Mode
INH
Access Detail
Object Code
HCS12
48
O
Reference Manual
116
M68HC12
O
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
ASLB
ASLB
Arithmetic Shift Left B
(same as LSLB)
Operation:
C
Description:
CCR Details:
b7 – – – – – – b0
0
Shifts all bits of accumulator B one bit position to the left. Bit 0 is loaded
with a 0. The C status bit is loaded from the most significant bit of B.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: B7
Set if the MSB of B was set before the shift; cleared otherwise
Source Form
ASLB
Address
Mode
INH
Access Detail
Object Code
HCS12
58
1
S12CPUV2
MOTOROLA
M68HC12
O
Reference Manual
Instruction Glossary
117
Instruction Glossary
ASLD
Arithmetic Shift Left Double Accumulator
(same as LSLD)
ASLD
Operation:
C
Description:
CCR Details:
b7 – – – – – – b0
b7 – – – – – – b0
Accumulator A
Accumulator B
0
Shifts all bits of double accumulator D one bit position to the left. Bit 0 is
loaded with a 0. The C status bit is loaded from the most significant bit
of D.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: D15
Set if the MSB of D was set before the shift; cleared otherwise
Source Form
ASLD
Address
Mode
INH
Access Detail
Object Code
HCS12
59
O
Reference Manual
118
M68HC12
O
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
ASR
Arithmetic Shift Right Memory
ASR
Operation:
b7 – – – – – – b0
Description:
CCR Details:
C
Shifts all bits of memory location M one place to the right. Bit 7 is held
constant. Bit 0 is loaded into the C status bit. This operation effectively
divides a two’s complement value by two without changing its sign. The
carry bit can be used to round the result.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: M0
Set if the LSB of M was set before the shift; cleared otherwise
Source Form
ASR opr16a
ASR oprx0_xysp
ASR oprx9,xysp
ASR oprx16,xysp
ASR [D,xysp]
ASR [oprx16,xysp]
Access Detail
Address
Mode
Object Code
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
77 hh ll
67 xb
67 xb ff
67 xb ee ff
67 xb
67 xb ee ff
HCS12
M68HC12
rPwO
rPw
rPwO
frPwP
fIfrPw
fIPrPw
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
119
Instruction Glossary
ASRA
ASRA
Arithmetic Shift Right A
Operation:
b7 – – – – – – b0
Description:
CCR Details:
C
Shifts all bits of accumulator A one place to the right. Bit 7 is held
constant. Bit 0 is loaded into the C status bit. This operation effectively
divides a two’s complement value by two without changing its sign. The
carry bit can be used to round the result.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: A0
Set if the LSB of A was set before the shift; cleared otherwise
Source Form
ASRA
Address
Mode
INH
Access Detail
Object Code
HCS12
47
O
Reference Manual
120
M68HC12
O
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
ASRB
ASRB
Arithmetic Shift Right B
Operation:
b7 – – – – – – b0
Description:
CCR Details:
C
Shifts all bits of accumulator B one place to the right. Bit 7 is held
constant. Bit 0 is loaded into the C status bit. This operation effectively
divides a two’s complement value by two without changing its sign. The
carry bit can be used to round the result.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: B0
Set if the LSB of B was set before the shift; cleared otherwise
Source Form
ASRB
Address
Mode
INH
Access Detail
Object Code
HCS12
57
O
S12CPUV2
MOTOROLA
M68HC12
O
Reference Manual
Instruction Glossary
121
Instruction Glossary
BCC
Operation:
Branch if Carry Cleared
(Same as BHS)
BCC
If C = 0, then (PC) + $0002 + Rel ⇒ PC
Simple branch
Description:
Tests the C status bit and branches if C = 0.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BCC rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
24 rr
HCS12
M68HC12
PPP/P(1)
PPP/P(1)
1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program
fetch cycle if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
BGT
2E
BGE
2C
BEQ
27
BLE
2F
BLT
2D
BHI
22
BHS/BCC
24
BEQ
27
BLS
23
BLO/BCS
25
BCS
25
BMI
2B
BVS
29
BEQ
27
BRA
20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Reference Manual
122
Complementary Branch
Mnemonic
Opcode
Comment
BLE
2F
Signed
BLT
2D
Signed
BNE
26
Signed
BGT
2E
Signed
BGE
2C
Signed
BLS
23
Unsigned
BLO/BCS
25
Unsigned
BNE
26
Unsigned
BHI
22
Unsigned
BHS/BCC
24
Unsigned
BCC
24
Simple
BPL
2A
Simple
BVC
28
Simple
BNE
26
Simple
BRN
21
Unconditional
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
BCLR
Operation:
Description:
CCR Details:
BCLR
Clear Bits in Memory
(M) • (Mask) ⇒ M
Clears bits in location M. To clear a bit, set the corresponding bit in the
mask byte. Bits in M that correspond to 0s in the mask byte are not
changed. Mask bytes can be located at PC + 2, PC + 3, or PC + 4,
depending on addressing mode used.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: 0; cleared
Source Form
BCLR opr8a, msk8
BCLR opr16a, msk8
BCLR oprx0_xysp, msk8
BCLR oprx9,xysp, msk8
BCLR oprx16,xysp, msk8
Access Detail
Address
Mode(1)
Object Code
DIR
EXT
IDX
IDX1
IDX2
4D dd mm
1D hh ll mm
0D xb mm
0D xb ff mm
0D xb ee ff mm
HCS12
M68HC12
rPwO
rPwP
rPwO
rPwP
frPwPO
rPOw
rPPw
rPOw
rPwP
frPwOP
1. Indirect forms of indexed addressing cannot be used with this instruction.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
123
Instruction Glossary
BCS
Operation:
BCS
Branch if Carry Set
(Same as BLO)
If C = 1, then (PC) + $0002 + Rel ⇒ PC
Simple branch
Description:
Tests the C status bit and branches if C = 1.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BCS rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
25 rr
HCS12
M68HC12
PPP/P(1)
PPP/P(1)
1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program
fetch cycle if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
BGT
2E
BGE
2C
BEQ
27
BLE
2F
BLT
2D
BHI
22
BHS/BCC
24
BEQ
27
BLS
23
BLO/BCS
25
BCS
25
BMI
2B
BVS
29
BEQ
27
BRA
20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Reference Manual
124
Complementary Branch
Mnemonic
Opcode
Comment
BLE
2F
Signed
BLT
2D
Signed
BNE
26
Signed
BGT
2E
Signed
BGE
2C
Signed
BLS
23
Unsigned
BLO/BCS
25
Unsigned
BNE
26
Unsigned
BHI
22
Unsigned
BHS/BCC
24
Unsigned
BCC
24
Simple
BPL
2A
Simple
BVC
28
Simple
BNE
26
Simple
BRN
21
Unconditional
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
BEQ
Operation:
BEQ
Branch if Equal
If Z = 1, then (PC) + $0002 + Rel ⇒ PC
Simple branch
Description:
Tests the Z status bit and branches if Z = 1.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BEQ rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
27 rr
HCS12
M68HC12
PPP/P(1)
PPP/P(1)
1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program
fetch cycle if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
BGT
2E
BGE
2C
BEQ
27
BLE
2F
BLT
2D
BHI
22
BHS/BCC
24
BEQ
27
BLS
23
BLO/BCS
25
BCS
25
BMI
2B
BVS
29
BEQ
27
BRA
20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
S12CPUV2
MOTOROLA
Complementary Branch
Mnemonic
Opcode
Comment
BLE
2F
Signed
BLT
2D
Signed
BNE
26
Signed
BGT
2E
Signed
BGE
2C
Signed
BLS
23
Unsigned
BLO/BCS
25
Unsigned
BNE
26
Unsigned
BHI
22
Unsigned
BHS/BCC
24
Unsigned
BCC
24
Simple
BPL
2A
Simple
BVC
28
Simple
BNE
26
Simple
BRN
21
Unconditional
Reference Manual
Instruction Glossary
125
Instruction Glossary
BGE
Operation:
Branch if Greater than or Equal to Zero
BGE
If N ⊕ V = 0, then (PC) + $0002 + Rel ⇒ PC
For signed two’s complement values
if (Accumulator) ≥ (Memory), then branch
Description:
BGE can be used to branch after comparing or subtracting signed two’s
complement values. After CMPA, CMPB, CPD, CPS, CPX, CPY, SBCA,
SBCB, SUBA, SUBB, or SUBD, the branch occurs if the CPU register
value is greater than or equal to the value in M. After CBA or SBA, the
branch occurs if the value in B is greater than or equal to the value in A.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BGE rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
2C rr
HCS12
M68HC12
PPP/P(1)
PPP/P(1)
1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program
fetch cycle if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
BGT
2E
BGE
2C
BEQ
27
BLE
2F
BLT
2D
BHI
22
BHS/BCC
24
BEQ
27
BLS
23
BLO/BCS
25
BCS
25
BMI
2B
BVS
29
BEQ
27
BRA
20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Reference Manual
126
Complementary Branch
Mnemonic
Opcode
Comment
BLE
2F
Signed
BLT
2D
Signed
BNE
26
Signed
BGT
2E
Signed
BGE
2C
Signed
BLS
23
Unsigned
BLO/BCS
25
Unsigned
BNE
26
Unsigned
BHI
22
Unsigned
BHS/BCC
24
Unsigned
BCC
24
Simple
BPL
2A
Simple
BVC
28
Simple
BNE
26
Simple
BRN
21
Unconditional
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
BGND
Description:
Enter Background Debug Mode
BGND
BGND operates like a software interrupt, except that no registers are
stacked. First, the current PC value is stored in internal CPU register
TMP2. Next, the BDM ROM and background register block become
active. The BDM ROM contains a substitute vector, mapped to the
address of the software interrupt vector, which points to routines in the
BDM ROM that control background operation. The substitute vector is
fetched, and execution continues from the address that it points to.
Finally, the CPU checks the location that TMP2 points to. If the value
stored in that location is $00 (the BGND opcode), TMP2 is incremented,
so that the instruction that follows the BGND instruction is the first
instruction executed when normal program execution resumes.
For all other types of BDM entry, the CPU performs the same sequence
of operations as for a BGND instruction, but the value stored in TMP2
already points to the instruction that would have executed next had BDM
not become active. If active BDM is triggered just as a BGND instruction
is about to execute, the BDM firmware does increment TMP2, but the
change does not affect resumption of normal execution.
While BDM is active, the CPU executes debugging commands received
via a special single-wire serial interface. BDM is terminated by the
execution of specific debugging commands. Upon exit from BDM, the
background/boot ROM and registers are disabled, the instruction queue
is refilled starting with the return address pointed to by TMP2, and
normal processing resumes.
BDM is normally disabled to avoid accidental entry. While BDM is
disabled, BGND executes as described, but the firmware causes
execution to return to the user program. Refer to Section 8. Instruction
Queue for more information concerning BDM.
CCR Details:
Source Form
BGND
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
00
HCS12
M68HC12
VfPPP
VfPPP
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
127
Instruction Glossary
BGT
Operation:
BGT
Branch if Greater than Zero
If Z + (N ⊕ V) = 0, then (PC) + $0002 + Rel ⇒ PC
For signed two’s complement values
if (Accumulator) > (Memory), then branch
Description:
BGT can be used to branch after comparing or subtracting signed two’s
complement values. After CMPA, CMPB, CPD, CPS, CPX, CPY, SBCA,
SBCB, SUBA, SUBB, or SUBD, the branch occurs if the CPU register
value is greater than the value in M. After CBA or SBA, the branch
occurs if the value in B is greater than the value in A.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BGT rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
2E rr
HCS12
M68HC12
PPP/P(1)
PPP/P(1)
1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program
fetch cycle if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
BGT
2E
BGE
2C
BEQ
27
BLE
2F
BLT
2D
BHI
22
BHS/BCC
24
BEQ
27
BLS
23
BLO/BCS
25
BCS
25
BMI
2B
BVS
29
BEQ
27
BRA
20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Reference Manual
128
Complementary Branch
Mnemonic
Opcode
Comment
BLE
2F
Signed
BLT
2D
Signed
BNE
26
Signed
BGT
2E
Signed
BGE
2C
Signed
BLS
23
Unsigned
BLO/BCS
25
Unsigned
BNE
26
Unsigned
BHI
22
Unsigned
BHS/BCC
24
Unsigned
BCC
24
Simple
BPL
2A
Simple
BVC
28
Simple
BNE
26
Simple
BRN
21
Unconditional
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
BHI
Operation:
BHI
Branch if Higher
If C + Z = 0, then (PC) + $0002 + Rel ⇒ PC
For unsigned values, if (Accumulator) > (Memory), then branch
Description:
BHI can be used to branch after comparing or subtracting unsigned
values. After CMPA, CMPB, CPD, CPS, CPX, CPY, SBCA, SBCB,
SUBA, SUBB, or SUBD, the branch occurs if the CPU register value is
greater than the value in M. After CBA or SBA, the branch occurs if the
value in B is greater than the value in A. BHI should not be used for
branching after instructions that do not affect the C bit, such as
increment, decrement, load, store, test, clear, or complement.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BHI rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
22 rr
HCS12
M68HC12
PPP/P(1)
PPP/P(1)
1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program
fetch cycle if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
BGT
2E
BGE
2C
BEQ
27
BLE
2F
BLT
2D
BHI
22
BHS/BCC
24
BEQ
27
BLS
23
BLO/BCS
25
BCS
25
BMI
2B
BVS
29
BEQ
27
BRA
20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
S12CPUV2
MOTOROLA
Complementary Branch
Mnemonic
Opcode
Comment
BLE
2F
Signed
BLT
2D
Signed
BNE
26
Signed
BGT
2E
Signed
BGE
2C
Signed
BLS
23
Unsigned
BLO/BCS
25
Unsigned
BNE
26
Unsigned
BHI
22
Unsigned
BHS/BCC
24
Unsigned
BCC
24
Simple
BPL
2A
Simple
BVC
28
Simple
BNE
26
Simple
BRN
21
Unconditional
Reference Manual
Instruction Glossary
129
Instruction Glossary
BHS
Operation:
Branch if Higher or Same
(Same as BCC)
BHS
If C = 0, then (PC) + $0002 + Rel ⇒ PC
For unsigned values, if (Accumulator) ≥ (Memory), then branch
Description:
BHS can be used to branch after subtracting or comparing unsigned
values. After CMPA, CMPB, CPD, CPS, CPX, CPY, SBCA, SBCB,
SUBA, SUBB, or SUBD, the branch occurs if the CPU register value is
greater than or equal to the value in M. After CBA or SBA, the branch
occurs if the value in B is greater than or equal to the value in A. BHS
should not be used for branching after instructions that do not affect the
C bit, such as increment, decrement, load, store, test, clear, or
complement.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BHS rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
24 rr
HCS12
M68HC12
PPP/P(1)
PPP/P(1)
1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program
fetch cycle if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
BGT
2E
BGE
2C
BEQ
27
BLE
2F
BLT
2D
BHI
22
BHS/BCC
24
BEQ
27
BLS
23
BLO/BCS
25
BCS
25
BMI
2B
BVS
29
BEQ
27
BRA
20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Reference Manual
130
Complementary Branch
Mnemonic
Opcode
Comment
BLE
2F
Signed
BLT
2D
Signed
BNE
26
Signed
BGT
2E
Signed
BGE
2C
Signed
BLS
23
Unsigned
BLO/BCS
25
Unsigned
BNE
26
Unsigned
BHI
22
Unsigned
BHS/BCC
24
Unsigned
BCC
24
Simple
BPL
2A
Simple
BVC
28
Simple
BNE
26
Simple
BRN
21
Unconditional
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
BITA
Operation:
Description:
CCR Details:
BITA
Bit Test A
(A) • (M)
Performs bitwise logical AND on the content of accumulator A and the
content of memory location M and modifies the condition codes
accordingly. Each bit of the result is the logical AND of the corresponding
bits of the accumulator and the memory location. Neither the content of
the accumulator nor the content of the memory location is affected.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: 0; cleared
Source Form
BITA #opr8i
BITA opr8a
BITA opr16a
BITA oprx0_xysp
BITA oprx9,xysp
BITA oprx16,xysp
BITA [D,xysp]
BITA [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
85 ii
95 dd
B5 hh ll
A5 xb
A5 xb ff
A5 xb ee ff
A5 xb
A5 xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
131
Instruction Glossary
BITB
Operation:
Description:
CCR Details:
BITB
Bit Test B
(B) • (M)
Performs bitwise logical AND on the content of accumulator B and the
content of memory location M and modifies the condition codes
accordingly. Each bit of the result is the logical AND of the corresponding
bits of the accumulator and the memory location. Neither the content of
the accumulator nor the content of the memory location is affected.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: 0; cleared
Source Form
BITB #opr8i
BITB opr8a
BITB opr16a
BITB oprx0_xysp
BITB oprx9,xysp
BITB oprx16,xysp
BITB [D,xysp]
BITB [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
C5 ii
D5 dd
F5 hh ll
E5 xb
E5 xb ff
E5 xb ee ff
E5 xb
E5 xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
Reference Manual
132
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
BLE
Operation:
BLE
Branch if Less Than or Equal to Zero
If Z + (N ⊕ V) = 1, then (PC) + $0002 + Rel ⇒ PC
For signed two’s complement numbers
if (Accumulator) ≤ (Memory), then branch
Description:
BLE can be used to branch after subtracting or comparing signed two’s
complement values. After CMPA, CMPB, CPD, CPS, CPX, CPY, SBCA,
SBCB, SUBA, SUBB, or SUBD, the branch occurs if the CPU register
value is less than or equal to the value in M. After CBA or SBA, the
branch occurs if the value in B is less than or equal to the value in A.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BLE rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
2F rr
HCS12
M68HC12
PPP/P(1)
PPP/P(1)
1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program
fetch cycle if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
BGT
2E
BGE
2C
BEQ
27
BLE
2F
BLT
2D
BHI
22
BHS/BCC
24
BEQ
27
BLS
23
BLO/BCS
25
BCS
25
BMI
2B
BVS
29
BEQ
27
BRA
20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
S12CPUV2
MOTOROLA
Complementary Branch
Mnemonic
Opcode
Comment
BLE
2F
Signed
BLT
2D
Signed
BNE
26
Signed
BGT
2E
Signed
BGE
2C
Signed
BLS
23
Unsigned
BLO/BCS
25
Unsigned
BNE
26
Unsigned
BHI
22
Unsigned
BHS/BCC
24
Unsigned
BCC
24
Simple
BPL
2A
Simple
BVC
28
Simple
BNE
26
Simple
BRN
21
Unconditional
Reference Manual
Instruction Glossary
133
Instruction Glossary
BLO
Operation:
BLO
Branch if Lower
(Same as BCS)
If C = 1, then (PC) + $0002 + Rel ⇒ PC
For unsigned values, if (Accumulator) < (Memory), then branch
Description:
BLO can be used to branch after subtracting or comparing unsigned
values. After CMPA, CMPB, CPD, CPS, CPX, CPY, SBCA, SBCB,
SUBA, SUBB, or SUBD, the branch occurs if the CPU register value is
less than the value in M. After CBA or SBA, the branch occurs if the
value in B is less than the value in A. BLO should not be used for
branching after instructions that do not affect the C bit, such as
increment, decrement, load, store, test, clear, or complement.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BLO rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
25 rr
HCS12
M68HC12
PPP/P(1)
PPP/P(1)
1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program
fetch cycle if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
BGT
2E
BGE
2C
BEQ
27
BLE
2F
BLT
2D
BHI
22
BHS/BCC
24
BEQ
27
BLS
23
BLO/BCS
25
BCS
25
BMI
2B
BVS
29
BEQ
27
BRA
20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Reference Manual
134
Complementary Branch
Mnemonic
Opcode
Comment
BLE
2F
Signed
BLT
2D
Signed
BNE
26
Signed
BGT
2E
Signed
BGE
2C
Signed
BLS
23
Unsigned
BLO/BCS
25
Unsigned
BNE
26
Unsigned
BHI
22
Unsigned
BHS/BCC
24
Unsigned
BCC
24
Simple
BPL
2A
Simple
BVC
28
Simple
BNE
26
Simple
BRN
21
Unconditional
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
BLS
Operation:
BLS
Branch if Lower or Same
If C + Z = 1, then (PC) + $0002 + Rel ⇒ PC
For unsigned values, if (Accumulator) ≤ (Memory), then branch
Description:
If BLS is executed immediately after execution of CBA, CMPA, CMPB,
CMPD, CPX, CPY, SBA, SUBA, SUBB, or SUBD, a branch occurs if and
only if the unsigned binary number in the accumulator is less than or
equal to the unsigned binary number in memory. Generally not useful
after INC/DEC, LD/ST, and TST/CLR/COM because these instructions
do not affect the C status bit.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BLS rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
23 rr
HCS12
M68HC12
PPP/P(1)
PPP/P(1)
1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program
fetch cycle if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
BGT
2E
BGE
2C
BEQ
27
BLE
2F
BLT
2D
BHI
22
BHS/BCC
24
BEQ
27
BLS
23
BLO/BCS
25
BCS
25
BMI
2B
BVS
29
BEQ
27
BRA
20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
S12CPUV2
MOTOROLA
Complementary Branch
Mnemonic
Opcode
Comment
BLE
2F
Signed
BLT
2D
Signed
BNE
26
Signed
BGT
2E
Signed
BGE
2C
Signed
BLS
23
Unsigned
BLO/BCS
25
Unsigned
BNE
26
Unsigned
BHI
22
Unsigned
BHS/BCC
24
Unsigned
BCC
24
Simple
BPL
2A
Simple
BVC
28
Simple
BNE
26
Simple
BRN
21
Unconditional
Reference Manual
Instruction Glossary
135
Instruction Glossary
BLT
Operation:
BLT
Branch if Less than Zero
If N ⊕ V = 1, then (PC) + $0002 + Rel ⇒ PC
For signed two’s complement numbers
if (Accumulator) < (Memory), then branch
Description:
BLT can be used to branch after subtracting or comparing signed two’s
complement values. After CMPA, CMPB, CMPD, CPS, CPX, CPY,
SBCA, SBCB, SUBA, SUBB, or SUBD, the branch occurs if the CPU
register value is less than the value in M. After CBA or SBA, the branch
occurs if the value in B is less than the value in A.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BLT rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
2D rr
HCS12
M68HC12
PPP/P(1)
PPP/P(1)
1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program
fetch cycle if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
BGT
2E
BGE
2C
BEQ
27
BLE
2F
BLT
2D
BHI
22
BHS/BCC
24
BEQ
27
BLS
23
BLO/BCS
25
BCS
25
BMI
2B
BVS
29
BEQ
27
BRA
20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Reference Manual
136
Complementary Branch
Mnemonic
Opcode
Comment
BLE
2F
Signed
BLT
2D
Signed
BNE
26
Signed
BGT
2E
Signed
BGE
2C
Signed
BLS
23
Unsigned
BLO/BCS
25
Unsigned
BNE
26
Unsigned
BHI
22
Unsigned
BHS/BCC
24
Unsigned
BCC
24
Simple
BPL
2A
Simple
BVC
28
Simple
BNE
26
Simple
BRN
21
Unconditional
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
BMI
Operation:
BMI
Branch if Minus
If N = 1, then (PC) + $0002 + Rel ⇒ PC
Simple branch
Description:
Tests the N status bit and branches if N = 1.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BMI rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
2B rr
HCS12
M68HC12
PPP/P(1)
PPP/P(1)
1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program
fetch cycle if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
BGT
2E
BGE
2C
BEQ
27
BLE
2F
BLT
2D
BHI
22
BHS/BCC
24
BEQ
27
BLS
23
BLO/BCS
25
BCS
25
BMI
2B
BVS
29
BEQ
27
BRA
20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
S12CPUV2
MOTOROLA
Complementary Branch
Mnemonic
Opcode
Comment
BLE
2F
Signed
BLT
2D
Signed
BNE
26
Signed
BGT
2E
Signed
BGE
2C
Signed
BLS
23
Unsigned
BLO/BCS
25
Unsigned
BNE
26
Unsigned
BHI
22
Unsigned
BHS/BCC
24
Unsigned
BCC
24
Simple
BPL
2A
Simple
BVC
28
Simple
BNE
26
Simple
BRN
21
Unconditional
Reference Manual
Instruction Glossary
137
Instruction Glossary
BNE
Operation:
Branch if Not Equal to Zero
BNE
If Z = 0, then (PC) + $0002 + Rel ⇒ PC
Simple branch
Description:
Tests the Z status bit and branches if Z = 0.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BNE rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
26 rr
HCS12
M68HC12
PPP/P(1)
PPP/P(1)
1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program
fetch cycle if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
BGT
2E
BGE
2C
BEQ
27
BLE
2F
BLT
2D
BHI
22
BHS/BCC
24
BEQ
27
BLS
23
BLO/BCS
25
BCS
25
BMI
2B
BVS
29
BEQ
27
BRA
20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Reference Manual
138
Complementary Branch
Mnemonic
Opcode
Comment
BLE
2F
Signed
BLT
2D
Signed
BNE
26
Signed
BGT
2E
Signed
BGE
2C
Signed
BLS
23
Unsigned
BLO/BCS
25
Unsigned
BNE
26
Unsigned
BHI
22
Unsigned
BHS/BCC
24
Unsigned
BCC
24
Simple
BPL
2A
Simple
BVC
28
Simple
BNE
26
Simple
BRN
21
Unconditional
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
BPL
Operation:
BPL
Branch if Plus
If N = 0, then (PC) + $0002 + Rel ⇒ PC
Simple branch
Description:
Tests the N status bit and branches if N = 0.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BPL rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
2A rr
HCS12
M68HC12
PPP/P(1)
PPP/P(1)
1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program
fetch cycle if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
BGT
2E
BGE
2C
BEQ
27
BLE
2F
BLT
2D
BHI
22
BHS/BCC
24
BEQ
27
BLS
23
BLO/BCS
25
BCS
25
BMI
2B
BVS
29
BEQ
27
BRA
20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
S12CPUV2
MOTOROLA
Complementary Branch
Mnemonic
Opcode
Comment
BLE
2F
Signed
BLT
2D
Signed
BNE
26
Signed
BGT
2E
Signed
BGE
2C
Signed
BLS
23
Unsigned
BLO/BCS
25
Unsigned
BNE
26
Unsigned
BHI
22
Unsigned
BHS/BCC
24
Unsigned
BCC
24
Simple
BPL
2A
Simple
BVC
28
Simple
BNE
26
Simple
BRN
21
Unconditional
Reference Manual
Instruction Glossary
139
Instruction Glossary
BRA
Operation:
Description:
Branch Always
BRA
(PC) + $0002 + Rel ⇒ PC
Unconditional branch to an address calculated as shown in the
expression. Rel is a relative offset stored as a two’s complement number
in the second byte of the branch instruction.
Execution time is longer when a conditional branch is taken than when
it is not, because the instruction queue must be refilled before execution
resumes at the new address. Since the BRA branch condition is always
satisfied, the branch is always taken, and the instruction queue must
always be refilled.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BRA rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
HCS12
20 rr
PPP
Reference Manual
140
M68HC12
PPP
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
BRCLR
Operation:
Description:
BRCLR
Branch if Bits Cleared
If (M) • (Mask) = 0, then branch
Performs a bitwise logical AND of memory location M and the mask
supplied with the instruction, then branches if and only if all bits with a
value of 1 in the mask byte correspond to bits with a value of 0 in the
tested byte. Mask operands can be located at PC + 1, PC + 2, or
PC + 4, depending on addressing mode. The branch offset is referenced
to the next address after the relative offset (rr) which is the last byte of
the instruction object code.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Source Form
BRCLR opr8a, msk8, rel8
BRCLR opr16a, msk8, rel8
BRCLR oprx0_xysp, msk8, rel8
BRCLR oprx9,xysp, msk8, rel8
BRCLR oprx16,xysp, msk8, rel8
Access Detail
Address
Mode(1)
Object Code
DIR
EXT
IDX
IDX1
IDX2
4F dd mm rr
1F hh ll mm rr
0F xb mm rr
0F xb ff mm rr
0F xb ee ff mm rr
HCS12
M68HC12
rPPP
rfPPP
rPPP
rfPPP
PrfPPP
rPPP
rfPPP
rPPP
rffPPP
frPffPPP
1. Indirect forms of indexed addressing cannot be used with this instruction.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
141
Instruction Glossary
BRN
Operation:
Description:
BRN
Branch Never
(PC) + $0002 ⇒ PC
Never branches. BRN is effectively a 2-byte NOP that requires one cycle
to execute. BRN is included in the instruction set to provide a
complement to the BRA instruction. The instruction is useful during
program debug, to negate the effect of another branch instruction
without disturbing the offset byte. A complement for BRA is also useful
in compiler implementations.
Execution time is longer when a conditional branch is taken than when
it is not, because the instruction queue must be refilled before execution
resumes at the new address. Since the BRN branch condition is never
satisfied, the branch is never taken, and only a single program fetch is
needed to update the instruction queue.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BRN rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
HCS12
21 rr
P
Reference Manual
142
M68HC12
P
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
BRSET
Operation:
Description:
BRSET
Branch if Bits Set
If (M) • (Mask) = 0, then branch
Performs a bitwise logical AND of the inverse of memory location M and
the mask supplied with the instruction, then branches if and only if all bits
with a value of 1 in the mask byte correspond to bits with a value of one
in the tested byte. Mask operands can be located at PC + 1, PC + 2, or
PC + 4, depending on addressing mode. The branch offset is referenced
to the next address after the relative offset (rr) which is the last byte of
the instruction object code.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Source Form
BRSET opr8a, msk8, rel8
BRSET opr16a, msk8, rel8
BRSET oprx0_xysp, msk8, rel8
BRSET oprx9,xysp, msk8, rel8
BRSET oprx16,xysp, msk8, rel8
Access Detail
Address
Mode(1)
Object Code
DIR
EXT
IDX
IDX1
IDX2
4E dd mm rr
1E hh ll mm rr
0E xb mm rr
0E xb ff mm rr
0E xb ee ff mm rr
HCS12
M68HC12
rPPP
rfPPP
rPPP
rfPPP
PrfPPP
rPPP
rfPPP
rPPP
rffPPP
frPffPPP
1. Indirect forms of indexed addressing cannot be used with this instruction.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
143
Instruction Glossary
BSET
Operation:
Description:
CCR Details:
BSET
Set Bit(s) in Memory
(M) + (Mask) ⇒ M
Sets bits in memory location M. To set a bit, set the corresponding bit in
the mask byte. All other bits in M are unchanged. The mask byte can be
located at PC + 2, PC + 3, or PC + 4, depending upon addressing mode.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: 0; cleared
Source Form
BSET opr8a, msk8
BSET opr16a, msk8
BSET oprx0_xysp, msk8
BSET oprx9,xysp, msk8
BSET oprx16,xysp, msk8
Access Detail
Address
Mode(1)
Object Code
DIR
EXT
IDX
IDX1
IDX2
4C dd mm
1C hh ll mm
0C xb mm
0C xb ff mm
0C xb ee ff mm
HCS12
M68HC12
rPwO
rPwP
rPwO
rPwP
frPwPO
rPOw
rPPw
rPOw
rPwP
frPwOP
1. Indirect forms of indexed addressing cannot be used with this instruction.
Reference Manual
144
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
BSR
Operation:
Description:
BSR
Branch to Subroutine
(SP) – $0002 ⇒ SP
RTNH : RTNL ⇒ M(SP) : M(SP+1)
(PC) + Rel ⇒ PC
Sets up conditions to return to normal program flow, then transfers
control to a subroutine. Uses the address of the instruction after the BSR
as a return address.
Decrements the SP by two, to allow the two bytes of the return address
to be stacked.
Stacks the return address (the SP points to the high-order byte of the
return address).
Branches to a location determined by the branch offset.
Subroutines are normally terminated with an RTS instruction, which
restores the return address from the stack.
CCR Details:
Source Form
BSR rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
HCS12
07 rr
SPPP
S12CPUV2
MOTOROLA
M68HC12
PPPS
Reference Manual
Instruction Glossary
145
Instruction Glossary
BVC
Operation:
Branch if Overflow Cleared
BVC
If V = 0, then (PC) + $0002 + Rel ⇒ PC
Simple branch
Description:
Tests the V status bit and branches if V = 0.
BVC causes a branch when a previous operation on two’s complement
binary values does not cause an overflow. That is, when BVC follows a
two’s complement operation, a branch occurs when the result of the
operation is valid.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BVC rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
28 rr
HCS12
M68HC12
PPP/P(1)
PPP/P(1)
1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program
fetch cycle if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
BGT
2E
BGE
2C
BEQ
27
BLE
2F
BLT
2D
BHI
22
BHS/BCC
24
BEQ
27
BLS
23
BLO/BCS
25
BCS
25
BMI
2B
BVS
29
BEQ
27
BRA
20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Reference Manual
146
Complementary Branch
Mnemonic
Opcode
Comment
BLE
2F
Signed
BLT
2D
Signed
BNE
26
Signed
BGT
2E
Signed
BGE
2C
Signed
BLS
23
Unsigned
BLO/BCS
25
Unsigned
BNE
26
Unsigned
BHI
22
Unsigned
BHS/BCC
24
Unsigned
BCC
24
Simple
BPL
2A
Simple
BVC
28
Simple
BNE
26
Simple
BRN
21
Unconditional
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
BVS
Operation:
BVS
Branch if Overflow Set
If V = 1, then (PC) + $0002 + Rel ⇒ PC
Simple branch
Description:
Tests the V status bit and branches if V = 1.
BVS causes a branch when a previous operation on two’s complement
binary values causes an overflow. That is, when BVS follows a two’s
complement operation, a branch occurs when the result of the operation
is invalid.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
BVS rel8
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
29 rr
HCS12
M68HC12
PPP/P(1)
PPP/P(1)
1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program
fetch cycle if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
BGT
2E
BGE
2C
BEQ
27
BLE
2F
BLT
2D
BHI
22
BHS/BCC
24
BEQ
27
BLS
23
BLO/BCS
25
BCS
25
BMI
2B
BVS
29
BEQ
27
BRA
20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
S12CPUV2
MOTOROLA
Complementary Branch
Mnemonic
Opcode
Comment
BLE
2F
Signed
BLT
2D
Signed
BNE
26
Signed
BGT
2E
Signed
BGE
2C
Signed
BLS
23
Unsigned
BLO/BCS
25
Unsigned
BNE
26
Unsigned
BHI
22
Unsigned
BHS/BCC
24
Unsigned
BCC
24
Simple
BPL
2A
Simple
BVC
28
Simple
BNE
26
Simple
BRN
21
Unconditional
Reference Manual
Instruction Glossary
147
Instruction Glossary
CALL
Operation:
Description:
CALL
Call Subroutine in Expanded Memory
(SP) – $0002 ⇒ SP; RTNH : RTNL ⇒ M(SP) : M(SP+1)
(SP) – $0001 ⇒ SP; (PPAGE) ⇒ M(SP)
page ⇒ PPAGE; Subroutine Address ⇒ PC
Sets up conditions to return to normal program flow, then transfers
control to a subroutine in expanded memory. Uses the address of the
instruction following the CALL as a return address. For code
compatibility, CALL also executes correctly in devices that do not have
expanded memory capability.
Decrements the SP by two, then stores the return address on the stack.
The SP points to the high-order byte of the return address.
Decrements the SP by one, then stacks the current memory page value
from the PPAGE register on the stack.
Writes a new page value supplied by the instruction to PPAGE and
transfers control to the subroutine.
In indexed-indirect modes, the subroutine address and the PPAGE
value are fetched from memory in the order M high byte, M low byte, and
new PPAGE value.
Expanded-memory subroutines must be terminated by an RTC
instruction, which restores the return address and PPAGE value from
the stack.
CCR Details:
Source Form
CALL opr16a, page
CALL oprx0_xysp, page
CALL oprx9,xysp, page
CALL oprx16,xysp, page
CALL [D,xysp]
CALL [oprx16,xysp]
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
4A hh ll pg
4B xb pg
4B xb ff pg
4B xb ee ff pg
4B xb
4B xb ee ff
HCS12
Reference Manual
148
gnSsPPP
gnSsPPP
gnSsPPP
fgnSsPPP
fIignSsPPP
fIignSsPPP
M68HC12
gnfSsPPP
gnfSsPPP
gnfSsPPP
fgnfSsPPP
fIignSsPPP
fIignSsPPP
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
CBA
Operation:
Description:
CCR Details:
Compare Accumulators
CBA
(A) – (B)
Compares the content of accumulator A to the content of accumulator B
and sets the condition codes, which may then be used for arithmetic and
logical conditional branches. The contents of the accumulators are not
changed.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: A7 • B7 • R7 + A7 • B7 • R7
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: A7 • B7 + B7 • R7 + R7 • A7
Set if there was a borrow from the MSB of the result; cleared
otherwise
Source Form
CBA
Address
Mode
INH
Access Detail
Object Code
HCS12
18 17
OO
S12CPUV2
MOTOROLA
M68HC12
OO
Reference Manual
Instruction Glossary
149
Instruction Glossary
CLC
Operation:
Description:
CLC
Clear Carry
0 ⇒ C bit
Clears the C status bit. This instruction is assembled as ANDCC #$FE.
The ANDCC instruction can be used to clear any combination of bits in
the CCR in one operation.
CLC can be used to set up the C bit prior to a shift or rotate instruction
involving the C bit.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
0
C: 0; cleared
Source Form
CLC
translates to... ANDCC #$FE
Address
Mode
IMM
Access Detail
Object Code
HCS12
10 FE
Reference Manual
150
P
M68HC12
P
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
CLI
Operation:
Description:
CLI
Clear Interrupt Mask
0 ⇒ I bit
Clears the I mask bit. This instruction is assembled as ANDCC #$EF.
The ANDCC instruction can be used to clear any combination of bits in
the CCR in one operation.
When the I bit is cleared, interrupts are enabled. There is a 1-cycle (bus
clock) delay in the clearing mechanism for the I bit so that, if interrupts
were previously disabled, the next instruction after a CLI will always be
executed, even if there was an interrupt pending prior to execution of the
CLI instruction.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
0
–
–
–
–
I:
0; cleared
Source Form
CLI
translates to... ANDCC #$EF
Address
Mode
IMM
Access Detail
Object Code
HCS12
10 EF
S12CPUV2
MOTOROLA
P
M68HC12
P
Reference Manual
Instruction Glossary
151
Instruction Glossary
CLR
Operation:
Description:
CCR Details:
Source Form
CLR opr16a
CLR oprx0_xysp
CLR oprx9,xysp
CLR oprx16,xysp
CLR [D,xysp]
CLR [oprx16,xysp]
CLR
Clear Memory
0⇒M
All bits in memory location M are cleared to 0.
S
X
H
I
N
Z
V
C
–
–
–
–
0
1
0
0
N:
Z:
V:
C:
0; cleared
1; set
0; cleared
0; cleared
Access Detail
Address
Mode
Object Code
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
79 hh ll
69 xb
69 xb ff
69 xb ee ff
69 xb
69 xb ee ff
HCS12
PwO
Pw
PwO
PwP
PIfw
PIPw
Reference Manual
152
M68HC12
wOP
Pw
PwO
PwP
PIfPw
PIPPw
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
CLRA
Operation:
Description:
CCR Details:
Source Form
CLRA
CLRA
Clear A
0⇒A
All bits in accumulator A are cleared to 0.
S
X
H
I
N
Z
V
C
–
–
–
–
0
1
0
0
N:
Z:
V:
C:
0; cleared
1; set
0; cleared
0; cleared
Address
Mode
INH
Access Detail
Object Code
HCS12
87
O
S12CPUV2
MOTOROLA
M68HC12
O
Reference Manual
Instruction Glossary
153
Instruction Glossary
CLRB
Operation:
Description:
CCR Details:
Source Form
CLRB
CLRB
Clear B
0⇒B
All bits in accumulator B are cleared to 0.
S
X
H
I
N
Z
V
C
–
–
–
–
0
1
0
0
N:
Z:
V:
C:
0; cleared
1; set
0; cleared
0; cleared
Address
Mode
INH
Access Detail
Object Code
HCS12
C7
O
Reference Manual
154
M68HC12
O
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
CLV
Operation:
Description:
CCR Details:
Clear Two’s Complement Overflow Bit
CLV
0 ⇒ V bit
Clears the V status bit. This instruction is assembled as ANDCC #$FD.
The ANDCC instruction can be used to clear any combination of bits in
the CCR in one operation.
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
0
–
V: 0; cleared
Source Form
CLV
translates to... ANDCC #$FD
Address
Mode
IMM
Access Detail
Object Code
HCS12
10 FD
S12CPUV2
MOTOROLA
P
M68HC12
P
Reference Manual
Instruction Glossary
155
Instruction Glossary
CMPA
Operation:
Description:
CCR Details:
CMPA
Compare A
(A) – (M)
Compares the content of accumulator A to the content of memory
location M and sets the condition codes, which may then be used for
arithmetic and logical conditional branching. The contents of A and
location M are not changed.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: A7 • M7 • R7 + A7 • M7 • R7
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: A7 • M7 + M7 • R7 + R7 • A7
Set if there was a borrow from the MSB of the result; cleared
otherwise
Source Form
CMPA #opr8i
CMPA opr8a
CMPA opr16a
CMPA oprx0_xysp
CMPA oprx9,xysp
CMPA oprx16,xysp
CMPA [D,xysp]
CMPA [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
81 ii
91 dd
B1 hh ll
A1 xb
A1 xb ff
A1 xb ee ff
A1 xb
A1 xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
Reference Manual
156
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
CMPB
Operation:
Description:
CCR Details:
CMPB
Compare B
(B) – (M)
Compares the content of accumulator B to the content of memory
location M and sets the condition codes, which may then be used for
arithmetic and logical conditional branching. The contents of B and
location M are not changed.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: B7 • M7 • R7 + B7 • M7 • R7
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: B7 • M7 + M7 • R7 + R7 • B7
Set if there was a borrow from the MSB of the result; cleared
otherwise
Source Form
CMPB #opr8i
CMPB opr8a
CMPB opr16a
CMPB oprx0_xysp
CMPB oprx9,xysp
CMPB oprx16,xysp
CMPB [D,xysp]
CMPB [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
C1 ii
D1 dd
F1 hh ll
E1 xb
E1 xb ff
E1 xb ee ff
E1 xb
E1 xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
157
Instruction Glossary
COM
Operation:
Description:
CCR Details:
Source Form
COM opr16a
COM oprx0_xysp
COM oprx9,xysp
COM oprx16,xysp
COM [D,xysp]
COM [oprx16,xysp]
(M) = $FF – (M) ⇒ M
Replaces the content of memory location M with its one’s complement.
Each bit of M is complemented. Immediately after a COM operation on
unsigned values, only the BEQ, BNE, LBEQ, and LBNE branches can
be expected to perform consistently. After operation on two’s
complement values, all signed branches are available.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
1
N:
Z:
V:
C:
Set if MSB of result is set; cleared otherwise
Set if result is $00; cleared otherwise
0; cleared
1; set (for M6800 compatibility)
Access Detail
Address
Mode
Object Code
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
71 hh ll
61 xb
61 xb ff
61 xb ee ff
61 xb
61 xb ee ff
HCS12
M68HC12
rPwO
rPw
rPwO
frPwP
fIfrPw
fIPrPw
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
Reference Manual
158
COM
Complement Memory
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
COMA
Operation:
Description:
CCR Details:
Source Form
COMA
(A) = $FF – (A) ⇒ A
Replaces the content of accumulator A with its one’s complement. Each
bit of A is complemented. Immediately after a COM operation on
unsigned values, only the BEQ, BNE, LBEQ, and LBNE branches can
be expected to perform consistently. After operation on two’s
complement values, all signed branches are available.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
1
N:
Z:
V:
C:
Set if MSB of result is set; cleared otherwise
Set if result is $00; cleared otherwise
0; cleared
1; set (for M6800 compatibility)
Address
Mode
INH
Access Detail
Object Code
HCS12
41
0
S12CPUV2
MOTOROLA
COMA
Complement A
M68HC12
0
Reference Manual
Instruction Glossary
159
Instruction Glossary
COMB
Operation:
Description:
CCR Details:
Source Form
COMB
(B) = $FF – (B) ⇒ B
Replaces the content of accumulator B with its one’s complement. Each
bit of B is complemented. Immediately after a COM operation on
unsigned values, only the BEQ, BNE, LBEQ, and LBNE branches can
be expected to perform consistently. After operation on two’s
complement values, all signed branches are available.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
1
N:
Z:
V:
C:
Set if MSB of result is set; cleared otherwise
Set if result is $00; cleared otherwise
0; cleared
1; set (for M6800 compatibility)
Address
Mode
INH
Access Detail
Object Code
HCS12
51
0
Reference Manual
160
COMB
Complement B
M68HC12
0
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
CPD
Operation:
Description:
CCR Details:
Compare Double Accumulator
CPD
(A : B) – (M : M + 1)
Compares the content of double accumulator D with a 16-bit value at the
address specified and sets the condition codes accordingly. The
compare is accomplished internally by a 16-bit subtract of (M : M + 1)
from D without modifying either D or (M : M + 1).
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: D15 • M15 • R15 + D15 • M15 • R15
Set if two’s complement overflow resulted from the operation;
cleared otherwise
C: D15 • M15 + M15 • R15 + R15 • D15
Set if the absolute value of the content of memory is larger than the
absolute value of the accumulator; cleared otherwise
Source Form
CPD #opr16i
CPD opr8a
CPD opr16a
CPD oprx0_xysp
CPD oprx9,xysp
CPD oprx16,xysp
CPD [D,xysp]
CPD [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
8C jj kk
9C dd
BC hh ll
AC xb
AC xb ff
AC xb ee ff
AC xb
AC xb ee ff
HCS12
M68HC12
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
161
Instruction Glossary
CPS
Operation:
Description:
CCR Details:
CPS
Compare Stack Pointer
(SP) – (M : M + 1)
Compares the content of the SP with a 16-bit value at the address
specified, and sets the condition codes accordingly. The compare is
accomplished internally by doing a 16-bit subtract of (M : M + 1) from the
SP without modifying either the SP or (M : M + 1).
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: S15 • M15 • R15 + S15 • M15 • R15
Set if two’s complement overflow resulted from the operation;
cleared otherwise
C: S15 • M15 + M15 • R15 + R15 • S15
Set if the absolute value of the content of memory is larger than the
absolute value of the SP; cleared otherwise
Source Form
CPS #opr16i
CPS opr8a
CPS opr16a
CPS oprx0_xysp
CPS oprx9,xysp
CPS oprx16,xysp
CPS [D,xysp]
CPS [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
8F jj kk
9F dd
BF hh ll
AF xb
AF xb ff
AF xb ee ff
AF xb
AF xb ee ff
HCS12
M68HC12
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
Reference Manual
162
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
CPX
Operation:
Description:
CCR Details:
CPX
Compare Index Register X
(X) – (M : M + 1)
Compares the content of index register X with a 16-bit value at the
address specified and sets the condition codes accordingly. The
compare is accomplished internally by a 16-bit subtract of (M : M + 1)
from index register X without modifying either index register X or
(M : M + 1).
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: X15 • M15 • R15 + X15 • M15 • R15
Set if two’s complement overflow resulted from the operation;
cleared otherwise
C: X15 • M15 + M15 • R15 + R15 • X15
Set if the absolute value of the content of memory is larger than the
absolute value of the index register; cleared otherwise
Source Form
CPX #opr16i
CPX opr8a
CPX opr16a
CPX oprx0_xysp
CPX oprx9,xysp
CPX oprx16,xysp
CPX [D,xysp]
CPX [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
8E jj kk
9E dd
BE hh ll
AE xb
AE xb ff
AE xb ee ff
AE xb
AE xb ee ff
HCS12
M68HC12
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
S12CPUV2
MOTOROLA
Reference Manual
Instruction Glossary
163
Instruction Glossary
CPY
Operation:
Description:
CCR Details:
CPY
Compare Index Register Y
(Y) – (M : M + 1)
Compares the content of index register Y to a 16-bit value at the address
specified and sets the condition codes accordingly. The compare is
accomplished internally by a 16-bit subtract of (M : M + 1) from Y without
modifying either Y or (M : M + 1).
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: Y15 • M15 • R15 + Y15 • M15 • R15
Set if two’s complement overflow resulted from the operation;
cleared otherwise
C: Y15 • M15 + M15 • R15 + R15 • Y15
Set if the absolute value of the content of memory is larger than the
absolute value of the index register; cleared otherwise
Source Form
CPY #opr16i
CPY opr8a
CPY opr16a
CPY oprx0_xysp
CPY oprx9,xysp
CPY oprx16,xysp
CPY [D,xysp]
CPY [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
8D jj kk
9D dd
BD hh ll
AD xb
AD xb ff
AD xb ee ff
AD xb
AD xb ee ff
HCS12
M68HC12
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
Reference Manual
164
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
DAA
Description:
CCR Details:
Source Form
DAA
DAA adjusts the content of accumulator A and the state of the C status
bit to represent the correct binary-coded-decimal sum and the
associated carry when a BCD calculation has been performed. To
execute DAA, the content of accumulator A, the state of the C status bit,
and the state of the H status bit must all be the result of performing an
ABA, ADD, or ADC on BCD operands, with or without an initial carry.
The table shows DAA operation for all legal combinations of input
operands. Columns 1 through 4 represent the results of ABA, ADC, or
ADD operations on BCD operands. The correction factor in column 5 is
added to the accumulator to restore the result of an operation on two
BCD operands to a valid BCD value and to set or clear the C bit. All
values are in hexadecimal.
1
Initial
C Bit Value
0
0
0
0
0
0
1
1
1
2
Value
of A[7:4]
0–9
0–8
0–9
A–F
9–F
A–F
0–2
0–2
0–3
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
?
∆
N:
Z:
V:
C:
Set if MSB of result is set; cleared otherwise
Set if result is $00; cleared otherwise
Undefined
Represents BCD carry. See bit table
Address
Mode
INH
3
Initial
H Bit Value
0
0
1
0
0
1
0
0
1
4
Value
of A[3:0]
0–9
A–F
0–3
0–9
A–F
0–3
0–9
A–F
0–3
5
Correction
Factor
00
06
06
60
66
66
60
66
66
6
Corrected
C Bit Value
0
0
0
1
1
1
1
1
1
Access Detail
Object Code
HCS12
18 07
OfO
S12CPUV2
MOTOROLA
DAA
Decimal Adjust A
M68HC12
OfO
Reference Manual
Instruction Glossary
165
Instruction Glossary
DBEQ
Operation:
Description:
DBEQ
Decrement and Branch if Equal to Zero
(Counter) – 1 ⇒ Counter
If (Counter) = 0, then (PC) + $0003 + Rel ⇒ PC
Subtract one from the specified counter register A, B, D, X, Y, or SP. If
the counter register has reached zero, execute a branch to the specified
relative destination. The DBEQ instruction is encoded into three bytes of
machine code including the 9-bit relative offset (–256 to +255 locations
from the start of the next instruction).
IBEQ and TBEQ instructions are similar to DBEQ except that the counter
is incremented or tested rather than being decremented. Bits 7 and 6 of
the instruction postbyte are used to determine which operation is to be
performed.
CCR Details:
Source Form
DBEQ abdxys, rel9
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code(1)
HCS12
04 lb rr
M68HC12
PPP/PPO
PPP
1. Encoding for lb is summarized in the following table. Bit 3 is not used (don’t care), bit 5 selects branch on zero
(DBEQ – 0) or not zero (DBNE – 1) versions, and bit 4 is the sign bit of the 9-bit relative offset. Bits 7 and 6 would be 0:0
for DBEQ.
Count
Register
Bits 2:0
Source Form
Object Code
Object Code
(If Offset is Positive) (If Offset is Negative)
A
B
000
001
DBEQ A, rel9
DBEQ B, rel9
04 00 rr
04 01 rr
04 10 rr
04 11 rr
D
X
Y
SP
100
101
110
111
DBEQ D, rel9
DBEQ X, rel9
DBEQ Y, rel9
DBEQ SP, rel9
04 04 rr
04 05 rr
04 06 rr
04 07 rr
04 14 rr
04 15 rr
04 16 rr
04 17 rr
Reference Manual
166
S12CPUV2
Instruction Glossary
MOTOROLA
Instruction Glossary
Glossary
DBNE
Operation:
Description:
Decrement and Branch if Not Equal to Zero
DBNE
(Counter) – 1 ⇒ Counter
If (Counter) not = 0, then (PC) + $0003 + Rel ⇒ PC
Subtract one from the specified counter register A, B, D, X, Y, or SP. If
the counter register has not been decremented to zero, execute a
branch to the specified relative destination. The DBNE instruction is
encoded into three bytes of machine code including a 9-bit relative offset
(–256 to +255 locations from the start of the next instruction).
IBNE and TBNE instructions are similar to DBNE except that the counter
is incremented or tested rather than being decremented. Bits 7 and 6 of
the instruction postbyte are used to determine which operation is to be
performed.
CCR Details:
Source Form
DBNE abdxys, rel9
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code(1)
HCS12
04 lb rr
M68HC12
PPP/PPO
PPP
1. Encoding for lb is summarized in the following table. Bit 3 is not used (don’t care), bit 5 selects branch on zero (DBEQ – 0)
or not zero (DBNE – 1) versions, and bit 4 is the sign bit of the 9-bit relative offset. Bits 7 and 6 would be 0:0 for DBNE.
Count
Register
Bits 2:0
Source Form
Object Code
Object Code
(If Offset is Positive) (If Offset is Negative)
A
B
000
001
DBNE A, rel9
DBNE B, rel9
04 20 rr
04 21 rr
04 30 rr
04 31 rr
D
X
Y
SP
100
101
110
111
DBNE D, rel9
DBNE X, rel9
DBNE Y, rel9
DBNE SP, rel9
04 24 rr
04 25 rr
04 26 rr
04 27 rr
04 34 rr
04 35 rr
04 36 rr
04 37 rr
S12CPUV2
Reference Manual
MOTOROLA
167
Instruction Glossary
DEC
Operation:
Description:
DEC
Decrement Memory
(M) – $01 ⇒ M
Subtract one from the content of memory location M.
The N, Z, and V status bits are set or cleared according to the results of
the operation. The C status bit is not affected by the operation, thus
allowing the DEC instruction to be used as a loop counter in
multiple-precision computations.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: Set if there was a two’s complement overflow as a result of the
operation; cleared otherwise. Two’s complement overflow occurs
if and only if (M) was $80 before the operation.
Source Form
DEC opr16a
DEC oprx0_xysp
DEC oprx9,xysp
DEC oprx16,xysp
DEC [D,xysp]
DEC [oprx16,xysp]
Address
Mode
Object Code(1)
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
73 hh ll
63 xb
63 xb ff
63 xb ee ff
63 xb
63 xb ee ff
Access Detail
HCS12
M68HC12
rPwO
rPw
rPwO
frPwP
fIfrPw
fIPrPw
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
1. Encoding for lb is summarized in the following table. Bit 3 is not used (don’t care), bit 5 selects branch on zero (DBEQ – 0)
or not zero (DBNE – 1) versions, and bit 4 is the sign bit of the 9-bit relative offset. Bits 7 and 6 would be 0:0 for DBNE.
Reference Manual
S12CPUV2
168
MOTOROLA
Instruction Glossary
Glossary
DECA
Operation:
Description:
DECA
Decrement A
(A) – $01 ⇒ A
Subtract one from the content of accumulator A.
The N, Z, and V status bits are set or cleared according to the results of
the operation. The C status bit is not affected by the operation, thus
allowing the DEC instruction to be used as a loop counter in
multiple-precision computations.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: Set if there was a two’s complement overflow as a result of the
operation; cleared otherwise. Two’s complement overflow occurs if
and only if (A) was $80 before the operation.
Source Form
DECA
Address
Mode
INH
Access Detail
Object Code
HCS12
43
O
M68HC12
O
S12CPUV2
Reference Manual
MOTOROLA
169
Instruction Glossary
DECB
Operation:
Description:
DECB
Decrement B
(B) – $01 ⇒ B
Subtract one from the content of accumulator B.
The N, Z, and V status bits are set or cleared according to the results of
the operation. The C status bit is not affected by the operation, thus
allowing the DEC instruction to be used as a loop counter in
multiple-precision computations.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: Set if there was a two’s complement overflow as a result of the
operation; cleared otherwise. Two’s complement overflow occurs if
and only if (B) was $80 before the operation.
Source Form
DECB
Address
Mode
INH
Access Detail
Object Code
HCS12
53
O
M68HC12
O
Reference Manual
S12CPUV2
170
MOTOROLA
Instruction Glossary
Glossary
DES
Operation:
Description:
Decrement Stack Pointer
DES
(SP) – $0001 ⇒ SP
Subtract one from the SP. This instruction assembles to LEAS –1,SP.
The LEAS instruction does not affect condition codes as DEX or DEY
instructions do.
CCR Details:
Source Form
DES
translates to... LEAS –1,SP
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
IDX
Access Detail
Object Code
HCS12
1B 9F
Pf
M68HC12
PP(1)
1. Due to internal M68HC12 CPU requirements, the program word fetch is performed twice to the same address during this
instruction.
S12CPUV2
Reference Manual
MOTOROLA
171
Instruction Glossary
DEX
Operation:
Description:
DEX
Decrement Index Register X
(X) – $0001 ⇒ X
Subtract one from index register X. LEAX –1,X can produce the same
result, but LEAX does not affect the Z bit. Although the LEAX instruction
is more flexible, DEX requires only one byte of object code.
Only the Z bit is set or cleared according to the result of this operation.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
–
∆
–
–
Z: Set if result is $0000; cleared otherwise
Source Form
DEX
Address
Mode
INH
Access Detail
Object Code
HCS12
09
O
M68HC12
O
Reference Manual
S12CPUV2
172
MOTOROLA
Instruction Glossary
Glossary
DEY
Operation:
Description:
DEY
Decrement Index Register Y
(Y) – $0001 ⇒ Y
Subtract one from index register Y. LEAY –1,Y can produce the same
result, but LEAY does not affect the Z bit. Although the LEAY instruction
is more flexible, DEY requires only one byte of object code.
Only the Z bit is set or cleared according to the result of this operation.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
–
∆
–
–
Z: Set if result is $0000; cleared otherwise
Source Form
DEY
Address
Mode
INH
Access Detail
Object Code
HCS12
03
O
M68HC12
O
S12CPUV2
Reference Manual
MOTOROLA
173
Instruction Glossary
EDIV
Operation:
Description:
CCR Details:
Extended Divide 32-Bit by 16-Bit
(Unsigned)
EDIV
(Y : D) ÷ (X) ⇒ Y; Remainder ⇒ D
Divides a 32-bit unsigned dividend by a 16-bit divisor, producing a 16-bit
unsigned quotient and an unsigned 16-bit remainder. All operands and
results are located in CPU registers. If an attempt to divide by zero is
made, C is set and the states of the N, Z, and V bits in the CCR are
undefined. In case of an overflow or a divide by zero, the contents of the
registers D and Y do not change.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Undefined after overflow or division by zero
Z: Set if result is $0000; cleared otherwise
Undefined after overflow or division by zero
V: Set if the result was > $FFFF; cleared otherwise Undefined after
division by zero
C: Set if divisor was $0000; cleared otherwise
Source Form
EDIV
Address
Mode
INH
Access Detail
Object Code
HCS12
11
ffffffffffO
M68HC12
ffffffffffO
Reference Manual
S12CPUV2
174
MOTOROLA
Instruction Glossary
Glossary
EDIVS
Operation:
Description:
CCR Details:
EDIVS
Extended Divide 32-Bit by 16-Bit
(Signed)
(Y : D) ÷ (X) ⇒ Y; Remainder ⇒ D
Divides a signed 32-bit dividend by a 16-bit signed divisor, producing a
signed 16-bit quotient and a signed 16-bit remainder. All operands and
results are located in CPU registers. If an attempt to divide by zero is
made, C is set and the states of the N, Z, and V bits in the CCR are
undefined. In case of an overflow or a divide by zero, the contents of the
registers D and Y do not change.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Undefined after overflow or division by zero
Z: Set if result is $0000; cleared otherwise
Undefined after overflow or division by zero
V: Set if the result was > $7FFF or < $8000; cleared otherwise
Undefined after division by zero
C: Set if divisor was $0000; cleared otherwise
Indicates division by zero
Source Form
EDIVS
Address
Mode
INH
Access Detail
Object Code
HCS12
18 14
OffffffffffO
M68HC12
OffffffffffO
S12CPUV2
Reference Manual
MOTOROLA
175
Instruction Glossary
Extended Multiply and Accumulate
(Signed)
16-Bit by 16-Bit to 32-Bit
EMACS
Operation:
Description:
CCR Details:
EMACS
(M(X) : M(X+1)) × (M(Y) : M(Y+1)) + (M ~ M+3) ⇒ M ~ M+3
A 16-bit value is multiplied by a 16-bit value to produce a 32-bit
intermediate result. This 32-bit intermediate result is then added to the
content of a 32-bit accumulator in memory. EMACS is a signed integer
operation. All operands and results are located in memory. When the
EMACS instruction is executed, the first source operand is fetched from
an address pointed to by X, and the second source operand is fetched
from an address pointed to by index register Y. Before the instruction is
executed, the X and Y index registers must contain values that point to
the most significant bytes of the source operands. The most significant
byte of the 32-bit result is specified by an extended address supplied
with the instruction.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00000000; cleared otherwise
V: M31 • I31 • R31 + M31 • I31 • R31
Set if result > $7FFFFFFF (+ overflow) or
< $80000000 (– underflow)
Indicates two’s complement overflow
C: M15 • I15 + I15 • R15 + R15 • M15
Set if there was a carry from bit 15 of the result; cleared otherwise
Indicates a carry from low word to high word of the result occurred
Source Form(1)
EMACS opr16a
Access Detail
Address
Mode
Object Code
Special
18 12 hh ll
HCS12
ORROfffRRfWWP
M68HC12
ORROfffRRfWWP
1. opr16a is an extended address specification. Both X and Y point to source operands.
Reference Manual
S12CPUV2
176
MOTOROLA
Instruction Glossary
Glossary
Place Larger of Two
Unsigned 16-Bit Values
in Accumulator D
EMAXD
Operation:
Description:
EMAXD
MAX ((D), (M : M + 1)) ⇒ D
Subtracts an unsigned 16-bit value in memory from an unsigned 16-bit
value in double accumulator D to determine which is larger, and leaves
the larger of the two values in D. The Z status bit is set when the result
of the subtraction is zero (the values are equal), and the C status bit is
set when the subtraction requires a borrow (the value in memory is
larger than the value in the accumulator). When C = 1, the value in D has
been replaced by the value in memory.
The unsigned value in memory is accessed by means of indexed
addressing modes, which allow a great deal of flexibility in specifying the
address of the operand. Auto increment/decrement variations of indexed
addressing facilitate finding the largest value in a list of values.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: D15 • M15 • R15 + D15 • M15 • R15
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: D15 • M15 + M15 • R15 + R15 • D15
Set if the value of the content of memory is larger than the value of
the accumulator; cleared otherwise
Condition codes reflect internal subtraction (R = D – M : M + 1)
Source Form
EMAXD oprx0_xysp
EMAXD oprx9,xysp
EMAXD oprx16,xysp
EMAXD [D,xysp]
EMAXD [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
18 1A xb
18 1A xb ff
18 1A xb ee ff
18 1A xb
18 1A xb ee ff
HCS12
M68HC12
ORPf
ORPO
OfRPP
OfIfRPf
OfIPRPf
ORfP
ORPO
OfRPP
OfIfRfP
OfIPRfP
S12CPUV2
Reference Manual
MOTOROLA
177
Instruction Glossary
Place Larger of Two
Unsigned 16-Bit Values
in Memory
EMAXM
Operation:
Description:
EMAXM
MAX ((D), (M : M + 1)) ⇒ M : M + 1
Subtracts an unsigned 16-bit value in memory from an unsigned 16-bit
value in double accumulator D to determine which is larger, and leaves
the larger of the two values in the memory location. The Z status bit is
set when the result of the subtraction is zero (the values are equal), and
the C status bit is set when the subtraction requires a borrow (the value
in memory is larger than the value in the accumulator). When C = 0, the
value in D has replaced the value in memory.
The unsigned value in memory is accessed by means of indexed
addressing modes, which allow a great deal of flexibility in specifying the
address of the operand.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: D15 • M15 • R15 + D15 • M15 • R15
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: D15 • M15 + M15 • R15 + R15 • D15
Set if the value of the content of memory is larger than the value of
the accumulator; cleared otherwise
Condition codes reflect internal subtraction (R = D – M : M + 1)
Source Form
EMAXM oprx0_xysp
EMAXM oprx9,xysp
EMAXM oprx16,xysp
EMAXM [D,xysp]
EMAXM [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
18 1E xb
18 1E xb ff
18 1E xb ee ff
18 1E xb
18 1E xb ee ff
HCS12
M68HC12
ORPW
ORPWO
OfRPWP
OfIfRPW
OfIPRPW
ORPW
ORPWO
OfRPWP
OfIfRPW
OfIPRPW
Reference Manual
S12CPUV2
178
MOTOROLA
Instruction Glossary
Glossary
Place Smaller of Two
Unsigned 16-Bit Values
in Accumulator D
EMIND
Operation:
Description:
EMIND
MIN ((D), (M : M + 1)) ⇒ D
Subtracts an unsigned 16-bit value in memory from an unsigned 16-bit
value in double accumulator D to determine which is larger, and leaves
the smaller of the two values in D. The Z status bit is set when the result
of the subtraction is zero (the values are equal), and the C status bit is
set when the subtraction requires a borrow (the value in memory is
larger than the value in the accumulator). When C = 0, the value in D has
been replaced by the value in memory.
The unsigned value in memory is accessed by means of indexed
addressing modes, which allow a great deal of flexibility in specifying the
address of the operand. Auto increment/decrement variations of indexed
addressing facilitate finding the smallest value in a list of values.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: D15 • M15 • R15 + D15 • M15 • R15
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: D15 • M15 + M15 • R15 + R15 • D15
Set if the value of the content of memory is larger than the value of
the accumulator; cleared otherwise
Condition codes reflect internal subtraction (R = D – M : M + 1)
Source Form
EMIND oprx0_xysp
EMIND oprx9,xysp
EMIND oprx16,xysp
EMIND [D,xysp]
EMIND [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
18 1B xb
18 1B xb ff
18 1B xb ee ff
18 1B xb
18 1B xb ee ff
HCS12
M68HC12
ORPf
ORPO
OfRPP
OfIfRPf
OfIPRPf
ORfP
ORPO
OfRPP
OfIfRfP
OfIPRfP
S12CPUV2
Reference Manual
MOTOROLA
179
Instruction Glossary
Place Smaller of Two
Unsigned 16-Bit Values
in Memory
EMINM
Operation:
Description:
EMINM
MIN ((D), (M : M + 1)) ⇒ M : M + 1
Subtracts an unsigned 16-bit value in memory from an unsigned 16-bit
value in double accumulator D to determine which is larger and leaves
the smaller of the two values in the memory location. The Z status bit is
set when the result of the subtraction is zero (the values are equal), and
the C status bit is set when the subtraction requires a borrow (the value
in memory is larger than the value in the accumulator). When C = 1, the
value in D has replaced the value in memory.
The unsigned value in memory is accessed by means of indexed
addressing modes, which allow a great deal of flexibility in specifying the
address of the operand.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: D15 • M15 • R15 + D15 • M15 • R15
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: D15 • M15 + M15 • R15 + R15 • D15
Set if the value of the content of memory is larger than the value of
the accumulator; cleared otherwise
Condition codes reflect internal subtraction (R = D – M : M + 1)
Source Form
EMINM oprx0_xysp
EMINM oprx9,xysp
EMINM oprx16,xysp
EMINM [D,xysp]
EMINM [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
18 1F xb
18 1F xb ff
18 1F xb ee ff
18 1F xb
18 1F xb ee ff
HCS12
M68HC12
ORPW
ORPWO
OfRPWP
OfIfRPW
OfIPRPW
ORPW
ORPWO
OfRPWP
OfIfRPW
OfIPRPW
Reference Manual
S12CPUV2
180
MOTOROLA
Instruction Glossary
Glossary
EMUL
Operation:
Description:
Extended Multiply
16-Bit by 16-Bit (Unsigned)
EMUL
(D) × (Y) ⇒ Y : D
An unsigned 16-bit value is multiplied by an unsigned 16-bit value to
produce an unsigned 32-bit result. The first source operand must be
loaded into 16-bit double accumulator D and the second source operand
must be loaded into index register Y before executing the instruction.
When the instruction is executed, the value in D is multiplied by the value
in Y. The upper 16-bits of the 32-bit result are stored in Y and the
low-order 16-bits of the result are stored in D.
The C status bit can be used to round the high-order 16 bits of the result.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
–
∆
N: Set if the MSB of the result is set; cleared otherwise
Z: Set if result is $00000000; cleared otherwise
C: Set if bit 15 of the result is set; cleared otherwise
Source Form
EMUL
Address
Mode
INH
Access Detail
Object Code
HCS12
13
ffO
M68HC12
ffO
S12CPUV2
Reference Manual
MOTOROLA
181
Instruction Glossary
A
EMULS
Operation:
Description:
Extended Multiply
16-Bit by 16-Bit (Signed)
EMULS
(D) × (Y) ⇒ Y : D
A signed 16-bit value is multiplied by a signed 16-bit value to produce a
signed 32-bit result. The first source operand must be loaded into 16-bit
double accumulator D, and the second source operand must be loaded
into index register Y before executing the instruction. When the
instruction is executed, D is multiplied by the value Y. The 16 high-order
bits of the 32-bit result are stored in Y and the 16 low-order bits of the
result are stored in D.
The C status bit can be used to round the high-order 16 bits of the result.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
–
∆
N: Set if the MSB of the result is set; cleared otherwise
Z: Set if result is $00000000; cleared otherwise
C: Set if bit 15 of the result is set; cleared otherwise
Source Form
EMULS
Address
Mode
INH
Access Detail
Object Code
18 13
HCS12
M68HC12
OfO
OffO(1)
OfO
1. EMULS has an extra free cycle if it is followed by another PAGE TWO instruction.
Reference Manual
S12CPUV2
182
MOTOROLA
Instruction Glossary
Glossary
EORA
Operation:
Description:
CCR Details:
EORA
Exclusive OR A
(A) ⊕ (M) ⇒ A
Performs the logical exclusive OR between the content of accumulator
A and the content of memory location M. The result is placed in A. Each
bit of A after the operation is the logical exclusive OR of the
corresponding bits of M and A before the operation.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: 0; cleared
Source Form
EORA #opr8i
EORA opr8a
EORA opr16a
EORA oprx0_xysp
EORA oprx9,xysp
EORA oprx16,xysp
EORA [D,xysp]
EORA [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
88 ii
98 dd
B8 hh ll
A8 xb
A8 xb ff
A8 xb ee ff
A8 xb
A8 xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
S12CPUV2
Reference Manual
MOTOROLA
183
Instruction Glossary
EORB
Operation:
Description:
CCR Details:
EORB
Exclusive OR B
(B) ⊕ (M) ⇒ B
Performs the logical exclusive OR between the content of accumulator
B and the content of memory location M. The result is placed in A. Each
bit of A after the operation is the logical exclusive OR of the
corresponding bits of M and B before the operation.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: 0; cleared
Source Form
EORB #opr8i
EORB opr8a
EORB opr16a
EORB oprx0_xysp
EORB oprx9,xysp
EORB oprx16,xysp
EORB [D,xysp]
EORB [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
C8 ii
D8 dd
F8 hh ll
E8 xb
E8 xb ff
E8 xb ee ff
E8 xb
E8 xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
Reference Manual
S12CPUV2
184
MOTOROLA
Instruction Glossary
Glossary
ETBL
Operation:
Description:
Extended Table Lookup and Interpolate
ETBL
(M : M + 1) + [(B) × ((M + 2 : M + 3) – (M : M + 1))] ⇒ D
ETBL linearly interpolates one of 256 result values that fall between
each pair of data entries in a lookup table stored in memory. Data entries
in the table represent the y values of endpoints of equally-spaced line
segments. Table entries and the interpolated result are 16-bit values.
The result is stored in the D accumulator.
Before executing ETBL, an index register points to the table entry
corresponding to the x value (X1 that is closest to, but less than or equal
to, the desired lookup point (XL, YL). This defines the left end of a line
segment and the right end is defined by the next data entry in the table.
Prior to execution, accumulator B holds a binary fraction (radix left of
MSB) representing the ratio of (XL–X1) ÷ (X2–X1).
The 16-bit unrounded result is calculated using the following expression:
D = Y1 + [(B) × (Y2 – Y1)]
Where:
(B) = (XL – X1) ÷ (X2 – X1)
Y1 = 16-bit data entry pointed to by <effective address>
Y2 = 16-bit data entry pointed to by <effective address> + 2
The intermediate value [(B) × (Y2 – Y1)] produces a 24-bit result with the
radix point between bits 7 and 8. Any indexed addressing mode, except
indirect modes or 9-bit and 16-bit offset modes, can be used to identify
the first data point (X1,Y1). The second data point is the next table entry.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
–
∆(1)
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
C: Set if result can be rounded up; cleared otherwise
1. C-bit was undefined in original M68HC12
Source Form
ETBL oprx0_xysp
Address
Mode
IDX
Access Detail
Object Code
HCS12
18 3F xb
ORRffffffP
M68HC12
ORRffffffP
S12CPUV2
Reference Manual
MOTOROLA
185
Instruction Glossary
EXG
EXG
Exchange Register Contents
Operation:
Description:
See table
Exchanges the contents of registers specified in the instruction as shown
below. Note that the order in which exchanges between 8-bit and 16-bit
registers are specified affects the high byte of the 16-bit registers
differently. Exchanges of D with A or B are ambiguous. Cases involving
TMP2 and TMP3 are reserved for Motorola use, so some assemblers
may not permit their use, but it is possible to generate these cases by
using DC.B or DC.W assembler directives.
S
CCR Details:
X
H
I
N
Z
V
C
Or:
–
–
–
–
–
–
–
–
S
X
H
I
N
Z
V
C
∆
⇓
∆
∆
∆
∆
∆
∆
None affected, unless the CCR is the destination register. Condition
codes take on the value of the corresponding source bits, except that the
X mask bit cannot change from 0 to 1. Software can leave the X bit set,
leave it cleared, or change it from 1 to 0, but it can be set only in
response to any reset or by recognition of an XIRQ interrupt.
Address
Mode
Source Form
EXG abcdxys,abcdxys
INH
Access Detail
Object Code(1)
HCS12
B7 eb
M68HC12
P
P
1. Legal coding for eb is summarized in the following table. Columns represent the high-order source digit. Rows represent
the low-order destination digit (bit 3 is a don’t care). Values are in hexadecimal.
8
9
A
B
C
D
E
F
TMP3L ⇒ A
$00:A ⇒ TMP3
B⇒A
A⇒B
XL ⇒ A
$00:A ⇒ X
YL ⇒ A
$00:A ⇒ Y
SPL ⇒ A
$00:A ⇒ SP
0
A⇔A
B⇔A
CCR ⇔ A
1
A⇔B
B⇔B
CCR ⇔ B
2
A ⇔ CCR
B ⇔ CCR
CCR ⇔ CCR
$00:A ⇒ TMP2 $00:B ⇒ TMP2 $00:CCR ⇒ TMP2
TMP2L ⇒ A
TMP2L ⇒ B
TMP2L ⇒ CCR
$00:CCR ⇒ D
$00:B ⇒ D
4 $00:A ⇒ D
B ⇒ CCR
$00:A ⇒ X
$00:B ⇒ X
$00:CCR ⇒ X
5
XL ⇒ A
XL ⇒ B
XL ⇒ CCR
$00:A ⇒ Y
$00:B ⇒ Y
$00:CCR ⇒ Y
6
YL ⇒ A
YL ⇒ B
YL ⇒ CCR
$00:A ⇒ SP
$00:B ⇒ SP
$00:CCR ⇒ SP
7
SPL ⇒ A
SPL ⇒ B
SPL ⇒ CCR
3
TMP3L ⇒ B
B⇒B
XL ⇒ B
YL ⇒ B
SPL ⇒ B
$FF:B ⇒ TMP3
$FF ⇒ A
$FF:B ⇒ X
$FF:B ⇒ Y
$FF:B ⇒ SP
TMP3L ⇒ CCR
B ⇒ CCR
XL ⇒ CCR
YL ⇒ CCR
SPL ⇒ CCR
$FF:CCR ⇒ TMP3 $FF:CCR ⇒ D $FF:CCR ⇒ X $FF:CCR ⇒ Y $FF:CCR ⇒ SP
TMP3 ⇔ TMP2
D ⇔ TMP2
X ⇔ TMP2
Y ⇔ TMP2
SP ⇔ TMP2
TMP3 ⇔ D
D⇔D
X⇔D
Y⇔D
SP ⇔ D
TMP3 ⇔ X
D⇔X
X⇔X
Y⇔X
SP ⇔ X
TMP3 ⇔ Y
D⇔Y
X⇔Y
Y⇔Y
SP ⇔ Y
TMP3 ⇔ SP
D ⇔ SP
X ⇔ SP
Y ⇔ SP
SP ⇔ SP
Reference Manual
S12CPUV2
186
MOTOROLA
Instruction Glossary
Glossary
FDIV
Operation:
Description:
FDIV
Fractional Divide
(D) ÷ (X) ⇒ X; Remainder ⇒ D
Divides an unsigned 16-bit numerator in double accumulator D by an
unsigned 16-bit denominator in index register X, producing an unsigned
16-bit quotient in X and an unsigned 16-bit remainder in D. If both the
numerator and the denominator are assumed to have radix points in the
same positions, the radix point of the quotient is to the left of bit 15. The
numerator must be less than the denominator. In the case of overflow
(denominator is less than or equal to the numerator) or division by zero,
the quotient is set to $FFFF, and the remainder is indeterminate.
FDIV is equivalent to multiplying the numerator by 216 and then
performing 32 by 16-bit integer division. The result is interpreted as a
binary-weighted fraction, which resulted from the division of a 16-bit
integer by a larger 16-bit integer. A result of $0001 corresponds to
0.000015, and $FFFF corresponds to 0.9998. The remainder of an IDIV
instruction can be resolved into a binary-weighted fraction by an FDIV
instruction. The remainder of an FDIV instruction can be resolved into
the next 16 bits of binary-weighted fraction by another FDIV instruction.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
–
∆
∆
∆
Z: Set if quotient is $0000; cleared otherwise
V: 1 if X ≤ D
Set if the denominator was less than or equal to the numerator;
cleared otherwise
C: X15 • X14 • X13 • X12 •... • X3 • X2 • X1 • X0
Set if denominator was $0000; cleared otherwise
Source Form
FDIV
Address
Mode
INH
Access Detail
Object Code
HCS12
18 11
OffffffffffO
M68HC12
OffffffffffO
S12CPUV2
Reference Manual
MOTOROLA
187
Instruction Glossary
IBEQ
Operation:
Description:
IBEQ
Increment and Branch if Equal to Zero
(Counter) + 1 ⇒ Counter
If (Counter) = 0, then (PC) + $0003 + Rel ⇒ PC
Add one to the specified counter register A, B, D, X, Y, or SP. If the
counter register has reached zero, branch to the specified relative
destination. The IBEQ instruction is encoded into three bytes of machine
code including a 9-bit relative offset (–256 to +255 locations from the
start of the next instruction).
DBEQ and TBEQ instructions are similar to IBEQ except that the counter
is decremented or tested rather than being incremented. Bits 7 and 6 of
the instruction postbyte are used to determine which operation is to be
performed.
CCR Details:
Source Form
IBEQ abdxys, rel9
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
Access Detail
Object Code(1)
HCS12
REL
04 lb rr
M68HC12
PPP/PPO
PPP
1. Encoding for lb is summarized in the following table. Bit 3 is not used (don’t care), bit 5 selects branch on zero (IBEQ –
0) or not zero (IBNE – 1) versions, and bit 0 is the sign bit of the 9-bit relative offset. Bits 7 and 6 should be 1:0 for IBEQ.
Count
Object Code
Bits 2:0 Source Form
Register
(If Offset is Positive)
Object Code
(If Offset is Negative)
A
B
000
001
IBEQ A, rel9
IBEQ B, rel9
04 80 rr
04 81 rr
04 90 rr
04 91 rr
D
X
Y
SP
100
101
110
111
IBEQ D, rel9
IBEQ X, rel9
IBEQ Y, rel9
IBEQ SP, rel9
04 84 rr
04 85 rr
04 86 rr
04 87 rr
04 94 rr
04 95 rr
04 96 rr
04 97 rr
Reference Manual
S12CPUV2
188
MOTOROLA
Instruction Glossary
Glossary
IBNE
Operation:
Description:
IBNE
Increment and Branch if Not Equal to Zero
(Counter) + 1 ⇒ Counter
If (Counter) not = 0, then (PC) + $0003 + Rel ⇒ PC
Add one to the specified counter register A, B, D, X, Y, or SP. If the
counter register has not been incremented to zero, branch to the
specified relative destination. The IBNE instruction is encoded into three
bytes of machine code including a 9-bit relative offset (–256 to +255
locations from the start of the next instruction).
DBNE and TBNE instructions are similar to IBNE except that the counter
is decremented or tested rather than being incremented. Bits 7 and 6 of
the instruction postbyte are used to determine which operation is to be
performed.
CCR Details:
Source Form
IBNE abdxys, rel9
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
Access Detail
Object Code(1)
HCS12
REL
04 lb rr
M68HC12
PPP/PPO
PPP
1. Encoding for lb is summarized in the following table. Bit 3 is not used (don’t care), bit 5 selects branch on zero (IBEQ –
0) or not zero (IBNE – 1) versions, and bit 0 is the sign bit of the 9-bit relative offset. Bits 7 and 6 should be 1:0 for IBNE.
Count
Object Code
Bits 2:0 Source Form
Register
(If Offset is Positive)
Object Code
(If Offset is Negative)
A
B
000
001
IBNE A, rel9
IBNE B, rel9
04 A0 rr
04 A1 rr
04 B0 rr
04 B1 rr
D
X
Y
SP
100
101
110
111
IBNE D, rel9
IBNE X, rel9
IBNE Y, rel9
IBNE SP, rel9
04 A4 rr
04 A5 rr
04 A6 rr
04 A7 rr
04 B4 rr
04 B5 rr
04 B6 rr
04 B7 rr
S12CPUV2
Reference Manual
MOTOROLA
189
Instruction Glossary
IDIV
Operation:
Description:
CCR Details:
IDIV
Integer Divide
(D) ÷ (X) ⇒ X; Remainder ⇒ D
Divides an unsigned 16-bit dividend in double accumulator D by an
unsigned 16-bit divisor in index register X, producing an unsigned 16-bit
quotient in X, and an unsigned 16-bit remainder in D. If both the divisor
and the dividend are assumed to have radix points in the same positions,
the radix point of the quotient is to the right of bit 0. In the case of division
by zero, C is set, the quotient is set to $FFFF, and the remainder is
indeterminate.
S
X
H
I
N
Z
V
C
–
–
–
–
–
∆
0
∆
Z: Set if quotient is $0000; cleared otherwise
V: 0; cleared
C: X15 • X14 • X13 • X12 •... • X3 • X2 • X1 • X0
Set if denominator was $0000; cleared otherwise
Source Form
IDIV
Address
Mode
INH
Access Detail
Object Code
HCS12
18 10
OffffffffffO
M68HC12
OffffffffffO
Reference Manual
S12CPUV2
190
MOTOROLA
Instruction Glossary
Glossary
IDIVS
Operation:
Description:
IDIVS
Integer Divide (Signed)
(D) ÷ (X) ⇒ X; Remainder ⇒ D
Performs signed integer division of a signed 16-bit numerator in double
accumulator D by a signed 16-bit denominator in index register X,
producing a signed 16-bit quotient in X, and a signed 16-bit remainder
in D. If division by zero is attempted, the values in D and X are not
changed, C is set, and the values of the N, Z, and V status bits are
undefined.
Other than division by zero, which is not legal and causes the C status
bit to be set, the only overflow case is:
$8000
–32,768
------------------ = --------------------- = +32,768
$FFFF
–1
But the highest positive value that can be represented in a 16-bit two’s
complement number is 32,767 ($7FFFF).
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Undefined after overflow or division by zero
Z: Set if quotient is $0000; cleared otherwise
Undefined after overflow or division by zero
V: Set if the result was > $7FFF or < $8000; cleared otherwise
Undefined after division by zero
C: X15 • X14 • X13 • X12 •... • X3 • X2 • X1 • X0
Set if denominator was $0000; cleared otherwise
Source Form
IDIVS
Address
Mode
INH
Access Detail
Object Code
HCS12
18 15
OffffffffffO
M68HC12
OffffffffffO
S12CPUV2
Reference Manual
MOTOROLA
191
Instruction Glossary
INC
Operation:
Description:
INC
Increment Memory
(M) + $01 ⇒ M
Add one to the content of memory location M.
The N, Z and V status bits are set or cleared according to the results of
the operation. The C status bit is not affected by the operation, thus
allowing the INC instruction to be used as a loop counter in
multiple-precision computations.
When operating on unsigned values, only BEQ, BNE, LBEQ, and LBNE
branches can be expected to perform consistently. When operating on
two’s complement values, all signed branches are available.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: Set if there is a two’s complement overflow as a result of the
operation; cleared otherwise. Two’s complement overflow occurs if
and only if (M) was $7F before the operation.
Source Form
INC opr16a
INC oprx0_xysp
INC oprx9,xysp
INC oprx16,xysp
INC [D,xysp]
INC [oprx16,xysp]
Access Detail
Address
Mode
Object Code
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
72 hh ll
62 xb
62 xb ff
62 xb ee ff
62 xb
62 xb ee ff
HCS12
M68HC12
rPwO
rPw
rPwO
frPwP
fIfrPw
fIPrPw
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
Reference Manual
S12CPUV2
192
MOTOROLA
Instruction Glossary
Glossary
INCA
Operation:
Description:
INCA
Increment A
(A) + $01 ⇒ A
Add one to the content of accumulator A.
The N, Z, and V status bits are set or cleared according to the results of
the operation. The C status bit is not affected by the operation, thus
allowing the INC instruction to be used as a loop counter in
multiple-precision computations.
When operating on unsigned values, only BEQ, BNE, LBEQ, and LBNE
branches can be expected to perform consistently. When operating on
two’s complement values, all signed branches are available.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: Set if there is a two’s complement overflow as a result of the
operation; cleared otherwise. Two’s complement overflow occurs if
and only if (A) was $7F before the operation.
Source Form
INCA
Address
Mode
INH
Access Detail
Object Code
HCS12
42
O
M68HC12
O
S12CPUV2
Reference Manual
MOTOROLA
193
Instruction Glossary
INCB
Operation:
Description:
INCB
Increment B
(B) + $01 ⇒ B
Add one to the content of accumulator B.
The N, Z, and V status bits are set or cleared according to the results of
the operation. The C status bit is not affected by the operation, thus
allowing the INC instruction to be used as a loop counter in
multiple-precision computations.
When operating on unsigned values, only BEQ, BNE, LBEQ, and LBNE
branches can be expected to perform consistently. When operating on
two’s complement values, all signed branches are available.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: Set if there is a two’s complement overflow as a result of the
operation; cleared otherwise. Two’s complement overflow occurs if
and only if (B) was $7F before the operation.
Source Form
INCB
Address
Mode
INH
Access Detail
Object Code
HCS12
52
O
M68HC12
O
Reference Manual
S12CPUV2
194
MOTOROLA
Instruction Glossary
Glossary
INS
Operation:
Description:
CCR Details:
Source Form
INS
translates to... LEAS 1,SP
INS
Increment Stack Pointer
(SP) + $0001 ⇒ SP
Add one to the SP. This instruction is assembled to LEAS 1,SP. The
LEAS instruction does not affect condition codes as an INX or INY
instruction would.
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
IDX
Access Detail
Object Code
HCS12
1B 81
Pf
M68HC12
PP(1)
1. Due to internal M68HC12 CPU requirements, the program word fetch is performed twice to the same address during this
instruction.
S12CPUV2
Reference Manual
MOTOROLA
195
Instruction Glossary
INX
Operation:
Description:
INX
Increment Index Register X
(X) + $0001 ⇒ X
Add one to index register X. LEAX 1,X can produce the same result but
LEAX does not affect the Z status bit. Although the LEAX instruction is
more flexible, INX requires only one byte of object code.
INX operation affects only the Z status bit.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
–
∆
–
–
Z: Set if result is $0000; cleared otherwise
Source Form
INX
Address
Mode
INH
Access Detail
Object Code
HCS12
08
O
M68HC12
O
Reference Manual
S12CPUV2
196
MOTOROLA
Instruction Glossary
Glossary
INY
Operation:
Description:
INY
Increment Index Register Y
(Y) + $0001 ⇒ Y
Add one to index register Y. LEAY 1,Y can produce the same result but
LEAY does not affect the Z status bit. Although the LEAY instruction is
more flexible, INY requires only one byte of object code.
INY operation affects only the Z status bit.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
–
∆
–
–
Z: Set if result is $0000; cleared otherwise
Source Form
INY
Address
Mode
INH
Access Detail
Object Code
HCS12
02
O
M68HC12
O
S12CPUV2
Reference Manual
MOTOROLA
197
Instruction Glossary
JMP
Operation:
Description:
CCR Details:
Source Form
JMP opr16a
JMP oprx0_xysp
JMP oprx9,xysp
JMP oprx16,xysp
JMP [D,xysp]
JMP [oprx16,xysp]
JMP
Jump
Effective Address ⇒ PC
Jumps to the instruction stored at the effective address. The effective
address is obtained according to the rules for extended or indexed
addressing.
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
06 hh ll
05 xb
05 xb ff
05 xb ee ff
05 xb
05 xb ee ff
HCS12
M68HC12
PPP
PPP
PPP
fPPP
fIfPPP
fIfPPP
PPP
PPP
PPP
fPPP
fIfPPP
fIfPPP
Reference Manual
S12CPUV2
198
MOTOROLA
Instruction Glossary
Glossary
JSR
Operation:
Description:
JSR
Jump to Subroutine
(SP) – $0002 ⇒ SP
RTNH : RTNL ⇒ M(SP) : M(SP + 1)
Subroutine Address ⇒ PC
Sets up conditions to return to normal program flow, then transfers
control to a subroutine. Uses the address of the instruction following the
JSR as a return address.
Decrements the SP by two to allow the two bytes of the return address
to be stacked.
Stacks the return address. The SP points to the high order byte of the
return address.
Calculates an effective address according to the rules for extended,
direct, or indexed addressing.
Jumps to the location determined by the effective address.
Subroutines are normally terminated with an RTS instruction, which
restores the return address from the stack.
CCR Details:
Source Form
JSR opr8a
JSR opr16a
JSR oprx0_xysp
JSR oprx9,xysp
JSR oprx16,xysp
JSR [D,xysp]
JSR [oprx16,xysp]
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
17 dd
16 hh ll
15 xb
15 xb ff
15 xb ee ff
15 xb
15 xb ee ff
HCS12
M68HC12
SPPP
SPPP
PPPS
PPPS
fPPPS
fIfPPPS
fIfPPPS
PPPS
PPPS
PPPS
PPPS
fPPPS
fIfPPPS
fIfPPPS
S12CPUV2
Reference Manual
MOTOROLA
199
Instruction Glossary
LBCC
Long Branch if Carry Cleared
(Same as LBHS)
Operation:
If C = 0, then (PC) + $0004 + Rel ⇒ PC
LBCC
Simple branch
Description:
Tests the C status bit and branches if C = 0.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBCC rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
REL
18 24 qq rr
HCS12
OPPP/OPO(1)
M68HC12
OPPP/OPO(1)
1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles
if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
LBGT
18 2E
LBGE
18 2C
LBEQ
18 27
LBLE
18 2F
LBLT
18 2D
LBHI
18 22
LBHS/LBCC
18 24
LBEQ
18 27
LBLS
18 23
LBLO/LBCS
18 25
LBCS
18 25
LBMI
18 2B
LBVS
18 29
LBEQ
18 27
LBRA
18 20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Complementary Branch
Mnemonic
Opcode
Comment
LBLE
18 2F
Signed
LBLT
18 2D
Signed
LBNE
18 26
Signed
LBGT
18 2E
Signed
LBGE
18 2C
Signed
LBLS
18 23
Unsigned
LBLO/LBCS
18 25
Unsigned
LBNE
18 26
Unsigned
LBHI
18 22
Unsigned
LBHS/LBCC
18 24
Unsigned
LBCC
18 24
Simple
LBPL
18 2A
Simple
LBVC
18 28
Simple
LBNE
18 26
Simple
LBRN
18 21
Unconditional
Reference Manual
S12CPUV2
200
MOTOROLA
Instruction Glossary
Glossary
LBCS
Operation:
Long Branch if Carry Set
(Same as LBLO)
LBCS
If C = 1, then (PC) + $0004 + Rel ⇒ PC
Simple branch
Description:
Tests the C status bit and branches if C = 1.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBCS rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
REL
18 25 qq rr
HCS12
OPPP/OPO(1)
M68HC12
OPPP/OPO(1)
1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles
if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
LBGT
18 2E
LBGE
18 2C
LBEQ
18 27
LBLE
18 2F
LBLT
18 2D
LBHI
18 22
LBHS/LBCC
18 24
LBEQ
18 27
LBLS
18 23
LBLO/LBCS
18 25
LBCS
18 25
LBMI
18 2B
LBVS
18 29
LBEQ
18 27
LBRA
18 20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Complementary Branch
Mnemonic
Opcode
Comment
LBLE
18 2F
Signed
LBLT
18 2D
Signed
LBNE
18 26
Signed
LBGT
18 2E
Signed
LBGE
18 2C
Signed
LBLS
18 23
Unsigned
LBLO/LBCS
18 25
Unsigned
LBNE
18 26
Unsigned
LBHI
18 22
Unsigned
LBHS/LBCC
18 24
Unsigned
LBCC
18 24
Simple
LBPL
18 2A
Simple
LBVC
18 28
Simple
LBNE
18 26
Simple
LBRN
18 21
Unconditional
S12CPUV2
Reference Manual
MOTOROLA
201
Instruction Glossary
LBEQ
Long Branch if Equal
Operation:
If Z = 1, (PC) + $0004 + Rel ⇒ PC
LBEQ
Simple branch
Description:
Tests the Z status bit and branches if Z = 1.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBEQ rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
REL
18 27 qq rr
HCS12
OPPP/OPO(1)
M68HC12
OPPP/OPO(1)
1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles
if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
LBGT
18 2E
LBGE
18 2C
LBEQ
18 27
LBLE
18 2F
LBLT
18 2D
LBHI
18 22
LBHS/LBCC
18 24
LBEQ
18 27
LBLS
18 23
LBLO/LBCS
18 25
LBCS
18 25
LBMI
18 2B
LBVS
18 29
LBEQ
18 27
LBRA
18 20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Complementary Branch
Mnemonic
Opcode
Comment
LBLE
18 2F
Signed
LBLT
18 2D
Signed
LBNE
18 26
Signed
LBGT
18 2E
Signed
LBGE
18 2C
Signed
LBLS
18 23
Unsigned
LBLO/LBCS
18 25
Unsigned
LBNE
18 26
Unsigned
LBHI
18 22
Unsigned
LBHS/LBCC
18 24
Unsigned
LBCC
18 24
Simple
LBPL
18 2A
Simple
LBVC
18 28
Simple
LBNE
18 26
Simple
LBRN
18 21
Unconditional
Reference Manual
S12CPUV2
202
MOTOROLA
Instruction Glossary
Glossary
LBGE
Operation:
Long Branch if Greater Than or Equal to Zero
LBGE
If N ⊕ V = 0, (PC) + $0004 + Rel ⇒ PC
For signed two’s complement numbers, if (Accumulator) ≥ Memory),
then branch
Description:
LBGE can be used to branch after subtracting or comparing signed two’s
complement values. After CMPA, CMPB, CPD, CPS, CPX, CPY, SBCA,
SBCB, SUBA, SUBB, or SUBD, the branch occurs if the CPU register
value is greater than or equal to the value in M. After CBA or SBA, the
branch occurs if the value in B is greater than or equal to the value in A.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBGE rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
HCS12
18 2C qq rr
OPPP/OPO(1)
M68HC12
OPPP/OPO(1)
1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles
if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
LBGT
18 2E
LBGE
18 2C
LBEQ
18 27
LBLE
18 2F
LBLT
18 2D
LBHI
18 22
LBHS/LBCC
18 24
LBEQ
18 27
LBLS
18 23
LBLO/LBCS
18 25
LBCS
18 25
LBMI
18 2B
LBVS
18 29
LBEQ
18 27
LBRA
18 20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Complementary Branch
Mnemonic
Opcode
Comment
LBLE
18 2F
Signed
LBLT
18 2D
Signed
LBNE
18 26
Signed
LBGT
18 2E
Signed
LBGE
18 2C
Signed
LBLS
18 23
Unsigned
LBLO/LBCS
18 25
Unsigned
LBNE
18 26
Unsigned
LBHI
18 22
Unsigned
LBHS/LBCC
18 24
Unsigned
LBCC
18 24
Simple
LBPL
18 2A
Simple
LBVC
18 28
Simple
LBNE
18 26
Simple
LBRN
18 21
Unconditional
S12CPUV2
Reference Manual
MOTOROLA
203
Instruction Glossary
LBGT
Operation:
LBGT
Long Branch if Greater Than Zero
If Z + (N ⊕ V) = 0, then (PC) + $0004 + Rel ⇒ PC
For signed two’s complement numbers, If (Accumulator) > (Memory),
then branch
Description:
LBGT can be used to branch after subtracting or comparing signed two’s
complement values. After CMPA, CMPB, CPD, CPS, CPX, CPY, SBCA,
SBCB, SUBA, SUBB, or SUBD, the branch occurs if the CPU register
value is greater than or equal to the value in M. After CBA or SBA, the
branch occurs if the value in B is greater than or equal to the value in A.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBGT rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
HCS12
18 2E qq rr
OPPP/OPO(1)
M68HC12
OPPP/OPO(1)
1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles
if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
LBGT
18 2E
LBGE
18 2C
LBEQ
18 27
LBLE
18 2F
LBLT
18 2D
LBHI
18 22
LBHS/LBCC
18 24
LBEQ
18 27
LBLS
18 23
LBLO/LBCS
18 25
LBCS
18 25
LBMI
18 2B
LBVS
18 29
LBEQ
18 27
LBRA
18 20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Complementary Branch
Mnemonic
Opcode
Comment
LBLE
18 2F
Signed
LBLT
18 2D
Signed
LBNE
18 26
Signed
LBGT
18 2E
Signed
LBGE
18 2C
Signed
LBLS
18 23
Unsigned
LBLO/LBCS
18 25
Unsigned
LBNE
18 26
Unsigned
LBHI
18 22
Unsigned
LBHS/LBCC
18 24
Unsigned
LBCC
18 24
Simple
LBPL
18 2A
Simple
LBVC
18 28
Simple
LBNE
18 26
Simple
LBRN
18 21
Unconditional
Reference Manual
S12CPUV2
204
MOTOROLA
Instruction Glossary
Glossary
LBHI
Operation:
Long Branch if Higher
LBHI
If C + Z = 0, then (PC) + $0004 + Rel ⇒ PC
For unsigned binary numbers, if (Accumulator) > (Memory), then branch
Description:
LBHI can be used to branch after subtracting or comparing unsigned
values. After CMPA, CMPB, CPD, CPS, CPX, CPY, SBCA, SBCB,
SUBA, SUBB, or SUBD, the branch occurs if the CPU register value is
greater than the value in M. After CBA or SBA, the branch occurs if the
value in B is greater than the value in A. LBHI should not be used for
branching after instructions that do not affect the C bit, such as
increment, decrement, load, store, test, clear, or complement.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBHI rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
HCS12
18 22 qq rr
OPPP/OPO(1)
M68HC12
OPPP/OPO(1)
1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles
if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
LBGT
18 2E
LBGE
18 2C
LBEQ
18 27
LBLE
18 2F
LBLT
18 2D
LBHI
18 22
LBHS/LBCC
18 24
LBEQ
18 27
LBLS
18 23
LBLO/LBCS
18 25
LBCS
18 25
LBMI
18 2B
LBVS
18 29
LBEQ
18 27
LBRA
18 20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Complementary Branch
Mnemonic
Opcode
Comment
LBLE
18 2F
Signed
LBLT
18 2D
Signed
LBNE
18 26
Signed
LBGT
18 2E
Signed
LBGE
18 2C
Signed
LBLS
18 23
Unsigned
LBLO/LBCS
18 25
Unsigned
LBNE
18 26
Unsigned
LBHI
18 22
Unsigned
LBHS/LBCC
18 24
Unsigned
LBCC
18 24
Simple
LBPL
18 2A
Simple
LBVC
18 28
Simple
LBNE
18 26
Simple
LBRN
18 21
Unconditional
S12CPUV2
Reference Manual
MOTOROLA
205
Instruction Glossary
LBHS
Operation:
Long Branch if Higher or Same
(Same as LBCC)
LBHS
If C = 0, then (PC) + $0004 + Rel ⇒ PC
For unsigned binary numbers, if (Accumulator) ≥ (Memory), then branch
Description:
LBHS can be used to branch after subtracting or comparing unsigned
values. After CMPA, CMPB, CPD, CPS, CPX, CPY, SBCA, SBCB,
SUBA, SUBB, or SUBD, the branch occurs if the CPU register value is
greater than or equal to the value in M. After CBA or SBA, the branch
occurs if the value in B is greater than or equal to the value in A. LBHS
should not be used for branching after instructions that do not affect the
C bit, such as increment, decrement, load, store, test, clear, or
complement.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBHS rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
HCS12
18 24 qq rr
OPPP/OPO(1)
M68HC12
OPPP/OPO(1)
1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles
if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
LBGT
18 2E
LBGE
18 2C
LBEQ
18 27
LBLE
18 2F
LBLT
18 2D
LBHI
18 22
LBHS/LBCC
18 24
LBEQ
18 27
LBLS
18 23
LBLO/LBCS
18 25
LBCS
18 25
LBMI
18 2B
LBVS
18 29
LBEQ
18 27
LBRA
18 20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Complementary Branch
Mnemonic
Opcode
Comment
LBLE
18 2F
Signed
LBLT
18 2D
Signed
LBNE
18 26
Signed
LBGT
18 2E
Signed
LBGE
18 2C
Signed
LBLS
18 23
Unsigned
LBLO/LBCS
18 25
Unsigned
LBNE
18 26
Unsigned
LBHI
18 22
Unsigned
LBHS/LBCC
18 24
Unsigned
LBCC
18 24
Simple
LBPL
18 2A
Simple
LBVC
18 28
Simple
LBNE
18 26
Simple
LBRN
18 21
Unconditional
Reference Manual
S12CPUV2
206
MOTOROLA
Instruction Glossary
Glossary
LBLE
Operation:
Long Branch if Less Than or Equal to Zero
LBLE
If Z + (N ⊕ V) = 1, then (PC) + $0004 + Rel ⇒ PC
For signed two’s complement numbers, if (Accumulator) ≤ (Memory),
then branch.
Description:
LBLE can be used to branch after subtracting or comparing signed two’s
complement values. After CMPA, CMPB, CPD, CPS, CPX, CPY, SBCA,
SBCB, SUBA, SUBB, or SUBD, the branch occurs if the CPU register
value is less than or equal to the value in M. After CBA or SBA, the
branch occurs if the value in B is less than or equal to the value in A.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBLE rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
REL
18 2F qq rr
HCS12
OPPP/OPO(1)
M68HC12
OPPP/OPO(1)
1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles
if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
LBGT
18 2E
LBGE
18 2C
LBEQ
18 27
LBLE
18 2F
LBLT
18 2D
LBHI
18 22
LBHS/LBCC
18 24
LBEQ
18 27
LBLS
18 23
LBLO/LBCS
18 25
LBCS
18 25
LBMI
18 2B
LBVS
18 29
LBEQ
18 27
LBRA
18 20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Complementary Branch
Mnemonic
Opcode
Comment
LBLE
18 2F
Signed
LBLT
18 2D
Signed
LBNE
18 26
Signed
LBGT
18 2E
Signed
LBGE
18 2C
Signed
LBLS
18 23
Unsigned
LBLO/LBCS
18 25
Unsigned
LBNE
18 26
Unsigned
LBHI
18 22
Unsigned
LBHS/LBCC
18 24
Unsigned
LBCC
18 24
Simple
LBPL
18 2A
Simple
LBVC
18 28
Simple
LBNE
18 26
Simple
LBRN
18 21
Unconditional
S12CPUV2
Reference Manual
MOTOROLA
207
Instruction Glossary
LBLO
Operation:
LBLO
Long Branch if Lower
(Same as LBCS)
If C = 1, then (PC) + $0004 + Rel ⇒ PC
For unsigned binary numbers, if (Accumulator) < (Memory), then branch
Description:
LBLO can be used to branch after subtracting or comparing unsigned
values. After CMPA, CMPB, CPD, CPS, CPX, CPY, SUBA, SUBB, or
SUBD, the branch occurs if the CPU register value is less than the value
in M. After CBA or SBA, the branch occurs if the value in B is less than
the value in A. LBLO should not be used for branching after instructions
that do not affect the C bit, such as increment, decrement, load, store,
test, clear, or complement.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBLO rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
REL
18 25 qq rr
HCS12
OPPP/OPO(1)
M68HC12
OPPP/OPO(1)
1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles
if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
LBGT
18 2E
LBGE
18 2C
LBEQ
18 27
LBLE
18 2F
LBLT
18 2D
LBHI
18 22
LBHS/LBCC
18 24
LBEQ
18 27
LBLS
18 23
LBLO/LBCS
18 25
LBCS
18 25
LBMI
18 2B
LBVS
18 29
LBEQ
18 27
LBRA
18 20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Complementary Branch
Mnemonic
Opcode
Comment
LBLE
18 2F
Signed
LBLT
18 2D
Signed
LBNE
18 26
Signed
LBGT
18 2E
Signed
LBGE
18 2C
Signed
LBLS
18 23
Unsigned
LBLO/LBCS
18 25
Unsigned
LBNE
18 26
Unsigned
LBHI
18 22
Unsigned
LBHS/LBCC
18 24
Unsigned
LBCC
18 24
Simple
LBPL
18 2A
Simple
LBVC
18 28
Simple
LBNE
18 26
Simple
LBRN
18 21
Unconditional
Reference Manual
S12CPUV2
208
MOTOROLA
Instruction Glossary
Glossary
LBLS
Operation:
Long Branch if Lower or Same
LBLS
If C + Z = 1, then (PC) + $0004 + Rel ⇒ PC
For unsigned binary numbers, if (Accumulator) ≤ (Memory), then branch
Description:
LBLS can be used to branch after subtracting or comparing unsigned
values. After CMPA, CMPB, CPD, CPS, CPX, CPY, SBCA, SBCB,
SUBA, SUBB, or SUBD, the branch occurs if the CPU register value is
less than or equal to the value in M. After CBA or SBA, the branch occurs
if the value in B is less than or equal to the value in A. LBLS should not
be used for branching after instructions that do not affect the C bit, such
as increment, decrement, load, store, test, clear, or complement.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBLS rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
REL
18 23 qq rr
HCS12
OPPP/OPO(1)
M68HC12
OPPP/OPO(1)
1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles
if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
LBGT
18 2E
LBGE
18 2C
LBEQ
18 27
LBLE
18 2F
LBLT
18 2D
LBHI
18 22
LBHS/LBCC
18 24
LBEQ
18 27
LBLS
18 23
LBLO/LBCS
18 25
LBCS
18 25
LBMI
18 2B
LBVS
18 29
LBEQ
18 27
LBRA
18 20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Complementary Branch
Mnemonic
Opcode
Comment
LBLE
18 2F
Signed
LBLT
18 2D
Signed
LBNE
18 26
Signed
LBGT
18 2E
Signed
LBGE
18 2C
Signed
LBLS
18 23
Unsigned
LBLO/LBCS
18 25
Unsigned
LBNE
18 26
Unsigned
LBHI
18 22
Unsigned
LBHS/LBCC
18 24
Unsigned
LBCC
18 24
Simple
LBPL
18 2A
Simple
LBVC
18 28
Simple
LBNE
18 26
Simple
LBRN
18 21
Unconditional
S12CPUV2
Reference Manual
MOTOROLA
209
Instruction Glossary
LBLT
Operation:
Long Branch if Less Than Zero
LBLT
If N ⊕ V = 1, (PC) + $0004 + Rel ⇒ PC
For signed two’s complement numbers, if (Accumulator) < (Memory),
then branch
Description:
LBLT can be used to branch after subtracting or comparing signed two-s
complement values. After CMPA, CMPB, CPD, CPS, CPX, CPY, SBCA,
SBCB, SUBA, SUBB, or SUBD, the branch occurs if the CPU register
value is less than the value in M. After CBA or SBA, the branch occurs
if the value in B is less than the value in A.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBLT rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
HCS12
18 2D qq rr
OPPP/OPO(1)
M68HC12
OPPP/OPO(1)
1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles
if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
LBGT
18 2E
LBGE
18 2C
LBEQ
18 27
LBLE
18 2F
LBLT
18 2D
LBHI
18 22
LBHS/LBCC
18 24
LBEQ
18 27
LBLS
18 23
LBLO/LBCS
18 25
LBCS
18 25
LBMI
18 2B
LBVS
18 29
LBEQ
18 27
LBRA
18 20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Complementary Branch
Mnemonic
Opcode
Comment
LBLE
18 2F
Signed
LBLT
18 2D
Signed
LBNE
18 26
Signed
LBGT
18 2E
Signed
LBGE
18 2C
Signed
LBLS
18 23
Unsigned
LBLO/LBCS
18 25
Unsigned
LBNE
18 26
Unsigned
LBHI
18 22
Unsigned
LBHS/LBCC
18 24
Unsigned
LBCC
18 24
Simple
LBPL
18 2A
Simple
LBVC
18 28
Simple
LBNE
18 26
Simple
LBRN
18 21
Unconditional
Reference Manual
S12CPUV2
210
MOTOROLA
Instruction Glossary
Glossary
LBMI
Operation:
LBMI
Long Branch if Minus
If N = 1, then (PC) + $0004 + Rel ⇒ PC
Simple branch
Description:
Tests the N status bit and branches if N = 1.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBMI rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
REL
18 2B qq rr
HCS12
OPPP/OPO(1)
M68HC12
OPPP/OPO(1)
1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles
if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
LBGT
18 2E
LBGE
18 2C
LBEQ
18 27
LBLE
18 2F
LBLT
18 2D
LBHI
18 22
LBHS/LBCC
18 24
LBEQ
18 27
LBLS
18 23
LBLO/LBCS
18 25
LBCS
18 25
LBMI
18 2B
LBVS
18 29
LBEQ
18 27
LBRA
18 20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Complementary Branch
Mnemonic
Opcode
Comment
LBLE
18 2F
Signed
LBLT
18 2D
Signed
LBNE
18 26
Signed
LBGT
18 2E
Signed
LBGE
18 2C
Signed
LBLS
18 23
Unsigned
LBLO/LBCS
18 25
Unsigned
LBNE
18 26
Unsigned
LBHI
18 22
Unsigned
LBHS/LBCC
18 24
Unsigned
LBCC
18 24
Simple
LBPL
18 2A
Simple
LBVC
18 28
Simple
LBNE
18 26
Simple
LBRN
18 21
Unconditional
S12CPUV2
Reference Manual
MOTOROLA
211
Instruction Glossary
LBNE
Operation:
Long Branch if Not Equal to Zero
LBNE
If Z = 0, then (PC) + $0004 + Rel ⇒ PC
Simple branch
Description:
Tests the Z status bit and branches if Z = 0.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBNE rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
REL
18 26 qq rr
HCS12
OPPP/OPO(1)
M68HC12
OPPP/OPO(1)
1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles
if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
LBGT
18 2E
LBGE
18 2C
LBEQ
18 27
LBLE
18 2F
LBLT
18 2D
LBHI
18 22
LBHS/LBCC
18 24
LBEQ
18 27
LBLS
18 23
LBLO/LBCS
18 25
LBCS
18 25
LBMI
18 2B
LBVS
18 29
LBEQ
18 27
LBRA
18 20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Complementary Branch
Mnemonic
Opcode
Comment
LBLE
18 2F
Signed
LBLT
18 2D
Signed
LBNE
18 26
Signed
LBGT
18 2E
Signed
LBGE
18 2C
Signed
LBLS
18 23
Unsigned
LBLO/LBCS
18 25
Unsigned
LBNE
18 26
Unsigned
LBHI
18 22
Unsigned
LBHS/LBCC
18 24
Unsigned
LBCC
18 24
Simple
LBPL
18 2A
Simple
LBVC
18 28
Simple
LBNE
18 26
Simple
LBRN
18 21
Unconditional
Reference Manual
S12CPUV2
212
MOTOROLA
Instruction Glossary
Glossary
LBPL
Operation:
LBPL
Long Branch if Plus
If N = 0, then (PC) + $0004 + Rel ⇒ PC
Simple branch
Description:
Tests the N status bit and branches if N = 0.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBPL rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
REL
18 2A qq rr
HCS12
OPPP/OPO(1)
M68HC12
OPPP/OPO(1)
1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles
if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
LBGT
18 2E
LBGE
18 2C
LBEQ
18 27
LBLE
18 2F
LBLT
18 2D
LBHI
18 22
LBHS/LBCC
18 24
LBEQ
18 27
LBLS
18 23
LBLO/LBCS
18 25
LBCS
18 25
LBMI
18 2B
LBVS
18 29
LBEQ
18 27
LBRA
18 20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Complementary Branch
Mnemonic
Opcode
Comment
LBLE
18 2F
Signed
LBLT
18 2D
Signed
LBNE
18 26
Signed
LBGT
18 2E
Signed
LBGE
18 2C
Signed
LBLS
18 23
Unsigned
LBLO/LBCS
18 25
Unsigned
LBNE
18 26
Unsigned
LBHI
18 22
Unsigned
LBHS/LBCC
18 24
Unsigned
LBCC
18 24
Simple
LBPL
18 2A
Simple
LBVC
18 28
Simple
LBNE
18 26
Simple
LBRN
18 21
Unconditional
S12CPUV2
Reference Manual
MOTOROLA
213
Instruction Glossary
LBRA
Operation:
Description:
Long Branch Always
LBRA
(PC) + $0004 + Rel ⇒ PC
Unconditional branch to an address calculated as shown in the
expression. Rel is a relative offset stored as a two’s complement number
in the second and third bytes of machine code corresponding to the long
branch instruction.
Execution time is longer when a conditional branch is taken than when
it is not, because the instruction queue must be refilled before execution
resumes at the new address. Since the LBRA branch condition is always
satisfied, the branch is always taken, and the instruction queue must
always be refilled, so execution time is always the larger value.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBRA rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
REL
18 20 qq rr
HCS12
OPPP
M68HC12
OPPP
Reference Manual
S12CPUV2
214
MOTOROLA
Instruction Glossary
Glossary
LBRN
Operation:
Description:
Long Branch Never
LBRN
(PC) + $0004 ⇒ PC
Never branches. LBRN is effectively a 4-byte NOP that requires three
cycles to execute. LBRN is included in the instruction set to provide a
complement to the LBRA instruction. The instruction is useful during
program debug, to negate the effect of another branch instruction
without disturbing the offset byte. A complement for LBRA is also useful
in compiler implementations.
Execution time is longer when a conditional branch is taken than when
it is not, because the instruction queue must be refilled before execution
resumes at the new address. Since the LBRN branch condition is never
satisfied, the branch is never taken, and the queue does not need to be
refilled, so execution time is always the smaller value.
CCR Details:
Source Form
LBRN rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
REL
18 21 qq rr
HCS12
OPO
M68HC12
OPO
S12CPUV2
Reference Manual
MOTOROLA
215
Instruction Glossary
LBVC
Operation:
Long Branch if Overflow Cleared
LBVC
If V = 0, then (PC) + $0004 + Rel ⇒ PC
Simple branch
Description:
Tests the V status bit and branches if V = 0.
LBVC causes a branch when a previous operation on two’s complement
binary values does not cause an overflow. That is, when LBVC follows a
two’s complement operation, a branch occurs when the result of the
operation is valid.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBVC rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
HCS12
18 28 qq rr
OPPP/OPO(1)
M68HC12
OPPP/OPO(1)
1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles
if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
LBGT
18 2E
LBGE
18 2C
LBEQ
18 27
LBLE
18 2F
LBLT
18 2D
LBHI
18 22
LBHS/LBCC
18 24
LBEQ
18 27
LBLS
18 23
LBLO/LBCS
18 25
LBCS
18 25
LBMI
18 2B
LBVS
18 29
LBEQ
18 27
LBRA
18 20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Complementary Branch
Mnemonic
Opcode
Comment
LBLE
18 2F
Signed
LBLT
18 2D
Signed
LBNE
18 26
Signed
LBGT
18 2E
Signed
LBGE
18 2C
Signed
LBLS
18 23
Unsigned
LBLO/LBCS
18 25
Unsigned
LBNE
18 26
Unsigned
LBHI
18 22
Unsigned
LBHS/LBCC
18 24
Unsigned
LBCC
18 24
Simple
LBPL
18 2A
Simple
LBVC
18 28
Simple
LBNE
18 26
Simple
LBRN
18 21
Unconditional
Reference Manual
S12CPUV2
216
MOTOROLA
Instruction Glossary
Glossary
LBVS
Operation:
Long Branch if Overflow Set
LBVS
If V = 1, then (PC) + $0004 + Rel ⇒ PC
Simple branch
Description:
Tests the V status bit and branches if V = 1.
LBVS causes a branch when a previous operation on two’s complement
binary values causes an overflow. That is, when LBVS follows a two’s
complement operation, a branch occurs when the result of the operation
is invalid.
See 3.8 Relative Addressing Mode for details of branch execution.
CCR Details:
Source Form
LBVS rel16
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
REL
Access Detail
Object Code
HCS12
18 29 qq rr
OPPP/OPO(1)
M68HC12
OPPP/OPO(1)
1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles
if the branch is not taken.
Test
r>m
r≥m
r=m
r≤m
r<m
r>m
r≥m
r=m
r≤m
r<m
Carry
Negative
Overflow
r=0
Always
Branch
Mnemonic
Opcode
LBGT
18 2E
LBGE
18 2C
LBEQ
18 27
LBLE
18 2F
LBLT
18 2D
LBHI
18 22
LBHS/LBCC
18 24
LBEQ
18 27
LBLS
18 23
LBLO/LBCS
18 25
LBCS
18 25
LBMI
18 2B
LBVS
18 29
LBEQ
18 27
LBRA
18 20
Boolean
Test
Z + (N ⊕ V) = 0
r≤m
N⊕V=0
r<m
Z=1
r≠m
Z + (N ⊕ V) = 1
r>m
N⊕V=1
r≥m
C+Z=0
r≤m
C=0
r<m
Z=1
r≠m
C+Z=1
r>m
C=1
r≥m
C=1
No Carry
N=1
Plus
V=1
No Overflow
Z=1
r≠0
—
Never
Complementary Branch
Mnemonic
Opcode
Comment
LBLE
18 2F
Signed
LBLT
18 2D
Signed
LBNE
18 26
Signed
LBGT
18 2E
Signed
LBGE
18 2C
Signed
LBLS
18 23
Unsigned
LBLO/LBCS
18 25
Unsigned
LBNE
18 26
Unsigned
LBHI
18 22
Unsigned
LBHS/LBCC
18 24
Unsigned
LBCC
18 24
Simple
LBPL
18 2A
Simple
LBVC
18 28
Simple
LBNE
18 26
Simple
LBRN
18 21
Unconditional
S12CPUV2
Reference Manual
MOTOROLA
217
Instruction Glossary
LDAA
Operation:
Description:
CCR Details:
LDAA
Load Accumulator A
(M) ⇒ A
Loads the content of memory location M into accumulator A. The
condition codes are set according to the data.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: 0; cleared
Source Form
LDAA #opr8i
LDAA opr8a
LDAA opr16a
LDAA oprx0_xysp
LDAA oprx9,xysp
LDAA oprx16,xysp
LDAA [D,xysp]
LDAA [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
86 ii
96 dd
B6 hh ll
A6 xb
A6 xb ff
A6 xb ee ff
A6 xb
A6 xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
Reference Manual
S12CPUV2
218
MOTOROLA
Instruction Glossary
Glossary
LDAB
Operation:
Description:
CCR Details:
LDAB
Load Accumulator B
(M) ⇒ B
Loads the content of memory location M into accumulator B. The
condition codes are set according to the data.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: 0; cleared
Source Form
LDAB #opr8i
LDAB opr8a
LDAB opr16a
LDAB oprx0_xysp
LDAB oprx9,xysp
LDAB oprx16,xysp
LDAB [D,xysp]
LDAB [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
C6 ii
D6 dd
F6 hh ll
E6 xb
E6 xb ff
E6 xb ee ff
E6 xb
E6 xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
S12CPUV2
Reference Manual
MOTOROLA
219
Instruction Glossary
LDD
Operation:
Description:
CCR Details:
LDD
Load Double Accumulator
(M : M+1) ⇒ A : B
Loads the contents of memory locations M and M+1 into double
accumulator D. The condition codes are set according to the data. The
information from M is loaded into accumulator A, and the information
from M+1 is loaded into accumulator B.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: 0; cleared
Source Form
LDD #opr16i
LDD opr8a
LDD opr16a
LDD oprx0_xysp
LDD oprx9,xysp
LDD oprx16,xysp
LDD [D,xysp]
LDD [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
CC jj kk
DC dd
FC hh ll
EC xb
EC xb ff
EC xb ee ff
EC xb
EC xb ee ff
HCS12
M68HC12
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
Reference Manual
S12CPUV2
220
MOTOROLA
Instruction Glossary
Glossary
LDS
Operation:
Description:
CCR Details:
LDS
Load Stack Pointer
(M : M+1) ⇒ SP
Loads the most significant byte of the SP with the content of memory
location M, and loads the least significant byte of the SP with the content
of the next byte of memory at M+1.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: 0; cleared
Source Form
LDS #opr16i
LDS opr8a
LDS opr16a
LDS oprx0_xysp
LDS oprx9,xysp
LDS oprx16,xysp
LDS [D,xysp]
LDS [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
CF jj kk
DF dd
FF hh ll
EF xb
EF xb ff
EF xb ee ff
EF xb
EF xb ee ff
HCS12
M68HC12
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
S12CPUV2
Reference Manual
MOTOROLA
221
Instruction Glossary
LDX
Operation:
Description:
CCR Details:
LDX
Load Index Register X
(M : M+1) ⇒ X
Loads the most significant byte of index register X with the content of
memory location M, and loads the least significant byte of X with the
content of the next byte of memory at M+1.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: 0; cleared
Source Form
LDX #opr16i
LDX opr8a
LDX opr16a
LDX oprx0_xysp
LDX oprx9,xysp
LDX oprx16,xysp
LDX [D,xysp]
LDX [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
CE jj kk
DE dd
FE hh ll
EE xb
EE xb ff
EE xb ee ff
EE xb
EE xb ee ff
HCS12
M68HC12
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
Reference Manual
S12CPUV2
222
MOTOROLA
Instruction Glossary
Glossary
LDY
Operation:
Description:
CCR Details:
LDY
Load Index Register Y
(M : M+1) ⇒ Y
Loads the most significant byte of index register Y with the content of
memory location M, and loads the least significant byte of Y with the
content of the next memory location at M+1.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: 0; cleared
Source Form
LDY #opr16i
LDY opr8a
LDY opr16a
LDY oprx0_xysp
LDY oprx9,xysp
LDY oprx16,xysp
LDY [D,xysp]
LDY [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
CD jj kk
DD dd
FD hh ll
ED xb
ED xb ff
ED xb ee ff
ED xb
ED xb ee ff
HCS12
M68HC12
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
S12CPUV2
Reference Manual
MOTOROLA
223
Instruction Glossary
LEAS
Operation:
Description:
Load Stack Pointer with Effective Address
LEAS
Effective Address ⇒ SP
Loads the stack pointer with an effective address specified by the
program. The effective address can be any indexed addressing mode
operand address except an indirect address. Indexed addressing mode
operand addresses are formed by adding an optional constant supplied
by the program or an accumulator value to the current value in X, Y, SP,
or PC. See 3.9 Indexed Addressing Modes for more details.
LEAS does not alter condition code bits. This allows stack modification
without disturbing CCR bits changed by recent arithmetic operations.
Operation is a bit more complex when LEAS is used with auto-increment
or auto-decrement operand specifications and the SP is the referenced
index register. The index register is loaded with what would have gone
out to the address bus in the case of a load index instruction. In the case
of a pre-increment or pre-decrement, the modification is made before the
index register is loaded. In the case of a post-increment or
post-decrement, modification would have taken effect after the address
went out on the address bus, so post-modification does not affect the
content of the index register.
In the unusual case where LEAS involves two different index registers
and post-increment or post-decrement, both index registers are modified
as demonstrated by the following example. Consider the instruction
LEAS 4,Y+. First S is loaded with the value of Y, then Y is incremented
by 4.
CCR Details:
Source Form
LEAS oprx0_xysp
LEAS oprx9,xysp
LEAS oprx16,xysp
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
IDX
IDX1
IDX2
1B xb
1B xb ff
1B xb ee ff
HCS12
Pf
PO
PP
M68HC12
PP(1)
PO
PP
1. Due to internal M68HC12 CPU requirements, the program word fetch is performed twice to the same address during this
instruction.
Reference Manual
S12CPUV2
224
MOTOROLA
Instruction Glossary
Glossary
LEAX
Operation:
Description:
Load X with Effective Address
LEAX
Effective Address ⇒ X
Loads index register X with an effective address specified by the
program. The effective address can be any indexed addressing mode
operand address except an indirect address. Indexed addressing mode
operand addresses are formed by adding an optional constant supplied
by the program or an accumulator value to the current value in X, Y, SP,
or PC. See 3.9 Indexed Addressing Modes for more details.
Operation is a bit more complex when LEAX is used with auto-increment
or auto-decrement operand specifications and index register X is the
referenced index register. The index register is loaded with what would
have gone out to the address bus in the case of a load indexed
instruction. In the case of a pre-increment or pre-decrement, the
modification is made before the index register is loaded. In the case of a
post-increment or post-decrement, modification would have taken effect
after the address went out on the address bus, so post-modification does
not affect the content of the index register.
In the unusual case where LEAX involves two different index registers
and post-increment and post-decrement, both index registers are
modified as demonstrated by the following example. Consider the
instruction LEAX 4,Y+. First X is loaded with the value of Y, then Y is
incremented by 4.
CCR Details:
Source Form
LEAX oprx0_xysp
LEAX oprx9,xysp
LEAX oprx16,xysp
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
IDX
IDX1
IDX2
1A xb
1A xb ff
1A xb ee ff
HCS12
Pf
PO
PP
M68HC12
PP(1)
PO
PP
1. Due to internal M68HC12 CPU requirements, the program word fetch is performed twice to the same address during this
instruction.
S12CPUV2
Reference Manual
MOTOROLA
225
Instruction Glossary
LEAY
Operation:
Description:
Load Y with Effective Address
LEAY
Effective Address ⇒ Y
Loads index register Y with an effective address specified by the
program. The effective address can be any indexed addressing mode
operand address except an indirect address. Indexed addressing mode
operand addresses are formed by adding an optional constant supplied
by the program or an accumulator value to the current value in X, Y, SP,
or PC. See 3.9 Indexed Addressing Modes for more details.
Operation is a bit more complex when LEAY is used with auto-increment
or auto-decrement operand specifications and index register Y is the
referenced index register. The index register is loaded with what would
have gone out to the address bus in the case of a load indexed
instruction. In the case of a pre-increment or pre-decrement, the
modification is made before the index register is loaded. In the case of a
post-increment or post-decrement, modification would have taken effect
after the address went out on the address bus, so post-modification does
not affect the content of the index register.
In the unusual case where LEAY involves two different index registers
and post-increment and post-decrement, both index registers are
modified as demonstrated by the following example. Consider the
instruction LEAY 4,X+. First Y is loaded with the value of X, then X is
incremented by 4.
CCR Details:
Source Form
LEAY oprx0_xysp
LEAY oprx9,xysp
LEAY oprx16,xysp
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Access Detail
Address
Mode
Object Code
IDX
IDX1
IDX2
19 xb
19 xb ff
19 xb ee ff
HCS12
Pf
PO
PP
M68HC12
PP(1)
PO
PP
1. Due to internal M68HC12 CPU requirements, the program word fetch is performed twice to the same address during this
instruction.
Reference Manual
S12CPUV2
226
MOTOROLA
Instruction Glossary
Glossary
LSL
LSL
Logical Shift Left Memory
(Same as ASL)
Operation:
C
Description:
CCR Details:
b7 – – – – – – b0
0
Shifts all bits of the memory location M one place to the left. Bit 0 is
loaded with 0. The C status bit is loaded from the most significant bit
of M.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: M7
Set if the LSB of M was set before the shift; cleared otherwise
Source Form
LSL opr16a
LSL oprx0_xysp
LSL oprx9,xysp
LSL oprx16,xysp
LSL [D,xysp]
LSL [oprx16,xysp]
Access Detail
Address
Mode
Object Code
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
78 hh ll
68 xb
68 xb ff
68 xb ee ff
68 xb
68 xb ee ff
HCS12
M68HC12
rPwO
rPw
rPwO
frPwP
fIfrPw
fIPrPw
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
S12CPUV2
Reference Manual
MOTOROLA
227
Instruction Glossary
LSLA
LSLA
Logical Shift Left A
(Same as ASLA)
Operation:
C
Description:
CCR Details:
b7 – – – – – – b0
0
Shifts all bits of accumulator A one place to the left. Bit 0 is loaded with 0.
The C status bit is loaded from the most significant bit of A.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: A7
Set if the LSB of A was set before the shift; cleared otherwise
Source Form
LSLA
Address
Mode
INH
Access Detail
Object Code
HCS12
48
O
M68HC12
O
Reference Manual
S12CPUV2
228
MOTOROLA
Instruction Glossary
Glossary
LSLB
LSLB
Logical Shift Left B
(Same as ASLB)
Operation:
C
Description:
CCR Details:
b7 – – – – – – b0
0
Shifts all bits of accumulator B one place to the left. Bit 0 is loaded with 0.
The C status bit is loaded from the most significant bit of B.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: B7
Set if the LSB of B was set before the shift; cleared otherwise
Source Form
LSLB
Address
Mode
INH
Access Detail
Object Code
HCS12
58
O
M68HC12
O
S12CPUV2
Reference Manual
MOTOROLA
229
Instruction Glossary
LSLD
Logical Shift Left Double
(Same as ASLD)
LSLD
Operation:
C
Description:
CCR Details:
b7 – – – – – – b0
b7 – – – – – – b0
Accumulator A
Accumulator B
0
Shifts all bits of double accumulator D one place to the left. Bit 0 is
loaded with 0. The C status bit is loaded from the most significant bit of
accumulator A.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: D15
Set if the MSB of D was set before the shift; cleared otherwise
Source Form
LSLD
Address
Mode
INH
Access Detail
Object Code
HCS12
59
O
M68HC12
O
Reference Manual
S12CPUV2
230
MOTOROLA
Instruction Glossary
Glossary
LSR
LSR
Logical Shift Right Memory
Operation:
0
Description:
CCR Details:
b7 – – – – – – b0
C
Shifts all bits of memory location M one place to the right. Bit 7 is loaded
with 0. The C status bit is loaded from the least significant bit of M.
S
X
H
I
N
Z
V
C
–
–
–
–
0
∆
∆
∆
N: 0; cleared
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: M0
Set if the LSB of M was set before the shift; cleared otherwise
Source Form
LSR opr16a
LSR oprx0_xysp
LSR oprx9,xysp
LSR oprx16,xysp
LSR [D,xysp]
LSR [oprx16,xysp]
Access Detail
Address
Mode
Object Code
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
74 hh ll
64 xb
64 xb ff
64 xb ee ff
64 xb
64 xb ee ff
HCS12
M68HC12
rPwO
rPw
rPwO
frPwP
fIfrPw
fIPrPw
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
S12CPUV2
Reference Manual
MOTOROLA
231
Instruction Glossary
LSRA
LSRA
Logical Shift Right A
Operation:
0
Description:
CCR Details:
b7 – – – – – – b0
C
Shifts all bits of accumulator A one place to the right. Bit 7 is loaded
with 0. The C status bit is loaded from the least significant bit of A.
S
X
H
I
N
Z
V
C
–
–
–
–
0
∆
∆
∆
C
N: 0; cleared
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: A0
Set if the LSB of A was set before the shift; cleared otherwise
Source Form
LSRA
Address
Mode
INH
Access Detail
Object Code
HCS12
44
O
M68HC12
O
Reference Manual
S12CPUV2
232
MOTOROLA
Instruction Glossary
Glossary
LSRB
LSRB
Logical Shift Right B
Operation:
0
Description:
CCR Details:
b7 – – – – – – b0
C
Shifts all bits of accumulator B one place to the right. Bit 7 is loaded
with 0. The C status bit is loaded from the least significant bit of B.
S
X
H
I
N
Z
V
C
–
–
–
–
0
∆
∆
∆
N: 0; cleared
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: B0
Set if the LSB of B was set before the shift; cleared otherwise
Source Form
LSRB
Address
Mode
INH
Access Detail
Object Code
HCS12
54
O
M68HC12
O
S12CPUV2
Reference Manual
MOTOROLA
233
Instruction Glossary
LSRD
Logical Shift Right Double
LSRD
Operation:
0
Description:
CCR Details:
b7 – – – – – – b0
b7 – – – – – – b0
Accumulator A
Accumulator B
C
Shifts all bits of double accumulator D one place to the right. D15 (MSB
of A) is loaded with 0. The C status bit is loaded from D0 (LSB of B).
S
X
H
I
N
Z
V
C
–
–
–
–
0
∆
∆
∆
N: 0; cleared
Z: Set if result is $0000; cleared otherwise
V: D0
Set if, after the shift operation, C is set; cleared otherwise
C: D0
Set if the LSB of D was set before the shift; cleared otherwise
Source Form
LSRD
Address
Mode
INH
Access Detail
Object Code
HCS12
49
O
M68HC12
O
Reference Manual
S12CPUV2
234
MOTOROLA
Instruction Glossary
Glossary
MAXA
Operation:
Description:
Place Larger of Two Unsigned 8-Bit Values
in Accumulator A
MAXA
MAX ((A), (M)) ⇒ A
Subtracts an unsigned 8-bit value in memory from an unsigned 8-bit
value in accumulator A to determine which is larger and leaves the larger
of the two values in A. The Z status bit is set when the result of the
subtraction is zero (the values are equal), and the C status bit is set
when the subtraction requires a borrow (the value in memory is larger
than the value in the accumulator). When C = 1, the value in A has been
replaced by the value in memory.
The unsigned value in memory is accessed by means of indexed
addressing modes, which allow a great deal of flexibility in specifying the
address of the operand. Auto increment/decrement variations of indexed
addressing facilitate finding the largest value in a list of values.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: A7 • M7 • R7 + A7 • M7 • R7
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: A7 • M7 + M7 • R7 + R7 • A7
Set if the value of the content of memory is larger than the value of
the accumulator; cleared otherwise
Condition codes reflect internal subtraction (R = A – M)
Source Form
MAXA oprx0_xysp
MAXA oprx9,xysp
MAXA oprx16,xysp
MAXA [D,xysp]
MAXA [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
18 18 xb
18 18 xb ff
18 18 xb ee ff
18 18 xb
18 18 xb ee ff
HCS12
M68HC12
OrPf
OrPO
OfrPP
OfIfrPf
OfIPrPf
OrfP
OrPO
OfrPP
OfIfrfP
OfIPrfP
S12CPUV2
Reference Manual
MOTOROLA
235
Instruction Glossary
MAXM
Operation:
Description:
Place Larger of Two Unsigned 8-Bit Values
in Memory
MAXM
MAX ((A), (M)) ⇒ M
Subtracts an unsigned 8-bit value in memory from an unsigned 8-bit
value in accumulator A to determine which is larger and leaves the larger
of the two values in the memory location. The Z status bit is set when the
result of the subtraction is zero (the values are equal), and the C status
bit is set when the subtraction requires a borrow (the value in memory is
larger than the value in the accumulator). When C = 0, the value in
accumulator A has replaced the value in memory.
The unsigned value in memory is accessed by means of indexed
addressing modes, which allow a great deal of flexibility in specifying the
address of the operand.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: A7 • M7 • R7 + A7 • M7 • R7
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: A7 • M7 + M7 • R7 + R7 • A7
Set if the value of the content of memory is larger than the value of
the accumulator; cleared otherwise
Condition codes reflect internal subtraction (R = A – M)
Source Form
MAXM oprx0_xysp
MAXM oprx9,xysp
MAXM oprx16,xysp
MAXM [D,xysp]
MAXM [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
18 1C xb
18 1C xb ff
18 1C xb ee ff
18 1C xb
18 1C xb ee ff
HCS12
M68HC12
OrPw
OrPwO
OfrPwP
OfIfrPw
OfIPrPw
OrPw
OrPwO
OfrPwP
OfIfrPw
OfIPrPw
Reference Manual
S12CPUV2
236
MOTOROLA
Instruction Glossary
Glossary
MEM
Operation:
Description:
MEM
Determine Grade of Membership
(Fuzzy Logic)
Grade of Membership ⇒ M(Y)
(Y) + $0001 ⇒ Y
(X) + $0004 ⇒ X
Before executing MEM, initialize A, X, and Y. Load A with the current
crisp value of a system input variable. Load Y with the fuzzy input RAM
location where the grade of membership is to be stored. Load X with the
first address of a 4-byte data structure that describes a trapezoidal
membership function. The data structure consists of:
•
Point_1 — The x-axis starting point for the leading side (at MX)
•
Slope_1 — The slope of the leading side (at MX+1)
•
Point_2 — The x-axis position of the rightmost point (at MX+2)
•
Slope_2 — The slope of the trailing side (at MX+3); the right side
slopes up and to the left from point_2
A slope_1 or slope_2 value of $00 is a special case in which the
membership function either starts with a grade of $FF at input = point_1,
or ends with a grade of $FF at input = point_2 (infinite slope).
During execution, the value of A remains unchanged. X is incremented
by four and Y is incremented by one.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
?
–
?
?
?
?
H, N, Z, V, and C may be altered by this instruction.
Source Form
MEM
Address
Mode
Special
Access Detail
Object Code
01
HCS12
M68HC12
RRfOw
RRfOw
S12CPUV2
Reference Manual
MOTOROLA
237
Instruction Glossary
Place Smaller of Two
Unsigned 8-Bit Values
in Accumulator A
MINA
Operation:
Description:
MINA
MIN ((A), (M)) ⇒ A
Subtracts an unsigned 8-bit value in memory from an unsigned 8-bit
value in accumulator A to determine which is larger, and leaves the
smaller of the two values in accumulator A. The Z status bit is set when
the result of the subtraction is zero (the values are equal), and the C
status bit is set when the subtraction requires a borrow (the value in
memory is larger than the value in the accumulator). When C = 0, the
value in accumulator A has been replaced by the value in memory.
The unsigned value in memory is accessed by means of indexed
addressing modes, which allow a great deal of flexibility in specifying the
address of the operand. Auto increment/decrement variations of indexed
addressing facilitate finding the smallest value in a list of values.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: A7 • M7 • R7 + A7 • M7 • R7
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: A7 • M7 + M7 • R7 + R7 • A7
Set if the value of the content of memory is larger than the value of
the accumulator; cleared otherwise
Condition codes reflect internal subtraction (R = A – M)
Source Form
MINA oprx0_xysp
MINA oprx9,xysp
MINA oprx16,xysp
MINA [D,xysp]
MINA [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
18 19 xb
18 19 xb ff
18 19 xb ee ff
18 19 xb
18 19 xb ee ff
HCS12
M68HC12
OrPf
OrPO
OfrPP
OfIfrPf
OfIPrPf
OrfP
OrPO
OfrPP
OfIfrfP
OfIPrfP
Reference Manual
S12CPUV2
238
MOTOROLA
Instruction Glossary
Glossary
Place Smaller of Two
Unsigned 8-Bit Values
in Memory
MINM
Operation:
Description:
MINM
MIN ((A), (M)) ⇒ M
Subtracts an unsigned 8-bit value in memory from an unsigned 8-bit
value in accumulator A to determine which is larger and leaves the
smaller of the two values in the memory location. The Z status bit is set
when the result of the subtraction is zero (the values are equal), and the
C status bit is set when the subtraction requires a borrow (the value in
memory is larger than the value in the accumulator). When C = 1, the
value in accumulator A has replaced the value in memory.
The unsigned value in memory is accessed by means of indexed
addressing modes, which allow a great deal of flexibility in specifying the
address of the operand.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: A7 • M7 • R7 + A7 • M7 • R7
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: A7 • M7 + M7 • R7 + R7 • A7
Set if the value of the content of memory is larger than the value of
the accumulator; cleared otherwise
Condition codes reflect internal subtraction (R = A – M)
Source Form
MINM oprx0_xysp
MINM oprx9,xysp
MINM oprx16,xysp
MINM [D,xysp]
MINM [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
18 1D xb
18 1D xb ff
18 1D xb ee ff
18 1D xb
18 1D xb ee ff
HCS12
M68HC12
OrPw
OrPwO
OfrPwP
OfIfrPw
OfIPrPw
OrPw
OrPwO
OfrPwP
OfIfrPw
OfIPrPw
S12CPUV2
Reference Manual
MOTOROLA
239
Instruction Glossary
MOVB
Operation:
Description:
Move a Byte of Data
from One Memory Location to Another
MOVB
(M1) ⇒ M2
Moves the content of one memory location to another memory location.
The content of the source memory location is not changed.
Move instructions use separate addressing modes to access the source
and destination of a move. The following combinations of addressing
modes are supported: IMM–EXT, IMM–IDX, EXT–EXT, EXT–IDX,
IDX–EXT, and IDX–IDX. IDX operands allow indexed addressing mode
specifications that fit in a single postbyte including 5-bit constant,
accumulator offsets, and auto increment/decrement modes. Nine-bit
and 16-bit constant offsets would require additional extension bytes and
are not allowed. Indexed indirect modes (for example [D,r]) are also not
allowed.
There are special considerations when using PC-relative addressing
with move instructions. These are discussed in 3.10 Instructions
Using Multiple Modes.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Source Form(1)
MOVB #opr8, opr16a
MOVB #opr8i, oprx0_xysp
MOVB opr16a, opr16a
MOVB opr16a, oprx0_xysp
MOVB oprx0_xysp, opr16a
MOVB oprx0_xysp, oprx0_xysp
Access Detail
Address
Mode
Object Code
IMM–EXT
IMM–IDX
EXT–EXT
EXT–IDX
IDX–EXT
IDX–IDX
18 0B ii hh ll
18 08 xb ii
18 0C hh ll hh ll
18 09 xb hh ll
18 0D xb hh ll
18 0A xb xb
HCS12
M68HC12
OPwP
OPwO
OrPwPO
OPrPw
OrPwP
OrPwO
OPwP
OPwO
OrPwPO
OPrPw
OrPwP
OrPwO
1. The first operand in the source code statement specifies the source for the move.
Reference Manual
S12CPUV2
240
MOTOROLA
Instruction Glossary
Glossary
MOVW
Operation:
Description:
Move a Word of Data
from One Memory Location to Another
MOVW
(M : M + 11) ⇒ M : M + 12
Moves the content of one 16-bit location in memory to another 16-bit
location in memory. The content of the source memory location is not
changed.
Move instructions use separate addressing modes to access the source
and destination of a move. The following combinations of addressing
modes are supported: IMM–EXT, IMM–IDX, EXT–EXT, EXT–IDX,
IDX–EXT, and IDX–IDX. IDX operands allow indexed addressing mode
specifications that fit in a single postbyte including 5-bit constant,
accumulator offsets, and auto increment/decrement modes. Nine-bit
and 16-bit constant offsets would require additional extension bytes and
are not allowed. Indexed indirect modes (for example [D,r]) are also not
allowed.
There are special considerations when using PC-relative addressing
with move instructions. These are discussed in 3.10 Instructions
Using Multiple Modes.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Source Form(1)
MOVW #opr16i, opr16a
MOVW #opr16i, oprx0_xysp
MOVW opr16a, opr16a
MOVW opr16a, oprx0_xysp
MOVW oprx0_xysp, opr16a
MOVW oprx0_xysp, oprx0_xysp
Access Detail
Address
Mode
Object Code
IMM–EXT
IMM–IDX
EXT–EXT
EXT–IDX
IDX–EXT
IDX–IDX
18 03 jj kk hh ll
18 00 xb jj kk
18 04 hh ll hh ll
18 01 xb hh ll
18 05 xb hh ll
18 02 xb xb
HCS12
M68HC12
OPWPO
OPPW
ORPWPO
OPRPW
ORPWP
ORPWO
OPWPO
OPPW
ORPWPO
OPRPW
ORPWP
ORPWO
1. The first operand in the source code statement specifies the source for the move.
S12CPUV2
Reference Manual
MOTOROLA
241
Instruction Glossary
MUL
Operation:
Description:
CCR Details:
Multiply
8-Bit by 8-Bit (Unsigned)
MUL
(A) × (B) ⇒ A : B
Multiplies the 8-bit unsigned binary value in accumulator A by the 8-bit
unsigned binary value in accumulator B and places the 16-bit unsigned
result in double accumulator D. The carry flag allows rounding the most
significant byte of the result through the sequence MUL, ADCA #0.
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
∆
C: R7
Set if bit 7 of the result (B bit 7) is set; cleared otherwise
Source Form
MUL
Address
Mode
INH
Access Detail
Object Code
HCS12
12
O
M68HC12
ffO
Reference Manual
S12CPUV2
242
MOTOROLA
Instruction Glossary
Glossary
NEG
Operation:
Description:
CCR Details:
Negate Memory
NEG
0 – (M) = (M) + 1 ⇒ M
Replaces the content of memory location M with its two’s complement
(the value $80 is left unchanged).
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise.
Z: Set if result is $00; cleared otherwise.
V: R7 • R6 • R5 • R4 • R3 • R2 • R1 • R0
Set if there is a two’s complement overflow from the implied
subtraction from zero; cleared otherwise. Two’s complement
overflow occurs if and only if (M) = $80
C: R7 + R6 + R5 + R4 + R3 + R2 + R1 + R0
Set if there is a borrow in the implied subtraction from zero; cleared
otherwise. Set in all cases except when (M) = $00.
Source Form
NEG opr16a
NEG oprx0_xysp
NEG oprx9,xysp
NEG oprx16,xysp
NEG [D,xysp]
NEG [oprx16,xysp]
Access Detail
Address
Mode
Object Code
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
70 hh ll
60 xb
60 xb ff
60 xb ee ff
60 xb
60 xb ee ff
HCS12
M68HC12
rPwO
rPw
rPwO
frPwP
fIfrPw
fIPrPw
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
S12CPUV2
Reference Manual
MOTOROLA
243
Instruction Glossary
NEGA
Operation:
Description:
CCR Details:
NEGA
Negate A
0 – (A) = (A) + 1 ⇒ A
Replaces the content of accumulator A with its two’s complement (the
value $80 is left unchanged).
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: R7 • R6 • R5 • R4 • R3 • R2 • R1 • R0
Set if there is a two’s complement overflow from the implied
subtraction from zero; cleared otherwise
Two’s complement overflow occurs if and only if (A) = $80
C: R7 + R6 + R5 + R4 + R3 + R2 + R1 + R0
Set if there is a borrow in the implied subtraction from zero; cleared
otherwise
Set in all cases except when (A) = $00
Source Form
NEGA
Address
Mode
INH
Access Detail
Object Code
HCS12
40
O
M68HC12
O
Reference Manual
S12CPUV2
244
MOTOROLA
Instruction Glossary
Glossary
NEGB
Operation:
Description:
CCR Details:
NEGB
Negate B
0 – (B) = (B) + 1 ⇒ B
Replaces the content of accumulator B with its two’s complement (the
value $80 is left unchanged).
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: R7 • R6 • R5 • R4 • R3 • R2 • R1 • R0
Set if there is a two’s complement overflow from the implied
subtraction from zero; cleared otherwise
Two’s complement overflow occurs if and only if (B) = $80
C: R7 + R6 + R5 + R4 + R3 + R2 + R1 + R0
Set if there is a borrow in the implied subtraction from zero; cleared
otherwise
Set in all cases except when (B) = $00
Source Form
NEGB
Address
Mode
INH
Access Detail
Object Code
HCS12
50
O
M68HC12
O
S12CPUV2
Reference Manual
MOTOROLA
245
Instruction Glossary
NOP
Operation:
Description:
CCR Details:
Source Form
NOP
NOP
Null Operation
No operation
This single-byte instruction increments the PC and does nothing else.
No other CPU registers are affected. NOP is typically used to produce a
time delay, although some software disciplines discourage CPU
frequency-based time delays. During debug, NOP instructions are
sometimes used to temporarily replace other machine code instructions,
thus disabling the replaced instruction(s).
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
A7
O
M68HC12
O
Reference Manual
S12CPUV2
246
MOTOROLA
Instruction Glossary
Glossary
ORAA
Operation:
Description:
CCR Details:
ORAA
Inclusive OR A
(A) + (M) ⇒ A
Performs bitwise logical inclusive OR between the content of
accumulator A and the content of memory location M and places the
result in A. Each bit of A after the operation is the logical inclusive OR of
the corresponding bits of M and of A before the operation.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: 0; cleared
Source Form
ORAA #opr8i
ORAA opr8a
ORAA opr16a
ORAA oprx0_xysp
ORAA oprx9,xysp
ORAA oprx16,xysp
ORAA [D,xysp]
ORAA [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
8A ii
9A dd
BA hh ll
AA xb
AA xb ff
AA xb ee ff
AA xb
AA xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
S12CPUV2
Reference Manual
MOTOROLA
247
Instruction Glossary
ORAB
Operation:
Description:
CCR Details:
ORAB
Inclusive OR B
(B) + (M) ⇒ B
Performs bitwise logical inclusive OR between the content of
accumulator B and the content of memory location M. The result is
placed in B. Each bit of B after the operation is the logical inclusive OR
of the corresponding bits of M and of B before the operation.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: 0; cleared
Source Form
ORAB #opr8i
ORAB opr8a
ORAB opr16a
ORAB oprx0_xysp
ORAB oprx9,xysp
ORAB oprx16,xysp
ORAB [D,xysp]
ORAB [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
CA ii
DA dd
FA hh ll
EA xb
EA xb ff
EA xb ee ff
EA xb
EA xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
Reference Manual
S12CPUV2
248
MOTOROLA
Instruction Glossary
Glossary
ORCC
Operation:
Description:
CCR Details:
Logical OR CCR with Mask
ORCC
(CCR) + (M) ⇒ CCR
Performs bitwise logical inclusive OR between the content of memory
location M and the content of the CCR and places the result in the CCR.
Each bit of the CCR after the operation is the logical OR of the
corresponding bits of M and of CCR before the operation. To set one or
more bits, set the corresponding bit of the mask equal to 1. Bits
corresponding to 0s in the mask are not changed by the ORCC
operation.
S
X
H
I
N
Z
V
C
⇑
–
⇑
⇑
⇑
⇑
⇑
⇑
Condition code bits are set if the corresponding bit was 1 before the
operation or if the corresponding bit in the instruction-provided mask
is 1. The X interrupt mask cannot be set by any software instruction.
Source Form
ORCC #opr8i
Address
Mode
IMM
Access Detail
Object Code
HCS12
14 ii
P
M68HC12
P
S12CPUV2
Reference Manual
MOTOROLA
249
Instruction Glossary
PSHA
Operation:
Description:
Push A onto Stack
PSHA
(SP) – $0001 ⇒ SP
(A) ⇒ M(SP)
Stacks the content of accumulator A. The stack pointer is decremented
by one. The content of A is then stored at the address the SP points to.
Push instructions are commonly used to save the contents of one or
more CPU registers at the start of a subroutine. Complementary pull
instructions can be used to restore the saved CPU registers just before
returning from the subroutine.
CCR Details:
Source Form
PSHA
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
36
Os
M68HC12
Os
Reference Manual
S12CPUV2
250
MOTOROLA
Instruction Glossary
Glossary
PSHB
Operation:
Description:
Push B onto Stack
PSHB
(SP) – $0001 ⇒ SP
(B) ⇒ M(SP)
Stacks the content of accumulator B. The stack pointer is decremented
by one. The content of B is then stored at the address the SP points to.
Push instructions are commonly used to save the contents of one or
more CPU registers at the start of a subroutine. Complementary pull
instructions can be used to restore the saved CPU registers just before
returning from the subroutine.
CCR Details:
Source Form
PSHB
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
37
Os
M68HC12
Os
S12CPUV2
Reference Manual
MOTOROLA
251
Instruction Glossary
PSHC
Operation:
Description:
Push CCR onto Stack
PSHC
(SP) – $0001 ⇒ SP
(CCR) ⇒ M(SP)
Stacks the content of the condition codes register. The stack pointer is
decremented by one. The content of the CCR is then stored at the
address to which the SP points.
Push instructions are commonly used to save the contents of one or
more CPU registers at the start of a subroutine. Complementary pull
instructions can be used to restore the saved CPU registers just before
returning from the subroutine.
CCR Details:
Source Form
PSHC
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
39
Os
M68HC12
Os
Reference Manual
S12CPUV2
252
MOTOROLA
Instruction Glossary
Glossary
PSHD
Operation:
Description:
Push Double Accumulator onto Stack
PSHD
(SP) – $0002 ⇒ SP
(A : B) ⇒ M(SP) : M(SP+1)
Stacks the content of double accumulator D. The stack pointer is
decremented by two, then the contents of accumulators A and B are
stored at the location to which the SP points.
After PSHD executes, the SP points to the stacked value of accumulator
A. This stacking order is the opposite of the order in which A and B are
stacked when an interrupt is recognized. The interrupt stacking order is
backward-compatible with the M6800, which had no 16-bit accumulator.
Push instructions are commonly used to save the contents of one or
more CPU registers at the start of a subroutine. Complementary pull
instructions can be used to restore the saved CPU registers just before
returning from the subroutine.
CCR Details:
Source Form
PSHD
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
3B
OS
M68HC12
OS
S12CPUV2
Reference Manual
MOTOROLA
253
Instruction Glossary
PSHX
Operation:
Description:
Push Index Register X onto Stack
PSHX
(SP) – $0002 ⇒ SP
(XH : XL) ⇒ M(SP) : M(SP+1)
Stacks the content of index register X. The stack pointer is decremented
by two. The content of X is then stored at the address to which the SP
points. After PSHX executes, the SP points to the stacked value of the
high-order half of X.
Push instructions are commonly used to save the contents of one or
more CPU registers at the start of a subroutine. Complementary pull
instructions can be used to restore the saved CPU registers just before
returning from the subroutine.
CCR Details:
Source Form
PSHX
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
34
OS
M68HC12
OS
Reference Manual
S12CPUV2
254
MOTOROLA
Instruction Glossary
Glossary
PSHY
Operation:
Description:
Push Index Register Y onto Stack
PSHY
(SP) – $0002 ⇒ SP
(YH : YL) ⇒ M(SP) : M(SP+1)
Stacks the content of index register Y. The stack pointer is decremented
by two. The content of Y is then stored at the address to which the SP
points. After PSHY executes, the SP points to the stacked value of the
high-order half of Y.
Push instructions are commonly used to save the contents of one or
more CPU registers at the start of a subroutine. Complementary pull
instructions can be used to restore the saved CPU registers just before
returning from the subroutine.
CCR Details:
Source Form
PSHY
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
35
OS
M68HC12
OS
S12CPUV2
Reference Manual
MOTOROLA
255
Instruction Glossary
PULA
Operation:
Description:
Pull A from Stack
PULA
(M(SP)) ⇒ A
(SP) + $0001 ⇒ SP
Accumulator A is loaded from the address indicated by the stack pointer.
The SP is then incremented by one.
Pull instructions are commonly used at the end of a subroutine, to
restore the contents of CPU registers that were pushed onto the stack
before subroutine execution.
CCR Details:
Source Form
PULA
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
32
ufO
M68HC12
ufO
Reference Manual
S12CPUV2
256
MOTOROLA
Instruction Glossary
Glossary
PULB
Operation:
Description:
Pull B from Stack
PULB
(M(SP)) ⇒ B
(SP) + $0001 ⇒ SP
Accumulator B is loaded from the address indicated by the stack pointer.
The SP is then incremented by one.
Pull instructions are commonly used at the end of a subroutine, to
restore the contents of CPU registers that were pushed onto the stack
before subroutine execution.
CCR Details:
Source Form
PULB
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
33
ufO
M68HC12
ufO
S12CPUV2
Reference Manual
MOTOROLA
257
Instruction Glossary
PULC
Operation:
Description:
Pull Condition Code Register from Stack
PULC
(M(SP)) ⇒ CCR
(SP) + $0001 ⇒ SP
The condition code register is loaded from the address indicated by the
stack pointer. The SP is then incremented by one.
Pull instructions are commonly used at the end of a subroutine to restore
the contents of CPU registers that were pushed onto the stack before
subroutine execution.
CCR Details:
S
X
H
I
N
Z
V
C
∆
⇓
∆
∆
∆
∆
∆
∆
Condition codes take on the value pulled from the stack, except that the
X mask bit cannot change from 0 to 1. Software can leave the X bit set,
leave it cleared, or change it from 1 to 0, but it can be set only by a reset
or by recognition of an XIRQ interrupt.
Source Form
PULC
Address
Mode
INH
Access Detail
Object Code
HCS12
38
ufO
M68HC12
ufO
Reference Manual
S12CPUV2
258
MOTOROLA
Instruction Glossary
Glossary
PULD
Operation:
Description:
Pull Double Accumulator from Stack
PULD
(M(SP) : M(SP+1)) ⇒ A : B
(SP) + $0002 ⇒ SP
Double accumulator D is loaded from the address indicated by the stack
pointer. The SP is then incremented by two.
The order in which A and B are pulled from the stack is the opposite of
the order in which A and B are pulled when an RTI instruction is
executed. The interrupt stacking order for A and B is
backward-compatible with the M6800, which had no 16-bit accumulator.
Pull instructions are commonly used at the end of a subroutine to restore
the contents of CPU registers that were pushed onto the stack before
subroutine execution.
CCR Details:
Source Form
PULD
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
3A
UfO
M68HC12
UfO
S12CPUV2
Reference Manual
MOTOROLA
259
Instruction Glossary
PULX
Operation:
Description:
Pull Index Register X from Stack
PULX
(M(SP) : M(SP+1)) ⇒ XH : XL
(SP) + $0002 ⇒ SP
Index register X is loaded from the address indicated by the stack
pointer. The SP is then incremented by two.
Pull instructions are commonly used at the end of a subroutine to restore
the contents of CPU registers that were pushed onto the stack before
subroutine execution.
CCR Details:
Source Form
PULX
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
30
UfO
M68HC12
UfO
Reference Manual
S12CPUV2
260
MOTOROLA
Instruction Glossary
Glossary
PULY
Operation:
Description:
Pull Index Register Y from Stack
PULY
(M(SP) : M(SP+1)) ⇒ YH : YL
(SP) + $0002 ⇒ SP
Index register Y is loaded from the address indicated by the stack
pointer. The SP is then incremented by two.
Pull instructions are commonly used at the end of a subroutine to restore
the contents of CPU registers that were pushed onto the stack before
subroutine execution.
CCR Details:
Source Form
PULY
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
31
UfO
M68HC12
UfO
S12CPUV2
Reference Manual
MOTOROLA
261
Instruction Glossary
REV
Operation:
Description:
Fuzzy Logic Rule Evaluation
REV
MIN-MAX Rule Evaluation
Performs an unweighted evaluation of a list of rules, using fuzzy input
values to produce fuzzy outputs. REV can be interrupted, so it does not
adversely affect interrupt latency.
The REV instruction uses an 8-bit offset from a base address stored in
index register Y to determine the address of each fuzzy input and fuzzy
output. For REV to execute correctly, each rule in the knowledge base
must consist of a table of 8-bit antecedent offsets followed by a table of
8-bit consequent offsets. The value $FE marks boundaries between
antecedents and consequents and between successive rules. The value
$FF marks the end of the rule list. REV can evaluate any number of rules
with any number of inputs and outputs.
Beginning with the address pointed to by the first rule antecedent, REV
evaluates each successive fuzzy input value until it encounters an $FE
separator. Operation is similar to that of a MINA instruction. The smallest
input value is the truth value of the rule. Then, beginning with the
address pointed to by the first rule consequent, the truth value is
compared to each successive fuzzy output value until another $FE
separator is encountered; if the truth value is greater than the current
output value, it is written to the output. Operation is similar to that of a
MAXM instruction. Rules are processed until an $FF terminator is
encountered.
Before executing REV, perform these set up operations.
•
X must point to the first 8-bit element in the rule list.
•
Y must point to the base address for fuzzy inputs and fuzzy
outputs.
•
A must contain the value $FF, and the CCR V bit must = 0.
(LDAA #$FF places the correct value in A and clears V.)
•
Clear fuzzy outputs to 0s.
Index register X points to the element in the rule list that is being
evaluated. X is automatically updated so that execution can resume
correctly if the instruction is interrupted. When execution is complete, X
points to the next address after the $FF separator at the end of the rule
list.
Reference Manual
S12CPUV2
262
MOTOROLA
Instruction Glossary
Glossary
REV
REV
Fuzzy Logic Rule Evaluation
(Continued)
Index register Y points to the base address for the fuzzy inputs and fuzzy
outputs. The value in Y does not change during execution.
Accumulator A holds intermediate results. During antecedent
processing, a MIN function compares each fuzzy input to the value
stored in A, and writes the smaller of the two to A. When all antecedents
have been evaluated, A contains the smallest input value. This is the
truth value used during consequent processing. Accumulator A must be
initialized to $FF for the MIN function to evaluate the inputs of the first
rule correctly. For subsequent rules, the value $FF is written to A when
an $FE marker is encountered. At the end of execution, accumulator A
holds the truth value for the last rule.
The V status bit signals whether antecedents (0) or consequents (1) are
being processed. V must be initialized to 0 for processing to begin with
the antecedents of the first rule. Once execution begins, the value of V
is automatically changed as $FE separators are encountered. At the end
of execution, V should equal 1, because the last element before the $FF
end marker should be a rule consequent. If V is equal to 0 at the end of
execution, the rule list is incorrect.
Fuzzy outputs must be cleared to $00 before processing begins in order
for the MAX algorithm used during consequent processing to work
correctly. Residual output values would cause incorrect comparison.
Refer to Section 9. Fuzzy Logic Support for details.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
?
–
?
?
∆
?
V: 1; Normally set, unless rule structure is erroneous
H, N, Z, and C may be altered by this instruction
Source Form
REV
(replace comma if interrupted)
Access Detail(1)
Address
Mode
Object Code
Special
18 3A
HCS12
Orf(t,tx)O
ff + Orf(t,
M68HC12
Orf(t,tx)O
ff + Orf(t,
1. The 3-cycle loop in parentheses is executed once for each element in the rule list. When an interrupt occurs, there is a
2-cycle exit sequence, a 4-cycle re-entry sequence, then execution resumes with a prefetch of the last antecedent or
consequent being processed at the time of the interrupt.
S12CPUV2
Reference Manual
MOTOROLA
263
Instruction Glossary
REVW
Operation:
Description:
Fuzzy Logic Rule Evaluation (Weighted)
REVW
MIN-MAX Rule Evaluation with Optional Rule Weighting
REVW performs either weighted or unweighted evaluation of a list of
rules, using fuzzy inputs to produce fuzzy outputs. REVW can be
interrupted, so it does not adversely affect interrupt latency.
For REVW to execute correctly, each rule in the knowledge base must
consist of a table of 16-bit antecedent pointers followed by a table of
16-bit consequent pointers. The value $FFFE marks boundaries
between antecedents and consequents, and between successive rules.
The value $FFFF marks the end of the rule list. REVW can evaluate any
number of rules with any number of inputs and outputs.
Setting the C status bit enables weighted evaluation. To use weighted
evaluation, a table of 8-bit weighting factors, one per rule, must be stored
in memory. Index register Y points to the weighting factors.
Beginning with the address pointed to by the first rule antecedent,
REVW evaluates each successive fuzzy input value until it encounters
an $FFFE separator. Operation is similar to that of a MINA instruction.
The smallest input value is the truth value of the rule. Next, if weighted
evaluation is enabled, a computation is performed, and the truth value is
modified. Then, beginning with the address pointed to by the first rule
consequent, the truth value is compared to each successive fuzzy output
value until another $FFFE separator is encountered; if the truth value is
greater than the current output value, it is written to the output. Operation
is similar to that of a MAXM instruction. Rules are processed until an
$FFFF terminator is encountered.
Perform these set up operations before execution:
•
X must point to the first 16-bit element in the rule list.
•
A must contain the value $FF, and the CCR V bit must = 0
(LDAA #$FF places the correct value in A and clears V).
•
Clear fuzzy outputs to 0s.
•
Set or clear the CCR C bit. When weighted evaluation is enabled,
Y must point to the first item in a table of 8-bit weighting factors.
Reference Manual
S12CPUV2
264
MOTOROLA
Instruction Glossary
Glossary
REVW
Fuzzy Logic Rule Evaluation (Weighted)
(Continued)
REVW
Index register X points to the element in the rule list that is being
evaluated. X is automatically updated so that execution can resume
correctly if the instruction is interrupted. When execution is complete, X
points to the address after the $FFFF separator at the end of the rule list.
Index register Y points to the weighting factor being used. Y is
automatically updated so that execution can resume correctly if the
instruction is interrupted. When execution is complete, Y points to the
last weighting factor used. When weighting is not used (C = 0), Y is not
changed.
Accumulator A holds intermediate results. During antecedent
processing, a MIN function compares each fuzzy input to the value
stored in A and writes the smaller of the two to A. When all antecedents
have been evaluated, A contains the smallest input value. For
unweighted evaluation, this is the truth value used during consequent
processing. For weighted evaluation, the value in A is multiplied by the
quantity (Rule Weight + 1) and the upper eight bits of the result replace
the content of A. Accumulator A must be initialized to $FF for the MIN
function to evaluate the inputs of the first rule correctly. For subsequent
rules, the value $FF is automatically written to A when an $FFFE marker
is encountered. At the end of execution, accumulator A holds the truth
value for the last rule.
The V status bit signals whether antecedents (0) or consequents (1) are
being processed. V must be initialized to 0 for processing to begin with
the antecedents of the first rule. Once execution begins, the value of V
is automatically changed as $FFFE separators are encountered. At the
end of execution, V should equal 1, because the last element before the
$FF end marker should be a rule consequent. If V is equal to 0 at the end
of execution, the rule list is incorrect.
Fuzzy outputs must be cleared to $00 before processing begins in order
for the MAX algorithm used during consequent processing to work
correctly. Residual output values would cause incorrect comparison.
Refer to Section 9. Fuzzy Logic Support for details.
S12CPUV2
Reference Manual
MOTOROLA
265
Instruction Glossary
REVW
CCR Details:
REVW
Fuzzy Logic Rule Evaluation (Weighted)
(Concluded)
S
X
H
I
N
Z
V
C
–
–
?
–
?
?
∆
!
V: 1; Normally set, unless rule structure is erroneous
C: Selects weighted (1) or unweighted (0) rule evaluation
H, N, Z, and C may be altered by this instruction
Source Form
REVW
(add 2 at end of ins if wts)
(replace comma if interrupted)
Access Detail(1)
Address
Mode
Object Code
Special
18 3B
HCS12
ORf(t,Tx)O
(r,RfRf)
ffff + ORf(t,
M68HC12
ORf(tTx)O
(r,RfRf)
ffff + ORf(t,
1. The 3-cycle loop in parentheses expands to five cycles for separators when weighting is enabled. The loop is executed
once for each element in the rule list. When an interrupt occurs, there is a 2-cycle exit sequence, a 4-cycle re-entry
sequence, then execution resumes with a prefetch of the last antecedent or consequent being processed at the time of
the interrupt.
Reference Manual
S12CPUV2
266
MOTOROLA
Instruction Glossary
Glossary
ROL
ROL
Rotate Left Memory
Operation:
C
Description:
CCR Details:
C
b7 – – – – – – b0
Shifts all bits of memory location M one place to the left. Bit 0 is loaded
from the C status bit. The C bit is loaded from the most significant bit of
M. Rotate operations include the carry bit to allow extension of shift and
rotate operations to multiple bytes. For example, to shift a 24-bit value
one bit to the left, the sequence ASL LOW, ROL MID, ROL HIGH could
be used where LOW, MID and HIGH refer to the low-order, middle and
high-order bytes of the 24-bit value, respectively.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: M7
Set if the MSB of M was set before the shift; cleared otherwise
Source Form
ROL opr16a
ROL oprx0_xysp
ROL oprx9,xysp
ROL oprx16,xysp
ROL [D,xysp]
ROL [oprx16,xysp]
Access Detail
Address
Mode
Object Code
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
75 hh ll
65 xb
65 xb ff
65 xb ee ff
65 xb
65 xb ee ff
HCS12
M68HC12
rPwO
rPw
rPwO
frPwP
fIfrPw
fIPrPw
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
S12CPUV2
Reference Manual
MOTOROLA
267
Instruction Glossary
ROLA
ROLA
Rotate Left A
Operation:
C
Description:
CCR Details:
b7 – – – – – – b0
C
Shifts all bits of accumulator A one place to the left. Bit 0 is loaded from
the C status bit. The C bit is loaded from the most significant bit of A.
Rotate operations include the carry bit to allow extension of shift and
rotate operations to multiple bytes. For example, to shift a 24-bit value
one bit to the left, the sequence ASL LOW, ROL MID, and ROL HIGH
could be used where LOW, MID, and HIGH refer to the low-order,
middle, and high-order bytes of the 24-bit value, respectively.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: A7
Set if the MSB of A was set before the shift; cleared otherwise
Source Form
ROLA
Address
Mode
INH
Access Detail
Object Code
HCS12
45
O
M68HC12
O
Reference Manual
S12CPUV2
268
MOTOROLA
Instruction Glossary
Glossary
ROLB
ROLB
Rotate Left B
Operation:
C
Description:
CCR Details:
C
b7 – – – – – – b0
Shifts all bits of accumulator B one place to the left. Bit 0 is loaded from
the C status bit. The C bit is loaded from the most significant bit of B.
Rotate operations include the carry bit to allow extension of shift and
rotate operations to multiple bytes. For example, to shift a 24-bit value
one bit to the left, the sequence ASL LOW, ROL MID, and ROL HIGH
could be used where LOW, MID, and HIGH refer to the low-order, middle
and high-order bytes of the 24-bit value, respectively.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: B7
Set if the MSB of B was set before the shift; cleared otherwise
Source Form
ROLB
Address
Mode
INH
Access Detail
Object Code
HCS12
55
O
M68HC12
O
S12CPUV2
Reference Manual
MOTOROLA
269
Instruction Glossary
ROR
ROR
Rotate Right Memory
Operation:
C
Description:
CCR Details:
b7 – – – – – – b0
C
Shifts all bits of memory location M one place to the right. Bit 7 is loaded
from the C status bit. The C bit is loaded from the least significant bit of
M. Rotate operations include the carry bit to allow extension of shift and
rotate operations to multiple bytes. For example, to shift a 24-bit value
one bit to the right, the sequence LSR HIGH, ROR MID, and ROR LOW
could be used where LOW, MID, and HIGH refer to the low-order,
middle, and high-order bytes of the 24-bit value, respectively.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: M0
Set if the LSB of M was set before the shift; cleared otherwise
Source Form
ROR opr16a
ROR oprx0_xysp
ROR oprx9,xysp
ROR oprx16,xysp
ROR [D,xysp]
ROR [oprx16,xysp]
Access Detail
Address
Mode
Object Code
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
76 hh ll
66 xb
66 xb ff
66 xb ee ff
66 xb
66 xb ee ff
HCS12
M68HC12
rPwO
rPw
rPwO
frPwP
fIfrPw
fIPrPw
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
Reference Manual
S12CPUV2
270
MOTOROLA
Instruction Glossary
Glossary
RORA
RORA
Rotate Right A
Operation:
C
Description:
CCR Details:
C
b7 – – – – – – b0
Shifts all bits of accumulator A one place to the right. Bit 7 is loaded from
the C status bit. The C bit is loaded from the least significant bit of A.
Rotate operations include the carry bit to allow extension of shift and
rotate operations to multiple bytes. For example, to shift a 24-bit value
one bit to the right, the sequence LSR HIGH, ROR MID, and ROR LOW
could be used where LOW, MID, and HIGH refer to the low-order,
middle, and high-order bytes of the 24-bit value, respectively.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: A0
Set if the LSB of A was set before the shift; cleared otherwise
Source Form
RORA
Address
Mode
INH
Access Detail
Object Code
HCS12
46
O
M68HC12
O
S12CPUV2
Reference Manual
MOTOROLA
271
Instruction Glossary
RORB
RORB
Rotate Right B
Operation:
C
Description:
CCR Details:
b7 – – – – – – b0
C
Shifts all bits of accumulator B one place to the right. Bit 7 is loaded from
the C status bit. The C bit is loaded from the least significant bit of B.
Rotate operations include the carry bit to allow extension of shift and
rotate operations to multiple bytes. For example, to shift a 24-bit value
one bit to the right, the sequence LSR HIGH, ROR MID, and ROR LOW
could be used where LOW, MID, and HIGH refer to the low-order, middle
and high-order bytes of the 24-bit value, respectively.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: N ⊕ C = [N • C] + [N • C] (for N and C after the shift)
Set if (N is set and C is cleared) or (N is cleared and C is set);
cleared otherwise (for values of N and C after the shift)
C: B0
Set if the LSB of B was set before the shift; cleared otherwise
Source Form
RORB
Address
Mode
INH
Access Detail
Object Code
HCS12
56
O
M68HC12
O
Reference Manual
S12CPUV2
272
MOTOROLA
Instruction Glossary
Glossary
RTC
Operation:
Description:
CCR Details:
Source Form
RTC
RTC
Return from Call
(M(SP)) ⇒ PPAGE
(SP) + $0001 ⇒ SP
(M(SP) : M(SP+1)) ⇒ PCH : PCL
(SP) + $0002 ⇒ SP
Terminates subroutines in expanded memory invoked by the CALL
instruction. Returns execution flow from the subroutine to the calling
program. The program overlay page (PPAGE) register and the return
address are restored from the stack; program execution continues at the
restored address. For code compatibility purposes, CALL and RTC also
execute correctly in devices that do not have expanded memory
capability.
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
0A
HCS12
M68HC12
uUnfPPP
uUnPPP
S12CPUV2
Reference Manual
MOTOROLA
273
Instruction Glossary
RTI
Operation:
Description:
RTI
Return from Interrupt
(M(SP)) ⇒ CCR; (SP) + $0001 ⇒ SP
(M(SP) : M(SP+1)) ⇒ B : A; (SP) + $0002 ⇒ SP
(M(SP) : M(SP+1)) ⇒ XH : XL; (SP) + $0004 ⇒ SP
(M(SP) : M(SP+1)) ⇒ PCH : PCL; (SP) – $0002 ⇒ SP
(M(SP) : M(SP+1)) ⇒ YH : YL; (SP) + $0004 ⇒ SP
Restores system context after interrupt service processing is completed.
The condition codes, accumulators B and A, index register X, the PC,
and index register Y are restored to a state pulled from the stack. The X
mask bit may be cleared as a result of an RTI instruction, but cannot be
set if it was cleared prior to execution of the RTI instruction.
If another interrupt is pending when RTI has finished restoring registers
from the stack, the SP is adjusted to preserve stack content, and the new
vector is fetched. This operation is functionally identical to the same
operation in the M68HC11, where registers actually are re-stacked, but
is faster.
CCR Details:
S
X
H
I
N
Z
V
C
∆
⇓
∆
∆
∆
∆
∆
∆
Condition codes take on the value pulled from the stack, except that the
X mask bit cannot change from 0 to 1. Software can leave the X bit set,
leave it cleared, or change it from 1 to 0, but it can be set only by a reset
or by recognition of an XIRQ interrupt.
Source Form
RTI
(with interrupt pending)
Address
Mode
INH
Access Detail
Object Code
HCS12
0B
uUUUUPPP
uUUUUfVfPPP
M68HC12
uUUUUPPP
uUUUUVfPPP
Reference Manual
S12CPUV2
274
MOTOROLA
Instruction Glossary
Glossary
RTS
Operation:
Description:
CCR Details:
Source Form
RTS
RTS
Return from Subroutine
(M(SP) : M(SP+1)) ⇒ PCH : PCL; (SP) + $0002 ⇒ SP
Restores context at the end of a subroutine. Loads the program counter
with a 16-bit value pulled from the stack and increments the stack pointer
by two. Program execution continues at the address restored from the
stack.
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
3D
HCS12
M68HC12
UfPPP
UfPPP
S12CPUV2
Reference Manual
MOTOROLA
275
Instruction Glossary
SBA
Operation:
Description:
CCR Details:
Subtract Accumulators
SBA
(A) – (B) ⇒ A
Subtracts the content of accumulator B from the content of accumulator
A and places the result in A. The content of B is not affected. For
subtraction instructions, the C status bit represents a borrow.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: A7 • B7 • R7 + A7 • B7 • R7
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: A7 • B7 + B7 • R7 + R7 • A7
Set if the absolute value of B is larger than the absolute value of A;
cleared otherwise
Source Form
SBA
Address
Mode
INH
Access Detail
Object Code
HCS12
18 16
OO
M68HC12
OO
Reference Manual
S12CPUV2
276
MOTOROLA
Instruction Glossary
Glossary
SBCA
Operation:
Description:
CCR Details:
Subtract with Carry from A
SBCA
(A) – (M) – C ⇒ A
Subtracts the content of memory location M and the value of the C status
bit from the content of accumulator A. The result is placed in A. For
subtraction instructions, the C status bit represents a borrow.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: A7 • M7 • R7 + A7 • M7 • R7
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: A7 • M7 + M7 • R7 + R7 • A7
Set if the absolute value of the content of memory plus previous
carry is larger than the absolute value of the accumulator; cleared
otherwise
Source Form
SBCA #opr8i
SBCA opr8a
SBCA opr16a
SBCA oprx0_xysp
SBCA oprx9,xysp
SBCA oprx16,xysp
SBCA [D,xysp]
SBCA [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
82 ii
92 dd
B2 hh ll
A2 xb
A2 xb ff
A2 xb ee ff
A2 xb
A2 xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
S12CPUV2
Reference Manual
MOTOROLA
277
Instruction Glossary
SBCB
Operation:
Description:
CCR Details:
Subtract with Carry from B
SBCB
(B) – (M) – C ⇒ B
Subtracts the content of memory location M and the value of the C status
bit from the content of accumulator B. The result is placed in B. For
subtraction instructions, the C status bit represents a borrow.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: B7 • M7 • R7 + B7 • M7 • R7
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: B7 • M7 + M7 • R7 + R7 • B7
Set if the absolute value of the content of memory plus previous
carry is larger than the absolute value of the accumulator; cleared
otherwise
Source Form
SBCB #opr8i
SBCB opr8a
SBCB opr16a
SBCB oprx0_xysp
SBCB oprx9,xysp
SBCB oprx16,xysp
SBCB [D,xysp]
SBCB [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
C2 ii
D2 dd
F2 hh ll
E2 xb
E2 xb ff
E2 xb ee ff
E2 xb
E2 xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
Reference Manual
S12CPUV2
278
MOTOROLA
Instruction Glossary
Glossary
SEC
Operation:
Description:
SEC
Set Carry
1 ⇒ C bit
Sets the C status bit. This instruction is assembled as ORCC #$01. The
ORCC instruction can be used to set any combination of bits in the CCR
in one operation.
SEC can be used to set up the C bit prior to a shift or rotate instruction
involving the C bit.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
1
C: 1; set
Source Form
SEC
translates to... ORCC #$01
Address
Mode
IMM
Access Detail
Object Code
HCS12
14 01
P
M68HC12
P
S12CPUV2
Reference Manual
MOTOROLA
279
Instruction Glossary
SEI
Operation:
Description:
SEI
Set Interrupt Mask
1 ⇒ I bit
Sets the I mask bit. This instruction is assembled as ORCC #$10. The
ORCC instruction can be used to set any combination of bits in the CCR
in one operation. When the I bit is set, all maskable interrupts are
inhibited, and the CPU will recognize only non-maskable interrupt
sources or an SWI.
CCR Details:
Source Form
SEI
translates to... ORCC #$10
S
X
H
I
N
Z
V
C
–
–
–
1
–
–
–
–
I:
1; set
Address
Mode
IMM
Access Detail
Object Code
HCS12
14 10
P
M68HC12
P
Reference Manual
S12CPUV2
280
MOTOROLA
Instruction Glossary
Glossary
SEV
Operation:
Description:
Set Two’s Complement Overflow Bit
SEV
1 ⇒ V bit
Sets the V status bit. This instruction is assembled as ORCC #$02. The
ORCC instruction can be used to set any combination of bits in the CCR
in one operation.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
1
–
V: 1; set
Source Form
SEV
translates to... ORCC #$02
Address
Mode
IMM
Access Detail
Object Code
HCS12
14 02
P
M68HC12
P
S12CPUV2
Reference Manual
MOTOROLA
281
Instruction Glossary
SEX
Operation:
Description:
CCR Details:
Source Form
SEX
Sign Extend into 16-Bit Register
If r1 bit 7 = 0, then $00 : (r1) ⇒ r2
If r1 bit 7 = 1, then $FF : (r1) ⇒ r2
This instruction is an alternate mnemonic for the TFR r1,r2 instruction,
where r1 is an 8-bit register and r2 is a 16-bit register. The result in r2 is
the 16-bit sign extended representation of the original two’s complement
number in r1. The content of r1 is unchanged in all cases except that of
SEX A,D (D is A : B).
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
SEX abc,dxys
INH
Access Detail
Object Code(1)
HCS12
B7 eb
M68HC12
P
P
1. Legal coding for eb is summarized in the following table. Columns represent the high-order source digit. Rows represent
the low-order destination digit (MSB is a don’t care). Values are in hexadecimal.
0
1
2
3
sex:A ⇒ TMP2
sex:B ⇒ TMP2
sex:CCR ⇒ TMP2
4
sex:A ⇒ D
SEX A,D
sex:B ⇒ D
SEX B,D
sex:CCR ⇒ D
SEX CCR,D
5
sex:A ⇒ X
SEX A,X
sex:B ⇒ X
SEX B,X
sex:CCR ⇒ X
SEX CCR,X
6
sex:A ⇒ Y
SEX A,Y
sex:B ⇒ Y
SEX B,Y
sex:CCR ⇒ Y
SEX CCR,Y
7
sex:A ⇒ SP
SEX A,SP
sex:B ⇒ SP
SEX B,SP
sex:CCR ⇒ SP
SEX CCR,SP
Reference Manual
S12CPUV2
282
MOTOROLA
Instruction Glossary
Glossary
STAA
Operation:
Description:
CCR Details:
STAA
Store Accumulator A
(A) ⇒ M
Stores the content of accumulator A in memory location M. The content
of A is unchanged.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: 0; cleared
Source Form
STAA opr8a
STAA opr16a
STAA oprx0_xysp
STAA oprx9,xysp
STAA oprx16,xysp
STAA [D,xysp]
STAA [oprx16,xysp]
Access Detail
Address
Mode
Object Code
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
5A dd
7A hh ll
6A xb
6A xb ff
6A xb ee ff
6A xb
6A xb ee ff
HCS12
Pw
PwO
Pw
PwO
PwP
PIfw
PIPw
M68HC12
Pw
wOP
Pw
PwO
PwP
PIfPw
PIPPw
S12CPUV2
Reference Manual
MOTOROLA
283
Instruction Glossary
STAB
Operation:
Description:
CCR Details:
STAB
Store Accumulator B
(B) ⇒ M
Stores the content of accumulator B in memory location M. The content
of B is unchanged.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: 0; cleared
Source Form
STAB opr8a
STAB opr16a
STAB oprx0_xysp
STAB oprx9,xysp
STAB oprx16,xysp
STAB [D,xysp]
STAB [oprx16,xysp]
Access Detail
Address
Mode
Object Code
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
5B dd
7B hh ll
6B xb
6B xb ff
6B xb ee ff
6B xb
6B xb ee ff
HCS12
Pw
PwO
Pw
PwO
PwP
PIfw
PIPw
M68HC12
Pw
wOP
Pw
PwO
PwP
PIfPw
PIPPw
Reference Manual
S12CPUV2
284
MOTOROLA
Instruction Glossary
Glossary
STD
Operation:
Description:
CCR Details:
STD
Store Double Accumulator
(A : B) ⇒ M : M + 1
Stores the content of double accumulator D in memory location
M : M + 1. The content of D is unchanged.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: 0; cleared
Source Form
STD opr8a
STD opr16a
STD oprx0_xysp
STD oprx9,xysp
STD oprx16,xysp
STD [D,xysp]
STD [oprx16,xysp]
Access Detail
Address
Mode
Object Code
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
5C dd
7C hh ll
6C xb
6C xb ff
6C xb ee ff
6C xb
6C xb ee ff
HCS12
PW
PWO
PW
PWO
PWP
PIfW
PIPW
M68HC12
PW
WOP
PW
PWO
PWP
PIfPW
PIPPW
S12CPUV2
Reference Manual
MOTOROLA
285
Instruction Glossary
STOP
Operation:
Description:
Stop Processing
STOP
(SP) – $0002 ⇒ SP; RTNH : RTNL ⇒ (M(SP) : M(SP+1))
(SP) – $0002 ⇒ SP; YH : YL ⇒ (M(SP) : M(SP+1))
(SP) – $0002 ⇒ SP; XH : XL ⇒ (M(SP) : M(SP+1))
(SP) – $0002 ⇒ SP; B : A⇒ (M(SP) : M(SP+1))
(SP) – $0001 ⇒ SP; CCR ⇒ (M(SP))
Stop All Clocks
When the S control bit is set, STOP is disabled and operates like a
2-cycle NOP instruction. When the S bit is cleared, STOP stacks CPU
context, stops all system clocks, and puts the device in standby mode.
Standby operation minimizes system power consumption. The contents
of registers and the states of I/O pins remain unchanged.
Asserting the RESET, XIRQ, or IRQ signals ends standby mode.
Stacking on entry to STOP allows the CPU to recover quickly when an
interrupt is used, provided a stable clock is applied to the device. If the
system uses a clock reference crystal that also stops during low-power
mode, crystal startup delay lengthens recovery time.
If XIRQ is asserted while the X mask bit = 0 (XIRQ interrupts enabled),
execution resumes with a vector fetch for the XIRQ interrupt. If the X
mask bit = 1 (XIRQ interrupts disabled), a 2-cycle recovery sequence
including an O cycle is used to adjust the instruction queue, and
execution continues with the next instruction after STOP.
CCR Details:
Source Form
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
Access Detail
Object Code
HCS12
M68HC12
OOSSSSsf
OOSSSfSs
(exiting STOP)
fVfPPP
fVfPPP
(continue)
ff
fO
(if STOP disabled)
OO
OO
STOP (entering STOP)
INH
18 3E
Reference Manual
S12CPUV2
286
MOTOROLA
Instruction Glossary
Glossary
STS
Operation:
Description:
CCR Details:
STS
Store Stack Pointer
(SPH : SPL) ⇒ M : M + 1
Stores the content of the stack pointer in memory. The most significant
byte of the SP is stored at the specified address, and the least significant
byte of the SP is stored at the next higher byte address (the specified
address plus one).
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: 0; cleared
Source Form
STS opr8a
STS opr16a
STS oprx0_xysp
STS oprx9,xysp
STS oprx16,xysp
STS [D,xysp]
STS [oprx16,xysp]
Access Detail
Address
Mode
Object Code
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
5F dd
7F hh ll
6F xb
6F xb ff
6F xb ee ff
6F xb
6F xb ee ff
HCS12
PW
PWO
PW
PWO
PWP
PIfW
PIPW
M68HC12
PW
WOP
PW
PWO
PWP
PIfPW
PIPPW
S12CPUV2
Reference Manual
MOTOROLA
287
Instruction Glossary
STX
Operation:
Description:
CCR Details:
STX
Store Index Register X
(XH : XL) ⇒ M : M + 1
Stores the content of index register X in memory. The most significant
byte of X is stored at the specified address, and the least significant byte
of X is stored at the next higher byte address (the specified address plus
one).
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: 0; cleared
Source Form
STX opr8a
STX opr16a
STX oprx0_xysp
STX oprx9,xysp
STX oprx16,xysp
STX [D,xysp]
STX [oprx16,xysp]
Access Detail
Address
Mode
Object Code
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
5E dd
7E hh ll
6E xb
6E xb ff
6E xb ee ff
6E xb
6E xb ee ff
HCS12
PW
PWO
PW
PWO
PWP
PIfW
PIPW
M68HC12
PW
WOP
PW
PWO
PWP
PIfPW
PIPPW
Reference Manual
S12CPUV2
288
MOTOROLA
Instruction Glossary
Glossary
STY
Operation:
Description:
CCR Details:
STY
Store Index Register Y
(YH : YL) ⇒ M : M + 1
Stores the content of index register Y in memory. The most significant
byte of Y is stored at the specified address, and the least significant byte
of Y is stored at the next higher byte address (the specified address plus
one).
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: 0; cleared
Source Form
STY opr8a
STY opr16a
STY oprx0_xysp
STY oprx9,xysp
STY oprx16,xysp
STY [D,xysp]
STY [oprx16,xysp]
Access Detail
Address
Mode
Object Code
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
5D dd
7D hh ll
6D xb
6D xb ff
6D xb ee ff
6D xb
6D xb ee ff
HCS12
PW
PWO
PW
PWO
PWP
PIfW
PIPW
M68HC12
PW
WOP
PW
PWO
PWP
PIfPW
PIPPW
S12CPUV2
Reference Manual
MOTOROLA
289
Instruction Glossary
SUBA
Operation:
Description:
CCR Details:
SUBA
Subtract A
(A) – (M) ⇒ A
Subtracts the content of memory location M from the content of
accumulator A, and places the result in A. For subtraction instructions,
the C status bit represents a borrow.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: A7 • M7 • R7 + A7 • M7 • R7
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: A7 • M7 + M7 • R7 + R7 • A7
Set if the value of the content of memory is larger than the value of
the accumulator; cleared otherwise
Source Form
SUBA #opr8i
SUBA opr8a
SUBA opr16a
SUBA oprx0_xysp
SUBA oprx9,xysp
SUBA oprx16,xysp
SUBA [D,xysp]
SUBA [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
80 ii
90 dd
B0 hh ll
A0 xb
A0 xb ff
A0 xb ee ff
A0 xb
A0 xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
Reference Manual
S12CPUV2
290
MOTOROLA
Instruction Glossary
Glossary
SUBB
Operation:
Description:
CCR Details:
SUBB
Subtract B
(B) – (M) ⇒ B
Subtracts the content of memory location M from the content of
accumulator B and places the result in B. For subtraction instructions,
the C status bit represents a borrow.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: B7 • M7 • R7 + B7 • M7 • R7
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: B7 • M7 + M7 • R7 + R7 • B7
Set if the value of the content of memory is larger than the value of
the accumulator; cleared otherwise
Source Form
SUBB #opr8i
SUBB opr8a
SUBB opr16a
SUBB oprx0_xysp
SUBB oprx9,xysp
SUBB oprx16,xysp
SUBB [D,xysp]
SUBB [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
C0 ii
D0 dd
F0 hh ll
E0 xb
E0 xb ff
E0 xb ee ff
E0 xb
E0 xb ee ff
HCS12
M68HC12
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
S12CPUV2
Reference Manual
MOTOROLA
291
Instruction Glossary
SUBD
Operation:
Description:
CCR Details:
Subtract Double Accumulator
SUBD
(A : B) – (M : M + 1) ⇒ A : B
Subtracts the content of memory location M : M + 1 from the content of
double accumulator D and places the result in D. For subtraction
instructions, the C status bit represents a borrow.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
∆
∆
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $0000; cleared otherwise
V: D15 • M15 • R15 + D15 • M15 • R15
Set if a two’s complement overflow resulted from the operation;
cleared otherwise
C: D15 • M15 + M15 • R15 + R15 • D15
Set if the value of the content of memory is larger than the value of
the accumulator; cleared otherwise
Source Form
SUBD #opr16i
SUBD opr8a
SUBD opr16a
SUBD oprx0_xysp
SUBD oprx9,xyssp
SUBD oprx16,xysp
SUBD [D,xysp]
SUBD [oprx16,xysp]
Access Detail
Address
Mode
Object Code
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
83 jj kk
93 dd
B3 hh ll
A3 xb
A3 xb ff
A3 xb ee ff
A3 xb
A3 xb ee ff
HCS12
M68HC12
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
Reference Manual
S12CPUV2
292
MOTOROLA
Instruction Glossary
Glossary
SWI
Operation:
Description:
CCR Details:
Source Form
SWI
SWI
Software Interrupt
(SP) – $0002 ⇒ SP; RTNH : RTNL ⇒ (M(SP) : M(SP+1))
(SP) – $0002 ⇒ SP; YH : YL ⇒ (M(SP) : M(SP+1))
(SP) – $0002 ⇒ SP; XH : XL ⇒ (M(SP) : M(SP+1))
(SP) – $0002 ⇒ SP; B : A⇒ (M(SP) : M(SP+1))
(SP) – $0001 ⇒ SP; CCR ⇒ (M(SP))
1⇒I
(SWI Vector) ⇒ PC
Causes an interrupt without an external interrupt service request. Uses
the address of the next instruction after SWI as a return address. Stacks
the return address, index registers Y and X, accumulators B and A, and
the CCR, decrementing the SP before each item is stacked. The I mask
bit is then set, the PC is loaded with the SWI vector, and instruction
execution resumes at that location. SWI is not affected by the I mask bit.
Refer to Section 7. Exception Processing for more information.
S
X
H
I
N
Z
V
C
–
–
–
1
–
–
–
–
I:
1; set
Address
Mode
INH
Access Detail
Object Code
HCS12
3F
VSPSSPSsP(1)
M68HC12
VSPSSPSsP(1)
1. The CPU also uses the SWI processing sequence for hardware interrupts and unimplemented opcode traps. A variation
of the sequence (VfPPP) is used for resets.
S12CPUV2
Reference Manual
MOTOROLA
293
Instruction Glossary
TAB
Operation:
Description:
CCR Details:
TAB
Transfer from Accumulator A
to Accumulator B
(A) ⇒ B
Moves the content of accumulator A to accumulator B. The former
content of B is lost; the content of A is not affected. Unlike the general
transfer instruction TFR A,B which does not affect condition codes, the
TAB instruction affects the N, Z, and V status bits for compatibility with
M68HC11.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: 0; cleared
Source Form
TAB
Address
Mode
INH
Access Detail
Object Code
HCS12
18 0E
OO
M68HC12
OO
Reference Manual
S12CPUV2
294
MOTOROLA
Instruction Glossary
Glossary
TAP
Operation:
Description:
TAP
Transfer from Accumulator A
to Condition Code Register
(A) ⇒ CCR
Transfers the logic states of bits [7:0] of accumulator A to the
corresponding bit positions of the CCR. The content of A remains
unchanged. The X mask bit can be cleared as a result of a TAP, but
cannot be set if it was cleared prior to execution of the TAP. If the I bit is
cleared, there is a 1-cycle delay before the system allows interrupt
requests. This prevents interrupts from occurring between instructions in
the sequences CLI, WAI and CLI, SEI.
This instruction is accomplished with the TFR A,CCR instruction. For
compatibility with the M68HC11, the mnemonic TAP is translated by the
assembler.
CCR Details:
S
X
H
I
N
Z
V
C
∆
⇓
∆
∆
∆
∆
∆
∆
Condition codes take on the value of the corresponding bit of
accumulator A, except that the X mask bit cannot change from 0 to 1.
Software can leave the X bit set, leave it cleared, or change it from 1 to
0, but it can only be set by a reset or by recognition of an XIRQ interrupt.
Source Form
TAP translates to...
TFR A,CCR
Address
Mode
INH
Access Detail
Object Code
HCS12
B7 02
P
M68HC12
P
S12CPUV2
Reference Manual
MOTOROLA
295
Instruction Glossary
TBA
Operation:
Description:
CCR Details:
TBA
Transfer from Accumulator B
to Accumulator A
(B) ⇒ A
Moves the content of accumulator B to accumulator A. The former
content of A is lost; the content of B is not affected. Unlike the general
transfer instruction TFR B,A, which does not affect condition codes, the
TBA instruction affects N, Z, and V for compatibility with M68HC11.
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
–
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
V: 0; cleared
Source Form
TBA
Address
Mode
INH
Access Detail
Object Code
HCS12
18 0F
OO
M68HC12
OO
Reference Manual
S12CPUV2
296
MOTOROLA
Instruction Glossary
Glossary
TBEQ
Operation:
Description:
TBEQ
Test and Branch if Equal to Zero
If (Counter) = 0, then (PC) + $0003 + Rel ⇒ PC
Tests the specified counter register A, B, D, X, Y, or SP. If the counter
register is zero, branches to the specified relative destination. TBEQ is
encoded into three bytes of machine code including a 9-bit relative offset
(–256 to +255 locations from the start of the next instruction).
DBEQ and IBEQ instructions are similar to TBEQ, except that the
counter is decremented or incremented rather than simply being tested.
Bits 7 and 6 of the instruction postbyte are used to determine which
operation is to be performed.
CCR Details:
Source Form
TBEQ abdxys,rel9
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
Access Detail
Object Code(1)
HCS12
REL
04 lb rr
M68HC12
PPP/PPO
PPP
1. Encoding for lb is summarized in the following table. Bit 3 is not used (don’t care), bit 5 selects branch on zero (TBEQ – 0)
or not zero (TBNE – 1) versions, and bit 4 is the sign bit of the 9-bit relative offset. Bits 7 and 6 should be 0:1 for TBEQ.
Count
Bits 2:0 Source Form
Register
Object Code
Object Code
(If Offset is Positive) (If Offset is Negative)
A
B
000
001
TBEQ A, rel9
TBEQ B, rel9
04 40 rr
04 41 rr
04 50 rr
04 51 rr
D
X
Y
SP
100
101
110
111
TBEQ D, rel9
TBEQ X, rel9
TBEQ Y, rel9
TBEQ SP, rel9
04 44 rr
04 45 rr
04 46 rr
04 47 rr
04 54 rr
04 55 rr
04 56 rr
04 57 rr
S12CPUV2
Reference Manual
MOTOROLA
297
Instruction Glossary
TBL
Operation:
Description:
TBL
Table Lookup and Interpolate
(M) + [(B) × ((M+1) – (M))] ⇒ A
Linearly interpolates one of 256 result values that fall between each pair
of data entries in a lookup table stored in memory. Data entries in the
table represent the Y values of endpoints of equally spaced line
segments. Table entries and the interpolated result are 8-bit values. The
result is stored in accumulator A.
Before executing TBL, an index register points to the table entry
corresponding to the X value (X1) that is closest to, but less than or equal
to, the desired lookup point (XL, YL). This defines the left end of a line
segment and the right end is defined by the next data entry in the table.
Prior to execution, accumulator B holds a binary fraction (radix point to
left of MSB), representing the ratio (XL–X1) ÷ (X2–X1).
The 8-bit unrounded result is calculated using the following expression:
A = Y1 + [(B) × (Y2 – Y1)]
Where
(B) = (XL – X1) ÷ (X2 – X1)
Y1 = 8-bit data entry pointed to by <effective address>
Y2 = 8-bit data entry pointed to by <effective address> + 1
The intermediate value [(B) × (Y2 – Y1)] produces a 16-bit result with the
radix point between bits 7 and 8. Any indexed addressing mode
referenced to X, Y, SP, or PC, except indirect modes or 9-bit and 16-bit
offset modes, can be used to identify the first data point (X1,Y1). The
second data point is the next table entry.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
–
∆(1)
1. C-bit was undefined in original M68HC12.
N: Set if MSB of result is set; cleared otherwise
Z: Set if result is $00; cleared otherwise
C: Set if result can be rounded up; cleared otherwise
Source Form
TBL oprx0_xysp
Address
Mode
IDX
Access Detail
Object Code
18 3D xb
HCS12
M68HC12
ORfffP
OrrffffP
Reference Manual
S12CPUV2
298
MOTOROLA
Instruction Glossary
Glossary
TBNE
Operation:
Description:
TBNE
Test and Branch if Not Equal to Zero
If (Counter) ≠ 0, then (PC) + $0003 + Rel ⇒ PC
Tests the specified counter register A, B, D, X, Y, or SP. If the counter
register is not zero, branches to the specified relative destination. TBNE
is encoded into three bytes of machine code including a 9-bit relative
offset (–256 to +255 locations from the start of the next instruction).
DBNE and IBNE instructions are similar to TBNE, except that the
counter is decremented or incremented rather than simply being tested.
Bits 7 and 6 of the instruction postbyte are used to determine which
operation is to be performed.
CCR Details:
Source Form
TBNE abdxys,rel9
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
Access Detail
Object Code(1)
HCS12
REL
04 lb rr
M68HC12
PPP/PPO
PPP
1. Encoding for lb is summarized in the following table. Bit 3 is not used (don’t care), bit 5 selects branch on zero (TBEQ –
0) or not zero (TBNE – 1) versions, and bit 4 is the sign bit of the 9-bit relative offset. Bits 7 and 6 should be 0:1 for TBNE.
Count
Bits 2:0 Source Form
Register
Object Code
Object Code
(If Offset is Positive) (If Offset is Negative)
A
B
000
001
TBNE A, rel9
TBNE B, rel9
04 60 rr
04 61 rr
04 70 rr
04 71 rr
D
X
Y
SP
100
101
110
111
TBNE D, rel9
TBNE X, rel9
TBNE Y, rel9
TBNE SP, rel9
04 64 rr
04 65 rr
04 66 rr
04 67 rr
04 74 rr
04 75 rr
04 76 rr
04 77 rr
S12CPUV2
Reference Manual
MOTOROLA
299
Instruction Glossary
TFR
TFR
Transfer Register Content
to Another Register
Operation:
See table.
Description:
Transfers the content of a source register to a destination register
specified in the instruction. The order in which transfers between 8-bit
and 16-bit registers are specified affects the high byte of the 16-bit
registers differently. Cases involving TMP2 and TMP3 are reserved for
Motorola use, so some assemblers may not permit their use. It is
possible to generate these cases by using DC.B or DC.W assembler
directives.
S
CCR Details:
X
H
I
N
Z
V
C
Or:
–
–
–
–
–
–
–
–
S
X
H
I
N
Z
V
C
∆
⇓
∆
∆
∆
∆
∆
∆
None affected, unless the CCR is the destination register. Condition
codes take on the value of the corresponding source bits, except that the
X mask bit cannot change from 0 to 1. Software can leave the X bit set,
leave it cleared, or change it from 1 to 0, but it can be set only by a reset
or by recognition of an XIRQ interrupt.
Address
Mode
Source Form
TFR abcdxys,abcdxys
Access Detail
Object Code(1)
HCS12
INH
B7 eb
M68HC12
P
P
1. Legal coding for eb is summarized in the following table. Columns represent the high-order source digit. Rows represent
the low-order destination digit (MSB is a don’t-care). Values are in hexadecimal.
0
1
2
3
4
5
6
7
0
A⇒A
B⇒A
CCR ⇒ A
TMP3L ⇒ A
B⇒A
XL ⇒ A
YL ⇒ A
SPL ⇒ A
1
A⇒B
B⇒B
CCR ⇒ B
TMP3L ⇒ B
B⇒B
XL ⇒ B
YL ⇒ B
SPL ⇒ B
2
A ⇒ CCR
B ⇒ CCR
CCR ⇒ CCR
TMP3L ⇒ CCR
B ⇒ CCR
XL ⇒ CCR
YL ⇒ CCR
SPL ⇒ CCR
3
sex:A ⇒ TMP2
sex:B ⇒ TMP2
sex:CCR ⇒ TMP2
TMP3 ⇒ TMP2
D ⇒ TMP2
X ⇒ TMP2
Y ⇒ TMP2
SP ⇒ TMP2
sex:A ⇒ D
SEX A,D
sex:A ⇒ X
SEX A,X
sex:A ⇒ Y
SEX A,Y
sex:A ⇒ SP
SEX A,SP
sex:B ⇒ D
SEX B,D
sex:B ⇒ X
SEX B,X
sex:B ⇒ Y
SEX B,Y
sex:B ⇒ SP
SEX B,SP
sex:CCR ⇒ D
SEX CCR,D
sex:CCR ⇒ X
SEX CCR,X
sex:CCR ⇒ Y
SEX CCR,Y
sex:CCR ⇒ SP
SEX CCR,SP
TMP3 ⇒ D
D⇒D
X⇒D
Y⇒D
SP ⇒ D
TMP3 ⇒ X
D⇒X
X⇒X
Y⇒X
SP ⇒ X
TMP3 ⇒ Y
D⇒Y
X⇒Y
Y⇒Y
SP ⇒ Y
TMP3 ⇒ SP
D ⇒ SP
X ⇒ SP
Y ⇒ SP
SP ⇒ SP
4
5
6
7
Reference Manual
S12CPUV2
300
MOTOROLA
Instruction Glossary
Glossary
TPA
Operation:
Description:
Transfer from Condition Code
Register to Accumulator A
TPA
(CCR) ⇒ A
Transfers the content of the condition code register to corresponding bit
positions of accumulator A. The CCR remains unchanged.
This mnemonic is implemented by the TFR CCR,A instruction. For
compatibility with the M68HC11, the mnemonic TPA is translated into
the TFR CCR,A instruction by the assembler.
CCR Details:
Source Form
TPA
translates to... TFR CCR,A
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
B7 20
P
M68HC12
P
S12CPUV2
Reference Manual
MOTOROLA
301
Instruction Glossary
TRAP
Operation:
Description:
Unimplemented Opcode Trap
TRAP
(SP) – $0002 ⇒ SP; RTNH : RTNL ⇒ (M(SP) : M(SP+1))
(SP) – $0002 ⇒ SP; YH : YL ⇒ (M(SP) : M(SP+1))
(SP) – $0002 ⇒ SP; XH : XL ⇒ (M(SP) : M(SP+1))
(SP) – $0002 ⇒ SP; B : A⇒ (M(SP) : M(SP+1))
(SP) – $0001 ⇒ SP; CCR ⇒ (M(SP))
1⇒I
(Trap Vector) ⇒ PC
Traps unimplemented opcodes. There are opcodes in all 256 positions
in the page 1 opcode map, but only 54 of the 256 positions on page 2 of
the opcode map are used. If the CPU attempts to execute one of the
unimplemented opcodes on page 2, an opcode trap interrupt occurs.
Unimplemented opcode traps are essentially interrupts that share the
$FFF8:$FFF9 interrupt vector.
TRAP uses the next address after the unimplemented opcode as a
return address. It stacks the return address, index registers Y and X,
accumulators B and A, and the CCR, automatically decrementing the SP
before each item is stacked. The I mask bit is then set, the PC is loaded
with the trap vector, and instruction execution resumes at that location.
This instruction is not maskable by the I bit. Refer to Section 7.
Exception Processing for more information.
CCR Details:
Source Form
TRAP trapnum
S
X
H
I
N
Z
V
C
–
–
–
1
–
–
–
–
I:
1; set
Address
Mode
INH
Access Detail
Object Code
HCS12
$18 tn(1)
OVSPSSPSsP
M68HC12
OfVSPSSPSsP
1. The value tn represents an unimplemented page 2 opcode in either of the two ranges $30 to $39 or $40 to $FF.
Reference Manual
S12CPUV2
302
MOTOROLA
Instruction Glossary
Glossary
TST
Operation:
Description:
TST
Test Memory
(M) – $00
Subtracts $00 from the content of memory location M and sets the
condition codes accordingly.
The subtraction is accomplished internally without modifying M.
The TST instruction provides limited information when testing unsigned
values. Since no unsigned value is less than zero, BLO and BLS have
no utility following TST. While BHI can be used after TST, it performs the
same function as BNE, which is preferred. After testing signed values,
all signed branches are available.
CCR Details:
Source Form
TST opr16a
TST oprx0_xysp
TST oprx9,xysp
TST oprx16,xysp
TST [D,xysp]
TST [oprx16,xysp]
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
0
N:
Z:
V:
C:
Set if MSB of result is set; cleared otherwise
Set if result is $00; cleared otherwise
0; cleared
0; cleared
Access Detail
Address
Mode
Object Code
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
F7 hh ll
E7 xb
E7 xb ff
E7 xb ee ff
E7 xb
E7 xb ee ff
HCS12
M68HC12
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
S12CPUV2
Reference Manual
MOTOROLA
303
Instruction Glossary
TSTA
Operation:
Description:
TSTA
Test A
(A) – $00
Subtracts $00 from the content of accumulator A and sets the condition
codes accordingly.
The subtraction is accomplished internally without modifying A.
The TSTA instruction provides limited information when testing
unsigned values. Since no unsigned value is less than zero, BLO and
BLS have no utility following TSTA. While BHI can be used after TST, it
performs the same function as BNE, which is preferred. After testing
signed values, all signed branches are available.
CCR Details:
Source Form
TSTA
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
0
N:
Z:
V:
C:
Set if MSB of result is set; cleared otherwise
Set if result is $00; cleared otherwise
0; cleared
0; cleared
Address
Mode
INH
Access Detail
Object Code
HCS12
97
O
M68HC12
O
Reference Manual
S12CPUV2
304
MOTOROLA
Instruction Glossary
Glossary
TSTB
Operation:
Description:
TSTB
Test B
(B) – $00
Subtracts $00 from the content of accumulator B and sets the condition
codes accordingly.
The subtraction is accomplished internally without modifying B.
The TSTB instruction provides limited information when testing
unsigned values. Since no unsigned value is less than zero, BLO and
BLS have no utility following TSTB. While BHI can be used after TST, it
performs the same function as BNE, which is preferred. After testing
signed values, all signed branches are available.
CCR Details:
Source Form
TSTB
S
X
H
I
N
Z
V
C
–
–
–
–
∆
∆
0
0
N:
Z:
V:
C:
Set if MSB of result is set; cleared otherwise
Set if result is $00; cleared otherwise
0; cleared
0; cleared
Address
Mode
INH
Access Detail
Object Code
HCS12
D7
O
M68HC12
O
S12CPUV2
Reference Manual
MOTOROLA
305
Instruction Glossary
TSX
Operation:
Description:
CCR Details:
Source Form
TSX
translates to... TFR SP,X
TSX
Transfer from Stack Pointer
to Index Register X
(SP) ⇒ X
This is an alternate mnemonic to transfer the stack pointer value to index
register X. The content of the SP remains unchanged. After a TSX
instruction, X points at the last value that was stored on the stack.
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
B7 75
P
M68HC12
P
Reference Manual
S12CPUV2
306
MOTOROLA
Instruction Glossary
Glossary
TSY
Operation:
Description:
CCR Details:
Source Form
TSY
translates to... TFR SP,Y
TSY
Transfer from Stack Pointer
to Index Register Y
(SP) ⇒ Y
This is an alternate mnemonic to transfer the stack pointer value to index
register Y. The content of the SP remains unchanged. After a TSY
instruction, Y points at the last value that was stored on the stack.
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
B7 76
P
M68HC12
P
S12CPUV2
Reference Manual
MOTOROLA
307
Instruction Glossary
TXS
Operation:
Description:
CCR Details:
Source Form
TXS
translates to... TFR X,SP
TXS
Transfer from Index Register X
to Stack Pointer
(X) ⇒ SP
This is an alternate mnemonic to transfer index register X value to the
stack pointer. The content of X is unchanged.
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
B7 57
P
M68HC12
P
Reference Manual
S12CPUV2
308
MOTOROLA
Instruction Glossary
Glossary
TYS
Operation:
Description:
CCR Details:
Source Form
TYS
translates to... TFR Y,SP
TYS
Transfer from Index Register Y
to Stack Pointer
(Y) ⇒ SP
This is an alternate mnemonic to transfer index register Y value to the
stack pointer. The content of Y is unchanged.
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
B7 67
P
M68HC12
P
S12CPUV2
Reference Manual
MOTOROLA
309
Instruction Glossary
WAI
Operation:
Description:
WAI
Wait for Interrupt
(SP) – $0002 ⇒ SP; RTNH : RTNL ⇒ (M(SP) : M(SP+1))
(SP) – $0002 ⇒ SP; YH : YL ⇒ (M(SP) : M(SP+1))
(SP) – $0002 ⇒ SP; XH : XL ⇒ (M(SP) : M(SP+1))
(SP) – $0002 ⇒ SP; B : A⇒ (M(SP) : M(SP+1))
(SP) – $0001 ⇒ SP; CCR ⇒ (M(SP))
Stop CPU Clocks
Puts the CPU into a wait state. Uses the address of the instruction
following WAI as a return address. Stacks the return address, index
registers Y and X, accumulators B and A, and the CCR, decrementing
the SP before each item is stacked.
The CPU then enters a wait state for an integer number of bus clock
cycles. During the wait state, CPU clocks are stopped, but other MCU
clocks can continue to run. The CPU leaves the wait state when it
senses an interrupt that has not been masked.
Upon leaving the wait state, the CPU sets the appropriate interrupt mask
bit(s), fetches the vector corresponding to the interrupt sensed, and
instruction execution continues at the location the vector points to.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
Source Form
WAI (before interrupt)
WAI (when interrupt comes)
INH
Access Detail
Object Code
HCS12
M68HC12
OSSSSsf
OSSSfSsf
fVfPPP
VfPPP
3E
Although the WAI instruction itself does not alter the condition codes, the
interrupt that causes the CPU to resume processing also causes the I
mask bit (and the X mask bit, if the interrupt was XIRQ) to be set as the
interrupt vector is fetched.
Reference Manual
S12CPUV2
310
MOTOROLA
Instruction Glossary
Glossary
WAV
Operation:
WAV
Weighted Average
Do until B = 0, leave SOP in Y : D, SOW in X
Partial Product = (M pointed to by X) × (M pointed to by Y)
Sum-of-Products (24-bit SOP) = Previous SOP + Partial Product
Sum-of-Weights (16-bit SOW) = Previous SOW + (M pointed to by Y)
(X) + $0001 ⇒ X; (Y) + $0001 ⇒ Y
(B) – $01 ⇒ B
Description:
Performs weighted average calculations on values stored in memory.
Uses indexed (X) addressing mode to reference one source operand list,
and indexed (Y) addressing mode to reference a second source operand
list. Accumulator B is used as a counter to control the number of
elements to be included in the weighted average.
For each pair of data points, a 24-bit sum of products (SOP) and a 16-bit
sum of weights (SOW) is accumulated in temporary registers. When B
reaches zero (no more data pairs), the SOP is placed in Y : D. The SOW
is placed in X. To arrive at the final weighted average, divide the content
of Y : D by X by executing an EDIV after the WAV.
This instruction can be interrupted. If an interrupt occurs during WAV
execution, the intermediate results (six bytes) are stacked in the order
SOW[15:0], SOP[15:0], $00:SOP[23:16] before the interrupt is processed.
The wavr pseudo-instruction is used to resume execution after an
interrupt. The mechanism is re-entrant. New WAV instructions can be
started and interrupted while a previous WAV instruction is interrupted.
This instruction is often used in fuzzy logic rule evaluation. Refer to
Section 9. Fuzzy Logic Support for more information.
CCR Details:
S
X
H
I
N
Z
V
C
–
–
?
–
?
1
?
?
Z: 1; set
H, N, V and C may be altered by this instruction
Source Form
WAV
Address
Mode
Object Code
Special
18 3C
Access Detail(1)
HCS12
M68HC12
Of(frr,ffff)O
Off(frr,fffff)O
(replace comma if interrupted)
SSS + UUUrr
SSSf + UUUrr
1. The replace comma sequence in parentheses represents the loop for one iteration of SOP and SOW accumulation.
S12CPUV2
Reference Manual
MOTOROLA
311
Instruction Glossary
XGDX
Operation:
Description:
CCR Details:
Source Form
XGDX
translates to... EXG D,X
Exchange Double Accumulator
and Index Register X
XGDX
(D) ⇔ (X)
Exchanges the content of double accumulator D and the content of index
register X. For compatibility with the M68HC11, the XGDX instruction is
translated into an EXG D,X instruction by the assembler.
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
B7 C5
P
M68HC12
P
Reference Manual
S12CPUV2
312
MOTOROLA
Instruction Glossary
Glossary
XGDY
Operation:
Description:
CCR Details:
Source Form
XGDY
translates to... EXG D,Y
Exchange Double Accumulator
and Index Register Y
XGDY
(D) ⇔ (Y)
Exchanges the content of double accumulator D and the content of index
register Y. For compatibility with the M68HC11, the XGDY instruction is
translated into an EXG D,Y instruction by the assembler.
S
X
H
I
N
Z
V
C
–
–
–
–
–
–
–
–
Address
Mode
INH
Access Detail
Object Code
HCS12
B7 C6
P
M68HC12
P
S12CPUV2
Reference Manual
MOTOROLA
313
Instruction Glossary
Reference Manual
S12CPUV2
314
MOTOROLA
Reference Manual — S12CPUV2
Section 7. Exception Processing
7.1 Introduction
Exceptions are events that require processing outside the normal flow of
instruction execution. This section describes exceptions and the way
each is handled.
7.2 Types of Exceptions
Central processor unit (CPU12) exceptions include:
•
Resets
– Power-on reset and RESET pin
– Clock monitor reset
– COP watchdog reset
•
An unimplemented opcode trap
•
A software interrupt instruction (SWI)
•
Non-maskable (X-bit) interrupts
•
Non-maskable (I-bit) interrupts
Each exception has an associated 16-bit vector, which points to the
memory location where the routine that handles the exception is located.
As shown in Table 7-1, vectors are stored in the upper bytes of the
standard 64-Kbyte address map.
The six highest vector addresses are used for resets and unmaskable
interrupt sources. The remaining vectors are used for maskable
interrupts. All vectors must be programmed to point to the address of the
appropriate service routine.
S12CPUV2
MOTOROLA
Reference Manual
Exception Processing
315
Exception Processing
Table 7-1. CPU12 Exception Vector Map(1)
Vector Address
Source
$FFFE–$FFFF
System reset
$FFFC–$FFFD
Clock monitor reset
$FFFA–$FFFB
COP reset
$FFF8–$FFF9
Unimplemented opcode trap
$FFF6–$FFF7
Software interrupt instruction (SWI)
$FFF4–$FFF5
XIRQ signal
$FFF2–$FFF3
IRQ signal
$FF00–$FFF1
Device-specific interrupt sources (HCS12)
$FFC0–$FFF1
Device-specific interrupt sources (M68HC12)
1. See Device User Guide and Interrupt Block Guide for further details
The CPU12 can handle up to 128 exception vectors, but the number
actually used varies from device to device, and some vectors are
reserved for Motorola use. Refer to Device User Guide for more
information.
Exceptions can be classified by the effect of the X and I interrupt mask
bits on recognition of a pending request.
•
Resets, the unimplemented opcode trap, and the SWI instruction
are not affected by the X and I mask bits.
•
Interrupt service requests from the XIRQ pin are inhibited when
X = 1, but are not affected by the I bit.
•
All other interrupts are inhibited when I = 1.
7.3 Exception Priority
A hardware priority hierarchy determines which reset or interrupt is
serviced first when simultaneous requests are made. Six sources are not
maskable. The remaining sources are maskable, and the device
integration module typically can change the relative priorities of
maskable interrupts. Refer to 7.5 Interrupts for more detail concerning
interrupt priority and servicing.
Reference Manual
316
S12CPUV2
Exception Processing
MOTOROLA
Exception Processing
Exception Priority
The priorities of the unmaskable sources are:
1. RESET pin or power-on reset (POR)
2. Clock monitor reset
3. Computer operating properly (COP) watchdog reset
4. Non-maskable interrupt request (XIRQ) signal
5. Unimplemented opcode trap
6. Software interrupt instruction (SWI)
External reset and POR share the highest exception-processing priority,
followed by clock monitor reset, and then the on-chip watchdog reset.
The XIRQ interrupt is pseudo-non-maskable. After reset, the X bit in the
CCR is set, which inhibits all interrupt service requests from the XIRQ
pin until the X bit is cleared. The X bit can be cleared by a program
instruction, but program instructions cannot change X from 0 to 1. Once
the X bit is cleared, interrupt service requests made via the XIRQ pin
become non-maskable.
The unimplemented page 2 opcode trap (TRAP) and the SWI are special
cases. In one sense, these two exceptions have very low priority,
because any enabled interrupt source that is pending prior to the time
exception processing begins will take precedence. However, once the
CPU begins processing a TRAP or SWI, neither can be interrupted.
Also, since these are mutually exclusive instructions, they have no
relative priority.
All remaining interrupts are subject to masking via the I bit in the CCR.
Most HCS12 microcontroller units (MCU) have an external IRQ pin,
which is assigned the highest I-bit interrupt priority and an internal
periodic real-time interrupt generator, which has the next highest priority.
The other maskable sources have default priorities that follow the
address order of the interrupt vectors — the higher the address, the
higher the priority of the interrupt. Other maskable interrupts are
associated with on-chip peripherals such as timers or serial ports.
Typically, logic in the device integration module can give one I-masked
source priority over other I-masked sources. Refer to the documentation
for the specific HCS12 derivative for more information.
S12CPUV2
MOTOROLA
Reference Manual
Exception Processing
317
Exception Processing
7.4 Resets
M68HC12 devices perform resets with a combination of hardware and
software. Integration module circuitry determines the type of reset that
has occurred, performs basic system configuration, then passes control
to the CPU12. The CPU fetches a vector determined by the type of reset
that has occurred, jumps to the address pointed to by the vector, and
begins to execute code at that address.
The are four possible sources of reset are:
•
Power-on reset (POR)
•
External reset (RESET pin)
•
COP reset
•
Clock monitor reset
Power-on reset (POR) and external reset share the same reset vector.
The computer operating properly (COP) reset and the clock monitor
reset each have a vector.
7.4.1 Power-On Reset
The HCS12 incorporate circuitry to detect a positive transition in the VDD
supply and initialize the device during cold starts, generally by asserting
the reset signal internally. The signal is typically released after a delay
that allows the device clock generator to stabilize.
7.4.2 External Reset
The MCU distinguishes between internal and external resets by sensing
how quickly the signal on the RESET pin rises to logic level 1 after it has
been asserted. When the MCU senses any of the four reset conditions,
internal circuitry drives the RESET signal low for N clock cycles, then
releases. M clock cycles later, the MCU samples the state of the signal
applied to the RESET pin. If the signal is still low, an external reset has
occurred. If the signal is high, reset is assumed to have been initiated
internally by either the COP system or the clock monitor.
Reference Manual
318
S12CPUV2
Exception Processing
MOTOROLA
Exception Processing
Interrupts
7.4.3 COP Reset
The MCU includes a computer operating properly (COP) system to help
protect against software failures. When the COP is enabled, software
must write a particular code sequence to a specific address to keep a
watchdog timer from timing out. If software fails to execute the sequence
properly, a reset occurs.
7.4.4 Clock Monitor Reset
The clock monitor circuit uses an internal RC circuit to determine
whether clock frequency is above a predetermined limit. If clock
frequency falls below the limit when the clock monitor is enabled, a reset
occurs.
7.5 Interrupts
Each HCS12 device can recognize a number of interrupt sources. Each
source has a vector in the vector table. The XIRQ signal, the
unimplemented opcode trap, and the SWI instruction are non-maskable,
and have a fixed priority. The remaining interrupt sources can be
masked by the I bit. In most devices, the external interrupt request pin is
assigned the highest maskable interrupt priority, and the internal
periodic real-time interrupt generator has the next highest priority. Other
maskable interrupts are associated with on-chip peripherals such as
timers or serial ports. These maskable sources have default priorities
that follow the address order of the interrupt vectors. The higher the
vector address, the higher the priority of the interrupt. Typically, a device
integration module incorporates logic that can give any one maskable
source priority over other maskable sources.
7.5.1 Non-Maskable Interrupt Request (XIRQ)
The XIRQ input is an updated version of the non-maskable interrupt
(NMI) input of earlier MCUs. The XIRQ function is disabled during
system reset and upon entering the interrupt service routine for an XIRQ
interrupt.
S12CPUV2
MOTOROLA
Reference Manual
Exception Processing
319
Exception Processing
During reset, both the I bit and the X bit in the CCR are set. This disables
maskable interrupts and interrupt service requests made by asserting
the XIRQ signal. After minimum system initialization, software can clear
the X bit using an instruction such as ANDCC #$BF. Software cannot set
the X bit from 0 to 1 once it has been cleared, and interrupt requests
made via the XIRQ pin become non-maskable. When a non-maskable
interrupt is recognized, both the X and I bits are set after context is
saved. The X bit is not affected by maskable interrupts. Execution of an
return-from-interrupt (RTI) instruction at the end of the interrupt service
routine normally restores the X and I bits to the pre-interrupt request
state.
7.5.2 Maskable Interrupts
Maskable interrupt sources include on-chip peripheral systems and
external interrupt service requests. Interrupts from these sources are
recognized when the global interrupt mask bit (I) in the CCR is cleared.
The default state of the I bit out of reset is 1, but it can be written at any
time.
The interrupt module manages maskable interrupt priorities. Typically,
an on-chip interrupt source is subject to masking by associated bits in
control registers in addition to global masking by the I bit in the CCR.
Sources generally must be enabled by writing one or more bits in
associated control registers. There may be other interrupt-related
control bits and flags, and there may be specific register read-write
sequences associated with interrupt service. Refer to individual on-chip
peripheral descriptions for details.
7.5.3 Interrupt Recognition
Once enabled, an interrupt request can be recognized at any time after
the I mask bit is cleared. When an interrupt service request is
recognized, the CPU responds at the completion of the instruction being
executed. Interrupt latency varies according to the number of cycles
required to complete the current instruction. Because the fuzzy logic rule
evaluation (REV), fuzzy logic rule evaluation weighted (REVW), and
weighted average (WAV) instructions can take many cycles to complete,
they are designed so that they can be interrupted. Instruction execution
resumes when interrupt execution is complete. When the CPU begins to
Reference Manual
320
S12CPUV2
Exception Processing
MOTOROLA
Exception Processing
Interrupts
service an interrupt, the instruction queue is refilled, a return address is
calculated, and then the return address and the contents of the CPU
registers are stacked as shown in Table 7-2.
Table 7-2. Stacking Order on Entry to Interrupts
Memory Location
CPU Registers
SP + 7
RTNH : RTNL
SP + 5
YH : YL
SP + 3
XH : XL
SP + 1
B:A
SP
CCR
After the CCR is stacked, the I bit (and the X bit, if an XIRQ interrupt
service request caused the interrupt) is set to prevent other interrupts
from disrupting the interrupt service routine. Execution continues at the
address pointed to by the vector for the highest-priority interrupt that was
pending at the beginning of the interrupt sequence. At the end of the
interrupt service routine, an RTI instruction restores context from the
stacked registers, and normal program execution resumes.
7.5.4 External Interrupts
External interrupt service requests are made by asserting an active-low
signal connected to the IRQ pin. Typically, control bits affect how the
signal is detected and recognized.
The I bit serves as the IRQ interrupt enable flag. When an IRQ interrupt
is recognized, the I bit is set to inhibit interrupts during the interrupt
service routine. Before other maskable interrupt requests can be
recognized, the I bit must be cleared. This is generally done by an RTI
instruction at the end of the service routine.
7.5.5 Return-from-Interrupt Instruction (RTI)
RTI is used to terminate interrupt service routines. RTI is an 8-cycle
instruction when no other interrupt is pending and 11 cycles (10 cycles
in M68HC12) when another interrupt is pending. In either case, the first
five cycles are used to restore (pull) the CCR, B:A, X, Y, and the return
S12CPUV2
MOTOROLA
Reference Manual
Exception Processing
321
Exception Processing
address from the stack. If no other interrupt is pending at this point, three
program words are fetched to refill the instruction queue from the area
of the return address and processing proceeds from there.
If another interrupt is pending after registers are restored, a new vector
is fetched, and the stack pointer is adjusted to point at the CCR value
that was just recovered (SP = SP – 9). This makes it appear that the
registers have been stacked again. After the SP is adjusted, three
program words are fetched to refill the instruction queue, starting at the
address the vector points to. Processing then continues with execution
of the instruction that is now at the head of the queue.
7.6 Unimplemented Opcode Trap
The CPU12 has opcodes in all 256 positions in the page 1 opcode map,
but only 54 of the 256 positions on page 2 of the opcode map are used.
If the CPU attempts to execute one of the 202 unused opcodes on
page 2, an unimplemented opcode trap occurs. The 202 unimplemented
opcodes are essentially interrupts that share a common interrupt vector,
$FFF8:$FFF9.
The CPU12 uses the next address after an unimplemented page 2
opcode as a return address. This differs from the M68HC11 illegal
opcode interrupt, which uses the address of an illegal opcode as the
return address. In the CPU12, the stacked return address can be used
to calculate the address of the unimplemented opcode for
software-controlled traps.
7.7 Software Interrupt Instruction (SWI)
Execution of the SWI instruction causes an interrupt without an interrupt
service request. SWI is not inhibited by the global mask bits in the CCR,
and execution of SWI sets the I mask bit. Once an SWI interrupt begins,
maskable interrupts are inhibited until the I bit in the CCR is cleared. This
typically occurs when an RTI instruction at the end of the SWI service
routine restores context.
Reference Manual
322
S12CPUV2
Exception Processing
MOTOROLA
Exception Processing
Exception Processing Flow
7.8 Exception Processing Flow
The first cycle in the exception processing flow for all CPU12 exceptions
is the same, regardless of the source of the exception. Between the first
and second cycles of execution, the CPU chooses one of three
alternative paths. The first path is for resets, the second path is for
pending X or I interrupts, and the third path is used for software
interrupts (SWI) and trapping unimplemented opcodes. The last two
paths are virtually identical, differing only in the details of calculating the
return address. Refer to Figure 7-1 for the following discussion.
7.8.1 Vector Fetch
The first cycle of all exception processing, regardless of the cause, is a
vector fetch. The vector points to the address where exception
processing will continue. Exception vectors are stored in a table located
at the top of the memory map ($FFxx). The CPU cannot use the fetched
vector until the third cycle of the exception processing sequence.
During the vector fetch cycle, the CPU issues a signal that tells the
interrupt module to drive the vector address of the highest priority,
pending exception onto the system address bus (the CPU does not
provide this address).
After the vector fetch, the CPU selects one of the three alternate
execution paths, depending upon the cause of the exception.
7.8.2 Reset Exception Processing
If reset caused the exception, processing continues to cycle 2.0. This
cycle sets the S, X, and I bits in the CCR. Cycles 3.0 through 5.0 are
program word fetches that refill the instruction queue. Fetches start at
the address pointed to by the reset vector. When the fetches are
completed, exception processing ends, and the CPU starts executing
the instruction at the head of the instruction queue.
S12CPUV2
MOTOROLA
Reference Manual
Exception Processing
323
Exception Processing
START
OPCODE TRAP?
YES
NO
1.0 - V
YES
FETCH VECTOR
T.1 - f
INTERNAL CALCULATIONS
2.2 - S
PUSH RETURN ADDRESS
RESET?
NO
INTERRUPT?
NO
YES
2.0 - f
NO BUS ACCESS
2.1 - S
PUSH RETURN ADDRESS
SET S, X, AND I
ADDRESS OF INST THAT WOULD HAVE
EXECUTED IF NO INTERRUPT
ADDRESS OF INST AFTER SWI OR
UNIMPLEMENTED OPCODE
3.0 - P
3.1 - P
3.2 - P
FETCH PROGRAM WORD
FETCH PROGRAM WORD
FETCH PROGRAM WORD
START TO FILL INSTRUCTION QUEUE
START TO FILL INSTRUCTION QUEUE
START TO FILL INSTRUCTION QUEUE
4.0 - P
4.1 - S
PUSH Y
4.2 - S
PUSH Y
5.1 - S
PUSH X
5.2 - S
PUSH X
6.1 - P
FETCH PROGRAM WORD
6.2 - P
FETCH PROGRAM WORD
FETCH PROGRAM WORD
CONTINUE TO FILL INSTRUCTION
QUEUE
5.0 - P
FETCH PROGRAM WORD
FINISH FILLING INSTRUCTION QUEUE
END
CONTINUE TO FILL INST. QUEUE
TRANSFER B:A TO 16-BIT TEMP REG
CONTINUE TO FILL INST. QUEUE
TRANSFER B:A TO 16-BIT TEMP REG
7.1 - S
PUSH B:A
7.2 - S
PUSH B:A
8.1 - s
PUSH CCR (BYTE)
8.2 - s
PUSH CCR (BYTE)
SET I BIT
IF XIRQ, SET X BIT
SET I BIT
9.2 - P
9.1 - P
FETCH PROGRAM WORD
FETCH PROGRAM WORD
FINISH FILLING INSTRUCTION QUEUE
FINISH FILLING INSTRUCTION QUEUE
END
END
Figure 7-1. Exception Processing Flow Diagram
Reference Manual
324
S12CPUV2
Exception Processing
MOTOROLA
Exception Processing
Exception Processing Flow
7.8.3 Interrupt and Unimplemented Opcode Trap Exception Processing
If an exception was not caused by a reset, a return address is calculated.
• Cycles 2.1and 2.2 are both S cycles (stack a 16-bit word), but the
CPU12 performs different return address calculations for each
type of exception.
– When an X- or I-related interrupt causes the exception, the
return address points to the next instruction that would have
been executed had processing not been interrupted.
– When an exception is caused by an SWI opcode or by an
unimplemented opcode (see 7.6 Unimplemented Opcode
Trap), the return address points to the next address after the
opcode.
•
Once calculated, the return address is pushed onto the stack.
•
Cycles 3.1 through 9.1 are identical to cycles 3.2 through 9.2 for
the rest of the sequence, except for optional setting of the X mask
bit performed in cycle 8.1 (see below).
•
Cycle 3.1/3.2 is the first of three program word fetches that refill
the instruction queue.
•
Cycle 4.1/4.2 pushes Y onto the stack.
•
Cycle 5.1/5.2 pushes X onto the stack.
•
Cycle 6.1/6.2 is the second of three program word fetches that
refill the instruction queue. During this cycle, the contents of the A
and B accumulators are concatenated into a 16-bit word in the
order B:A. This makes register order in the stack frame the same
as that of the M68HC11, M6801, and the M6800.
•
Cycle 7.1/7.2 pushes the 16-bit word containing B:A onto the
stack.
•
Cycle 8.1/8.2 pushes the 8-bit CCR onto the stack, then updates
the mask bits.
– When an XIRQ interrupt causes an exception, both X and I are
set, which inhibits further interrupts during exception
processing.
– When any other interrupt causes an exception, the I bit is set,
but the X bit is not changed.
S12CPUV2
MOTOROLA
Reference Manual
Exception Processing
325
Exception Processing
•
Cycle 9.1/9.2 is the third of three program word fetches that refill
the instruction queue. It is the last cycle of exception processing.
After this cycle the CPU starts executing the first cycle of the
instruction at the head of the instruction queue.
Reference Manual
326
S12CPUV2
Exception Processing
MOTOROLA
Reference Manual — S12CPUV2
Section 8.
Instruction Queue
8.1 Introduction
This section describes development and debug support features related
to the central processor unit (CPU12). Topics include:
•
Single-wire background debug interface
•
Hardware breakpoint system
•
Instruction queue operation and reconstruction
•
Instruction tagging
1 = Valid Data
TRACE — Trace Flag
Indicates when tracing is enabled. Firmware in the BDM ROM sets
TRACE in response to a TRACE1 command and TRACE is cleared
upon completion of the TRACE1 command. Do not attempt to write
TRACE directly with WRITE_BD_BYTE commands.
0 = Tracing not enabled
1 = TRACE1 command in progress
8.2 External Reconstruction of the Queue
The CPU12 uses an instruction queue to buffer program information and
increase instruction throughput. The HCS12 implements the queue
somewhat differently from the original M68HC12. The HCS12 queue
consists of three 16-bit stages while the M68HC12 queue consists of two
16-bit stages, plus a 16-bit holding latch. Program information is always
fetched in aligned 16-bit words. At least three bytes of program
information are available to the CPU when instruction execution begins.
The holding latch in the M68HC12 is used when a word of program
information arrives before the queue can advance.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Queue
327
Instruction Queue
Because of the queue, program information is fetched a few cycles
before it is used by the CPU. Internally, the microcontroller unit (MCU)
only needs to buffer the fetched data. But, in order to monitor
cycle-by-cycle CPU activity externally, it is necessary to capture data
and address to discern what is happening in the instruction queue.
Two external pins, IPIPE1 and IPIPE0, provide time-multiplexed
information about data movement in the queue and instruction
execution. The instruction queue and cycle-by-cycle activity can be
reconstructed in real time or from trace history captured by a logic
analyzer. However, neither scheme can be used to stop the CPU12
at a specific instruction. By the time an operation is visible outside the
MCU, the instruction has already begun execution. A separate
instruction tagging mechanism is provided for this purpose. A tag follows
the information in the queue as the queue is advanced. During
debugging, the CPU enters active background debug mode when
a tagged instruction reaches the head of the queue, rather than
executing the tagged instruction. For more information about tagging,
refer to 8.6 Instruction Tagging.
8.3 Instruction Queue Status Signals
The IPIPE1 and IPIPE0 signals carry time-multiplexed information about
data movement and instruction execution during normal CPU operation.
The signals are available on two multifunctional device pins. During
reset, the pins are used as mode-select input signals MODA and MODB.
To reconstruct the queue, the information carried by the status signals
must be captured externally. In general, data movement and execution
start information are considered to be distinct 2-bit values, with the
low-order bit on IPIPE0 and the high-order bit on IPIPE1.
Reference Manual
328
S12CPUV2
Instruction Queue
MOTOROLA
Instruction Queue
Instruction Queue Status Signals
8.3.1 HCS12 Timing Detail
In the HCS12, data-movement information is available when E clock is
high or on falling edges of the E clock; execution-start information is
available when E clock is low or on rising edges of the E clock, as shown
in Figure 8-1. Data-movement information refers to data on the bus.
Execution-start information refers to the bus cycle that starts with that
E-low time and continues through the following E-high time. Table 8-1
summarizes the information encoded on the IPIPE1 and IPIPE0 pins.
EX1 REFERS TO
THIS CYCLE
CYCLE 0
CYCLE 1
ADDR0
ADDR1
E CLOCK
ADDRESS
DATA
IPIPE[1:0]
DATA0
EX0
DM0
DATA1
EX1
DM1
DM0 REFERS TO DATA
CAPTURED AT THE END
OF CURRENT E-HIGH PERIOD
Figure 8-1. Queue Status Signal Timing (HCS12)
8.3.2 M68HC12 Timing Detail
In the M68HC12, data movement information is available on rising
edges of the E clock; execution start information is available on falling
edges of the E clock, as shown in Figure 8-2. Data movement
information refers to data on the bus at the previous falling edge of E.
Execution information refers to the bus cycle from the current falling
edge to the next falling edge of E. Table 8-1 summarizes the information
encoded on the IPIPE1 and IPIPE0 pins.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Queue
329
Instruction Queue
EX1 REFERS TO
THIS CYCLE
CYCLE 0
CYCLE 1
CYCLE 2
ADDR0
ADDR1
ADDR2
E CLOCK
ADDRESS
DATA
DATA0
IPIPE[1:0]
DATA1
EX1
DM0
DATA2
EX2
DM1
DM0 REFERS TO DATA
CAPTURED AT
PREVIOUS E FALL
Figure 8-2. Queue Status Signal Timing (M68HC12)
Table 8-1. IPIPE1 and IPIPE0 Decoding (HCS12 and M68HC12)
Mnemonic
Data Movement
Meaning
Capture at E Fall in HCS12 (E Rise in M68HC12)
0:0
—
No movement
0:1
LAT(1)
Latch data from bus
1:0
ALD
Advance queue and load from bus
1:1
ALL(1)
Advance queue and load from latch
Execution Start
Capture at E Rise in HCS12 (E Fall in M68HC12)
0:0
—
No start
0:1
INT
Start interrupt sequence
1:0
SEV
Start even instruction
1:1
SOD
Start odd instruction
1. The HCS12 implementation does not include a holding latch, so these data movement
codes are used only in the original M68HC12.
Reference Manual
330
S12CPUV2
Instruction Queue
MOTOROLA
Instruction Queue
Instruction Queue Status Signals
8.3.3 Null (Code 0:0)
The 0:0 data movement state indicates that there was no data
movement in the instruction queue; the 0:0 execution start state
indicates continuation of an instruction or interrupt sequence (no new
instruction or interrupt start).
8.3.4 LAT — Latch Data from Bus (Code 0:1)
This code is not used in the HCS12. In the M68HC12, fetched program
information has arrived, but the queue is not ready to advance. The
information is latched into a buffer. Later, when the queue does
advance, stage 1 is refilled from the buffer or from the data bus if the
buffer is empty. In some instruction sequences, there can be several
latch cycles before the queue advances. In these cases, the buffer is
filled on the first latch event and additional latch requests are ignored.
8.3.5 ALD — Advance and Load from Data Bus (Code 1:0)
The instruction queue is advanced by one word and stage one is refilled
with a word of program information from the data bus. The CPU
requested the information two bus cycles earlier but, due to access
delays, the information was not available until the E cycle referred to by
the ALD code.
8.3.6 ALL — Advance and Load from Latch (Code 1:1)
This code is not used in the HCS12. In the M68HC12, the 2-stage
instruction queue is advanced by one word and stage one is refilled with
a word of program information from the buffer. The information was
latched from the data bus at the falling edge of a previous E cycle
because the instruction queue was not ready to advance when it arrived.
8.3.7 INT — Interrupt Sequence Start (Code 0:1)
The E cycle associated with this code is the first cycle of an interrupt
sequence. Normally, this cycle is a read of the interrupt vector. However,
in systems that have interrupt vectors in external memory and an 8-bit
data bus, this cycle reads the upper byte of the 16-bit interrupt vector.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Queue
331
Instruction Queue
8.3.8 SEV — Start Instruction on Even Address (Code 1:0)
The E cycle associated with this code is the first cycle of the instruction
in the even (high order) half of the word at the head of the instruction
queue. The queue treats the $18 prebyte for instructions on page 2 of
the opcode map as a special 1-byte, 1-cycle instruction, except that
interrupts are not recognized at the boundary between the prebyte and
the rest of the instruction.
8.3.9 SOD — Start Instruction on Odd Address (Code 1:1)
The E cycle associated with this code is the first cycle of the instruction
in the odd (low order) half of the word at the head of the instruction
queue. The queue treats the $18 prebyte for instructions on page 2 of
the opcode map as a special 1-byte, 1-cycle instruction, except that
interrupts are not recognized at the boundary between the prebyte and
the rest of the instruction.
8.4 Queue Reconstruction (for HCS12)
The raw signals required for queue reconstruction are the address bus
(ADDR), the data bus (DATA), the system clock (E), and the queue
status signals (IPIPE1 and IPIPE2). An ALD data movement implies a
read; therefore, it is not necessary to capture the R/W signal. An E clock
cycle begins at a falling edge of E. Addresses and execution status must
be captured at the rising E edge in the middle of the cycle. Data and
data-movement status must be captured at the falling edge of E at the
end of the cycle. These captures can then be organized into records with
one record per E clock cycle.
Implementation details depend on the type of MCU and the mode of
operation. For instance, the data bus can be eight bits or 16 bits wide,
and nonmultiplexed or multiplexed. In all cases, the externally
reconstructed queue must use 16-bit words. Demultiplexing and
assembly of 8-bit data into 16-bit words is done before program
information enters the real queue, so it must also be done for the
external reconstruction.
Reference Manual
332
S12CPUV2
Instruction Queue
MOTOROLA
Instruction Queue
Queue Reconstruction (for HCS12)
An example:
Systems with an 8-bit data bus and a program stored in external
memory require two cycles for each program word fetch. MCU
bus-control logic freezes the CPU clocks long enough to do two 8-bit
accesses rather than a single 16-bit access, so the CPU sees only
16-bit words of program information. To recover the 16-bit program
words externally, latch the data bus state at the falling edge of E when
ADDR0 = 0, and gate the outputs of the latch onto DATA[15:8] when
an ALD cycle occurs. Since the 8-bit data bus is connected to
DATA[7:0], the 16-bit word on the data lines corresponds to the ALD
during the last half of the second 8-bit fetch, which is always to an odd
address. IPIPE[1:0] status signals indicate 0:0 for the second half of
the E cycle corresponding to the first 8-bit fetch.
Some MCUs have address lines to support memory expansion beyond
the standard 64-Kbyte address space. When memory expansion is
used, expanded addresses must also be captured and maintained.
8.4.1 Queue Reconstruction Registers (for HCS12)
Queue reconstruction requires the following registers, which can be
implemented as software variables when previously captured trace data
is used, or as hardware latches in real time.
8.4.1.1 fetch_add Register
This register buffers the fetch address.
8.4.1.2 st1_add, st1_dat Registers
These registers contain address and data for the first stage of the
reconstructed instruction queue.
8.4.1.3 st2_add, st2_dat Registers
These registers contain address and data for the middle stage of the
reconstructed instruction queue.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Queue
333
Instruction Queue
8.4.1.4 st3_add, st3_dat Registers
These registers contain address and data for the final stage of the
reconstructed instruction queue. When the IPIPE[1:0] signals indicate
the execution status, the address and opcode can be found in these
registers.
8.4.2 Reconstruction Algorithm (for HCS12)
This section describes how to use IPIPE[1:0] signals and queue
reconstruction registers to reconstruct the queue.
Typically, the first few cycles of raw capture data are not useful because
it takes several cycles before an instruction propagates to the head of
the queue. During these first raw cycles, the only meaningful information
available is data movement signals. Information on the external address
and data buses during this setup time is still captured and propagated
through the reconstructed queue, but the information reflects the actions
of instructions that were fetched before data collection started.
In the special case of a reset, there is a five-cycle sequence (VfPPP)
during which the reset vector is fetched and the instruction queue is
filled, before execution of the first instruction begins. Due to the timing of
the switchover of the IPIPE[1:0] pins from their alternate function as
mode-select inputs, the status information on these two pins may be
erroneous during the first cycle or two after the release of reset. This is
not a problem because the status is correct in time for queue
reconstruction logic to correctly replicate the queue.
On an advance-and-load-from-data-bus (ALD) cycle, the information in
the instruction queue must advance by one stage. Whatever was in
stage three of the queue simply disappears. The previous contents of
stage two go to stage three, the previous contents of stage one go to
stage two, and the contents of fetch_add and data from the current cycle
go to stage one.
Figure 8-3 shows the reset sequence and illustrates the relationship
between instruction cycle codes (VfPPP) and pipe status signals. One
cycle of the data bus is shown to indicate the relationship between the
ALD data movement code and the data value it refers to. The SEV
execution start code indicates that the reset vector pointed to an even
address in this example.
Reference Manual
334
S12CPUV2
Instruction Queue
MOTOROLA
Instruction Queue
Queue Reconstruction (for M68HC12)
INSTRUCTION
CYCLE CODES
V
f
P
P
E CLOCK
DM
FIRST
USER
INSTRUCTION
P
DM
DM
EX
10
ALD
10
SEV
DATA BUS
IPIPE[1:0]
00
00
00
00
00
10
ALD
00
10
ALD
00
Figure 8-3. Reset Sequence for HCS12
8.5 Queue Reconstruction (for M68HC12)
The raw signals required for queue reconstruction are the address bus
(ADDR), the data bus (DATA), the system clock (E), and the queue
status signals (IPIPE1 and IPIPE0). An E-clock cycle begins after an E
fall. Addresses and data movement status must be captured at the E rise
in the middle of the cycle. Data and execution start status must be
captured at the E fall at the end of the cycle. These captures can then be
organized into records with one record per E clock cycle.
Implementation details depend upon the type of device and the mode of
operation. For instance, the data bus can be eight bits or 16 bits wide,
and non-multiplexed or multiplexed. In all cases, the externally
reconstructed queue must use 16-bit words. Demultiplexing and
assembly of 8-bit data into 16-bit words is done before program
information enters the real queue, so it must also be done for the
external reconstruction.
An example:
Systems with an 8-bit data bus and a program stored in external
memory require two cycles for each program word fetch. MCU bus
control logic freezes the CPU clocks long enough to do two 8-bit
accesses rather than a single 16-bit access, so the CPU sees only
16-bit words of program information. To recover the 16-bit program
words externally, latch the data bus state at the falling edge of E when
ADDR0 = 0, and gate the outputs of the latch onto DATA[15:8] when
a LAT or ALD cycle occurs. Since the 8-bit data bus is connected to
DATA[7:0], the 16-bit word on the data lines corresponds to the ALD
or LAT status indication at the E rise after the second 8-bit fetch,
S12CPUV2
MOTOROLA
Reference Manual
Instruction Queue
335
Instruction Queue
which is always to an odd address. IPIPE1 and IPIPE0 status signals
indicate 0:0 at the beginning (E fall) and middle (E rise) of the first 8-bit
fetch.
Some M68HC12 devices have address lines to support memory
expansion beyond the standard 64-Kbyte address space. When
memory expansion is used, expanded addresses must also be captured
and maintained.
8.5.1 Queue Reconstruction Registers (for M68HC12)
Queue reconstruction requires these registers, which can be
implemented as software variables when previously captured trace data
is used or as hardware latches in real time.
8.5.1.1 in_add, in_dat Registers
These registers contain the address and data from the previous external
bus cycle. Depending on how records are read and processed from the
raw capture information, it may be possible to simply read this
information from the raw capture data file when needed.
8.5.1.2 fetch_add, fetch_dat Registers
These registers buffer address and data for information that was fetched
before the queue was ready to advance.
8.5.1.3 st1_add, st1_dat Registers
These registers contain address and data for the first stage of the
reconstructed instruction queue.
8.5.1.4 st2_add, st2_dat Registers
These registers contain address and data for the final stage of the
reconstructed instruction queue. When the IPIPE1 and IPIPE0 signals
indicate that an instruction is starting to execute, the address and
opcode can be found in these registers.
Reference Manual
336
S12CPUV2
Instruction Queue
MOTOROLA
Instruction Queue
Queue Reconstruction (for M68HC12)
8.5.2 Reconstruction Algorithm (for M68HC12)
This subsection describes in detail how to use IPIPE1 and IPIPE0
signals and queue reconstruction registers to reconstruct the queue. An
“is_full” flag is used to indicate when the fetch_add and fetch_dat buffer
registers contain information. The use of the flag is explained more fully
in subsequent paragraphs.
Typically, the first few cycles of raw capture data are not useful because
it takes several cycles before an instruction propagates to the head of
the queue. During these first raw cycles, the only meaningful information
available are data movement signals. Information on the external
address and data buses during this setup time reflects the actions of
instructions that were fetched before data collection started.
In the special case of a reset, there is a 5-cycle sequence (VfPPP)
during which the reset vector is fetched and the instruction queue is
filled, before execution of the first instruction begins. Due to the timing of
the switchover of the IPIPE1 and IPIPE0 pins from their alternate
function as mode select inputs, the status information on these two pins
may be erroneous during the first cycle or two after the release of reset.
This is not a problem because the status is correct in time for queue
reconstruction logic to correctly replicate the queue.
Before starting to reconstruct the queue, clear the is_full flag to indicate
that there is no meaningful information in the fetch_add and fetch_dat
buffers. Further movement of information in the instruction queue is
based on the decoded status on the IPIPE1 and IPIPE0 signals at the
rising edges of E.
8.5.2.1 LAT Decoding
On a latch cycle (LAT), check the is_full flag. If and only if is_full = 0,
transfer the address and data from the previous bus cycle (in_add and
in_dat) into the fetch_add and fetch_dat registers, respectively. Then,
set the is_full flag. The usual reason for a latch request instead of an
advance request is that the previous instruction ended with a single
aligned byte of program information in the last stage of the instruction
queue. Since the odd half of this word still holds the opcode for the next
instruction, the queue cannot advance on this cycle. However, the cycle
to fetch the next word of program information has already started and the
data is on its way.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Queue
337
Instruction Queue
8.5.2.2 ALD Decoding
On an advance-and-load-from-data-bus (ALD) cycle, the information in
the instruction queue must advance by one stage. Whatever was in
stage 2 of the queue is simply thrown away. The previous contents of
stage 1 are moved to stage 2, and the address and data from the
previous cycle (in_add and in_dat) are transferred into stage 1 of the
instruction queue. Finally, clear the is_full flag to indicate the buffer latch
is ready for new data. Usually, there would be no useful information in
the fetch buffer when an ALD cycle was encountered, but in the case of
a change-of-flow, any data that was there needs to be flushed out (by
clearing the is_full flag).
8.5.2.3 ALL Decoding
On an advance-and-load-from-latch (ALL) cycle, the information in the
instruction queue must advance by one stage. Whatever was in stage 2
of the queue is simply thrown away. The previous contents of stage 1 are
moved to stage 2, and the contents of the fetch buffer latch are
transferred into stage 1 of the instruction queue. One or more cycles
preceding the ALL cycle will have been a LAT cycle. After updating the
instruction queue, clear the is_full flag to indicate the fetch buffer is ready
for new information.
Figure 8-4 shows the reset sequence and illustrates the relationship
between instruction cycle codes (VfPPP) and pipe status signals. One
cycle of the data bus is shown to indicate the relationship between the
ALD data movement code and the data value it refers to. The SEV
execution start code indicates that the reset vector pointed to an even
address in this example.
INSTRUCTION
CYCLE CODES
V
f
P
P
P
DM
DM
EX
DM
10
ALD
10
SEV
10
ALD
FIRST USER
INSTRUCTION
E CLOCK
DATA BUS
IPIPE[1:0]
00
00
00
00
00
00
10
ALD
00
Figure 8-4. Reset Sequence for M68HC12
Reference Manual
338
S12CPUV2
Instruction Queue
MOTOROLA
Instruction Queue
Instruction Tagging
8.6 Instruction Tagging
The instruction queue and cycle-by-cycle CPU activity can be
reconstructed in real time or from trace history that was captured by a
logic analyzer. However, the reconstructed queue cannot be used to
stop the CPU at a specific instruction, because execution has already
begun by the time an operation is visible outside the MCU. A separate
instruction tagging mechanism is provided for this purpose.
Executing the BDM TAGGO command configures two MCU pins for
tagging. The TAGLO signal shares a pin with the LSTRB signal, and the
TAGHI signal shares the BKGD pin. Tagging information is latched on
the falling edge of ECLK, as shown in Figure 8-5.
TAGS ARE APPLIED TO PROGRAM INFORMATION
CAPTURED ON THIS E CLOCK TRANSITION
E CLOCK
LSTRB/TAGLO
TAGLO
VALID
LSTRB VALID
TAGHI
VALID
BKGD/TAGHI
Figure 8-5. Tag Input Timing
Table 8-2 shows the functions of the two independent tagging pins. The
presence of logic level 0 on either pin at the fall of ECLK tags (marks)
the associated byte of program information as it is read into the
instruction queue. Tagging is allowed in all modes. Tagging is disabled
when BDM becomes active.
Table 8-2. Tag Pin Function
TAGHI
TAGLO
Tag
1
1
No tag
1
0
Low byte
0
1
High byte
0
0
Both bytes
S12CPUV2
MOTOROLA
Reference Manual
Instruction Queue
339
Instruction Queue
In HCS12 and M68HC12 derivatives that have hardware breakpoint
capability, the breakpoint control logic and BDM control logic use the
same internal signals for instruction tagging. The CPU does not
differentiate between the two kinds of tags.
The tag follows program information as it advances through the queue.
When a tagged instruction reaches the head of the queue, the CPU
enters active background debug mode rather than executing the
instruction.
Reference Manual
340
S12CPUV2
Instruction Queue
MOTOROLA
Reference Manual — S12CPUV2
Section 9. Fuzzy Logic Support
9.1 Introduction
The instruction set of the central processor unit (CPU12) is the first
instruction set to specifically address the needs of fuzzy logic. This
section describes the use of fuzzy logic in control systems, discusses the
CPU12 fuzzy logic instructions, and provides examples of fuzzy logic
programs.
The CPU12 includes four instructions that perform specific fuzzy logic
tasks. In addition, several other instructions are especially useful in fuzzy
logic programs. The overall C-friendliness of the instruction set also aids
development of efficient fuzzy logic programs.
This section explains the basic fuzzy logic algorithm for which the four
fuzzy logic instructions are intended. Each of the fuzzy logic instructions
are then explained in detail. Finally, other custom fuzzy logic algorithms
are discussed, with emphasis on use of other CPU12 instructions.
The four fuzzy logic instructions are:
• MEM (determine grade of membership), which evaluates
trapezoidal membership functions
• REV (fuzzy logic rule evaluation) and REVW (fuzzy logic rule
evaluation weighted), which perform unweighted or weighted
MIN-MAX rule evaluation
• WAV (weighted average), which performs weighted average
defuzzification on singleton output membership functions.
Other instructions that are useful for custom fuzzy logic programs
include:
• MINA (place smaller of two unsigned 8-bit values in
accumulator A)
• EMIND (place smaller of two unsigned 16-bit values in
accumulator D)
• MAXM (place larger of two unsigned 8-bit values in memory)
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
341
Fuzzy Logic Support
•
•
•
•
EMAXM (place larger of two unsigned 16-bit values in memory)
TBL (table lookup and interpolate)
ETBL (extended table lookup and interpolate)
EMACS (extended multiply and accumulate signed 16-bit by
16-bit to 32-bit)
For higher resolution fuzzy programs, the fast extended precision math
instructions in the CPU12 are also beneficial. Flexible indexed
addressing modes help simplify access to fuzzy logic data structures
stored as lists or tabular data structures in memory.
The actual logic additions required to implement fuzzy logic support in
the CPU12 are quite small, so there is no appreciable increase in cost
for the typical user. A fuzzy inference kernel for the CPU12 requires
one-fifth as much code space and executes almost 50 times faster than
a comparable kernel implemented on a typical midrange microcontroller.
By incorporating fuzzy logic support into a high-volume,
general-purpose microcontroller product family, Motorola has made
fuzzy logic available for a huge base of applications.
9.2 Fuzzy Logic Basics
This is an overview of basic fuzzy logic concepts. It can serve as a
general introduction to the subject, but that is not the main purpose.
There are a number of fuzzy logic programming strategies. This
discussion concentrates on the methods implemented in the CPU12
fuzzy logic instructions. The primary goal is to provide a background for
a detailed explanation of the CPU12 fuzzy logic instructions.
In general, fuzzy logic provides for set definitions that have fuzzy
boundaries rather than the crisp boundaries of Aristotelian logic. These
sets can overlap so that, for a specific input value, one or more sets
associated with linguistic labels may be true to a degree at the same
time. As the input varies from the range of one set into the range of an
adjacent set, the first set becomes progressively less true while the
second set becomes progressively more true.
Fuzzy logic has membership functions which emulate human concepts
like “temperature is warm”; that is, conditions are perceived to have
gradual boundaries. This concept seems to be a key element of the
human ability to solve certain types of complex problems that have
eluded traditional control methods.
Reference Manual
342
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
Fuzzy Logic Basics
Fuzzy sets provide a means of using linguistic expressions like
“temperature is warm” in rules which can then be evaluated with a high
degree of numerical precision and repeatability. This directly contradicts
the common misperception that fuzzy logic produces approximate
results — a specific set of input conditions always produces the same
result, just as a conventional control system does.
A microcontroller-based fuzzy logic control system has two parts:
•
A fuzzy inference kernel which is executed periodically to
determine system outputs based on current system inputs
•
A knowledge base which contains membership functions and
rules
Figure 9-1 is a block diagram of this kind of fuzzy logic system.
SYSTEM
INPUTS
KNOWLEDGE
BASE
INPUT
MEMBERSHIP
FUNCTIONS
FUZZY
INFERENCE
KERNEL
FUZZIFICATION
…
RULE LIST
RULE EVALUATION
…
OUTPUT
MEMBERSHIP
FUNCTIONS
FUZZY INPUTS
(IN RAM)
FUZZY OUTPUTS
(IN RAM)
DEFUZZIFICATION
SYSTEM
OUTPUTS
Figure 9-1. Block Diagram of a Fuzzy Logic System
The knowledge base can be developed by an application expert without
any microcontroller programming experience. Membership functions are
simply expressions of the expert’s understanding of the linguistic terms
that describe the system to be controlled. Rules are ordinary language
statements that describe the actions a human expert would take to solve
the application problem.
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
343
Fuzzy Logic Support
Rules and membership functions can be reduced to relatively simple
data structures (the knowledge base) stored in non-volatile memory. A
fuzzy inference kernel can be written by a programmer who does not
know how the application system works. The only thing the programmer
needs to do with knowledge base information is store it in the memory
locations used by the kernel.
One execution pass through the fuzzy inference kernel generates
system output signals in response to current input conditions. The kernel
is executed as often as needed to maintain control. If the kernel is
executed more often than needed, processor bandwidth and power are
wasted; delaying too long between passes can cause the system to get
too far out of control. Choosing a periodic rate for a fuzzy control system
is the same as it would be for a conventional control system.
9.2.1 Fuzzification (MEM)
During the fuzzification step, the current system input values are
compared against stored input membership functions to determine the
degree to which each label of each system input is true. This is
accomplished by finding the y-value for the current input value on a
trapezoidal membership function for each label of each system input.
The MEM instruction in the CPU12 performs this calculation for one label
of one system input. To perform the complete fuzzification task for a
system, several MEM instructions must be executed, usually in a
program loop structure.
Figure 9-2 shows a system of three input membership functions, one for
each label of the system input. The x-axis of all three membership
functions represents the range of possible values of the system input.
The vertical line through all three membership functions represents a
specific system input value. The y-axis represents degree of truth and
varies from completely false ($00 or 0 percent) to completely true ($FF
or 100 percent). The y-value where the vertical line intersects each of the
membership functions, is the degree to which the current input value
matches the associated label for this system input. For example, the
expression “temperature is warm” is 25 percent true ($40). The value
$40 is stored to a random-access memory (RAM) location and is called
a fuzzy input (in this case, the fuzzy input for “temperature is warm”).
There is a RAM location for each fuzzy input (for each label of each
system input).
Reference Manual
344
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
Fuzzy Logic Basics
MEMBERSHIP FUNCTIONS
FOR TEMPERATURE
$FF
FUZZY INPUTS
HOT
$C0
$80
$40
TEMPERATURE IS HOT
$00
TEMPERATURE IS WARM
$40
TEMPERATURE IS COLD
$C0
$00
0°F
$FF
32°F
64°F
96°F
128°F
WARM
$C0
$80
$40
$00
32°F
0°F
64°F
96°F
128°F
$FF
COLD
$C0
$80
$40
$00
0°F
32°F
64°F
96°F
128°F
CURRENT
TEMPERATURE
IS 64°F
Figure 9-2. Fuzzification Using Membership Functions
When the fuzzification step begins, the current value of the system input
is in an accumulator of the CPU12, one index register points to the first
membership function definition in the knowledge base, and a second
index register points to the first fuzzy input in RAM. As each fuzzy input
is calculated by executing a MEM instruction, the result is stored to the
fuzzy input and both pointers are updated automatically to point to the
locations associated with the next fuzzy input. The MEM instruction
takes care of everything except counting the number of labels per
system input and loading the current value of any subsequent system
inputs.
The end result of the fuzzification step is a table of fuzzy inputs
representing current system conditions.
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
345
Fuzzy Logic Support
9.2.2 Rule Evaluation (REV and REVW)
Rule evaluation is the central element of a fuzzy logic inference program.
This step processes a list of rules from the knowledge base using current
fuzzy input values from RAM to produce a list of fuzzy outputs in RAM.
These fuzzy outputs can be thought of as raw suggestions for what the
system output should be in response to the current input conditions.
Before the results can be applied, the fuzzy outputs must be further
processed, or defuzzified, to produce a single output value that
represents the combined effect of all of the fuzzy outputs.
The CPU12 offers two variations of rule evaluation instructions. The
REV instruction provides for unweighted rules (all rules are considered
to be equally important). The REVW instruction is similar but allows each
rule to have a separate weighting factor which is stored in a separate
parallel data structure in the knowledge base. In addition to the weights,
the two rule evaluation instructions also differ in the way rules are
encoded into the knowledge base.
An understanding of the structure and syntax of rules is needed to
understand how a microcontroller performs the rule evaluation task. An
example of a typical rule is:
If temperature is warm and pressure is high, then heat is
(should be) off.
At first glance, it seems that encoding this rule in a compact form
understandable to the microcontroller would be difficult, but it is actually
simple to reduce the rule to a small list of memory pointers. The
antecedent portion of the rule is a statement of input conditions and the
consequent portion of the rule is a statement of output actions.
The antecedent portion of a rule is made up of one or more (in this case
two) antecedents connected by a fuzzy and operator. Each antecedent
expression consists of the name of a system input, followed by is,
followed by a label name. The label must be defined by a membership
function in the knowledge base. Each antecedent expression
corresponds to one of the fuzzy inputs in RAM. Since and is the only
operator allowed to connect antecedent expressions, there is no need to
include these in the encoded rule. The antecedents can be encoded as
a simple list of pointers to (or addresses of) the fuzzy inputs to which they
refer.
Reference Manual
346
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
Fuzzy Logic Basics
The consequent portion of a rule is made up of one or more (in this case
one) consequents. Each consequent expression consists of the name of
a system output, followed by is, followed by a label name. Each
consequent expression corresponds to a specific fuzzy output in RAM.
Consequents for a rule can be encoded as a simple list of pointers to (or
addresses of) the fuzzy outputs to which they refer.
The complete rules are stored in the knowledge base as a list of pointers
or addresses of fuzzy inputs and fuzzy outputs. For the rule evaluation
logic to work, there must be some means of knowing which pointers refer
to fuzzy inputs and which refer to fuzzy outputs. There also must be a
way to know when the last rule in the system has been reached.
•
One method of organization is to have a fixed number of rules with
a specific number of antecedents and consequents.
•
A second method, employed in Motorola Freeware M68HC11
kernels, is to mark the end of the rule list with a reserved value,
and use a bit in the pointers to distinguish antecedents from
consequents.
•
A third method of organization, used in the CPU12, is to mark the
end of the rule list with a reserved value, and separate
antecedents and consequents with another reserved value. This
permits any number of rules, and allows each rule to have any
number of antecedents and consequents, subject to the limits
imposed by availability of system memory.
Each rule is evaluated sequentially, but the rules as a group are treated
as if they were all evaluated simultaneously. Two mathematical
operations take place during rule evaluation. The fuzzy and operator
corresponds to the mathematical minimum operation and the fuzzy or
operation corresponds to the mathematical maximum operation. The
fuzzy and is used to connect antecedents within a rule. The fuzzy or is
implied between successive rules. Before evaluating any rules, all fuzzy
outputs are set to zero (meaning not true at all). As each rule is
evaluated, the smallest (minimum) antecedent is taken to be the overall
truth of the rule. This rule truth value is applied to each consequent of
the rule (by storing this value to the corresponding fuzzy output) unless
the fuzzy output is already larger (maximum). If two rules affect the same
fuzzy output, the rule that is most true governs the value in the fuzzy
output because the rules are connected by an implied fuzzy or.
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
347
Fuzzy Logic Support
In the case of rule weighting, the truth value for a rule is determined as
usual by finding the smallest rule antecedent. Before applying this truth
value to the consequents for the rule, the value is multiplied by a fraction
from zero (rule disabled) to one (rule fully enabled). The resulting
modified truth value is then applied to the fuzzy outputs.
The end result of the rule evaluation step is a table of suggested or “raw”
fuzzy outputs in RAM. These values were obtained by plugging current
conditions (fuzzy input values) into the system rules in the knowledge
base. The raw results cannot be supplied directly to the system outputs
because they may be ambiguous. For instance, one raw output can
indicate that the system output should be medium with a degree of truth
of 50 percent while, at the same time, another indicates that the system
output should be low with a degree of truth of 25 percent. The
defuzzification step resolves these ambiguities.
9.2.3 Defuzzification (WAV)
The final step in the fuzzy logic program combines the raw fuzzy outputs
into a composite system output. Unlike the trapezoidal shapes used for
inputs, the CPU12 typically uses singletons for output membership
functions. As with the inputs, the x-axis represents the range of possible
values for a system output. Singleton membership functions consist of
the x-axis position for a label of the system output. Fuzzy outputs
correspond to the y-axis height of the corresponding output membership
function.
The WAV instruction calculates the numerator and denominator sums
for weighted average of the fuzzy outputs according to the formula:
n
∑ Si Fi
i=1
System Output = ----------------------n
Fi
∑
i=1
Where n is the number of labels of a system output, Si are the singleton
positions from the knowledge base, and Fi are fuzzy outputs from RAM.
For a common fuzzy logic program on the CPU12, n is eight or less
(though this instruction can handle any value to 255) and Si and Fi are
8-bit values. The final divide is performed with a separate EDIV
instruction placed immediately after the WAV instruction.
Reference Manual
348
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
Example Inference Kernel
Before executing WAV, an accumulator must be loaded with the number
of iterations (n), one index register must be pointed at the list of singleton
positions in the knowledge base, and a second index register must be
pointed at the list of fuzzy outputs in RAM. If the system has more than
one system output, the WAV instruction is executed once for each
system output.
9.3 Example Inference Kernel
Figure 9-3 is a complete fuzzy inference kernel written in CPU12
assembly language. Numbers in square brackets are cycle counts for an
HCS12 device. The kernel uses two system inputs with seven labels
each and one system output with seven labels. The program assembles
to 57 bytes. It executes in about 20 µs at an 25-MHz bus rate. The basic
structure can easily be extended to a general-purpose system with a
larger number of inputs and outputs.
*
01 [2]
02 [2]
03 [3]
04 [1]
05 [5]
06 [3]
07 [3]
08 [1]
09 [5]
10 [3]
FUZZIFY
LDX
LDY
LDAA
LDAB
MEM
DBNE
LDAA
LDAB
MEM
DBNE
#INPUT_MFS
#FUZ_INS
CURRENT_INS
#7
11 [1]
12 [2]
RULE_EVAL
13 [3]
14 [2]
15 [2]
16 [1]
17 [3n+4]
LDAB
CLR
DBNE
LDX
LDY
LDAA
REV
#7
1,Y+
b,RULE_EVAL
#RULE_START
#FUZ_INS
#$FF
;Loop count
;Clr a fuzzy out & inc ptr
;Loop to clr all fuzzy outs
;Point at first rule element
;Point at fuzzy ins and outs
;Init A (and clears V-bit)
;Process rule list
18 [2]
DEFUZ
19 [2]
20 [1]
21 [7b+4]
22 [11]
23 [1]
24 [3]
*
***** End
LDY
LDX
LDAB
WAV
EDIV
TFR
STAB
#FUZ_OUT
#SGLTN_POS
#7
;Point at fuzzy outputs
;Point at singleton positions
;7 fuzzy outs per COG output
;Calculate sums for wtd av
;Final divide for wtd av
;Move result to A:B
;Store system output
GRAD_LOOP
GRAD_LOOP1
B,GRAD_LOOP
CURRENT_INS+1
#7
B,GRAD_LOOP1
Y,D
COG_OUT
;Point at MF definitions
;Point at fuzzy input table
;Get first input value
;7 labels per input
;Evaluate one MF
;For 7 labels of 1 input
;Get second input value
;7 labels per input
;Evaluate one MF
;For 7 labels of 1 input
Figure 9-3. Fuzzy Inference Engine
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
349
Fuzzy Logic Support
Lines 1 to 3 set up pointers and load the system input value into the A
accumulator.
Line 4 sets the loop count for the loop in lines 5 and 6.
Lines 5 and 6 make up the fuzzification loop for seven labels of one
system input. The MEM instruction finds the y-value on a trapezoidal
membership function for the current input value, for one label of the
current input, and then stores the result to the corresponding fuzzy input.
Pointers in X and Y are automatically updated by four and one so they
point at the next membership function and fuzzy input respectively.
Line 7 loads the current value of the next system input. Pointers in X and
Y already point to the right places as a result of the automatic update
function of the MEM instruction in line 5.
Line 8 reloads a loop count.
Lines 9 and 10 form a loop to fuzzify the seven labels of the second
system input. When the program drops to line 11, the Y index register is
pointing at the next location after the last fuzzy input, which is the first
fuzzy output in this system.
Line 11 sets the loop count to clear seven fuzzy outputs.
Lines 12 and 13 form a loop to clear all fuzzy outputs before rule
evaluation starts.
Line 14 initializes the X index register to point at the first element in the
rule list for the REV instruction.
Line 15 initializes the Y index register to point at the fuzzy inputs and
outputs in the system. The rule list (for REV) consists of 8-bit offsets from
this base address to particular fuzzy inputs or fuzzy outputs. The special
value $FE is interpreted by REV as a marker between rule antecedents
and consequents.
Line 16 initializes the A accumulator to the highest 8-bit value in
preparation for finding the smallest fuzzy input referenced by a rule
antecedent. The LDAA #$FF instruction also clears the V-bit in the
CPU12’s condition code register so the REV instruction knows it is
processing antecedents. During rule list processing, the V bit is toggled
each time an $FE is detected in the list. The V bit indicates whether REV
is processing antecedents or consequents.
Reference Manual
350
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
MEM Instruction Details
Line 17 is the REV instruction, a self-contained loop to process
successive elements in the rule list until an $FF character is found. For
a system of 17 rules with two antecedents and one consequent each, the
REV instruction takes 259 cycles, but it is interruptible so it does not
cause a long interrupt latency.
Lines 18 through 20 set up pointers and an iteration count for the WAV
instruction.
Line 21 is the beginning of defuzzification. The WAV instruction
calculates a sum-of-products and a sum-of-weights.
Line 22 completes defuzzification. The EDIV instruction performs a
32-bit by 16-bit divide on the intermediate results from WAV to get the
weighted average.
Line 23 moves the EDIV result into the double accumulator.
Line 24 stores the low 8-bits of the defuzzification result.
This example inference program shows how easy it is to incorporate
fuzzy logic into general applications using the CPU12. Code space and
execution time are no longer serious factors in the decision to use fuzzy
logic. The next section begins a much more detailed look at the fuzzy
logic instructions of the CPU12.
9.4 MEM Instruction Details
This section provides a more detailed explanation of the membership
function evaluation instruction (MEM), including details about abnormal
special cases for improperly defined membership functions.
9.4.1 Membership Function Definitions
Figure 9-4 shows how a normal membership function is specified in the
CPU12. Typically, a software tool is used to input membership functions
graphically, and the tool generates data structures for the target
processor and software kernel. Alternatively, points and slopes for the
membership functions can be determined and stored in memory with
define-constant assembler directives.
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
351
Fuzzy Logic Support
GRAPHICAL REPRESENTATION
$FF
$E0
$C0
DEGREE
OF
TRUTH
$A0
$80
slope_2
$60
$40
slope_1
point_1
point_2
$20
$00
$00
$10
$20
$30
$40
$50
$60
$70
$80
$90
$A0
$B0
$C0
$D0
$E0
$F0
$FF
INPUT RANGE
MEMORY REPRESENTATION
ADDR
$40
X-POSITION OF point_1
ADDR+1
$D0
X-POSITION OF point_2
ADDR+2
$08
slope_1 ($FF/(X-POS OF SATURATION – point_1))
ADDR+3
$04
slope_2 ($FF/(point_2 – X-POS OF SATURATION))
Figure 9-4. Defining a Normal Membership Function
An internal CPU algorithm calculates the y-value where the current input
intersects a membership function. This algorithm assumes the
membership function obeys some common-sense rules. If the
membership function definition is improper, the results may be unusual.
See 9.4.2 Abnormal Membership Function Definitions for a
discussion of these cases.
These rules apply to normal membership functions.
•
$00 ≤ point1 < $FF
•
$00 < point2 ≤ $FF
•
point1 < point2
•
The sloping sides of the trapezoid meet at or above $FF.
Each system input such as temperature has several labels such as cold,
cool, normal, warm, and hot. Each label of each system input must have
a membership function to describe its meaning in an unambiguous
numerical way. Typically, there are three to seven labels per system
input, but there is no practical restriction on this number as far as the
fuzzification step is concerned.
Reference Manual
352
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
MEM Instruction Details
9.4.2 Abnormal Membership Function Definitions
In the CPU12, it is possible (and proper) to define “crisp” membership
functions. A crisp membership function has one or both sides vertical
(infinite slope). Since the slope value $00 is not used otherwise, it is
assigned to mean infinite slope to the MEM instruction in the CPU12.
Although a good fuzzy development tool will not allow the user to specify
an improper membership function, it is possible to have program errors
or memory errors which result in erroneous abnormal membership
functions. Although these abnormal shapes do not correspond to any
working systems, understanding how the CPU12 treats these cases can
be helpful for debugging.
A close examination of the MEM instruction algorithm will show how
such membership functions are evaluated. Figure 9-5 is a complete flow
diagram for the execution of a MEM instruction. Each rectangular box
represents one CPU bus cycle. The number in the upper left corner
corresponds to the cycle number and the letter corresponds to the cycle
type (refer to Section 6. Instruction Glossary for details). The upper
portion of the box includes information about bus activity during this
cycle (if any). The lower portion of the box, which is separated by a
dashed line, includes information about internal CPU processes. It is
common for several internal functions to take place during a single CPU
cycle (for example, in cycle 2, two 8-bit subtractions take place and a flag
is set based on the results).
Consider 4a: If (((Slope_2 = 0) or (Grade_2 > $FF)) and (flag_d12n = 0)).
The flag_d12n is zero as long as the input value (in accumulator A) is
within the trapezoid. Everywhere outside the trapezoid, one or the other
delta term will be negative, and the flag will equal one. Slope_2 equals
zero indicates the right side of the trapezoid has infinite slope, so the
resulting grade should be $FF everywhere in the trapezoid, including at
point_2, as far as this side is concerned. The term grade_2 greater than
$FF means the value is far enough into the trapezoid that the right
sloping side of the trapezoid has crossed above the $FF cutoff level and
the resulting grade should be $FF as far as the right sloping side is
concerned. 4a decides if the value is left of the right sloping side
(Grade = $FF), or on the sloping portion of the right side of the trapezoid
(Grade = Grade_2). 4b could still override this tentative value in grade.
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
353
Fuzzy Logic Support
START
1-R
2-R
READ WORD @ 0,X — Point_1 AND Point_2
X=X+4
READ WORD @ –2,X — Slope_1 AND Slope_2
Y=Y+1
2a — Delta_1 = ACCA – Point_1
2b — Delta_2 = Point_2 – ACCA
2c — IF (Delta_1 OR Delta_2) < 0 THEN flag_d12n = 1 ELSE flag_d12n = 0
3-f
NO BUS ACCESS
3a — IF flag_d12n = 1 THEN Grade_1 = 0 ELSE Grade_1 = Slope_1 * Delta_1
3b — IF flag_d12n = 1 THEN Grade_2 = 0 ELSE Grade_2 = Slope_2 * Delta_2
4-O
IF MISALIGNED THEN READ PROGRAM WORD TO FILL INSTRUCTION QUEUE ELSE NO BUS ACCESS
4a — IF (((Slope_2 = 0) OR (Grade_2 > $FF)) AND (flag_d12n = 0)) THEN GRADE = $FF
ELSE GRADE = Grade_2
4b — IF (((Slope_1 = 0) OR (Grade_1 > $FF)) AND (flag_d12n = 0)) THEN GRADE = GRADE
ELSE GRADE = Grade_1
5-w
WRITE BYTE @ –1,Y — FUZZY INPUT RESULT (GRADE)
END
Figure 9-5. MEM Instruction Flow Diagram
In 4b, slope_1 is zero if the left side of the trapezoid has infinite slope
(vertical). If so, the result (grade) should be $FF at and to the right of
point_1 everywhere within the trapezoid as far as the left side is
concerned. The grade_1 greater than $FF term corresponds to the input
being to the right of where the left sloping side passes the $FF cutoff
level. If either of these conditions is true, the result (grade) is left at the
value it got from 4a. The “else” condition in 4b corresponds to the input
falling on the sloping portion of the left side of the trapezoid (or possibly
outside the trapezoid), so the result is grade equal grade_1. If the input
was outside the trapezoid, flag_d12n would be one and grade_1 and
Reference Manual
354
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
MEM Instruction Details
grade_2 would have been forced to $00 in cycle 3. The else condition of
4b would set the result to $00.
The special cases shown here represent abnormal membership function
definitions. The explanations describe how the specific algorithm in the
CPU12 resolves these unusual cases. The results are not all intuitively
obvious, but rather fall out from the specific algorithm. Remember, these
cases should not occur in a normal system.
9.4.2.1 Abnormal Membership Function Case 1
This membership function is abnormal because the sloping sides cross
below the $FF cutoff level. The flag_d12n signal forces the membership
function to evaluate to $00 everywhere except from point_1 to point_2.
Within this interval, the tentative values for grade_1 and grade_2
calculated in cycle 3 fall on the crossed sloping sides. In step 4a, grade
gets set to the grade_2 value, but in 4b this is overridden by the grade_1
value, which ends up as the result of the MEM instruction. One way to
say this is that the result follows the left sloping side until the input
passes point_2, where the result goes to $00.
MEMORY DEFINITION: $60, $80, $04, $04; point_1, point_2, slope_1, slope_2
GRAPHICAL REPRESENTATION
P1
P2
HOW INTERPRETED
P1
P2
Figure 9-6. Abnormal Membership Function Case 1
If point_1 was to the right of point_2, flag_d12n would force the result to
be $00 for all input values. In fact, flag_d12n always limits the region of
interest to the space greater than or equal to point_1 and less than or
equal to point_2.
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
355
Fuzzy Logic Support
9.4.2.2 Abnormal Membership Function Case 2
Like the previous example, the membership function in case 2 is
abnormal because the sloping sides cross below the $FF cutoff level, but
the left sloping side reaches the $FF cutoff level before the input gets to
point_2. In this case, the result follows the left sloping side until it
reaches the $FF cutoff level. At this point, the (grade_1 > $FF) term of
4b kicks in, making the expression true so grade equals grade (no
overwrite). The result from here to point_2 becomes controlled by the
“else” part of 4a (grade = grade_2), and the result follows the right
sloping side.
MEMORY DEFINITION: $60, $C0, $04, $04; point_1, point_2, slope_1, slope_2
GRAPHICAL REPRESENTATION
P1
P2
HOW INTERPRETED
P1
LEFT SIDE P2
CROSSES $FF
Figure 9-7. Abnormal Membership Function Case 2
9.4.2.3 Abnormal Membership Function Case 3
The membership function in case 3 is abnormal because the sloping
sides cross below the $FF cutoff level, and the left sloping side has
infinite slope. In this case, 4a is not true, so grade equals grade_2. 4b is
true because slope_1 is zero, so 4b does not overwrite grade.
MEMORY DEFINITION: $60, $80, $00, $04; point_1, point_2, slope_1, slope_2
GRAPHICAL REPRESENTATION
P1
P2
HOW INTERPRETED
P1
P2
Figure 9-8. Abnormal Membership Function Case 3
Reference Manual
356
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
REV and REVW Instruction Details
9.5 REV and REVW Instruction Details
This section provides a more detailed explanation of the rule evaluation
instructions (REV and REVW). The data structures used to specify rules
are somewhat different for the weighted versus unweighted versions of
the instruction. One uses 8-bit offsets in the encoded rules, while the
other uses full 16-bit addresses. This affects the size of the rule data
structure and execution time.
9.5.1 Unweighted Rule Evaluation (REV)
This instruction implements basic min-max rule evaluation. CPU
registers are used for pointers and intermediate calculation results.
Since the REV instruction is essentially a list-processing instruction,
execution time is dependent on the number of elements in the rule list.
The REV instruction is interruptible (typically within three bus cycles), so
it does not adversely affect worst case interrupt latency. Since all
intermediate results and instruction status are held in stacked CPU
registers, the interrupt service code can even include independent REV
and REVW instructions.
9.5.1.1 Set Up Prior to Executing REV
Some CPU registers and memory locations need to be set up prior to
executing the REV instruction. X and Y index registers are used as index
pointers to the rule list and the fuzzy inputs and outputs. The A
accumulator is used for intermediate calculation results and needs to be
set to $FF initially. The V condition code bit is used as an instruction
status indicator to show whether antecedents or consequents are being
processed. Initially, the V bit is cleared to zero to indicate antecedents
are being processed. The fuzzy outputs (working RAM locations) need
to be cleared to $00. If these values are not initialized before executing
the REV instruction, results will be erroneous.
The X index register is set to the address of the first element in the rule
list (in the knowledge base). The REV instruction automatically updates
this pointer so that the instruction can resume correctly if it is interrupted.
After the REV instruction finishes, X will point at the next address past
the $FF separator character that marks the end of the rule list.
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
357
Fuzzy Logic Support
The Y index register is set to the base address for the fuzzy inputs and
outputs (in working RAM). Each rule antecedent is an unsigned 8-bit
offset from this base address to the referenced fuzzy input. Each rule
consequent is an unsigned 8-bit offset from this base address to the
referenced fuzzy output. The Y index register remains constant
throughout execution of the REV instruction.
The 8-bit A accumulator is used to hold intermediate calculation results
during execution of the REV instruction. During antecedent processing,
A starts out at $FF and is replaced by any smaller fuzzy input that is
referenced by a rule antecedent (MIN). During consequent processing,
A holds the truth value for the rule. This truth value is stored to any fuzzy
output that is referenced by a rule consequent, unless that fuzzy output
is already larger (MAX).
Before starting to execute REV, A must be set to $FF (the largest 8-bit
value) because rule evaluation always starts with processing of the
antecedents of the first rule. For subsequent rules in the list, A is
automatically set to $FF when the instruction detects the $FE marker
character between the last consequent of the previous rule and the first
antecedent of a new rule.
The instruction LDAA #$FF clears the V bit at the same time it initializes
A to $FF. This satisfies the REV setup requirement to clear the V bit as
well as the requirement to initialize A to $FF. Once the REV instruction
starts, the value in the V bit is automatically maintained as $FE separator
characters are detected.
The final requirement to clear all fuzzy outputs to $00 is part of the MAX
algorithm. Each time a rule consequent references a fuzzy output, that
fuzzy output is compared to the truth value for the current rule. If the
current truth value is larger, it is written over the previous value in the
fuzzy output. After all rules have been evaluated, the fuzzy output
contains the truth value for the most-true rule that referenced that fuzzy
output.
After REV finishes, A will hold the truth value for the last rule in the rule
list. The V condition code bit should be one because the last element
before the $FF end marker should have been a rule consequent. If V is
zero after executing REV, it indicates the rule list was structured
incorrectly.
Reference Manual
358
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
REV and REVW Instruction Details
9.5.1.2 Interrupt Details
The REV instruction includes a 3-cycle processing loop for each byte in
the rule list (including antecedents, consequents, and special separator
characters). Within this loop, a check is performed to see if any qualified
interrupt request is pending. If an interrupt is detected, the current CPU
registers are stacked and the interrupt is honored. When the interrupt
service routine finishes, an RTI instruction causes the CPU to recover its
previous context from the stack, and the REV instruction is resumed as
if it had not been interrupted.
The stacked value of the program counter (PC), in case of an interrupted
REV instruction, points to the REV instruction rather than the instruction
that follows. This causes the CPU to try to execute a new REV
instruction upon return from the interrupt. Since the CPU registers
(including the V bit in the condition codes register) indicate the current
status of the interrupted REV instruction, this effectively causes the rule
evaluation operation to resume from where it left off.
9.5.1.3 Cycle-by-Cycle Details for REV
The central element of the REV instruction is a 3-cycle loop that is
executed once for each byte in the rule list. There is a small amount of
housekeeping activity to get this loop started as REV begins and a small
sequence to end the instruction. If an interrupt comes, there is a special
small sequence to save CPU status on the stack before honoring the
requested interrupt.
Figure 9-9 is a REV instruction flow diagram. Each rectangular box
represents one CPU clock cycle. Decision blocks and connecting arrows
are considered to take no time at all. The letters in the small rectangles
in the upper left corner of each bold box correspond to execution cycle
codes (refer to Section 6. Instruction Glossary for details). Lower case
letters indicate a cycle where 8-bit or no data is transferred. Upper case
letters indicate cycles where 16-bit or no data is transferred.
When a value is read from memory, it cannot be used by the CPU until
the second cycle after the read takes place. This is due to access and
propagation delays.
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
359
Fuzzy Logic Support
START
1.0 - O
2.0 - r
READ PROGRAM WORD IF $18 MISALIGNED
READ BYTE @ 0,X (RULE ELEMENT Rx)
X = X + 1 POINT AT NEXT RULE ELEMENT
3.0 - f
NO BUS ACCESS
4.0 - t
UPDATE RX WITH VALUE READ IN CYC 2 OR 5
IF Rx $FE OR $FF
THEN READ BYTE @ Rx,Y (FUZZY IN OR OUT Fy)
ELSE NO BUS ACCESS
IF Rx = $FE & V WAS 1, RESET ACCA TO $FF
IF Rx = $FE TOGGLE V-BIT
YES
INTERRUPT PENDING?
NO
5.0 - t
$FF
Rx = $FF, OTHER?
5.2 - f
NO BUS ACCESS
ADJUST PC TO POINT AT CURRENT REV INSTRUCTION
OTHER
READ BYTE @ 0,X (RULE ELEMENT Rx)
X = X + 1 POINT AT NEXT RULE ELEMENT
6.2 - f
NO BUS ACCESS
ADJUST X = X – 1
CONTINUE TO INTERRUPT STACKING
1 (MAX)
V-BIT
0 (MIN)
6.0 - x
NO BUS ACCESS
UPDATE Fy WITH VALUE READ IN CYC 4.0
6.1 - x
IF Rx $FE THEN A = MIN(A, Fy)
ELSE A = A (NO CHANGE TO A)
NO
UPDATE FY WITH VALUE READ IN CYC 4.0
IF Rx $FE OR $FF, AND ACCA > Fy
THEN WRITE BYTE @ Rx,Y
ELSE NO BUS ACCESS
Rx = $FF (END OF RULES)?
YES
7.0 - O
READ PROGRAM WORD IF $3A MISALIGNED
END
Figure 9-9. REV Instruction Flow Diagram
Reference Manual
360
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
REV and REVW Instruction Details
Since there is more than one flow path through the REV instruction,
cycle numbers have a decimal place. This decimal place indicates which
of several possible paths is being used. The CPU normally moves
forward by one digit at a time within the same flow (flow number is
indicated after the decimal point in the cycle number). There are two
exceptions possible to this orderly sequence through an instruction. The
first is a branch back to an earlier cycle number to form a loop as in
6.0 to 4.0. The second type of sequence change is from one flow to a
parallel flow within the same instruction such as 4.0 to 5.2, which occurs
if the REV instruction senses an interrupt. In this second type of
sequence branch, the whole number advances by one and the flow
number changes to a new value (the digit after the decimal point).
In cycle 1.0, the CPU12 does an optional program word access to
replace the $18 prebyte of the REV instruction. Notice that cycle 7.0 is
also an O type cycle. One or the other of these will be a program word
fetch, while the other will be a free cycle where the CPU does not access
the bus. Although the $18 page prebyte is a required part of the REV
instruction, it is treated by the CPU12 as a somewhat separate single
cycle instruction.
Rule evaluation begins at cycle 2.0 with a byte read of the first element
in the rule list. Usually this would be the first antecedent of the first rule,
but the REV instruction can be interrupted, so this could be a read of any
byte in the rule list. The X index register is incremented so it points to the
next element in the rule list. Cycle 3.0 is needed to satisfy the required
delay between a read and when data is valid to the CPU. Some internal
CPU housekeeping activity takes place during this cycle, but there is no
bus activity. By cycle 4.0, the rule element that was read in cycle 2.0 is
available to the CPU.
Cycle 4.0 is the first cycle of the main three cycle rule evaluation loop.
Depending upon whether rule antecedents or consequents are being
processed, the loop will consist of cycles 4.0, 5.0, 6.0, or the sequence
4.0, 5.0, 6.1. This loop is executed once for every byte in the rule list,
including the $FE separators and the $FF end-of-rules marker.
At each cycle 4.0, a fuzzy input or fuzzy output is read, except during the
loop passes associated with the $FE and $FF marker bytes, where no
bus access takes place during cycle 4.0. The read access uses the Y
index register as the base address and the previously read rule byte (Rx)
as an unsigned offset from Y. The fuzzy input or output value read here
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
361
Fuzzy Logic Support
will be used during the next cycle 6.0 or 6.1. Besides being used as the
offset from Y for this read, the previously read Rx is checked to see if it
is a separator character ($FE). If Rx was $FE and the V bit was one, this
indicates a switch from processing consequents of one rule to starting to
process antecedents of the next rule. At this transition, the A
accumulator is initialized to $FF to prepare for the min operation to find
the smallest fuzzy input. Also, if Rx is $FE, the V bit is toggled to indicate
the change from antecedents to consequents, or consequents to
antecedents.
During cycle 5.0, a new rule byte is read unless this is the last loop pass,
and Rx is $FF (marking the end of the rule list). This new rule byte will
not be used until cycle 4.0 of the next pass through the loop.
Between cycle 5.0 and 6.x, the V-bit is used to decide which of two paths
to take. If V is zero, antecedents are being processed and the CPU
progresses to cycle 6.0. If V is one, consequents are being processed
and the CPU goes to cycle 6.1.
During cycle 6.0, the current value in the A accumulator is compared to
the fuzzy input that was read in the previous cycle 4.0, and the lower
value is placed in the A accumulator (min operation). If Rx is $FE, this is
the transition between rule antecedents and rule consequents, and this
min operation is skipped (although the cycle is still used). No bus access
takes place during cycle 6.0 but cycle 6.x is considered an x type cycle
because it could be a byte write (cycle 6.1) or a free cycle (cycle 6.0 or
6.1 with Rx = $FE or $FF).
If an interrupt arrives while the REV instruction is executing, REV can
break between cycles 4.0 and 5.0 in an orderly fashion so that the rule
evaluation operation can resume after the interrupt has been serviced.
Cycles 5.2 and 6.2 are needed to adjust the PC and X index register so
the REV operation can recover after the interrupt. PC is adjusted
backward in cycle 5.2 so it points to the currently running REV
instruction. After the interrupt, rule evaluation will resume, but the values
that were stored on the stack for index registers, accumulator A, and
CCR will cause the operation to pick up where it left off. In cycle 6.2, the
X index register is adjusted backward by one because the last rule byte
needs to be re-fetched when the REV instruction resumes.
After cycle 6.2, the REV instruction is finished, and execution would
continue to the normal interrupt processing flow.
Reference Manual
362
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
REV and REVW Instruction Details
9.5.2 Weighted Rule Evaluation (REVW)
This instruction implements a weighted variation of min-max rule
evaluation. The weighting factors are stored in a table with one 8-bit
entry per rule. The weight is used to multiply the truth value of the rule
(minimum of all antecedents) by a value from zero to one to get the
weighted result. This weighted result is then applied to the consequents,
just as it would be for unweighted rule evaluation.
Since the REVW instruction is essentially a list-processing instruction,
execution time is dependent on the number of rules and the number of
elements in the rule list. The REVW instruction is interruptible (typically
within three to five bus cycles), so it does not adversely affect worst case
interrupt latency. Since all intermediate results and instruction status are
held in stacked CPU registers, the interrupt service code can even
include independent REV and REVW instructions.
The rule structure is different for REVW than for REV. For REVW, the
rule list is made up of 16-bit elements rather than 8-bit elements. Each
antecedent is represented by the full 16-bit address of the corresponding
fuzzy input. Each rule consequent is represented by the full address of
the corresponding fuzzy output.
The markers separating antecedents from consequents are the
reserved 16-bit value $FFFE, and the end of the last rule is marked by
the reserved 16-bit value $FFFF. Since $FFFE and $FFFF correspond
to the addresses of the reset vector, there would never be a fuzzy input
or output at either of these locations.
9.5.2.1 Set Up Prior to Executing REVW
Some CPU registers and memory locations need to be set up prior to
executing the REVW instruction. X and Y index registers are used as
index pointers to the rule list and the list of rule weights. The A
accumulator is used for intermediate calculation results and needs to be
set to $FF initially. The V condition code bit is used as an instruction
status indicator that shows whether antecedents or consequents are
being processed. Initially the V bit is cleared to zero to indicate
antecedents are being processed. The C condition code bit is used to
indicate whether rule weights are to be used (1) or not (0). The fuzzy
outputs (working RAM locations) need to be cleared to $00. If these
values are not initialized before executing the REVW instruction, results
will be erroneous.
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
363
Fuzzy Logic Support
The X index register is set to the address of the first element in the rule
list (in the knowledge base). The REVW instruction automatically
updates this pointer so that the instruction can resume correctly if it is
interrupted. After the REVW instruction finishes, X will point at the next
address past the $FFFF separator word that marks the end of the rule
list.
The Y index register is set to the starting address of the list of rule
weights. Each rule weight is an 8-bit value. The weighted result is the
truncated upper eight bits of the 16-bit result, which is derived by
multiplying the minimum rule antecedent value ($00–$FF) by the weight
plus one ($001–$100). This method of weighting rules allows an 8-bit
weighting factor to represent a value between zero and one inclusive.
The 8-bit A accumulator is used to hold intermediate calculation results
during execution of the REVW instruction. During antecedent
processing, A starts out at $FF and is replaced by any smaller fuzzy
input that is referenced by a rule antecedent. If rule weights are enabled
by the C condition code bit equal one, the rule truth value is multiplied by
the rule weight just before consequent processing starts. During
consequent processing, A holds the truth value (possibly weighted) for
the rule. This truth value is stored to any fuzzy output that is referenced
by a rule consequent, unless that fuzzy output is already larger (MAX).
Before starting to execute REVW, A must be set to $FF (the largest 8-bit
value) because rule evaluation always starts with processing of the
antecedents of the first rule. For subsequent rules in the list, A is
automatically set to $FF when the instruction detects the $FFFE marker
word between the last consequent of the previous rule, and the first
antecedent of a new rule.
Both the C and V condition code bits must be set up prior to starting a
REVW instruction. Once the REVW instruction starts, the C bit remains
constant and the value in the V bit is automatically maintained as $FFFE
separator words are detected.
The final requirement to clear all fuzzy outputs to $00 is part of the MAX
algorithm. Each time a rule consequent references a fuzzy output, that
fuzzy output is compared to the truth value (weighted) for the current
rule. If the current truth value is larger, it is written over the previous
value in the fuzzy output. After all rules have been evaluated, the fuzzy
output contains the truth value for the most-true rule that referenced that
fuzzy output.
Reference Manual
364
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
REV and REVW Instruction Details
After REVW finishes, A will hold the truth value (weighted) for the last
rule in the rule list. The V condition code bit should be one because the
last element before the $FFFF end marker should have been a rule
consequent. If V is zero after executing REVW, it indicates the rule list
was structured incorrectly.
9.5.2.2 Interrupt Details
The REVW instruction includes a 3-cycle processing loop for each word
in the rule list (this loop expands to five cycles between antecedents and
consequents to allow time for the multiplication with the rule weight).
Within this loop, a check is performed to see if any qualified interrupt
request is pending. If an interrupt is detected, the current CPU registers
are stacked and the interrupt is honored. When the interrupt service
routine finishes, an RTI instruction causes the CPU to recover its
previous context from the stack, and the REVW instruction is resumed
as if it had not been interrupted.
The stacked value of the program counter (PC), in case of an interrupted
REVW instruction, points to the REVW instruction rather than the
instruction that follows. This causes the CPU to try to execute a new
REVW instruction upon return from the interrupt. Since the CPU
registers (including the C bit and V bit in the condition codes register)
indicate the current status of the interrupted REVW instruction, this
effectively causes the rule evaluation operation to resume from where it
left off.
9.5.2.3 Cycle-by-Cycle Details for REVW
The central element of the REVW instruction is a 3-cycle loop that is
executed once for each word in the rule list. For the special case pass
(where the $FFFE separator word is read between the rule antecedents
and the rule consequents, and weights are enabled by the C bit equal
one), this loop takes five cycles. There is a small amount of
housekeeping activity to get this loop started as REVW begins and a
small sequence to end the instruction. If an interrupt comes, there is a
special small sequence to save CPU status on the stack before the
interrupt is serviced.
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
365
Fuzzy Logic Support
Figure 9-10 is a detailed flow diagram for the REVW instruction. Each
rectangular box represents one CPU clock cycle. Decision blocks and
connecting arrows are considered to take no time at all. The letters in the
small rectangles in the upper left corner of each bold box correspond to
the execution cycle codes (refer to Section 6. Instruction Glossary for
details). Lower case letters indicate a cycle where 8-bit or no data is
transferred. Upper case letters indicate cycles where 16-bit data could
be transferred.
In cycle 2.0, the first element of the rule list (a 16-bit address) is read
from memory. Due to propagation delays, this value cannot be used for
calculations until two cycles later (cycle 4.0). The X index register, which
is used to access information from the rule list, is incremented by two to
point at the next element of the rule list.
The operations performed in cycle 4.0 depend on the value of the word
read from the rule list. $FFFE is a special token that indicates a transition
from antecedents to consequents or from consequents to antecedents
of a new rule. The V bit can be used to decide which transition is taking
place, and V is toggled each time the $FFFE token is detected. If V was
zero, a change from antecedents to consequents is taking place, and it
is time to apply weighting (provided it is enabled by the C bit equal one).
The address in TMP2 (derived from Y) is used to read the weight byte
from memory. In this case, there is no bus access in cycle 5.0, but the
index into the rule list is updated to point to the next rule element.
The old value of X (X0) is temporarily held on internal nodes, so it can be
used to access a rule word in cycle 7.2. The read of the rule word is
timed to start two cycles before it will be used in cycle 4.0 of the next loop
pass. The actual multiply takes place in cycles 6.2 through 8.2. The 8-bit
weight from memory is incremented (possibly overflowing to $100)
before the multiply, and the upper eight bits of the 16-bit internal result
is used as the weighted result. By using weight+1, the result can range
from 0.0 times A to 1.0 times A. After 8.2, flow continues to the next loop
pass at cycle 4.0.
Reference Manual
366
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
REV and REVW Instruction Details
START
1.0 - O
READ PROGRAM WORD IF $18 MISALIGNED
2.0 - R
READ WORD @ 0,X (RULE ELEMENT Rx)
X = X + 2 POINT AT NEXT RULE ELEMENT
3.0 - f
NO BUS ACCESS
TMP2 = Y – 1 (WEIGHT POINTER KEPT IN TMP2)
UPDATE Rx WITH VALUE READ IN CYC 2 OR 5
4.0 - t
IF Rx = $FFFF
THEN NO BUS ACCESS
IF Rx = $FFFE
IF V = 0, THEN TMP2 = TMP2 + 1
IF V = 0 AND C = 1,
THEN READ RULE WEIGHT @,TMP2
ELSE NO BUS ACCESS
IF Rx = OTHER
THEN READ BYTE @,Rx FUZZY IN/OUT FRx
TOGGLE V BIT; IF V NOW 0, A = $FF
NO
5.0 - T
IF Rx $FFFF
THEN READ RULE WORD @,X0
5.3 - f
6.3 - f
MIN
OR DEFAULT
MIN/MAX/MUL?
NO BUS ACCESS
ADJUST PC TO POINT AT CURRENT REVW INSTRUCTION
X0 = X, X = X0 + 2
MUL
V=C=1 and Rx=$FFFE
MAX
V = 1 & RX $FFFE or $FFFF
6.1 - x
YES
INTERRUPT PENDING?
IF A > FRx WRITE A TO Rx
ELSE NO BUS ACCESS
NO BUS ACCESS
ADJUST X = X – 2 POINTER TO RULE LIST
7.3 - f
NO BUS ACCESS
IF (Rx = $FFFE OR $FFFE) AND V = 0
THEN TMP2 = TMP2 – 1
8.3 - f
NO BUS ACCESS
Y = TMP2 + 1
6.0 - x
NO BUS ACCESS
CONTINUE TO INTERRUPT STACKING
A = MIN(A, FRx)
6.2 - f
NO
BEGIN MULTIPLY OF (wt + 1) * A fi A : B
Rx = $FFFF (END OF RULES)?
YES
7.0 - O
7.2 - R
READ PROGRAM WORD IF $3B MISALIGNED
ADJUST PC TO POINT AT NEXT INSTRUCTION
IF C = 1 (WEIGHTS ENABLED), Y = TMP2 + 1
NO BUS ACCESS
READ RULE WORD @,X0
CONTINUE MULTIPLY
8.2 - f
NO BUS ACCESS
FINISH MULTIPLY
END
Figure 9-10. REVW Instruction Flow Diagram
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
367
Fuzzy Logic Support
At cycle 4.0, if Rx is $FFFE and V was one, a change from consequents
to antecedents of a new rule is taking place, so accumulator A must be
reinitialized to $FF. During processing of rule antecedents, A is updated
with the smaller of A, or the current fuzzy input (cycle 6.0). Cycle 5.0 is
usually used to read the next rule word and update the pointer in X. This
read is skipped if the current Rx is $FFFF (end of rules mark). If this is a
weight multiply pass, the read is delayed until cycle 7.2. During
processing of consequents, cycle 6.1 is used to optionally update a fuzzy
output if the value in accumulator A is larger.
After all rules have been processed, cycle 7.0 is used to update the PC
to point at the next instruction. If weights were enabled, Y is updated to
point at the location that immediately follows the last rule weight.
9.6 WAV Instruction Details
The WAV instruction performs weighted average calculations used in
defuzzification. The pseudo-instruction wavr is used to resume an
interrupted weighted average operation. WAV calculates the numerator
and denominator sums using:
n
∑ Si Fi
i=1
System Output = ----------------------n
Fi
∑
i=1
Where n is the number of labels of a system output, Si are the singleton
positions from the knowledge base, and Fi are fuzzy outputs from RAM.
Si and Fi are 8-bit values. The 8-bit B accumulator holds the iteration
count n. Internal temporary registers hold intermediate sums, 24 bits for
the numerator and 16 bits for the denominator. This makes this
instruction suitable for n values up to 255 although eight is a more typical
value. The final long division is performed with a separate EDIV
instruction immediately after the WAV instruction. The WAV instruction
returns the numerator and denominator sums in the correct registers for
the EDIV. (EDIV performs the unsigned division Y = Y : D / X; remainder
in D.)
Reference Manual
368
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
WAV Instruction Details
Execution time for this instruction depends on the number of iterations
(labels for the system output). WAV is interruptible so that worst case
interrupt latency is not affected by the execution time for the complete
weighted average operation. WAV includes initialization for the 24-bit
and 16-bit partial sums so the first entry into WAV looks different than a
resume from interrupt operation. The CPU12 handles this difficulty with
a pseudo-instruction (wavr), which is specifically intended to resume an
interrupted weighted average calculation. Refer to 9.6.3
Cycle-by-Cycle Details for WAV and wavr for more detail.
9.6.1 Set Up Prior to Executing WAV
Before executing the WAV instruction, index registers X and Y and
accumulator B must be set up. Index register X is a pointer to the Si
singleton list. X must have the address of the first singleton value in the
knowledge base. Index register Y is a pointer to the fuzzy outputs Fi. Y
must have the address of the first fuzzy output for this system output. B
is the iteration count n. The B accumulator must be set to the number of
labels for this system output.
9.6.2 WAV Interrupt Details
The WAV instruction includes a 7-cycle processing loop for each label of
the system output (8 cycles in M68HC12). Within this loop, the CPU
checks whether a qualified interrupt request is pending. If an interrupt is
detected, the current values of the internal temporary registers for the
24-bit and 16-bit sums are stacked, the CPU registers are stacked, and
the interrupt is serviced.
A special processing sequence is executed when an interrupt is
detected during a weighted average calculation. This exit sequence
adjusts the PC so that it points to the second byte of the WAV object
code ($3C), before the PC is stacked. Upon return from the interrupt, the
$3C value is interpreted as a wavr pseudo-instruction. The wavr
pseudo-instruction causes the CPU to execute a special WAV
resumption sequence. The wavr recovery sequence adjusts the PC so
that it looks like it did during execution of the original WAV instruction,
then jumps back into the WAV processing loop. If another interrupt
occurs before the weighted average calculation finishes, the PC is
adjusted again as it was for the first interrupt. WAV can be interrupted
any number of times, and additional WAV instructions can be executed
while a WAV instruction is interrupted.
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
369
Fuzzy Logic Support
9.6.3 Cycle-by-Cycle Details for WAV and wavr
The WAV instruction is unusual in that the logic flow has two separate
entry points. The first entry point is the normal start of a WAV instruction.
The second entry point is used to resume the weighted average
operation after a WAV instruction has been interrupted. This recovery
operation is called the wavr pseudo-instruction.
Figure 9-12 is a flow diagram of the WAV instruction in the HCS12,
including the wavr pseudo-instruction. Figure 9-12 is a flow diagram of
the WAV instruction in the M68HC12, including the wavr
pseudo-instruction. Each rectangular box in these figures represents
one CPU clock cycle. Decision blocks and connecting arrows are
considered to take no time at all. The letters in the small rectangles in
the upper left corner of the boxes correspond to execution cycle codes
(refer to Section 6. Instruction Glossary for details). Lower case letters
indicate a cycle where 8-bit or no data is transferred. Upper case letters
indicate cycles where 16-bit data could be transferred.
The cycle-by-cycle description provided here refers to the HCS12 flow in
Figure 9-11. In terms of cycle-by-cycle bus activity, the $18 page select
prebyte is treated as a special 1-byte instruction. In cycle 1.0 of the WAV
instruction, one word of program information will be fetched into the
instruction queue if the $18 is located at an odd address. If the $18 is at
an even address, the instruction queue cannot advance so there is no
bus access in this cycle.
In cycle 2.0, three internal 16-bit temporary registers are cleared in
preparation for summation operations, but there is no bus access. The
WAV instruction maintains a 32-bit sum-of-products in TMP1 : TMP2
and a 16-bit sum-of-weights in TMP3. By keeping these sums inside the
CPU, bus accesses are reduced and the WAV operation is optimized for
high speed.
Cycles 3.0 through 9.0 form the 7-cycle main loop for WAV. The value in
the 8-bit B accumulator is used to count the number of loop iterations. B
is decremented at the top of the loop in cycle 3.0, and the test for zero is
located at the bottom of the loop after cycle 9.0. Cycle 4.0 and 5.0 are
used to fetch the 8-bit operands for one iteration of the loop. X and Y
index registers are used to access these operands. The index registers
are incremented as the operands are fetched. Cycle 6.0 is used to
accumulate the current fuzzy output into TMP3. Cycles 7.0 through 9.0
are used to perform the eight by eight multiply of Fi times Si, and
Reference Manual
370
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
WAV Instruction Details
accumulate this result into TMP1 : TMP2. Even though the
sum-of-products will not exceed 24 bits, the sum is maintained in the
32-bit combined TMP1 : TMP2 register because it is easier to use
existing 16-bit operations than it would be to create a new smaller
operation to handle the high order bits of this sum.
Since the weighted average operation could be quite long, it is made to
be interruptible. The usual longest latency path is from very early in cycle
6.0, through cycle 9.0, to the top of the loop to cycle 3.0, through cycle
5.0 to the interrupt check.
If the WAV instruction is interrupted, the internal temporary registers
TMP3, TMP2, and TMP1 need to be stored on the stack so the operation
can be resumed. Since the WAV instruction included initialization in
cycle 2.0, the recovery path after an interrupt needs to be different. The
wavr pseudo-instruction has the same opcode as WAV, but it is on the
first page of the opcode map so there is no page prebyte ($18) like there
is for WAV. When WAV is interrupted, the PC is adjusted to point at the
second byte of the WAV object code, so that it will be interpreted as the
wavr pseudo-instruction on return from the interrupt, rather than the
WAV instruction. During the recovery sequence, the PC is readjusted in
case another interrupt comes before the weighted average operation
finishes.
The resume sequence includes recovery of the temporary registers from
the stack (1.1 through 3.1), and reads to get the operands for the current
iteration. The normal WAV flow is then rejoined at cycle 6.0.
Upon normal completion of the instruction (cycle 10.0), the PC is
adjusted so it points to the next instruction. The results are transferred
from the TMP registers into CPU registers in such a way that the EDIV
instruction can be used to divide the sum-of-products by the
sum-of-weights. TMP1 : TMP2 is transferred into Y : D and TMP3 is
transferred into X.
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
371
Fuzzy Logic Support
wavr
WAV
1.0 - O
READ PROGRAM WORD IF $18 MISALIGNED
2.0 - f
NO BUS ACCESS
READ WORD @ 0,SP (UNSTACK TMP1)
SP = SP + 2
TMP1 = TMP2 = TMP3 = $0000
3.0 - f
1.1 - U
2.1 - U
READ WORD @ 0,SP (UNSTACK TMP2)
SP = SP + 2
NO BUS ACCESS
B = B – 1 DECREMENT ITERATION COUNTER
3.1 - U
READ WORD @ 0,SP (UNSTACK TMP3)
SP = SP + 2
4.0 - f
READ BYTE @ 0,Y (FUZZY OUTPUT Fi)
4.1 - r
READ BYTE @ –1,Y (FUZZY OUTPUT Fi)
5.1 - r
READ BYTE @ –1,X (SINGLETON Si)
6.1 - S
WRITE WORD @ –2,SP (STACK TMP3)
Y = Y + 1 point at next fuzzy output
5.0 - r
READ BYTE @ 0,X (SINGLETON Si)
X = X + 1 POINT AT NEXT SINGLETON
YES
INTERRUPT PENDING?
NO
6.0 - f
NO BUS ACCESS
TMP3 = TMP3 + Fi
SP = SP – 2
7.0 - f
7.1 - S
NO BUS ACCESS
START MULTIPLY, PPROD = Si*Fi
8.0 - f
SP = SP – 2
8.1 - S
NO BUS ACCESS
FINISH MULTIPLY, TMP2 = TMP2 + PPROD
9.0 - f
WRITE WORD @ –2,SP (STACK TMP2)
WRITE WORD @ –2,SP (STACK TMP1)
SP = SP – 2
ADJUST PC TO POINT AT $3C wavr PSEUDO-OPCODE
NO BUS ACCESS
TMP1 = TMP1 + (CARRY FROM PPROD ADD)
CONTINUE TO INTERRUPT STACKING
NO
B = 0?
YES
10.0 - O
READ PROGRAM WORD IF $3C MISALIGNED
ADJUST PC TO POINT AT NEXT INSTRUCTION
Y : D = TMP1 : TMP2; X = TMP3
END
Figure 9-11. WAV and wavr Instruction Flow Diagram (for HCS12)
Reference Manual
372
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
WAV Instruction Details
WAV
wavr
1.0 - O
READ PROGRAM WORD IF $18 MISALIGNED
2.0 - f
NO BUS ACCESS
3.0 - f
2.1 - U
READ WORD @ 0,SP (UNSTACK TMP3)
SP = SP + 2
NO BUS ACCESS
TMP1 = TMP2 = TMP3 = $0000
3.1 - U
READ WORD @ 0,SP (UNSTACK TMP2)
SP = SP + 2
4.0 - f
4.1 - U
NO BUS ACCESS
READ WORD @ 0,SP (UNSTACK TMP1)
B = B – 1 DECREMENT ITERATION COUNTER
SP = SP + 2
5.0 - r
5.1 - r
READ BYTE @ –1,Y (FUZZY OUTPUT Fi)
6.1 - r
READ BYTE @ –1,X (SINGLETON Si)
7.1 - S
WRITE WORD @ –2,SP (STACK TMP1)
READ BYTE @ 0,Y (FUZZY OUTPUT Fi)
Y = Y + 1 point at next fuzzy output
6.0 - r
READ BYTE @ 0,X (SINGLETON Si)
X = X + 1 POINT AT NEXT SINGLETON
YES
INTERRUPT PENDING?
NO
7.0 - f
NO BUS ACCESS
TMP1 = TMP1 + Fi
8.0 - f
SP = SP – 2
8.1 - S
NO BUS ACCESS
WRITE WORD @ –2,SP (STACK TMP2)
START MULTIPLY PPROD = Si*Fi
SP = SP – 2
9.0 - f
9.1 - S
NO BUS ACCESS
CONTINUE MULTIPLY
10.0 - f
SP = SP – 2
ADJUST PC TO POINT AT $3C wavr PSEUDO-OPCODE
NO BUS ACCESS
10.1 - f
FINISH MULTIPLY, TMP2 = TMP2 + PPROD
11.0 - f
WRITE WORD @ –2,SP (STACK TMP3)
NO BUS ACCESS
NO BUS ACCESS
TMP3 = TMP3 + (CARRY FROM PPROD ADD)
NO
CONTINUE TO INTERRUPT STACKING
B = 0?
YES
12.0 - O
READ PROGRAM WORD IF $3C MISALIGNED
ADJUST PC TO POINT AT NEXT INSTRUCTION
Y : D = TMP3 : TMP2; X = TMP1
END
Figure 9-12. WAV and wavr Instruction Flow Diagram (for M68HC12)
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
373
Fuzzy Logic Support
9.7 Custom Fuzzy Logic Programming
The basic fuzzy logic inference techniques described earlier are suitable
for a broad range of applications, but some systems may require
customization. The built-in fuzzy instructions use 8-bit resolution and
some systems may require finer resolution. The rule evaluation
instructions only support variations of MIN-MAX rule evaluation and
other methods have been discussed in fuzzy logic literature. The
weighted average of singletons is not the only defuzzification technique.
The CPU12 has several instructions and addressing modes that can be
helpful when developing custom fuzzy logic systems.
9.7.1 Fuzzification Variations
The MEM instruction supports trapezoidal membership functions and
several other varieties, including membership functions with vertical
sides (infinite slope sides). Triangular membership functions are a
subset of trapezoidal functions. Some practitioners refer to s-, z-, and
π-shaped membership functions. These refer to a trapezoid butted
against the right end of the x-axis, a trapezoid butted against the left end
of the x-axis, and a trapezoidal membership function that isn’t butted
against either end of the x-axis, respectively. Many other membership
function shapes are possible, if memory space and processing
bandwidth are sufficient.
Tabular membership functions offer complete flexibility in shape and
very fast evaluation time. However, tables take a very large amount of
memory space (as many as 256 bytes per label of one system input).
The excessive size to specify tabular membership functions makes them
impractical for most microcontroller-based fuzzy systems. The CPU12
instruction set includes two instructions (TBL and ETBL) for lookup and
interpolation of compressed tables.
The TBL instruction uses 8-bit table entries (y-values) and returns an
8-bit result. The ETBL instruction uses 16-bit table entries (y-values) and
returns a 16-bit result. A flexible indexed addressing mode is used to
identify the effective address of the data point at the beginning of the line
segment, and the data value for the end point of the line segment is the
next consecutive memory location (byte for TBL and word for ETBL). In
both cases, the B accumulator represents the ratio of (the x-distance
from the beginning of the line segment to the lookup point) to (the
Reference Manual
374
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
Custom Fuzzy Logic Programming
x-distance from the beginning of the line segment to the end of the line
segment). B is treated as an 8-bit binary fraction with radix point left of
the MSB, so each line segment can effectively be divided into 256
pieces. During execution of the TBL or ETBL instruction, the difference
between the end point y-value and the beginning point y-value (a signed
byte-TBL or word-ETBL) is multiplied by the B accumulator to get an
intermediate delta-y term. The result is the y-value of the beginning
point, plus this signed intermediate delta-y value.
Because indexed addressing mode is used to identify the starting point
of the line segment of interest, there is a great deal of flexibility in
constructing tables. A common method is to break the x-axis range into
256 equal width segments and store the y value for each of the resulting
257 endpoints. The 16-bit D accumulator is then used as the x input to
the table. The upper eight bits (A) is used as a coarse lookup to find the
line segment of interest, and the lower eight bits (B) is used to interpolate
within this line segment.
In the program sequence
LDX
#TBL_START
LDD
DATA_IN
TBL
A,X
The notation A,X causes the TBL instruction to use the Ath line segment
in the table. The low-order half of D (B) is used by TBL to calculate the
exact data value from this line segment. This type of table uses only 257
entries to approximate a table with 16 bits of resolution. This type of table
has the disadvantage of equal width line segments, which means just as
many points are needed to describe a flat portion of the desired function
as are needed for the most active portions.
Another type of table stores x:y coordinate pairs for the endpoints of
each linear segment. This type of table may reduce the table storage
space compared to the previous fixed-width segments because flat
areas of the functions can be specified with a single pair of endpoints.
This type of table is a little harder to use with the CPU12 TBL and ETBL
instructions because the table instructions expect y-values for segment
endpoints to be in consecutive memory locations.
Consider a table made up of an arbitrary number of x:y coordinate pairs,
where all values are eight bits. The table is entered with the x-coordinate
of the desired point to lookup in the A accumulator. When the table is
exited, the corresponding y-value is in the A accumulator. Figure 9-13
shows one way to work with this type of table.
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
375
Fuzzy Logic Support
BEGIN
FIND_LOOP
LDY
CMPA
#TABLE_START-2
2,+Y
;setup initial table pointer
;find first Xn > XL
;(auto pre-inc Y by 2)
BLS
FIND_LOOP
;loop if XL .le. Xn
* on fall thru, XB@-2,Y YB@-1,Y XE@0,Y and YE@1,Y
TFR
D,X
;save XL in high half of X
CLRA
;zero upper half of D
LDAB
0,Y
;D = 0:XE
SUBB
-2,Y
;D = 0:(XE-XB)
EXG
D,X
;X = (XE-XB).. D = XL:junk
SUBA
-2,Y
;A = (XL-XB)
EXG
A,D
;D = 0:(XL-XB), uses trick of EXG
FDIV
;X reg = (XL-XB)/(XE-XB)
EXG
D,X
;move fractional result to A:B
EXG
A,B
;byte swap - need result in B
TSTA
;check for rounding
BPL
NO_ROUND
INCB
;round B up by 1
NO_ROUND
LDAA
1,Y
;YE
PSHA
;put on stack for TBL later
LDAA
-1,Y
;YB
PSHA
;now YB@0,SP and YE@1,SP
TBL
2,SP+
;interpolate and deallocate
;stack temps
Figure 9-13. Endpoint Table Handling
The basic idea is to find the segment of interest, temporarily build a
1-segment table of the correct format on the stack, then use TBL with
stack relative indexed addressing to interpolate. The most difficult part
of the routine is calculating the proportional distance from the beginning
of the segment to the lookup point versus the width of the segment
((XL–XB)/(XE–XB)). With this type of table, this calculation must be done
at run time. In the previous type of table, this proportional term is an
inherent part (the lowest order bits) of the data input to the table.
Some fuzzy theorists have suggested membership functions should be
shaped like normal distribution curves or other mathematical functions.
This may be correct, but the processing requirements to solve for an
intercept on such a function would be unacceptable for most
microcontroller-based fuzzy systems. Such a function could be encoded
into a table of one of the previously described types.
For many common systems, the thing that is most important about
membership function shape is that there is a gradual transition from
non-membership to membership as the system input value approaches
the central range of the membership function.
Reference Manual
376
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
Custom Fuzzy Logic Programming
Examine the human problem of stopping a car at an intersection. Rules
such as “If intersection is close and speed is fast, apply brakes” might be
used. The meaning (reflected in membership function shape and
position) of the labels “close” and “fast” will be different for a teenager
than they are for a grandmother, but both can accomplish the goal of
stopping. It makes intuitive sense that the exact shape of a membership
function is much less important than the fact that it has gradual
boundaries.
9.7.2 Rule Evaluation Variations
The REV and REVW instructions expect fuzzy input and fuzzy output
values to be 8-bit values. In a custom fuzzy inference program, higher
resolution may be desirable (although this is not a common
requirement). The CPU12 includes variations of minimum and maximum
operations that work with the fuzzy MIN-MAX inference algorithm. The
problem with the fuzzy inference algorithm is that the min and max
operations need to store their results differently, so the min and max
instructions must work differently or more than one variation of these
instructions is needed.
The CPU12 has MIN and MAX instructions for 8- or 16-bit operands,
where one operand is in an accumulator and the other is a referenced
memory location. There are separate variations that replace the
accumulator or the memory location with the result. While processing
rule antecedents in a fuzzy inference program, a reference value must
be compared to each of the referenced fuzzy inputs, and the smallest
input must end up in an accumulator. The instruction
EMIND
2,X+
;process one rule antecedent
automates the central operations needed to process rule antecedents.
The E stands for extended, so this instruction compares 16-bit operands.
The D at the end of the mnemonic stands for the D accumulator, which
is both the first operand for the comparison and the destination of the
result. The 2,X+ is an indexed addressing specification that says X
points to the second operand for the comparison and it will be
post-incremented by 2 to point at the next rule antecedent.
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
377
Fuzzy Logic Support
When processing rule consequents, the operand in the accumulator
must remain constant (in case there is more than one consequent in the
rule), and the result of the comparison must replace the referenced fuzzy
output in RAM. To do this, use the instruction
EMAXM
2,X+
;process one rule consequent
The M at the end of the mnemonic indicates that the result will replace
the referenced memory operand. Again, indexed addressing is used.
These two instructions would form the working part of a 16-bit resolution
fuzzy inference routine.
There are many other methods of performing inference, but none of
these are as widely used as the min-max method. Since the CPU12 is a
general-purpose microcontroller, the programmer has complete
freedom to program any algorithm desired. A custom programmed
algorithm would typically take more code space and execution time than
a routine that used the built-in REV or REVW instructions.
9.7.3 Defuzzification Variations
Other CPU12 instructions can help with custom defuzzification routines
in two main areas:
•
The first case is working with operands that are more than eight
bits.
•
The second case involves using an entirely different approach
than weighted average of singletons.
The primary part of the WAV instruction is a multiply and accumulate
operation to get the numerator for the weighted average calculation.
When working with operands as large as 16 bits, the EMACS instruction
could at least be used to automate the multiply and accumulate function.
The CPU12 has extended math capabilities, including the EMACS
instruction which uses 16-bit input operands and accumulates the sum
to a 32-bit memory location and 32-bit by 16-bit divide instructions.
One benefit of the WAV instruction is that both a sum of products and a
sum of weights are maintained, while the fuzzy output operand is only
accessed from memory once. Since memory access time is such a
significant part of execution time, this provides a speed advantage
compared to conventional instructions.
Reference Manual
378
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Fuzzy Logic Support
Custom Fuzzy Logic Programming
The weighted average of singletons is the most commonly used
technique in microcontrollers because it is computationally less difficult
than most other methods. The simplest method is called max
defuzzification, which simply uses the largest fuzzy output as the system
result. However, this approach does not take into account any other
fuzzy outputs, even when they are almost as true as the chosen max
output. Max defuzzification is not a good general choice because it only
works for a subset of fuzzy logic applications.
The CPU12 is well suited for more computationally challenging
algorithms than weighted average. A 32-bit by 16-bit divide instruction
takes 11 or 12 25-MHz cycles for unsigned or signed variations. A 16-bit
by 16-bit multiply with a 32-bit result takes only three 25-MHz cycles.
The EMACS instruction uses 16-bit operands and accumulates the
result in a 32-bit memory location, taking only 12 25-MHz cycles per
iteration, including accessing all operands from memory and storing the
result to memory.
S12CPUV2
MOTOROLA
Reference Manual
Fuzzy Logic Support
379
Fuzzy Logic Support
Reference Manual
380
S12CPUV2
Fuzzy Logic Support
MOTOROLA
Reference Manual — S12CPUV2
Appendix A. Instruction Reference
A.1 Introduction
This appendix provides quick references for the instruction set, opcode
map, and encoding.
A
0 7
B
15
D
0
8-BIT ACCUMULATORS A AND B
OR
16-BIT DOUBLE ACCUMULATOR D
15
X
0
INDEX REGISTER X
15
Y
0
INDEX REGISTER Y
15
SP
0
STACK POINTER
15
PC
0
PROGRAM COUNTER
7
S X H I N Z V C
0
CONDITION CODE REGISTER
CARRY
OVERFLOW
ZERO
NEGATIVE
MASK (DISABLE) IRQ INTERRUPTS
HALF-CARRY
(USED IN BCD ARITHMETIC)
MASK (DISABLE) XIRQ INTERRUPTS
RESET OR XIRQ SET X,
INSTRUCTIONS MAY CLEAR X
BUT CANNOT SET X
STOP DISABLE (IGNORE STOP OPCODES)
RESET DEFAULT IS 1
Figure A-1. Programming Model
S12CPUV2
MOTOROLA
Reference Manual
Instruction Reference
381
Instruction Reference
A.2 Stack and Memory Layout
SP BEFORE
INTERRUPT
SP +9
HIGHER ADDRESSES
RTNLO
RTNHI
YLO
YHI
XLO
XHI
A
B
SP AFTER
INTERRUPT
CCR
LOWER ADDRESSES
STACK UPON ENTRY TO SERVICE ROUTINE
IF SP WAS ODD BEFORE INTERRUPT
SP +8
RTNLO
STACK UPON ENTRY TO SERVICE ROUTINE
IF SP WAS EVEN BEFORE INTERRUPT
SP +9
SP +9
SP +10
SP +6
YLO
RTNHI
SP +7
SP +7
RTNHI
RTNLO
SP +8
SP +4
XLO
YHI
SP +5
SP +5
YHI
YLO
SP +6
SP +2
A
XHI
SP +3
SP +4
XHI
XLO
SP +4
SP
CCR
B
SP +1
SP +1
B
A
SP +2
SP –1
SP –1
CCR
SP
SP –2
A.3 Interrupt Vector Locations
$FFFE, $FFFF
$FFFC, $FFFD
$FFFA, $FFFB
$FFF8, $FFF9
$FFF6, $FFF7
$FFF4, $FFF5
$FFF2, $FFF3
$FFC0–$FFF1 (M68HC12)
$FF00–$FFF1 (HCS12)
Power-On (POR) or External Reset
Clock Monitor Reset
Computer Operating Properly (COP Watchdog Reset
Unimplemented Opcode Trap
Software Interrupt Instruction (SWI)
XIRQ
IRQ
Device-Specific Interrupt Sources
Device-Specific Interrupt Sources
Reference Manual
382
S12CPUV2
Instruction Reference
MOTOROLA
Instruction Reference
A.4 Notation Used in Instruction Set Summary
CPU Register Notation
Accumulator A — A or a
Accumulator B — B or b
Accumulator D — D or d
Index Register X — X or x
Index Register Y — Y or y
Stack Pointer — SP, sp, or s
Program Counter — PC, pc, or p
Condition Code Register — CCR or c
Explanation of Italic Expressions in Source Form Column
abc — A or B or CCR
abcdxys — A or B or CCR or D or X or Y or SP. Some assemblers also allow T2 or T3.
abd — A or B or D
abdxys — A or B or D or X or Y or SP
dxys — D or X or Y or SP
msk8 — 8-bit mask, some assemblers require # symbol before value
opr8i — 8-bit immediate value
opr16i — 16-bit immediate value
opr8a — 8-bit address used with direct address mode
opr16a — 16-bit address value
oprx0_xysp — Indexed addressing postbyte code:
oprx3,–xys Predecrement X or Y or SP by 1 . . . 8
oprx3,+xys Preincrement X or Y or SP by 1 . . . 8
oprx3,xys– Postdecrement X or Y or SP by 1 . . . 8
oprx3,xys+ Postincrement X or Y or SP by 1 . . . 8
oprx5,xysp 5-bit constant offset from X or Y or SP or PC
abd,xysp Accumulator A or B or D offset from X or Y or SP or PC
oprx3 — Any positive integer 1 . . . 8 for pre/post increment/decrement
oprx5 — Any integer in the range –16 . . . +15
oprx9 — Any integer in the range –256 . . . +255
oprx16 — Any integer in the range –32,768 . . . 65,535
page — 8-bit value for PPAGE, some assemblers require # symbol before this value
rel8 — Label of branch destination within –128 to +127 locations
rel9 — Label of branch destination within –256 to +255 locations
rel16 — Any label within 64K memory space
trapnum — Any 8-bit integer in the range $30-$39 or $40-$FF
xys — X or Y or SP
xysp — X or Y or SP or PC
Operators
+ — Addition
– —
Subtraction
• —
+ —
Logical AND
Logical OR (inclusive)
Continued on next page
S12CPUV2
MOTOROLA
Reference Manual
Instruction Reference
383
Instruction Reference
Operators (continued)
⊕ — Logical exclusive OR
× —
÷ —
Multiplication
M —
: —
Negation. One’s complement (invert each bit of M)
⇒ —
⇔ —
Division
Concatenate
Example: A : B means the 16-bit value formed by concatenating 8-bit accumulator A
with 8-bit accumulator B.
A is in the high-order position.
Transfer
Example: (A) ⇒ M means the content of accumulator A is transferred to memory
location M.
Exchange
Example: D ⇔ X means exchange the contents of D with those of X.
Address Mode Notation
INH — Inherent; no operands in object code
IMM — Immediate; operand in object code
DIR — Direct; operand is the lower byte of an address from $0000 to $00FF
EXT — Operand is a 16-bit address
REL — Two’s complement relative offset; for branch instructions
IDX — Indexed (no extension bytes); includes:
5-bit constant offset from X, Y, SP, or PC
Pre/post increment/decrement by 1 . . . 8
Accumulator A, B, or D offset
IDX1 — 9-bit signed offset from X, Y, SP, or PC; 1 extension byte
IDX2 — 16-bit signed offset from X, Y, SP, or PC; 2 extension bytes
[IDX2] — Indexed-indirect; 16-bit offset from X, Y, SP, or PC
[D, IDX] — Indexed-indirect; accumulator D offset from X, Y, SP, or PC
Machine Coding
dd — 8-bit direct address $0000 to $00FF. (High byte assumed to be $00).
ee — High-order byte of a 16-bit constant offset for indexed addressing.
eb — Exchange/Transfer post-byte. See Table A-5 on page 405.
ff — Low-order eight bits of a 9-bit signed constant offset for indexed addressing,
or low-order byte of a 16-bit constant offset for indexed addressing.
hh — High-order byte of a 16-bit extended address.
ii — 8-bit immediate data value.
jj — High-order byte of a 16-bit immediate data value.
kk — Low-order byte of a 16-bit immediate data value.
lb — Loop primitive (DBNE) post-byte. See Table A-6 on page 406.
ll — Low-order byte of a 16-bit extended address.
Reference Manual
384
S12CPUV2
Instruction Reference
MOTOROLA
Instruction Reference
mm — 8-bit immediate mask value for bit manipulation instructions.
Set bits indicate bits to be affected.
pg — Program page (bank) number used in CALL instruction.
qq — High-order byte of a 16-bit relative offset for long branches.
tn — Trap number $30–$39 or $40–$FF.
rr — Signed relative offset $80 (–128) to $7F (+127).
Offset relative to the byte following the relative offset byte, or
low-order byte of a 16-bit relative offset for long branches.
xb — Indexed addressing post-byte. See Table A-3 on page 403
and Table A-4 on page 404.
Access Detail
Each code letter except (,), and comma equals one CPU cycle. Uppercase = 16-bit
operation and lowercase = 8-bit operation. For complex sequences see the CPU12
Reference Manual (CPU12RM/AD) for more detailed information.
f — Free cycle, CPU doesn’t use bus
g — Read PPAGE internally
I — Read indirect pointer (indexed indirect)
i — Read indirect PPAGE value (CALL indirect only)
n — Write PPAGE internally
O — Optional program word fetch (P) if instruction is misaligned and has
an odd number of bytes of object code — otherwise, appears as
a free cycle (f); Page 2 prebyte treated as a separate 1-byte instruction
P — Program word fetch (always an aligned-word read)
r — 8-bit data read
R — 16-bit data read
s — 8-bit stack write
S — 16-bit stack write
w — 8-bit data write
W — 16-bit data write
u — 8-bit stack read
U — 16-bit stack read
V — 16-bit vector fetch (always an aligned-word read)
t — 8-bit conditional read (or free cycle)
T — 16-bit conditional read (or free cycle)
x — 8-bit conditional write (or free cycle)
() — Indicate a microcode loop
, — Indicates where an interrupt could be honored
Special Cases
PPP/P — Short branch, PPP if branch taken, P if not
OPPP/OPO — Long branch, OPPP if branch taken, OPO if not
S12CPUV2
MOTOROLA
Reference Manual
Instruction Reference
385
Instruction Reference
Condition Codes Columns
– — Status bit not affected by operation.
0 — Status bit cleared by operation.
1 — Status bit set by operation.
∆ — Status bit affected by operation.
fl — Status bit may be cleared or remain set, but is not set by operation.
⇑ — Status bit may be set or remain cleared, but is not cleared by operation.
? — Status bit may be changed by operation but the final state is not defined.
! — Status bit used for a special purpose.
Reference Manual
386
S12CPUV2
Instruction Reference
MOTOROLA
Instruction Reference
Table A-1. Instruction Set Summary (Sheet 1 of 14)
Source Form
Operation
Addr.
Mode
Machine
Coding (hex)
Access Detail
HCS12
M68HC12
SXHI
NZVC
ABA
(A) + (B) ⇒ A
Add Accumulators A and B
INH
18 06
OO
OO – – ∆ – ∆ ∆ ∆ ∆
ABX
(B) + (X) ⇒ X
Translates to LEAX B,X
IDX
1A E5
Pf
PP1
––––
––––
ABY
(B) + (Y) ⇒ Y
Translates to LEAY B,Y
IDX
19 ED
Pf
PP1
––––
––––
ADCA #opr8i
ADCA opr8a
ADCA opr16a
ADCA oprx0_xysp
ADCA oprx9,xysp
ADCA oprx16,xysp
ADCA [D,xysp]
ADCA [oprx16,xysp]
(A) + (M) + C ⇒ A
Add with Carry to A
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
89 ii
99 dd
B9 hh ll
A9 xb
A9 xb ff
A9 xb ee ff
A9 xb
A9 xb ee ff
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P ––∆– ∆∆∆∆
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
ADCB #opr8i
ADCB opr8a
ADCB opr16a
ADCB oprx0_xysp
ADCB oprx9,xysp
ADCB oprx16,xysp
ADCB [D,xysp]
ADCB [oprx16,xysp]
(B) + (M) + C ⇒ B
Add with Carry to B
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
C9 ii
D9 dd
F9 hh ll
E9 xb
E9 xb ff
E9 xb ee ff
E9 xb
E9 xb ee ff
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P ––∆– ∆∆∆∆
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
ADDA #opr8i
ADDA opr8a
ADDA opr16a
ADDA oprx0_xysp
ADDA oprx9,xysp
ADDA oprx16,xysp
ADDA [D,xysp]
ADDA [oprx16,xysp]
(A) + (M) ⇒ A
Add without Carry to A
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
8B ii
9B dd
BB hh ll
AB xb
AB xb ff
AB xb ee ff
AB xb
AB xb ee ff
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P ––∆– ∆∆∆∆
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
ADDB #opr8i
ADDB opr8a
ADDB opr16a
ADDB oprx0_xysp
ADDB oprx9,xysp
ADDB oprx16,xysp
ADDB [D,xysp]
ADDB [oprx16,xysp]
(B) + (M) ⇒ B
Add without Carry to B
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
CB ii
DB dd
FB hh ll
EB xb
EB xb ff
EB xb ee ff
EB xb
EB xb ee ff
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P ––∆– ∆∆∆∆
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
ADDD #opr16i
ADDD opr8a
ADDD opr16a
ADDD oprx0_xysp
ADDD oprx9,xysp
ADDD oprx16,xysp
ADDD [D,xysp]
ADDD [oprx16,xysp]
(A:B) + (M:M+1) ⇒ A:B
Add 16-Bit to D (A:B)
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
C3 jj kk
D3 dd
F3 hh ll
E3 xb
E3 xb ff
E3 xb ee ff
E3 xb
E3 xb ee ff
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
––––
∆∆∆∆
ANDA #opr8i
ANDA opr8a
ANDA opr16a
ANDA oprx0_xysp
ANDA oprx9,xysp
ANDA oprx16,xysp
ANDA [D,xysp]
ANDA [oprx16,xysp]
(A) • (M) ⇒ A
Logical AND A with Memory
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
84 ii
94 dd
B4 hh ll
A4 xb
A4 xb ff
A4 xb ee ff
A4 xb
A4 xb ee ff
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
––––
∆∆0–
ANDB #opr8i
ANDB opr8a
ANDB opr16a
ANDB oprx0_xysp
ANDB oprx9,xysp
ANDB oprx16,xysp
ANDB [D,xysp]
ANDB [oprx16,xysp]
(B) • (M) ⇒ B
Logical AND B with Memory
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
C4 ii
D4 dd
F4 hh ll
E4 xb
E4 xb ff
E4 xb ee ff
E4 xb
E4 xb ee ff
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
––––
∆∆0–
ANDCC #opr8i
(CCR) • (M) ⇒ CCR
Logical AND CCR with Memory
IMM
10 ii
P
P ⇓⇓⇓⇓ ⇓⇓⇓⇓
Note 1. Due to internal CPU requirements, the program word fetch is performed twice to the same address during this instruction.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Reference
387
Instruction Reference
Table A-1. Instruction Set Summary (Sheet 2 of 14)
Source Form
ASL opr16a
ASL oprx0_xysp
ASL oprx9,xysp
ASL oprx16,xysp
ASL [D,xysp]
ASL [oprx16,xysp]
ASLA
ASLB
Operation
0
b0
b7
C
Arithmetic Shift Left
Arithmetic Shift Left Accumulator A
Arithmetic Shift Left Accumulator B
ASLD
Addr.
Mode
Machine
Coding (hex)
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
INH
INH
Access Detail
SXHI
NZVC
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
O
O
––––
∆∆∆∆
O
––––
∆∆∆∆
rPwO
rPw
rPwO
frPwP
fIfrPw
fIPrPw
O
O
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
O
O
––––
∆∆∆∆
24 rr
PPP/P1
PPP/P1
––––
––––
rPOw
rPPw
rPOw
rPwP
frPwOP
––––
∆∆0–
HCS12
M68HC12
78 hh ll
68 xb
68 xb ff
68 xb ee ff
68 xb
68 xb ee ff
48
58
rPwO
rPw
rPwO
frPwP
fIfrPw
fIPrPw
O
O
INH
59
O
77 hh ll
67 xb
67 xb ff
67 xb ee ff
67 xb
67 xb ee ff
47
57
0
C
b7 A b0 b7
Arithmetic Shift Left Double
B
b0
ASR opr16a
ASR oprx0_xysp
ASR oprx9,xysp
ASR oprx16,xysp
ASR [D,xysp]
ASR [oprx16,xysp]
ASRA
ASRB
b7
Arithmetic Shift Right
Arithmetic Shift Right Accumulator A
Arithmetic Shift Right Accumulator B
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
INH
INH
BCC rel8
Branch if Carry Clear (if C = 0)
REL
BCLR opr8a, msk8
BCLR opr16a, msk8
BCLR oprx0_xysp, msk8
BCLR oprx9,xysp, msk8
BCLR oprx16,xysp, msk8
(M) • (mm) ⇒ M
Clear Bit(s) in Memory
DIR
EXT
IDX
IDX1
IDX2
4D dd mm
1D hh ll mm
0D xb mm
0D xb ff mm
0D xb ee ff mm
rPwO
rPwP
rPwO
rPwP
frPwPO
BCS rel8
Branch if Carry Set (if C = 1)
REL
25 rr
PPP/P1
PPP/P1
––––
––––
BEQ rel8
Branch if Equal (if Z = 1)
REL
27 rr
PPP/P1
PPP/P1
––––
––––
BGE rel8
Branch if Greater Than or Equal
(if N ⊕ V = 0) (signed)
REL
2C rr
PPP/P1
PPP/P1
––––
––––
BGND
Place CPU in Background Mode
see CPU12 Reference Manual
INH
00
VfPPP
VfPPP
––––
––––
BGT rel8
Branch if Greater Than
(if Z + (N ⊕ V) = 0) (signed)
REL
2E rr
PPP/P1
PPP/P1
––––
––––
BHI rel8
Branch if Higher
(if C + Z = 0) (unsigned)
REL
22 rr
PPP/P1
PPP/P1
––––
––––
BHS rel8
Branch if Higher or Same
(if C = 0) (unsigned)
same function as BCC
REL
24 rr
PPP/P1
PPP/P1
––––
––––
BITA #opr8i
BITA opr8a
BITA opr16a
BITA oprx0_xysp
BITA oprx9,xysp
BITA oprx16,xysp
BITA [D,xysp]
BITA [oprx16,xysp]
(A) • (M)
Logical AND A with Memory
Does not change Accumulator or Memory
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
85 ii
95 dd
B5 hh ll
A5 xb
A5 xb ff
A5 xb ee ff
A5 xb
A5 xb ee ff
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
––––
∆∆0–
BITB #opr8i
BITB opr8a
BITB opr16a
BITB oprx0_xysp
BITB oprx9,xysp
BITB oprx16,xysp
BITB [D,xysp]
BITB [oprx16,xysp]
(B) • (M)
Logical AND B with Memory
Does not change Accumulator or Memory
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
C5 ii
D5 dd
F5 hh ll
E5 xb
E5 xb ff
E5 xb ee ff
E5 xb
E5 xb ee ff
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
––––
∆∆0–
BLE rel8
Branch if Less Than or Equal
(if Z + (N ⊕ V) = 1) (signed)
REL
2F rr
PPP/P1
PPP/P1
––––
––––
BLO rel8
Branch if Lower
(if C = 1) (unsigned)
same function as BCS
REL
25 rr
PPP/P1
PPP/P1
––––
––––
b0
C
Note 1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program fetch cycle if the branch is not taken.
Reference Manual
388
S12CPUV2
Instruction Reference
MOTOROLA
Instruction Reference
Table A-1. Instruction Set Summary (Sheet 3 of 14)
Source Form
Addr.
Mode
Operation
Machine
Coding (hex)
Access Detail
SXHI
NZVC
1
1
HCS12
M68HC12
BLS rel8
Branch if Lower or Same
(if C + Z = 1) (unsigned)
REL
23 rr
PPP/P
PPP/P
––––
––––
BLT rel8
Branch if Less Than
(if N ⊕ V = 1) (signed)
REL
2D rr
PPP/P1
PPP/P1
––––
––––
BMI rel8
Branch if Minus (if N = 1)
REL
2B rr
PPP/P1
PPP/P1
1
––––
––––
BNE rel8
Branch if Not Equal (if Z = 0)
REL
26 rr
PPP/P
PPP/P1
––––
––––
BPL rel8
Branch if Plus (if N = 0)
REL
2A rr
PPP/P1
PPP/P1
––––
––––
BRA rel8
Branch Always (if 1 = 1)
REL
20 rr
PPP
PPP
––––
––––
Branch if (M) • (mm) = 0
BRCLR opr8a, msk8, rel8
BRCLR opr16a, msk8, rel8
(if All Selected Bit(s) Clear)
BRCLR oprx0_xysp, msk8, rel8
BRCLR oprx9,xysp, msk8, rel8
BRCLR oprx16,xysp, msk8, rel8
DIR
EXT
IDX
IDX1
IDX2
rPPP
4F dd mm rr
rfPPP
1F hh ll mm rr
rPPP
0F xb mm rr
rfPPP
0F xb ff mm rr
0F xb ee ff mm rr PrfPPP
rPPP
rfPPP
rPPP
rffPPP
frPffPPP
––––
––––
BRN rel8
REL
21 rr
P
––––
––––
BRSET opr8, msk8, rel8
Branch if (M) • (mm) = 0
BRSET opr16a, msk8, rel8
(if All Selected Bit(s) Set)
BRSET oprx0_xysp, msk8, rel8
BRSET oprx9,xysp, msk8, rel8
BRSET oprx16,xysp, msk8, rel8
Branch Never (if 1 = 0)
DIR
EXT
IDX
IDX1
IDX2
rPPP
4E dd mm rr
rfPPP
1E hh ll mm rr
rPPP
0E xb mm rr
rfPPP
0E xb ff mm rr
0E xb ee ff mm rr PrfPPP
rPPP
rfPPP
rPPP
rffPPP
frPffPPP
––––
––––
BSET opr8, msk8
BSET opr16a, msk8
BSET oprx0_xysp, msk8
BSET oprx9,xysp, msk8
BSET oprx16,xysp, msk8
DIR
EXT
IDX
IDX1
IDX2
4C dd mm
1C hh ll mm
0C xb mm
0C xb ff mm
0C xb ee ff mm
rPwO
rPwP
rPwO
rPwP
frPwPO
rPOw
rPPw
rPOw
rPwP
frPwOP
––––
∆∆0–
(M) + (mm) ⇒ M
Set Bit(s) in Memory
P
BSR rel8
(SP) – 2 ⇒ SP; RTNH:RTNL ⇒ M(SP):M(SP+1)
Subroutine address ⇒ PC
Branch to Subroutine
REL
07 rr
SPPP
PPPS
––––
––––
BVC rel8
Branch if Overflow Bit Clear (if V = 0)
REL
28 rr
PPP/P1
PPP/P1
––––
––––
PPP/P1
––––
––––
gnfSsPPP
gnfSsPPP
gnfSsPPP
fgnfSsPPP
fIignSsPPP
fIignSsPPP
––––
––––
BVS rel8
Branch if Overflow Bit Set (if V = 1)
REL
29 rr
PPP/P1
CALL opr16a, page
CALL oprx0_xysp, page
CALL oprx9,xysp, page
CALL oprx16,xysp, page
CALL [D,xysp]
CALL [oprx16, xysp]
(SP) – 2 ⇒ SP; RTNH:RTNL ⇒ M(SP):M(SP+1)
(SP) – 1 ⇒ SP; (PPG) ⇒ M(SP);
pg ⇒ PPAGE register; Program address ⇒ PC
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
4A hh ll pg
4B xb pg
4B xb ff pg
4B xb ee ff pg
4B xb
4B xb ee ff
gnSsPPP
gnSsPPP
gnSsPPP
fgnSsPPP
fIignSsPPP
fIignSsPPP
Call subroutine in extended memory
(Program may be located on another
expansion memory page.)
Indirect modes get program address
and new pg value based on pointer.
CBA
(A) – (B)
Compare 8-Bit Accumulators
INH
18 17
OO
OO
––––
∆∆∆∆
CLC
0⇒C
Translates to ANDCC #$FE
IMM
10 FE
P
P
––––
–––0
CLI
0⇒I
Translates to ANDCC #$EF
(enables I-bit interrupts)
IMM
10 EF
P
P
–––0
––––
CLR opr16a
CLR oprx0_xysp
CLR oprx9,xysp
CLR oprx16,xysp
CLR [D,xysp]
CLR [oprx16,xysp]
CLRA
CLRB
0⇒M
Clear Memory Location
PwO
Pw
PwO
PwP
PIfw
PIPw
O
O
wOP
Pw
PwO
PwP
PIfPw
PIPPw
O
O
0100
Clear Accumulator A
Clear Accumulator B
79 hh ll
69 xb
69 xb ff
69 xb ee ff
69 xb
69 xb ee ff
87
C7
––––
0⇒A
0⇒B
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
INH
INH
IMM
10 FD
P
P
––––
––0–
CLV
0⇒V
Translates to ANDCC #$FD
Note 1. PPP/P indicates this instruction takes three cycles to refill the instruction queue if the branch is taken and one program fetch cycle if the branch is not taken.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Reference
389
Instruction Reference
Table A-1. Instruction Set Summary (Sheet 4 of 14)
Source Form
Operation
Addr.
Mode
Machine
Coding (hex)
Access Detail
HCS12
M68HC12
SXHI
NZVC
CMPA #opr8i
CMPA opr8a
CMPA opr16a
CMPA oprx0_xysp
CMPA oprx9,xysp
CMPA oprx16,xysp
CMPA [D,xysp]
CMPA [oprx16,xysp]
(A) – (M)
Compare Accumulator A with Memory
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
81 ii
91 dd
B1 hh ll
A1 xb
A1 xb ff
A1 xb ee ff
A1 xb
A1 xb ee ff
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
––––
∆∆∆∆
CMPB #opr8i
CMPB opr8a
CMPB opr16a
CMPB oprx0_xysp
CMPB oprx9,xysp
CMPB oprx16,xysp
CMPB [D,xysp]
CMPB [oprx16,xysp]
(B) – (M)
Compare Accumulator B with Memory
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
C1 ii
D1 dd
F1 hh ll
E1 xb
E1 xb ff
E1 xb ee ff
E1 xb
E1 xb ee ff
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
––––
∆∆∆∆
COM opr16a
COM oprx0_xysp
COM oprx9,xysp
COM oprx16,xysp
COM [D,xysp]
COM [oprx16,xysp]
COMA
COMB
(M) ⇒ M equivalent to $FF – (M) ⇒ M
1’s Complement Memory Location
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
INH
INH
71 hh ll
61 xb
61 xb ff
61 xb ee ff
61 xb
61 xb ee ff
41
51
rPwO
rPw
rPwO
frPwP
fIfrPw
fIPrPw
O
O
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
O
O
––––
∆∆01
CPD #opr16i
CPD opr8a
CPD opr16a
CPD oprx0_xysp
CPD oprx9,xysp
CPD oprx16,xysp
CPD [D,xysp]
CPD [oprx16,xysp]
(A:B) – (M:M+1)
Compare D to Memory (16-Bit)
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
8C jj kk
9C dd
BC hh ll
AC xb
AC xb ff
AC xb ee ff
AC xb
AC xb ee ff
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
––––
∆∆∆∆
CPS #opr16i
CPS opr8a
CPS opr16a
CPS oprx0_xysp
CPS oprx9,xysp
CPS oprx16,xysp
CPS [D,xysp]
CPS [oprx16,xysp]
(SP) – (M:M+1)
Compare SP to Memory (16-Bit)
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
8F jj kk
9F dd
BF hh ll
AF xb
AF xb ff
AF xb ee ff
AF xb
AF xb ee ff
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
––––
∆∆∆∆
CPX #opr16i
CPX opr8a
CPX opr16a
CPX oprx0_xysp
CPX oprx9,xysp
CPX oprx16,xysp
CPX [D,xysp]
CPX [oprx16,xysp]
(X) – (M:M+1)
Compare X to Memory (16-Bit)
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
8E jj kk
9E dd
BE hh ll
AE xb
AE xb ff
AE xb ee ff
AE xb
AE xb ee ff
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
––––
∆∆∆∆
CPY #opr16i
CPY opr8a
CPY opr16a
CPY oprx0_xysp
CPY oprx9,xysp
CPY oprx16,xysp
CPY [D,xysp]
CPY [oprx16,xysp]
(Y) – (M:M+1)
Compare Y to Memory (16-Bit)
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
8D jj kk
9D dd
BD hh ll
AD xb
AD xb ff
AD xb ee ff
AD xb
AD xb ee ff
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
––––
∆∆∆∆
DAA
Adjust Sum to BCD
Decimal Adjust Accumulator A
INH
18 07
OfO
OfO
––––
∆∆?∆
DBEQ abdxys, rel9
(cntr) – 1⇒ cntr
if (cntr) = 0, then Branch
else Continue to next instruction
REL
(9-bit)
04 lb rr
PPP (branch)
PPO (no
branch)
PPP
––––
––––
(A) ⇒ A
Complement Accumulator A
(B) ⇒ B
Complement Accumulator B
Decrement Counter and Branch if = 0
(cntr = A, B, D, X, Y, or SP)
Reference Manual
390
S12CPUV2
Instruction Reference
MOTOROLA
Instruction Reference
Table A-1. Instruction Set Summary (Sheet 5 of 14)
Source Form
DBNE abdxys, rel9
Addr.
Mode
Operation
(cntr) – 1 ⇒ cntr
If (cntr) not = 0, then Branch;
else Continue to next instruction
Machine
Coding (hex)
Access Detail
HCS12
REL
(9-bit)
04 lb rr
PPP (branch)
PPO (no
branch)
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
INH
INH
73 hh ll
63 xb
63 xb ff
63 xb ee ff
63 xb
63 xb ee ff
43
53
rPwO
rPw
rPwO
frPwP
fIfrPw
fIPrPw
O
O
SXHI
NZVC
PPP
––––
––––
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
O
O
––––
∆∆∆–
M68HC12
Decrement Counter and Branch if ≠ 0
(cntr = A, B, D, X, Y, or SP)
DEC opr16a
DEC oprx0_xysp
DEC oprx9,xysp
DEC oprx16,xysp
DEC [D,xysp]
DEC [oprx16,xysp]
DECA
DECB
(M) – $01 ⇒ M
Decrement Memory Location
(A) – $01 ⇒ A
(B) – $01 ⇒ B
Decrement A
Decrement B
DES
(SP) – $0001 ⇒ SP
Translates to LEAS –1,SP
IDX
1B 9F
Pf
PP1
––––
––––
DEX
(X) – $0001 ⇒ X
Decrement Index Register X
INH
09
O
O
––––
–∆––
DEY
(Y) – $0001 ⇒ Y
Decrement Index Register Y
INH
03
O
O
––––
–∆––
EDIV
(Y:D) ÷ (X) ⇒ Y Remainder ⇒ D
32 by 16 Bit ⇒ 16 Bit Divide (unsigned)
INH
11
ffffffffffO
ffffffffffO
––––
∆∆∆∆
EDIVS
(Y:D) ÷ (X) ⇒ Y Remainder ⇒ D
32 by 16 Bit ⇒ 16 Bit Divide (signed)
INH
18 14
OffffffffffO
OffffffffffO
––––
∆∆∆∆
EMACS opr16a 2
(M(X):M(X+1)) × (M(Y):M(Y+1)) + (M~M+3) ⇒ M~M+3
Special
18 12 hh ll
ORROfffRRfWWP
ORROfffRRfWWP
––––
∆∆∆∆
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
18 1A xb
18 1A xb ff
18 1A xb ee ff
18 1A xb
18 1A xb ee ff
ORPf
ORPO
OfRPP
OfIfRPf
OfIPRPf
ORfP
ORPO
OfRPP
OfIfRfP
OfIPRfP
––––
∆∆∆∆
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
18 1E xb
18 1E xb ff
18 1E xb ee ff
18 1E xb
18 1E xb ee ff
ORPW
ORPWO
OfRPWP
OfIfRPW
OfIPRPW
ORPW
ORPWO
OfRPWP
OfIfRPW
OfIPRPW
––––
∆∆∆∆
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
18 1B xb
18 1B xb ff
18 1B xb ee ff
18 1B xb
18 1B xb ee ff
ORPf
ORPO
OfRPP
OfIfRPf
OfIPRPf
ORfP
ORPO
OfRPP
OfIfRfP
OfIPRfP
––––
∆∆∆∆
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
18 1F xb
18 1F xb ff
18 1F xb ee ff
18 1F xb
18 1F xb ee ff
ORPW
ORPWO
OfRPWP
OfIfRPW
OfIPRPW
ORPW
ORPWO
OfRPWP
OfIfRPW
OfIPRPW
––––
∆∆∆∆
16 by 16 Bit ⇒ 32 Bit
Multiply and Accumulate (signed)
EMAXD oprx0_xysp
EMAXD oprx9,xysp
EMAXD oprx16,xysp
EMAXD [D,xysp]
EMAXD [oprx16,xysp]
MAX((D), (M:M+1)) ⇒ D
MAX of 2 Unsigned 16-Bit Values
EMAXM oprx0_xysp
EMAXM oprx9,xysp
EMAXM oprx16,xysp
EMAXM [D,xysp]
EMAXM [oprx16,xysp]
MAX((D), (M:M+1)) ⇒ M:M+1
MAX of 2 Unsigned 16-Bit Values
EMIND oprx0_xysp
EMIND oprx9,xysp
EMIND oprx16,xysp
EMIND [D,xysp]
EMIND [oprx16,xysp]
MIN((D), (M:M+1)) ⇒ D
MIN of 2 Unsigned 16-Bit Values
EMINM oprx0_xysp
EMINM oprx9,xysp
EMINM oprx16,xysp
EMINM [D,xysp]
EMINM [oprx16,xysp]
MIN((D), (M:M+1)) ⇒ M:M+1
MIN of 2 Unsigned 16-Bit Values
EMUL
(D) × (Y) ⇒ Y:D
16 by 16 Bit Multiply (unsigned)
INH
13
ffO
ffO
––––
∆∆–∆
EMULS
(D) × (Y) ⇒ Y:D
16 by 16 Bit Multiply (signed)
INH
18 13
OfO
OfO
––––
∆∆–∆
(A) ⊕ (M) ⇒ A
Exclusive-OR A with Memory
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
––––
∆∆0–
EORA #opr8i
EORA opr8a
EORA opr16a
EORA oprx0_xysp
EORA oprx9,xysp
EORA oprx16,xysp
EORA [D,xysp]
EORA [oprx16,xysp]
N, Z, V and C status bits reflect result of
internal compare ((D) – (M:M+1))
N, Z, V and C status bits reflect result of
internal compare ((D) – (M:M+1))
N, Z, V and C status bits reflect result of
internal compare ((D) – (M:M+1))
N, Z, V and C status bits reflect result of
internal compare ((D) – (M:M+1))
(if followed by page 2 instruction)
OffO
OfO
88 ii
98 dd
B8 hh ll
A8 xb
A8 xb ff
A8 xb ee ff
A8 xb
A8 xb ee ff
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
Notes:
1. Due to internal CPU requirements, the program word fetch is performed twice to the same address during this instruction.
2. opr16a is an extended address specification. Both X and Y point to source operands.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Reference
391
Instruction Reference
Table A-1. Instruction Set Summary (Sheet 6 of 14)
Source Form
Operation
Addr.
Mode
Machine
Coding (hex)
Access Detail
SXHI
NZVC
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
––––
∆∆0–
ORRffffffP
––––
∆∆–∆
?
HCS12
M68HC12
EORB #opr8i
EORB opr8a
EORB opr16a
EORB oprx0_xysp
EORB oprx9,xysp
EORB oprx16,xysp
EORB [D,xysp]
EORB [oprx16,xysp]
(B) ⊕ (M) ⇒ B
Exclusive-OR B with Memory
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
C8 ii
D8 dd
F8 hh ll
E8 xb
E8 xb ff
E8 xb ee ff
E8 xb
E8 xb ee ff
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
ETBL oprx0_xysp
(M:M+1)+ [(B)×((M+2:M+3) – (M:M+1))] ⇒ D
16-Bit Table Lookup and Interpolate
IDX
18 3F xb
ORRffffffP
C Bit is undefined
in HC12
Initialize B, and index before ETBL.
<ea> points at first table entry (M:M+1)
and B is fractional part of lookup value
(no indirect addr. modes or extensions allowed)
EXG abcdxys,abcdxys
(r1) ⇔ (r2) (if r1 and r2 same size) or
$00:(r1) ⇒ r2 (if r1=8-bit; r2=16-bit) or
(r1low) ⇔ (r2) (if r1=16-bit; r2=8-bit)
INH
B7 eb
P
P
––––
––––
r1 and r2 may be
A, B, CCR, D, X, Y, or SP
FDIV
(D) ÷ (X) ⇒ X; Remainder ⇒ D
16 by 16 Bit Fractional Divide
INH
18 11
OffffffffffO
OffffffffffO
––––
–∆∆∆
IBEQ abdxys, rel9
(cntr) + 1⇒ cntr
If (cntr) = 0, then Branch
else Continue to next instruction
REL
(9-bit)
04 lb rr
PPP (branch)
PPO (no
branch)
PPP
––––
––––
REL
(9-bit)
04 lb rr
PPP (branch)
PPO (no
branch)
PPP
––––
––––
Increment Counter and Branch if = 0
(cntr = A, B, D, X, Y, or SP)
IBNE abdxys, rel9
(cntr) + 1⇒ cntr
if (cntr) not = 0, then Branch;
else Continue to next instruction
Increment Counter and Branch if ≠ 0
(cntr = A, B, D, X, Y, or SP)
IDIV
(D) ÷ (X) ⇒ X; Remainder ⇒ D
16 by 16 Bit Integer Divide (unsigned)
INH
18 10
OffffffffffO
OffffffffffO
––––
–∆0∆
IDIVS
(D) ÷ (X) ⇒ X; Remainder ⇒ D
16 by 16 Bit Integer Divide (signed)
INH
18 15
OffffffffffO
OffffffffffO
––––
∆∆∆∆
INC opr16a
INC oprx0_xysp
INC oprx9,xysp
INC oprx16,xysp
INC [D,xysp]
INC [oprx16,xysp]
INCA
INCB
(M) + $01 ⇒ M
Increment Memory Byte
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
INH
INH
72 hh ll
62 xb
62 xb ff
62 xb ee ff
62 xb
62 xb ee ff
42
52
rPwO
rPw
rPwO
frPwP
fIfrPw
fIPrPw
O
O
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
O
O
––––
∆∆∆–
(A) + $01 ⇒ A
(B) + $01 ⇒ B
Increment Acc. A
Increment Acc. B
INS
(SP) + $0001 ⇒ SP
Translates to LEAS 1,SP
IDX
1B 81
Pf
PP1
––––
––––
INX
(X) + $0001 ⇒ X
Increment Index Register X
INH
08
O
O
––––
–∆––
INY
(Y) + $0001 ⇒ Y
Increment Index Register Y
INH
02
O
O
––––
–∆––
JMP opr16a
JMP oprx0_xysp
JMP oprx9,xysp
JMP oprx16,xysp
JMP [D,xysp]
JMP [oprx16,xysp]
Routine address ⇒ PC
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
06 hh ll
05 xb
05 xb ff
05 xb ee ff
05 xb
05 xb ee ff
PPP
PPP
PPP
fPPP
fIfPPP
fIfPPP
PPP
PPP
PPP
fPPP
fIfPPP
fIfPPP
––––
––––
Jump
Note 1. Due to internal CPU requirements, the program word fetch is performed twice to the same address during this instruction.
Reference Manual
392
S12CPUV2
Instruction Reference
MOTOROLA
Instruction Reference
Table A-1. Instruction Set Summary (Sheet 7 of 14)
Source Form
Operation
JSR opr8a
JSR opr16a
JSR oprx0_xysp
JSR oprx9,xysp
JSR oprx16,xysp
JSR [D,xysp]
JSR [oprx16,xysp]
(SP) – 2 ⇒ SP;
RTNH:RTNL ⇒ M(SP):M(SP+1);
Subroutine address ⇒ PC
LBCC rel16
Long Branch if Carry Clear (if C = 0)
Jump to Subroutine
Addr.
Mode
Machine
Coding (hex)
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
REL
Access Detail
SXHI
NZVC
PPPS
PPPS
PPPS
PPPS
fPPPS
fIfPPPS
fIfPPPS
––––
––––
OPPP/OPO1
OPPP/OPO1
1
HCS12
M68HC12
17 dd
16 hh ll
15 xb
15 xb ff
15 xb ee ff
15 xb
15 xb ee ff
SPPP
SPPP
PPPS
PPPS
fPPPS
fIfPPPS
fIfPPPS
18 24 qq rr
––––
––––
LBCS rel16
Long Branch if Carry Set (if C = 1)
REL
18 25 qq rr
OPPP/OPO
OPPP/OPO1
––––
––––
LBEQ rel16
Long Branch if Equal (if Z = 1)
REL
18 27 qq rr
OPPP/OPO1
OPPP/OPO1
––––
––––
LBGE rel16
Long Branch Greater Than or Equal
(if N ⊕ V = 0) (signed)
REL
18 2C qq rr
OPPP/OPO1
OPPP/OPO1
––––
––––
LBGT rel16
Long Branch if Greater Than
(if Z + (N ⊕ V) = 0) (signed)
REL
18 2E qq rr
OPPP/OPO1
OPPP/OPO1
––––
––––
LBHI rel16
Long Branch if Higher
(if C + Z = 0) (unsigned)
REL
18 22 qq rr
OPPP/OPO1
OPPP/OPO1
––––
––––
LBHS rel16
Long Branch if Higher or Same
(if C = 0) (unsigned)
same function as LBCC
REL
18 24 qq rr
OPPP/OPO1
OPPP/OPO1
––––
––––
LBLE rel16
Long Branch if Less Than or Equal
(if Z + (N ⊕ V) = 1) (signed)
REL
18 2F qq rr
OPPP/OPO1
OPPP/OPO1
––––
––––
LBLO rel16
Long Branch if Lower
(if C = 1) (unsigned)
same function as LBCS
REL
18 25 qq rr
OPPP/OPO1
OPPP/OPO1
––––
––––
LBLS rel16
Long Branch if Lower or Same
(if C + Z = 1) (unsigned)
REL
18 23 qq rr
OPPP/OPO1
OPPP/OPO1
––––
––––
LBLT rel16
Long Branch if Less Than
(if N ⊕ V = 1) (signed)
REL
18 2D qq rr
OPPP/OPO1
OPPP/OPO1
––––
––––
LBMI rel16
Long Branch if Minus (if N = 1)
REL
18 2B qq rr
OPPP/OPO1
OPPP/OPO1
––––
––––
LBNE rel16
Long Branch if Not Equal (if Z = 0)
REL
18 26 qq rr
OPPP/OPO1
OPPP/OPO1
––––
––––
LBPL rel16
Long Branch if Plus (if N = 0)
REL
18 2A qq rr
OPPP/OPO1
OPPP/OPO1
––––
––––
LBRA rel16
Long Branch Always (if 1=1)
REL
18 20 qq rr
OPPP
OPPP
––––
––––
LBRN rel16
Long Branch Never (if 1 = 0)
REL
18 21 qq rr
OPO
OPO
––––
––––
LBVC rel16
Long Branch if Overflow Bit Clear (if V=0)
REL
18 28 qq rr
OPPP/OPO1
OPPP/OPO1
––––
––––
LBVS rel16
Long Branch if Overflow Bit Set (if V = 1)
REL
18 29 qq rr
OPPP/OPO1
OPPP/OPO1
––––
––––
LDAA #opr8i
LDAA opr8a
LDAA opr16a
LDAA oprx0_xysp
LDAA oprx9,xysp
LDAA oprx16,xysp
LDAA [D,xysp]
LDAA [oprx16,xysp]
(M) ⇒ A
Load Accumulator A
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
86 ii
96 dd
B6 hh ll
A6 xb
A6 xb ff
A6 xb ee ff
A6 xb
A6 xb ee ff
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
––––
∆∆0–
LDAB #opr8i
LDAB opr8a
LDAB opr16a
LDAB oprx0_xysp
LDAB oprx9,xysp
LDAB oprx16,xysp
LDAB [D,xysp]
LDAB [oprx16,xysp]
(M) ⇒ B
Load Accumulator B
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
C6 ii
D6 dd
F6 hh ll
E6 xb
E6 xb ff
E6 xb ee ff
E6 xb
E6 xb ee ff
P
rPf
rPO
rPf
rPO
frPP
fIfrPf
fIPrPf
P
rfP
rOP
rfP
rPO
frPP
fIfrfP
fIPrfP
––––
∆∆0–
LDD #opr16i
LDD opr8a
LDD opr16a
LDD oprx0_xysp
LDD oprx9,xysp
LDD oprx16,xysp
LDD [D,xysp]
LDD [oprx16,xysp]
(M:M+1) ⇒ A:B
Load Double Accumulator D (A:B)
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
CC jj kk
DC dd
FC hh ll
EC xb
EC xb ff
EC xb ee ff
EC xb
EC xb ee ff
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
––––
∆∆0–
Note 1. OPPP/OPO indicates this instruction takes four cycles to refill the instruction queue if the branch is taken and three cycles if the branch is not taken.
S12CPUV2
MOTOROLA
Reference Manual
Instruction Reference
393
Instruction Reference
Table A-1. Instruction Set Summary (Sheet 8 of 14)
Source Form
Operation
Addr.
Mode
Machine
Coding (hex)
Access Detail
HCS12
M68HC12
SXHI
NZVC
LDS #opr16i
LDS opr8a
LDS opr16a
LDS oprx0_xysp
LDS oprx9,xysp
LDS oprx16,xysp
LDS [D,xysp]
LDS [oprx16,xysp]
(M:M+1) ⇒ SP
Load Stack Pointer
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
CF jj kk
DF dd
FF hh ll
EF xb
EF xb ff
EF xb ee ff
EF xb
EF xb ee ff
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
––––
∆∆0–
LDX #opr16i
LDX opr8a
LDX opr16a
LDX oprx0_xysp
LDX oprx9,xysp
LDX oprx16,xysp
LDX [D,xysp]
LDX [oprx16,xysp]
(M:M+1) ⇒ X
Load Index Register X
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
CE jj kk
DE dd
FE hh ll
EE xb
EE xb ff
EE xb ee ff
EE xb
EE xb ee ff
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
––––
∆∆0–
LDY #opr16i
LDY opr8a
LDY opr16a
LDY oprx0_xysp
LDY oprx9,xysp
LDY oprx16,xysp
LDY [D,xysp]
LDY [oprx16,xysp]
(M:M+1) ⇒ Y
Load Index Register Y
IMM
DIR
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
CD jj kk
DD dd
FD hh ll
ED xb
ED xb ff
ED xb ee ff
ED xb
ED xb ee ff
PO
RPf
RPO
RPf
RPO
fRPP
fIfRPf
fIPRPf
OP
RfP
ROP
RfP
RPO
fRPP
fIfRfP
fIPRfP
––––
∆∆0–
LEAS oprx0_xysp
LEAS oprx9,xysp
LEAS oprx16,xysp
Effective Address ⇒ SP
Load Effective Address into SP
IDX
IDX1
IDX2
1B xb
1B xb ff
1B xb ee ff
Pf
PO
PP
PP1
PO
PP
––––
––––
LEAX oprx0_xysp
LEAX oprx9,xysp
LEAX oprx16,xysp
Effective Address ⇒ X
Load Effective Address into X
IDX
IDX1
IDX2
1A xb
1A xb ff
1A xb ee ff
Pf
PO
PP
PP1
PO
PP
––––
––––
LEAY oprx0_xysp
LEAY oprx9,xysp
LEAY oprx16,xysp
Effective Address ⇒ Y
Load Effective Address into Y
IDX
IDX1
IDX2
19 xb
19 xb ff
19 xb ee ff
Pf
PO
PP
PP1
PO
PP
––––
––––
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
INH
INH
78 hh ll
68 xb
68 xb ff
68 xb ee ff
68 xb
68 xb ee ff
48
58
rPwO
rPw
rPwO
frPPw
fIfrPw
fIPrPw
O
O
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
O
O
––––
∆∆∆∆
INH
59
O
O
––––
∆∆∆∆
EXT
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
INH
INH
74 hh ll
64 xb
64 xb ff
64 xb ee ff
64 xb
64 xb ee ff
44
54
rPwO
rPw
rPwO
frPwP
fIfrPw
fIPrPw
O
O
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
O
O
––––
0∆∆∆
INH
49
O
O
––––
0∆∆∆
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
18 18 xb
18 18 xb ff
18 18 xb ee ff
18 18 xb
18 18 xb ee ff
OrPf
OrPO
OfrPP
OfIfrPf
OfIPrPf
OrfP
OrPO
OfrPP
OfIfrfP
OfIPrfP
––––
∆∆∆∆
LSL opr16a
LSL oprx0_xysp
LSL oprx9,xysp
LSL oprx16,xysp
LSL [D,xysp]
LSL [oprx16,xysp]
LSLA
LSLB
0
b7
C
Logical Shift Left
same function as ASL
b0
Logical Shift Accumulator A to Left
Logical Shift Accumulator B to Left
LSLD
0
b0
b7 A
b7
B
C
Logical Shift Left D Accumulator
same function as ASLD
LSR opr16a
LSR oprx0_xysp
LSR oprx9,xysp
LSR oprx16,xysp
LSR [D,xysp]
LSR [oprx16,xysp]
LSRA
LSRB
b0
0
b7
Logical Shift Right
b0
C
Logical Shift Accumulator A to Right
Logical Shift Accumulator B to Right
LSRD
0
b0
A
b7
b7
B
Logical Shift Right D Accumulator
MAXA oprx0_xysp
MAXA oprx9,xysp
MAXA oprx16,xysp
MAXA [D,xysp]
MAXA [oprx16,xysp]
MAX((A), (M)) ⇒ A
MAX of 2 Unsigned 8-Bit Values
N, Z, V and C status bits reflect result of
internal compare ((A) – (M)).
b0
C
Note 1. Due to internal CPU requirements, the program word fetch is performed twice to the same address during this instruction.
Reference Manual
394
S12CPUV2
Instruction Reference
MOTOROLA
Instruction Reference
Table A-1. Instruction Set Summary (Sheet 9 of 14)
Source Form
Operation
Access Detail
Addr.
Mode
Machine
Coding (hex)
HCS12
M68HC12
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
18 1C xb
18 1C xb ff
18 1C xb ee ff
18 1C xb
18 1C xb ee ff
OrPw
OrPwO
OfrPwP
OfIfrPw
OfIPrPw
Special
01
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
IDX
IDX1
IDX2
[D,IDX]
[IDX2]
SXHI
NZVC
OrPw
OrPwO
OfrPwP
OfIfrPw
OfIPrPw
––––
∆∆∆∆
RRfOw
RRfOw
––?–
????
18 19 xb
18 19 xb ff
18 19 xb ee ff
18 19 xb
18 19 xb ee ff
OrPf
OrPO
OfrPP
OfIfrPf
OfIPrPf
OrfP
OrPO
OfrPP
OfIfrfP
OfIPrfP
––––
∆∆∆∆
18 1D xb
18 1D xb ff
18 1D xb ee ff
18 1D xb
18 1D xb ee ff
OrPw
OrPwO
OfrPwP
OfIfrPw
OfIPrPw
OrPw
OrPwO
OfrPwP
OfIfrPw
OfIPrPw
––––
∆∆∆∆
MOVB #opr8, opr16a1
(M1) ⇒ M2
MOVB #opr8i, oprx0_xysp1
Memory to Memory Byte-Move (8-Bit)
1
MOVB opr16a, opr16a
1
MOVB opr16a, oprx0_xysp
MOVB oprx0_xysp, opr16a1
MOVB oprx0_xysp, oprx0_xysp1
OPwP
IMM-EXT 18 0B ii hh ll
OPwO
IMM-IDX 18 08 xb ii
EXT-EXT 18 0C hh ll hh ll OrPwPO
OPrPw
EXT-IDX 18 09 xb hh ll
OrPwP
IDX-EXT 18 0D xb hh ll
OrPwO
IDX-IDX 18 0A xb xb
OPwP
OPwO
OrPwPO
OPrPw
OrPwP
OrPwO
––––
––––
MOVW #oprx16, opr16a1
(M:M+11) ⇒ M:M+12
MOVW #opr16i, oprx0_xysp1
Memory to Memory Word-Move (16-Bit)
MOVW opr16a, opr16a1
MOVW opr16a, oprx0_xysp1
MOVW oprx0_xysp, opr16a1
MOVW oprx0_xysp, oprx0_xysp1
IMM-EXT 18 03 jj kk hh ll OPWPO
OPPW
IMM-IDX 18 00 xb jj kk
EXT-EXT 18 04 hh ll hh ll ORPWPO
OPRPW
EXT-IDX 18 01 xb hh ll
ORPWP
IDX-EXT 18 05 xb hh ll
ORPWO
IDX-IDX 18 02 xb xb
OPWPO
OPPW
ORPWPO
OPRPW
ORPWP
ORPWO
––––
––––
ffO
––––
–––∆
rOPw
rPw
rPOw
frPPw
fIfrPw
fIPrPw
O
––––
∆∆∆∆
MAXM oprx0_xysp
MAXM oprx9,xysp
MAXM oprx16,xysp
MAXM [D,xysp]
MAXM [oprx16,xysp]
MAX((A), (M)) ⇒ M
MAX of 2 Unsigned 8-Bit Values
MEM
µ (grade) ⇒ M(Y);
(X) + 4 ⇒ X; (Y) + 1 ⇒ Y; A unchanged
N, Z, V and C status bits reflect result of
internal compare ((A) – (M)).
if (A) < P1 or (A) > P2 then µ = 0, else
µ = MIN[((A) – P1)×S1, (P2 – (A))×S2, $FF]
where:
A = current crisp input value;
X points at 4-byte data structure that describes a trapezoidal
membership function (P1, P2, S1, S2);
Y points at fuzzy input (RAM location).
See CPU12 Reference Manual for special cases.
MINA oprx0_xysp
MINA oprx9,xysp
MINA oprx16,xysp
M