



+
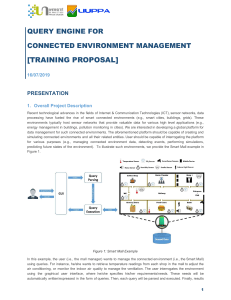
Area_E Area_A Area_B Area_C Area_D
=- -

(0,0) (399,0)
(0,399) (399,399)
(0,0) (399,0)
(0,399) (399,399)
A1 A2 A3
A4 A5 A6
A7 A8 A9
(a) (b)
(0,0) (399,0)
(0,399) (399,399)
B1 B2 B3
B4 B6
B7 B8 B9
(c)
(0,0) (399,0)
(0,399) (399,399)
C1 C2 C3
C4 C6
C7 C8 C9
(d)
(0, 399)
(b)(a)
(0, 0)
(0, 399) (399, 399) (399, 399)
(0, 0) (399, 0)(399, 0)
 6
6
 7
7
 8
8
 9
9
 10
10
 11
11
 12
12
 13
13
 14
14
 15
15
 16
16
1
/
16
100%


![[ciir-publications.cs.umass.edu]](http://s1.studylibfr.com/store/data/009557090_1-fe10e8e9594ee37ae769fe35a2448716-300x300.png)






